Web Application Firewall(Web Application Firewall,簡稱WAF)安全報表向您展示WAF不同模組防護規則的防護記錄。您可以使用安全報表,查看已啟用的Web核心防護規則、IP黑名單規則、自訂規則等的防護資料,進行業務安全分析。
前提條件
已將Web業務添加為WAF 3.0的防護對象和防護對象組。
已為防護對象配置了防護規則。Web 核心防护规则模組預設啟用,無需手動設定;其他防護模組需要手動設定具體規則後,才會生效。更多資訊,請參見防護配置概述。
查看安全報表
安全報表在請求量較大時採用動態採樣與資料還原機制。系統按QPS均值自動調整採樣比例,並基於採樣比還原統計結果,報表中展示的為預估全量資料,可準確反映攻擊趨勢和分布。如需擷取完整原始日誌用於深度分析或合規審計,請開通Log Service。
根據WAF執行個體所屬地區的不同,在華東1(杭州)和新加坡分別設定了管控平面。其中,中國內地的WAF執行個體將使用華東1(杭州)的管控平面進行管控,非中國內地的WAF執行個體將使用新加坡的管控平面進行管控。
在Web Application Firewall3.0控制台的安全报表頁面,共分為攻擊趨勢圖、攻擊類型分布圖、TOP5命中情況統計和日誌列表四大板塊展示報表資訊。您可以通過簡單搜索或進階搜尋設定過濾條件,搜尋查詢對應的安全報表資料。
普通搜尋 | 進階搜尋 |
|
|
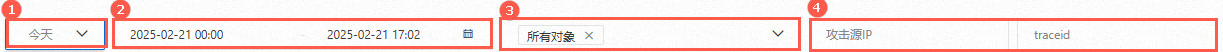
時間範圍(圖①),預設展示今天的資料,可以查詢最近15分钟、最近30分钟、最近1小时、最近24小时、今天、昨天、7 天、30 天內的資料。 | |
自訂日期搜尋範圍(圖②),可以根據實際需要選擇特定的時間段,以便更精準地查看安全報表資料。 | |
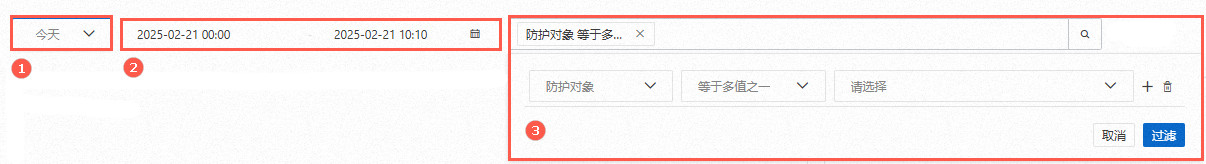
防護對象(圖③),預設已選擇所有对象,表示查詢已接入WAF防護的所有對象的資料,您也可以只查詢某個對象的資料。 | 設定過濾條件(圖③),支援添加多個過濾條件,最多可設定10條。 |
請輸入攻擊源IP或traceid(圖④)。 | \ |
攻擊趨勢圖
在攻擊趨勢圖中,您可以查看警示量和攔截量的走勢。預設展示全部防護對象的資料,也可以根據您設定的過濾條件動態重新整理。將滑鼠移至上方在趨勢圖的任意時間點上,可以顯示該時刻的警示數量和攔截數量。
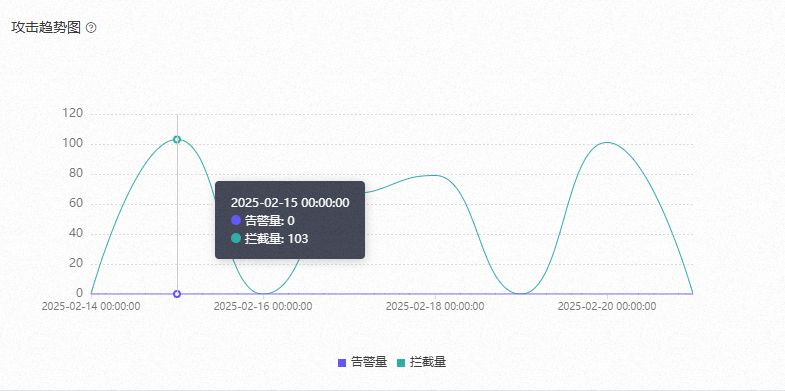
拦截量:記錄被攔截防護動作阻止的請求,或未能通過JS驗證、滑塊、嚴格滑塊、動態令牌等安全檢查而遭到攔截的請求。
告警量:記錄命中規則並觸發觀察動作的請求。
攻擊類型分布圖
統計請求命中規則的總次數,一條請求可能命中多個防護模組或多條規則,支援查看Web 核心防护规则、IP黑名单、自定义规则、扫描防护、CC防护、区域封禁、BOT管理、信息泄露防护、洪峰限流和AI应用防护。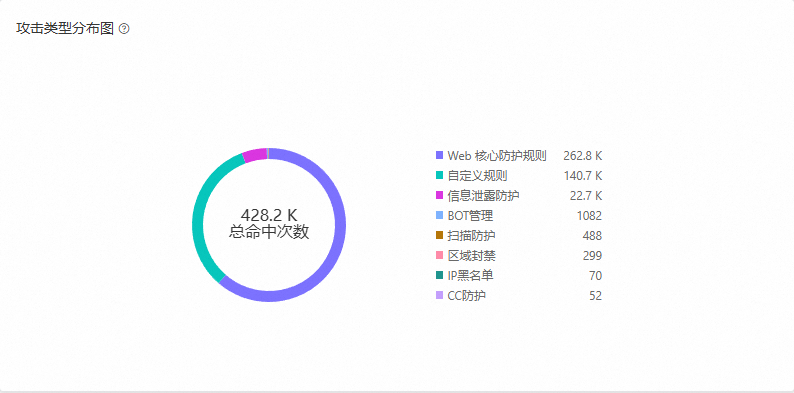
單擊餅狀圖中的Web 核心防护规则部分,查看Web核心防護規則中各攻擊類型(如SQL注入、XSS、代碼執行等)的佔比餅圖。
單擊餅狀圖中其他防護模板,查看攻擊規則的佔比餅圖。
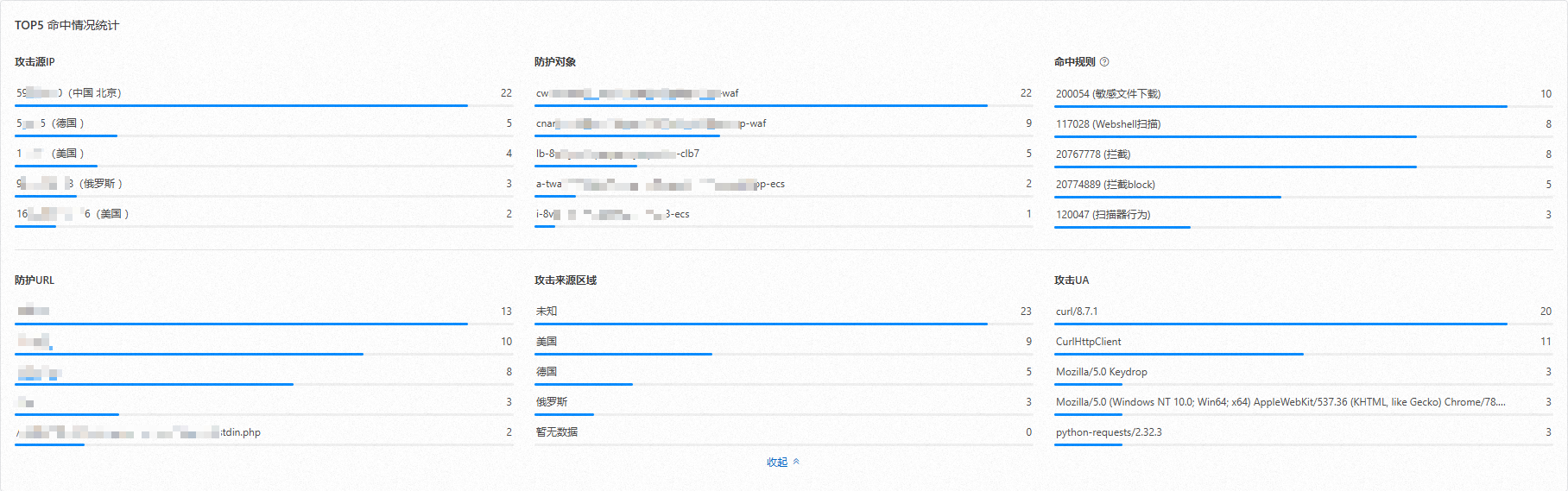
TOP5命中情況統計
查看攻击源IP、防护对象、命中規則、防護URL、攻擊來源區域和攻击UA的命中統計情況。
資料類型 | 說明 | 支援的操作 |
攻击源IP | 發起攻擊請求次數最多的前5個IP及其所屬地區。 | 將滑鼠移至上方在目標資料類型上,單擊過濾或排除,可直接產生相應的過濾條件。 |
防護URL | 命中規則次數最多的前5個URL。 | |
攻擊來源區域 | 發起攻擊請求次數最多的前5個地區。 | |
攻击UA | 發動攻擊次數最多的前5個User-Agent。 | |
防护对象 | 觸發防護規則次數最多的前5個防護對象。 | 將滑鼠移至上方在目標資料類型上,單擊過濾或排除,可直接產生相應的過濾條件;單擊查看防护规则,可跳轉查看該防護對象的具體防護規則。 |
命中規則 | 被叫用次數最多的前5個防護規則的ID。 說明 一條請求可能命中多條規則。 |
日誌列表
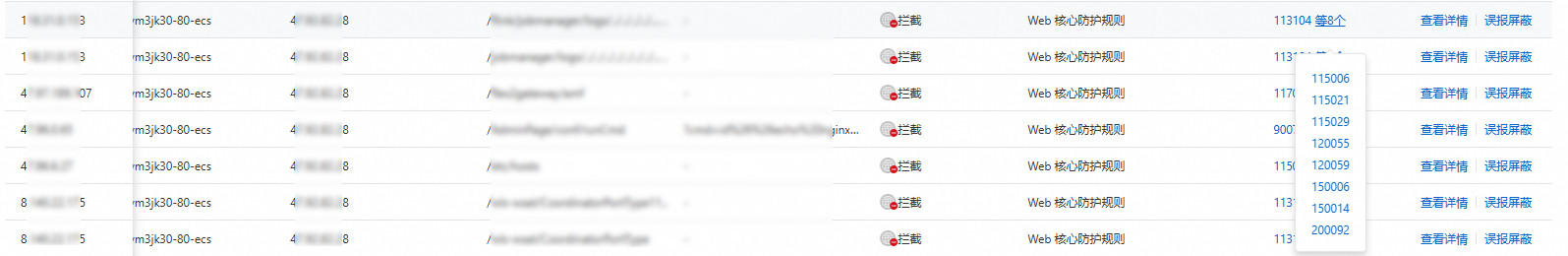
查看攻击IP、所属区域、防护对象、攻击时间、Host、攻击URL、协议、端口、请求方法、请求参数、规则动作、防護模組、規則ID和AI分析的詳細資料。單擊右上方 表徵圖,自訂欄表展示資訊。
表徵圖,自訂欄表展示資訊。
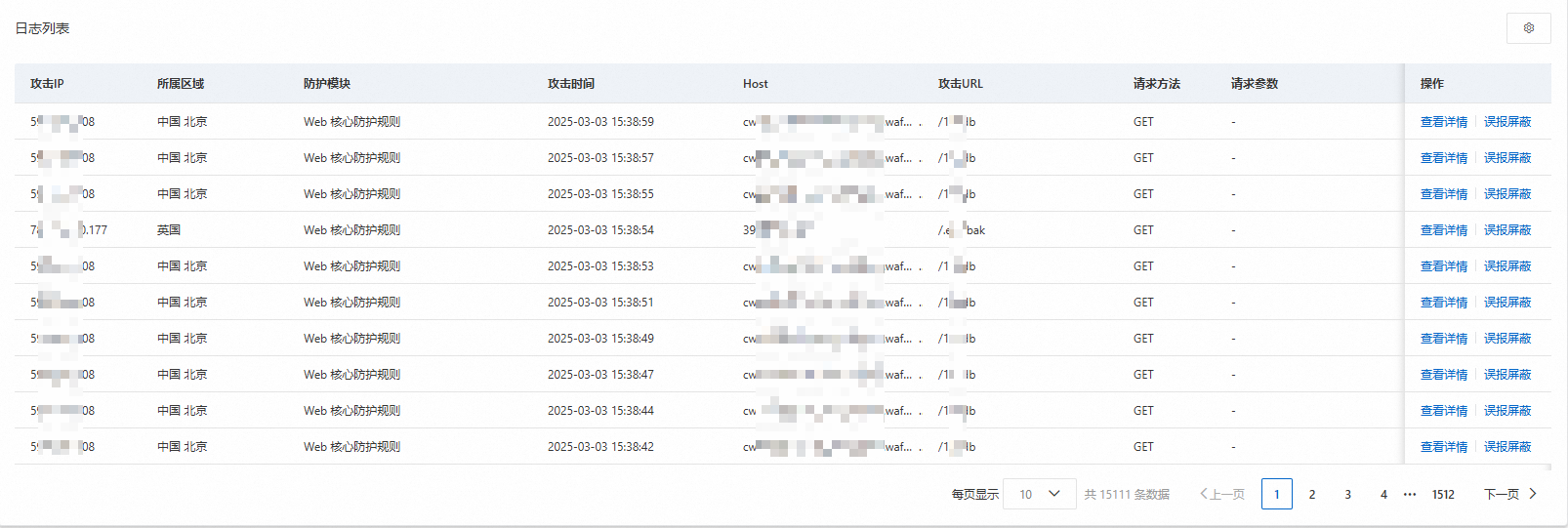
單擊某個攻擊事件操作列下的查看詳情,可以查看攻击详情,擷取關於攻擊事件和防護規則的更多資訊。
如果您確認某條日誌為誤判,可單擊該攻擊事件操作列下的误报屏蔽,確認白名單規則條件後,單擊确定。
建立完規則後,WAF會自動建立一個規則模板名稱為AutoTemplate的模板,並自動添加一條白名單規則,且規則來源為自定义。
通過單擊AI分析列的表徵圖,可對單條日誌執行安全AI助手分析。當前僅支援Web核心防護規則產生的日誌,不支援其他類型日誌及混合雲接入方式下的日誌分析。
一條請求可能命中多個防護模組或多條規則,您可以將滑鼠移至上方在规则ID上或單擊查看详情查看命中的具體規則ID。