Web Application Firewall(Web Application Firewall,簡稱WAF)日誌是記錄和分析網路流量及安全事件的重要工具,對於識別潛在威脅、進行安全審計和確保合規性至關重要。然而,當WAF日誌容量達到上限時,會導致日誌資料無法記錄,進而影響到安全監控和事件響應的能力。本文將為您介紹日誌容量達到上限後的常用解決方案。
背景資訊
WAF日誌記錄了對Web應用的所有訪問請求及防火牆的響應情況。這些日誌包含了攻擊檢測、過濾、阻斷等詳細資料,充足的日誌容量可以確保所有安全事件被完整記錄,協助管理員進行詳細分析和審計。如果日誌容量達到上限,可能會產生以下影響:
日誌丟失
當日誌使用量達到日誌儲存總量上限後,新的日誌資料將無法記錄,導致重要的安全事件資訊丟失。
安全威脅無法及時檢測
無法記錄新日誌,如果您有其他安全分析類的服務依賴WAF日誌,則可能會使得潛在的安全威脅無法被及時檢測和響應,增加了安全風險。
合規性問題
某些行業和法規要求企業保留日誌資料以供審計,日誌使用量達到日誌儲存總量上限後無法記錄新的日誌,可能導致合規性問題。
日誌容量達到上限如何處理
WAF日誌容量達到上限後,通常採用以下四種方法進行處理:
升級日誌儲存容量
升級日誌儲存容量是最直接的解決方案。通過配置更大的儲存空間可以確保WAF有足夠的容量來記錄所有的安全事件和網路流量資料。具體操作請參見升級日誌儲存空間
細粒度配置減少儲存空間使用量
通過針對不同業務的重要性,精細化地配置日誌記錄策略。例如對於非重要業務,僅記錄攻擊日誌和必選欄位,或者少量可選欄位降低儲存空間佔用量。具體操作請參見細粒度配置減少儲存空間使用量
減少日誌儲存時間長度
最佳化日誌儲存時間長度也是一種有效方法。根據業務需求,縮短日誌保留的時間,可以減少儲存空間的佔用。例如,將日誌保留期限從原來的30天縮短為7天,能夠在不丟失關鍵資料的前提下,節省大量的儲存空間。具體操作請參見減少日誌儲存時間長度
減少日誌索引欄位
關閉“索引自動更新”功能,並刪除部分不需要的欄位索引,可以顯著減少索引空間的佔用。索引雖然有助於快速查詢和分析日誌,但也會消耗大量的儲存空間。通過最佳化索引配置,可以在保證查詢效率的同時,減少儲存空間的使用。具體操作請參見減少日誌索引欄位
升級日誌儲存空間
僅針對訂用帳戶進階版、企業版、旗艦版的執行個體,支援查看和升級日誌儲存容量。隨用隨付執行個體按實際用量結算費用,並由Log Service統一出賬,因此沒有容量限制,無需單獨設定日誌容量。
登入Web Application Firewall3.0控制台,在左側導覽列,選擇,單擊右上方的升級容量。
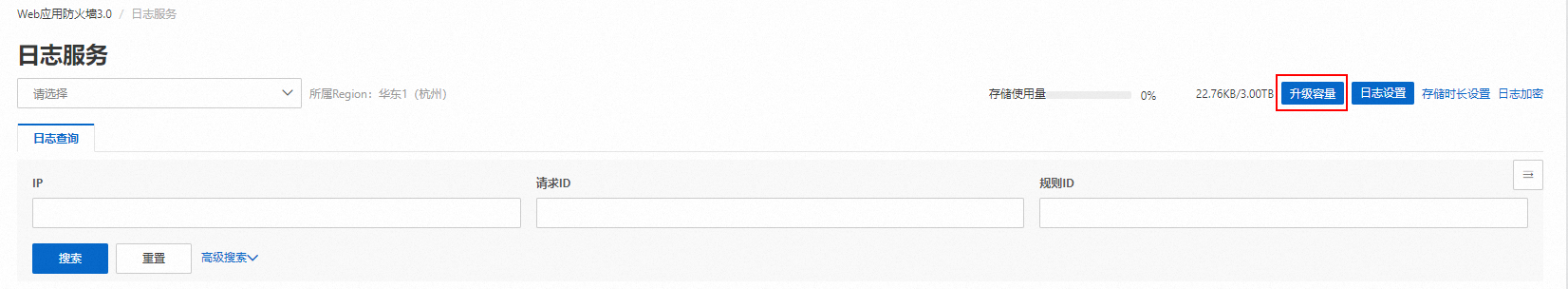
選擇更大的日誌儲存容量規格,並完成購買。
細粒度配置減少儲存空間使用量
日誌投遞欄位設定允許對單個防護對象進行精細化欄位配置和日誌儲存類型設定,如果針對某個防護對象進行了特定的欄位和日誌儲存類型配置,設定後的欄位優先順序高於預設欄位設定。
登入Web Application Firewall3.0控制台,在左側導覽列,選擇,單擊右上方的。
在投递设置頁簽中,單擊目標防護對象的SLS投递字段列的字段配置,完成如下表所示的配置操作。
配置項
配置說明
必選欄位
必選欄位表示WAF日誌中一定包含的欄位,目前不支援您對必選欄位進行編輯,欄位詳情請參見必選日誌欄位說明。
可選欄位
可選欄位表示您可以手動選擇是否在WAF日誌中包含這些欄位。WAF日誌只會記錄您已啟用的可選欄位,欄位詳情請參見可選日誌欄位說明。
說明啟用更多可選欄位將會增加WAF日誌的儲存容量使用。如果您有足夠的日誌儲存容量,建議啟用更多可選欄位以便更全面地進行日誌分析。
儲存類型
儲存類型配置支援您根據您購買的日誌儲存容量,選擇不同的日誌儲存選項:全量日誌、攔截日誌、攔截與觀察日誌。選擇合適的儲存類型有助於平衡安全監控與日誌儲存成本。
全量日誌:記錄所有請求,包括正常請求、可疑請求及被攔截的攻擊請求。適用於需要全面審計和深入分析的情境。
攔截日誌:僅記錄被WAF攔截的攻擊請求。適合關注安全事件並希望減少非關鍵日誌儲存資源消耗的使用者。
攔截與觀察日誌:記錄被WAF標記為可疑的請求和被攔截的攻擊請求。適用於希望監測潛在威脅的同時控制日誌儲存使用量的使用者。
對於非重要業務,您只需記錄攻擊日誌和必選欄位,或少量可選欄位,以降低儲存空間佔用。在完成日誌投遞欄位的配置後,單擊確定並看到操作成功提示後,代表當前配置已對單個防護對象生效。
減少日誌儲存時間長度
登入Web Application Firewall3.0控制台,在左側導覽列,選擇,單擊右上方的儲存時間長度設定,此時進入Log Service控制台。
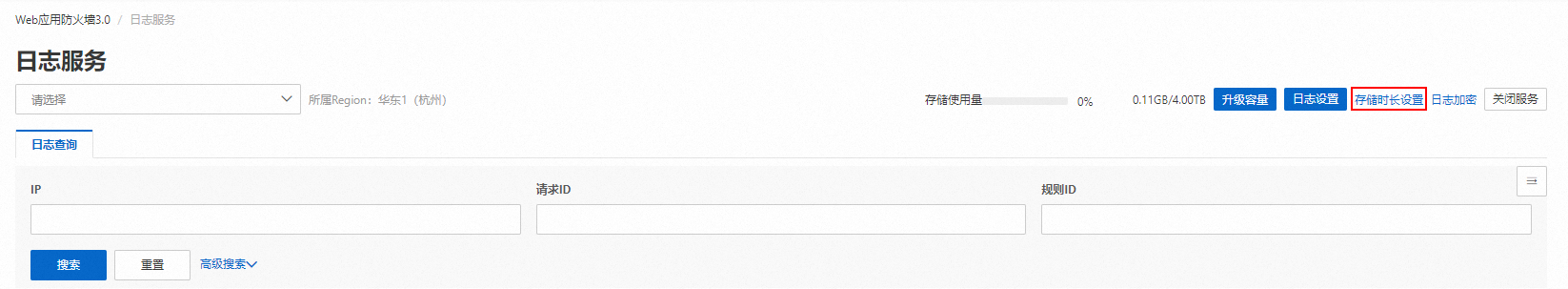
在Logstore屬性面板中單擊右上方的修改,減少資料儲存時間後,單擊儲存。
重要在調整日誌儲存時間時,務必確保符合相關法規和合規性要求,以避免因資料保留不足而導致的合規性問題。
當日誌儲存時間達到您所設定的限定天數時後,超期的日誌將會自動刪除。

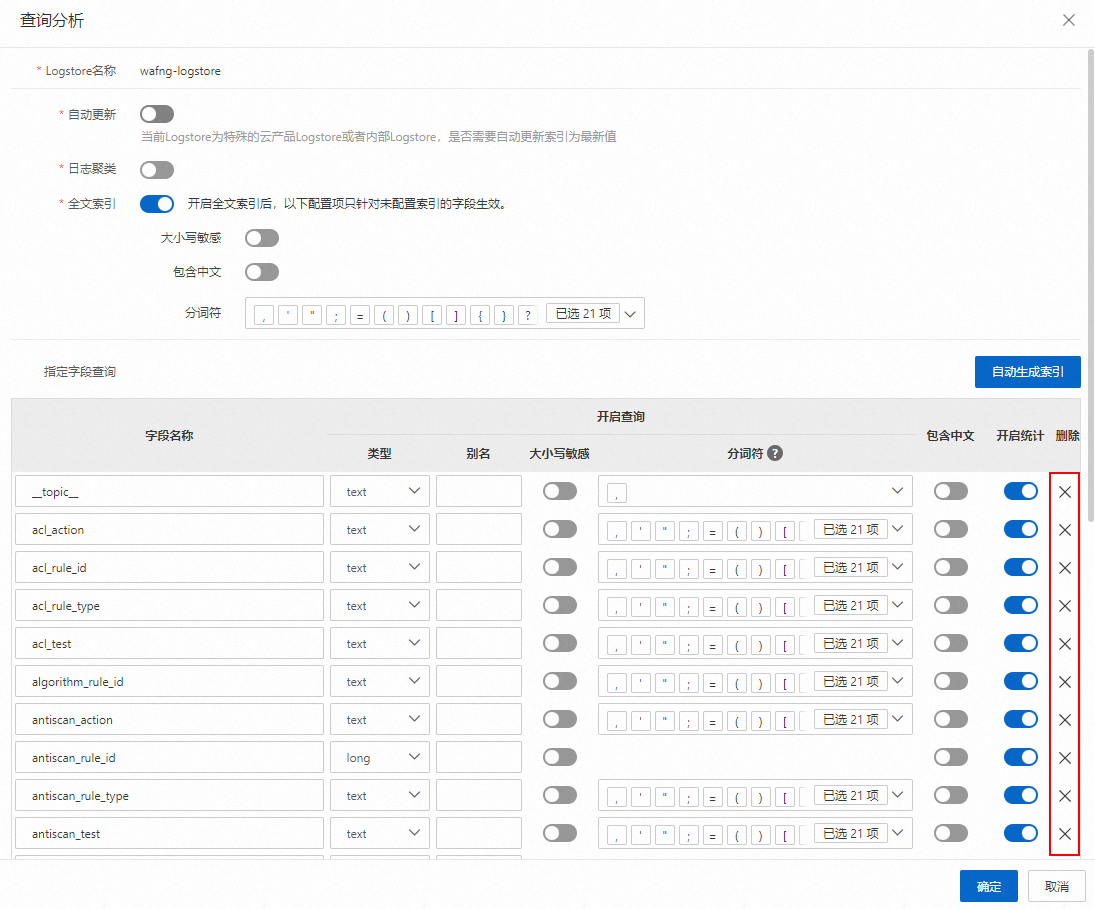
減少日誌索引欄位
登入Log Service控制台,在Project列表地區,單擊以
wafng開頭的目標Project。
在左側導覽列,單擊日誌儲存
 ,在日誌庫列表中單擊目標Logstore。
,在日誌庫列表中單擊目標Logstore。
在Logstore的查詢和分析頁面,選擇。
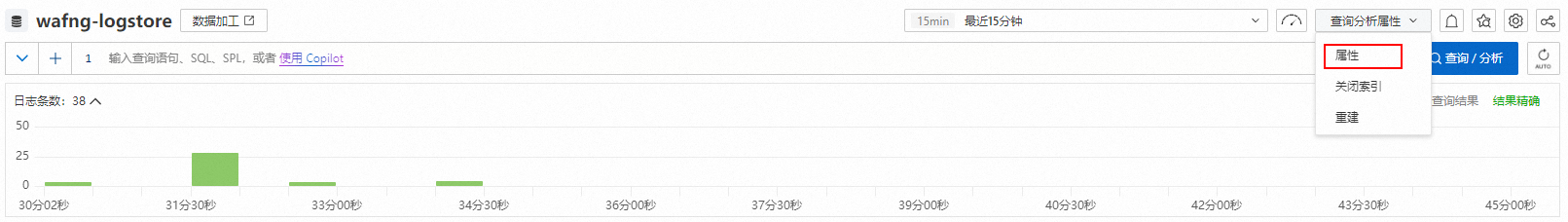
關閉自動更新索引。當前Logstore為特殊的雲產品Logstore或者內部Logstore時,預設開啟索引自動更新開關,此時指定欄位查詢地區為不可操作狀態,在查詢分析面板中,關閉自動更新開關。
警告如果您在SLS配置了自訂報表和警示功能,刪除WAF產品專屬Logstore的索引,可能會影響自訂報表和警示功能,請謹慎操作
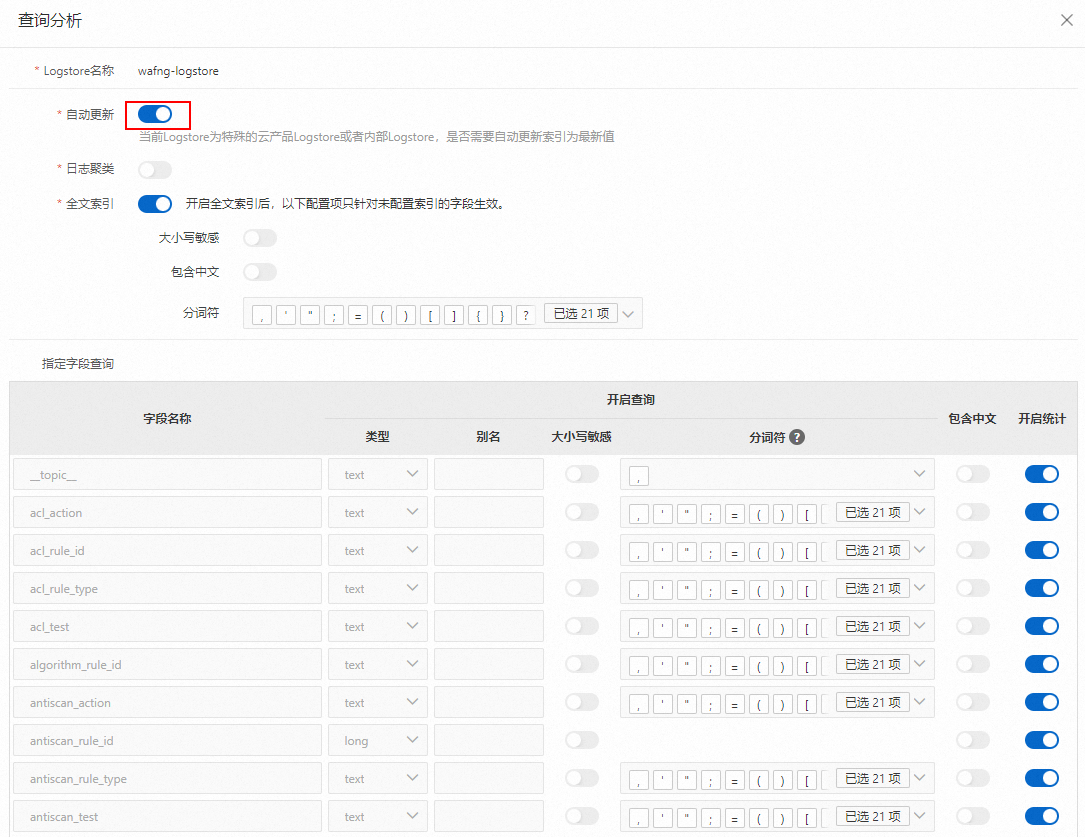
刪除索引。關閉自動更新開關後,您可以在指定欄位查詢地區刪除不需要的欄位索引,刪除索引後單擊確認。