Web Application Firewall(Web Application Firewall,簡稱WAF)可防禦SQL注入、跨站指令碼、CC攻擊、惡意Bot等Web攻擊。本文介紹如何基於業務需求,開通WAF 3.0隨用隨付執行個體。
適用範圍
請確保您的阿里雲帳號未開通任何版本的WAF執行個體,若已開通WAF 2.0執行個體且需使用WAF 3.0執行個體,請根據以下情況進行操作:
WAF 2.0執行個體中存在運行中的業務:使用遷移工具將WAF 2.0執行個體升級到WAF 3.0。
WAF 2.0執行個體中無運行業務:關閉WAF2.0執行個體後,執行本文的開通操作。
開通WAF隨用隨付執行個體
隨用隨付版WAF除請求處理費用外,還收取功能費用(包括WAF執行個體本身的費用等)。因此開通WAF後無論是否進行配置,立即開始計費。具體計費規則請參見計費說明。
選擇商品類型為Web应用防火墙3.0,並選擇按量版本:适用于业务用量有较大的波动变化的个人/企业网站,或者对安全功能使用和计费模式有灵活的需求。為按量付费後,完成如下配置。
配置項
說明
地域
決定WAF防護節點的位置,影響訪問延遲和資料合規性。
若網站伺服器位於中國內地,請選擇中国内地,其他情況下,請選擇非中国内地。
WAF版本
預設為按量3.0,無需配置。
流量计费保护阈值
為防止大流量攻擊導致 QPS激增併產生高額費用,可設定流量計費保護閾值,以限定 WAF 可處理的峰值 QPS。
當業務在一小時內實際峰值 QPS 超過該閾值時,WAF 執行個體將進入沙箱,不再保證產品服務等級協議(SLA),接入的業務可能隨時出現訪問異常。更多資訊,請參見流量計費保護。
若希望優先保障業務防護能力,請保持預設的最高閾值。
若希望優先控製成本,可適當降低該閾值。
價格參考:除基礎流量費外,當QPS峰值超過1,000 QPS時,超出部分按每小時0.01美元/5 QPS額外計費。例如,QPS峰值為1,500 QPS時,每小時額外費用為1美元。
服务关联角色
為了提供流量存取控制、監控分析等服務,WAF需要訪問您的雲端服務資源,請點擊创建服务关联角色,系統會自動建立角色AliyunServiceRoleForWaf,無需手動對此角色做任何修改。
單擊立即购买並完成下單。
(可選)若您的網站流量和防護功能使用方式在未來至少一個月內相對穩定,且不涉及極低流量或僅短期試用 WAF 的情境,建議購買SeCU資源套件,進一步降低隨用隨付的開銷。
開始使用
開通執行個體後,可以參考以下步驟使用WAF 3.0:
成本最佳化建議
為控制隨用隨付版 WAF 的成本並避免非預期高額費用,可參考以下最佳化措施:
常見問題
為什麼沒有配置WAF,沒有接入資源,還是計費了?
隨用隨付版WAF除請求處理費用外,還收取功能費用(包括WAF執行個體本身的費用等)。因此開通WAF服務後,無論是否有流量到達,立即開始產生費用。
當您不再計劃使用WAF,取消最後一個接入的資源後,控制台也將彈出如下頁面,提示您關閉WAF以停止計費。
SeCU是什嗎?怎麼看每天的WAF消耗?
SeCU簡介:WAF 3.0隨用隨付版的總費用由請求處理費和功能費構成,兩項費用均以SeCU作為計量單元。SeCU的單價為0.01美元,即1 SeCU收費0.01美元。SeCU具體的計算方式,請參見隨用隨付計費說明。
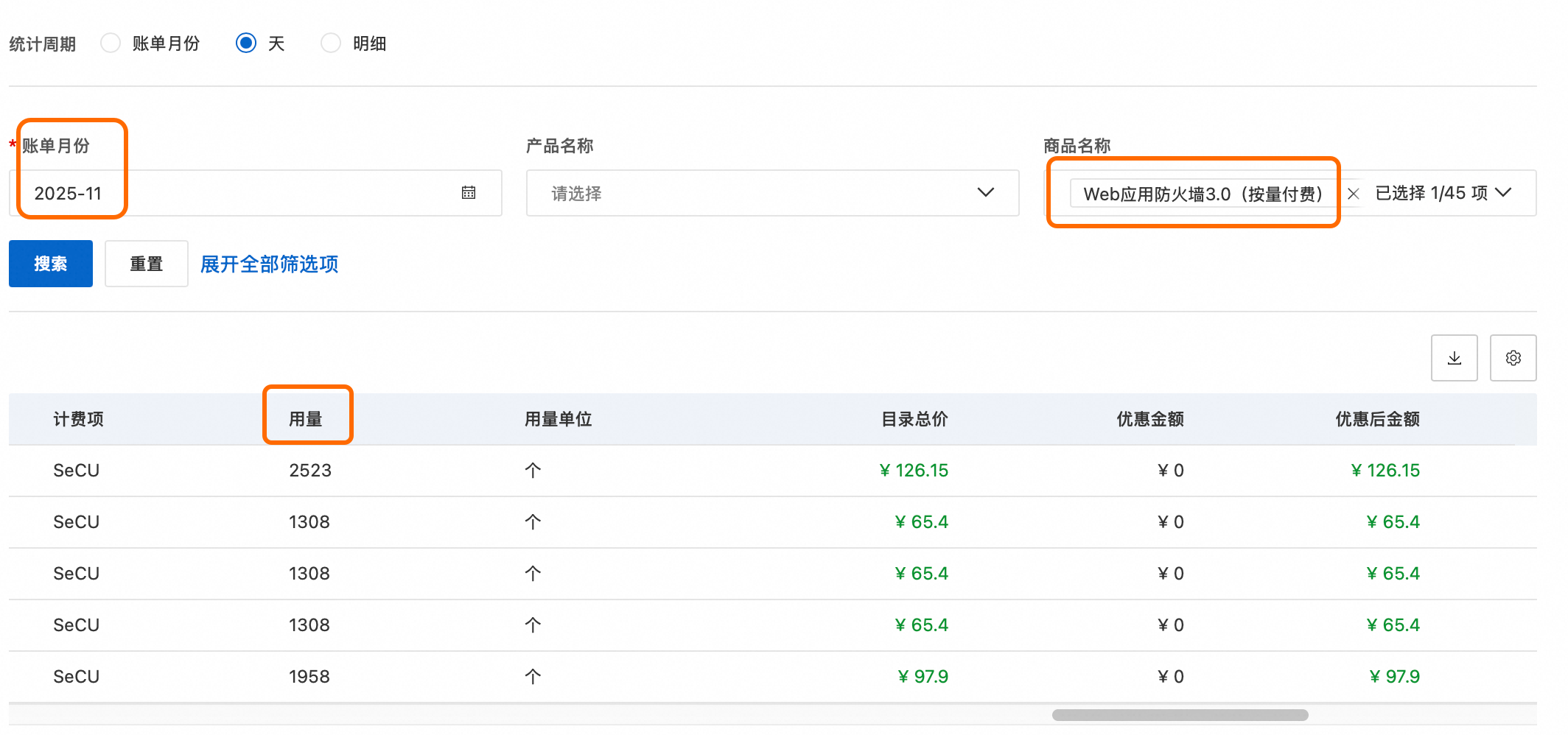
查看消耗:在WAF控制台左側導覽列,選擇,查看近七日每日的SeCU消耗情況,支援單擊查看计费详情查看具體計費項目的消耗量。如需查看七日前的SeCU消耗,請參考賬單詳情(新版)與賬單詳情(舊版)進行查看。
SeCU資源套件是什嗎?如何使用?
SeCU資源套件是WAF 3.0隨用隨付版的成本最佳化方案,在購買隨用隨付WAF執行個體後,可購買SeCU資源套件抵扣隨用隨付WAF產生的總費用。SeCU資源套件是預付費的,購買後無需配置立即生效。詳細資料,請參見SeCU資源套件。
如何關閉WAF停止計費?
若不再計劃使用WAF,希望關閉WAF停止計費時,請參照如下步驟關閉WAF執行個體。
關閉WAF執行個體前,請確認接入到WAF的網站網域名稱DNS已解析回來源站點。
關閉WAF執行個體後,所有網站網域名稱配置資訊將被清空。若仍有請求到達WAF執行個體,將無法被正常轉寄,導致網站無法訪問。
進入總覽頁面,在頂部功能表列,選擇WAF執行個體的資源群組和地區(中国内地、非中国内地)。
若顯示如下介面,請單擊右上方访问控制台。若未顯示如下介面,請跳過此步驟。
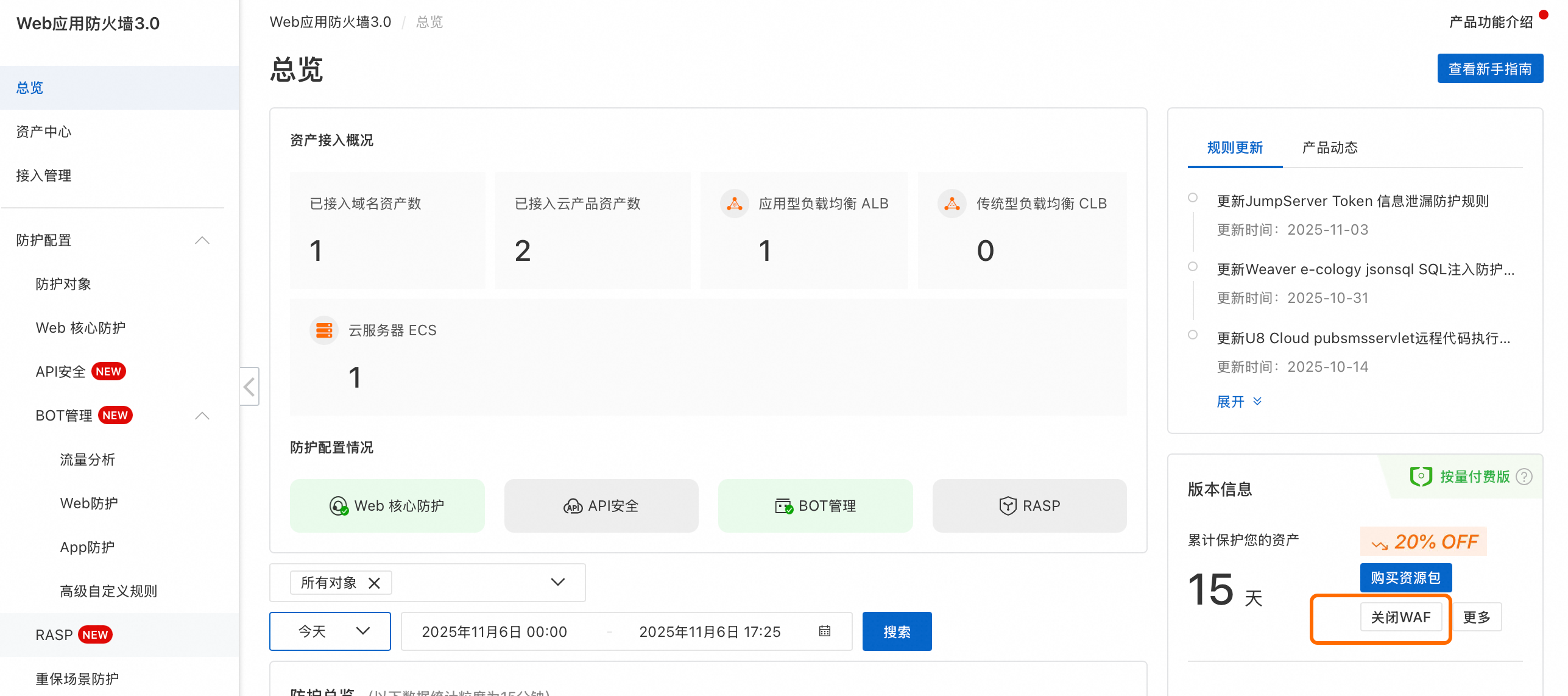
在頁面右側地區單擊關閉WAF,在頁面彈出的提示框中勾選相關內容後單擊确定。
關閉了WAF後為什麼還是繼續在計費?
關閉 WAF 後仍產生費用,可能由以下原因導致:
未正確完成關閉操作:可能僅取消了資產接入或關閉了WAF防護開關,請嚴格按照如何關閉WAF停止計費?的步驟進行關閉操作。
賬單產生存在延遲:隨用隨付版WAF於次日產生賬單,例如,若在10月2日關閉 WAF,則10月3日將產生10月2日的賬單;自10月3日起,不再產生新的賬單。
地區未正確切換:若購買了非中国内地的WAF,需要在總覽頁面頂部功能表列,切換地區後再操作。