開通Web Application Firewall (WAF)後,阿里雲預設為WAF提供最大5 Gbps的DDoS基礎防護能力。DDoS基礎防護通過對進入WAF的流量進行清洗,有效防禦DDoS攻擊,緩解WAF因流量激增進入黑洞。本文介紹什麼是DDoS基礎防護、如何防禦WAF進入黑洞、WAF進入黑洞後如何處理。
DDoS基礎防護
防護能力
阿里雲免費為Web Application Firewall (WAF)提供最大5 Gbps的DDoS基礎防護能力。不同地區支援的最大免費防護規格不同,更多資訊,請參見DDoS基礎防護黑洞閾值。
防護原理
在不影響正常業務的前提下,DDoS基礎防護會對流入WAF的流量(包括正常流量和攻擊流量)進行清洗,將可疑DDoS攻擊流量從原始網路路徑中重新導向到清洗裝置上,識別並剝離惡意流量後,將還原的合法流量回注到原始網路中轉寄給WAF,有效防禦DDoS攻擊。
流量清洗
當流入WAF的流量觸發流量清洗條件時,DDoS基礎防護會對流量進行清洗。執行個體處於清洗狀態時,您可以在Web Application Firewall3.0控制台頂部橫幅地區收到提示資訊。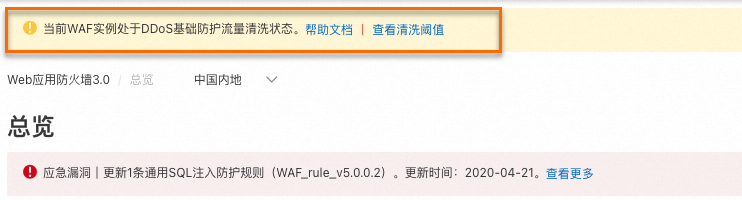
清洗條件
當流入WAF的流量滿足流量模型特徵,且達到設定的清洗閾值時,會觸發流量清洗。
流量模型的特徵:DDoS基礎防護能夠基於阿里雲的巨量資料能力,自動學習您的業務流量基準,並結合演算法識別異常攻擊。
流量大小:根據實際QPS設定的清洗閾值。一個WAF執行個體防護的公網IP資產的清洗閾值相同,包括獨享IP、共用叢集智能負載平衡的所有防護節點。
說明如果流入WAF的業務頻寬超過清洗閾值,但沒有被識別到攻擊行為,則不會觸發清洗操作。
清洗閾值
流量清洗的方法包括過濾攻擊報文、限制流量速度、限制資料包速度等。所以,在使用DDoS基礎防護時,您需要設定以下閾值:
BPS(Bits per Second,資料轉送速率)清洗閾值:當入方向流量超過BPS清洗閾值時,會觸發流量清洗。
PPS(Packet per Second,資料包收發速率)清洗閾值:當入方向資料包數超過PPS清洗閾值時,會觸發流量清洗。
WAF的清洗閾值由實際業務QPS決定,具體計算方式如下表所示。
類型
對應值
最大BPS清洗閾值(Mbps)
MAX(800,QPS*4.5/150)
最大PPS清洗閾值(pps)
MAX(800000,QPS*4.5)
最終清洗閾值以控制台顯示為準。
查看和設定清洗閾值
系統預設清洗閾值為DDoS基礎防護支援的最大清洗閾值。如果該閾值過高,無法觸發流量清洗,您可以修改清洗閾值。
登入流量安全產品控制台。
在左側導覽列,單擊資產中心。
在頂部功能表列左上方處,選擇資產所在地區。
單擊WAF頁簽,定位到目標執行個體,在清洗閾值列,查看最大BPS清洗閾值、最大PPS清洗閾值。
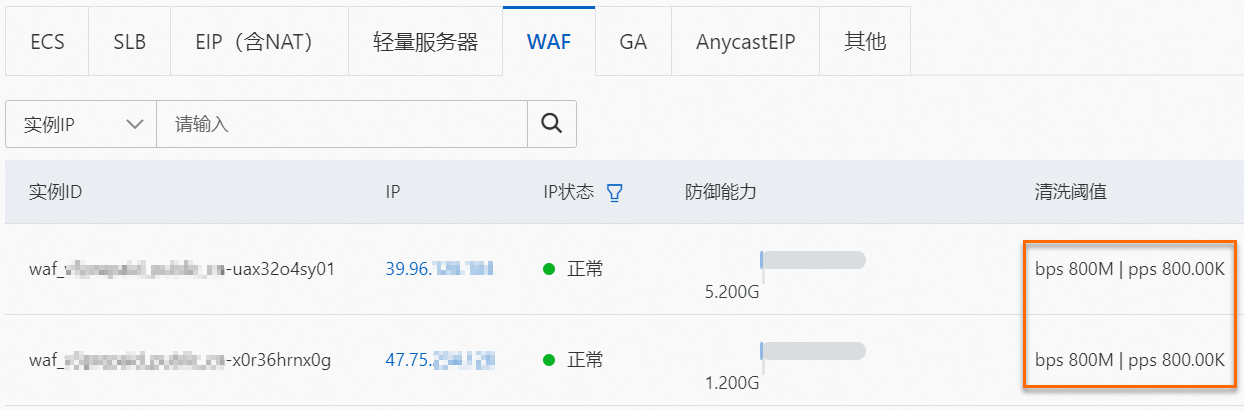
可選:如果執行個體對應的閾值不符合您的實際業務情況,您可以修改清洗閾值。
定位到目標執行個體,單擊對應IP。
在IP詳情頁面,單擊清洗設定。
系統預設:DDoS基礎防護服務根據WAF執行個體的流量負載自動調整清洗閾值。
手動設定:選擇流量和報文數量的清洗閾值。
說明當DDoS檢測到攻擊時,如果流量或者報文數量其中之一達到閾值,就會觸發流量清洗。
清洗閾值手動設定建議:
清洗閾值需要略高於實際訪問值。閾值如果設定過高,起不到防禦效果;如果設定過低,DDoS原生防護觸發流量清洗可能會影響正常的訪問。
如果清洗影響了正常的請求,請適當調高清洗閾值。
網站進行推廣或促銷活動時,建議您適當調高清洗閾值。
黑洞
當流入WAF的峰值頻寬(清洗後的流量頻寬、沒有DDoS攻擊行為的流量頻寬)超過DDoS基礎防護閾值5 Gbps,WAF將進入黑洞。進入黑洞後,所有訪問WAF的流量(包括正常請求和攻擊請求)都會被丟棄。
一個WAF執行個體防護的公網IP資產的黑洞閾值(即最大防護能力)相同,包括獨享IP、共用叢集智能負載平衡的所有防護節點。
此時,您會在Web Application Firewall3.0控制台頂部橫幅地區,收到提示資訊。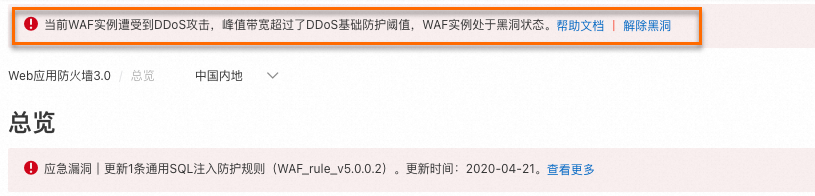
為避免因WAF進入黑洞造成您的網站長時間無法被訪問,我們建議您在資訊中心的語音接收管理頁面,勾選DDoS黑洞的語音警示通知,並設定訊息接收人。具體操作,請參見配置訊息中心警示。
當WAF進入黑洞時,即使在夜間,您也將收到語音提醒,請您及時上線處理。
如何預防黑洞
DDoS防禦能力越大,黑洞閾值就越大,WAF被DDoS攻擊導致觸發黑洞的可能就越低。如果DDoS基礎防護的防禦能力不能滿足您的業務需要,您可以通過購買商用版DDoS防護產品,例如DDoS原生防護或DDoS高防服務,提升DDoS防禦能力,避免WAF進入黑洞。關於DDoS選型的更多資訊,請參見如何選擇DDoS防護產品。
如何解除黑洞
手動解除:如果您希望立即解除黑洞,您可以在WAF控制台頂部橫幅地區,單擊解除黑洞,參考黑洞自動解除最佳實務,手動解除黑洞狀態。具體操作,請參見黑洞自動解除最佳實務。
自動解除:您也可以耐心等待,當DDoS攻擊結束後的一段時間(即黑洞自動解除時間),DDoS基礎防護會自動為WAF解除黑洞,恢複互連網訪問。
您可以在流量安全產品控制台的資產中心頁面,查看當前解除黑洞時間。同一UID的黑洞次數越多,黑洞時間越長。
獨享IP或共用叢集智能負載平衡與黑洞
開啟獨享IP或共用叢集智能負載平衡,並不能直接防禦WAF進入黑洞,但可以避免重要IP因WAF被黑洞而無法訪問、保證業務流量正常從WAF回原始伺服器。
WAF處於清洗或黑洞狀態時,不支援開啟独享IP、共享集群智能负载均衡。
開啟独享IP
所有網域名稱接入同一個WAF執行個體後會預設分配一個共用的IP,用於監聽相關業務請求。獨享IP則支援單獨為某個網域名稱額外分配一個WAF IP,專門用於監聽該網域名稱的業務請求,且不受共用WAF IP的影響。更多資訊,請參見網域名稱獨享IP。
開啟独享IP後,共用WAF IP和獨享IP的黑洞狀態相互不受影響。
如果独享IP進入黑洞後,關閉独享IP,DDoS攻擊可能會轉移到預設分配的共用WAF IP中,從而影響其他網域名稱的正常業務。
開啟共享集群智能负载均衡
共用叢集智能負載平衡為WAF執行個體配備至少三個不同地區的防護節點,以實現異地多節點自動容災,同時通過智能DNS解析能力和Least-time回源演算法,保證業務流量從接入防護節點到轉寄回來源站點伺服器整個鏈路的路徑和時延最短。更多資訊,請參見智能負載平衡。
開啟共享集群智能负载均衡後,如果某個地區的防護節點進入黑洞,WAF會自動為您切換防護節點,保證業務流量正常從WAF回原始伺服器。
關閉共享集群智能负载均衡後,如果某個防護節點進入黑洞,則會影響該條鏈路的業務無法正常回源到伺服器。
常見問題
WAF配置了多個網域名稱,如何查看是哪個網域名稱被攻擊?
一般情況下,駭客會解析某個已接入WAF防護的網域名稱,在擷取WAF IP後,對其發起DDoS攻擊。大流量的DDoS攻擊都是針對WAF IP,從攻擊流量中無法得知具體哪個網域名稱被攻擊。
您可以使用網域名稱拆分來獲知哪個網域名稱被攻擊。例如,您可以將部分網域名稱解析到WAF,部分網域名稱解析到其他地址(ECS來源站點、CDN或SLB 等),如果拆分之後WAF不再被黑洞,說明駭客的攻擊目標在拆分出去的部分網域名稱。但是,這種方式操作比較複雜,且可能導致來源站點等其他資產的暴露,從而引發更大的安全問題。因此,除非在必要情況下,不建議您通過這種方式來判斷哪個網域名稱被攻擊。
通過更換WAF IP,是否就能不會被黑洞了?
更換WAF IP無法解決實際問題。
WAF處於清洗或黑洞狀態時,刪除所有網域名稱後重新接入網域名稱、關閉WAF執行個體重新購買執行個體後,WAF會為執行個體分配原來被DDoS攻擊的WAF IP。
說明解除清洗或黑洞後,如果您希望重新分配新WAF IP,可執行如下操作:
刪除所有網域名稱後,重新接入WAF。
開啟獨享IP和共用叢集智能負載平衡。
如果駭客針對您的網域名稱進行攻擊,即使您更換了WAF IP,駭客只需要ping您的網域名稱就能擷取到更換後的IP,並且繼續發起DDoS攻擊。
DDoS攻擊和CC攻擊有什麼區別?WAF為什麼不能防禦DDoS攻擊?
大流量的DDoS攻擊主要是針對IP的四層攻擊,而CC攻擊是針對七層應用的攻擊(例如HTTP GET/POST Flood)。WAF可以防禦CC攻擊,但對於大流量的DDoS攻擊,由於需要通過足夠大的頻寬資源把所有流量都硬抗下來再進行清洗,只能通過DDoS防護服務來防護。
針對CC攻擊,使用DDoS高防還是Web Application Firewall?
CC攻擊通過使用Proxy 伺服器向客戶目標伺服器發送大量看似合法的請求,導致伺服器效能異常問題。
Web Application Firewall的CC防護策略需要根據業務需求,手動設定合理的防護策略。例如,使用WAF自訂防護策略功能的頻率設定,根據業務需求調整防護路徑和觸發防護的閾值,選擇合適的處置動作。對於請求特徵不合理,在分析異常的請求特徵基礎上,使用WAF自訂防護策略的ACL存取控制規則設定對應的封鎖策略。對於面向中國使用者的網站,在遭受攻擊時通過封鎖海外訪問來緩解攻擊。對於爬蟲造成負載飆升等異常,開啟並使用Bot管理模組。
DDoS高防:針對複雜CC攻擊可實現自動化防護,根據攻擊的實際情況快速自動地適配並調整防護策略。AI智能防護自學習網站業務流量基準,結合演算法分析攻擊異常,自動下發精確的存取控制規則。
從防護能力來說,DDos高防提供了更強大的防禦峰值能力。從精細化原則設定,WAF提供了更細粒度的應用程式層精準存取控制及限速能力。如果您的CC攻擊水位很高,優先建議DDoS高防,如果CC攻擊水位不是很高,且需要應用程式層細粒度的存取控制策略、混合爬蟲攻擊,優先建議Web Application Firewall。