使用CNAME接入方式接入Web Application Firewall(Web Application Firewall,簡稱WAF)前,先要將需要防護的網域名稱接入WAF。本文介紹如何將要防護的網域名稱添加到WAF。
前提條件
已購買WAF執行個體,且當前執行個體支援接入的網域名稱數量未超過限制。
說明支援接入的網域名稱數量由WAF的執行個體規格和擴充網域名稱包數量決定。更多資訊,請參見網域名稱擴充包。
如果您的網站部署在中國內地伺服器上,您需要確保該網站的網域名稱已完成ICP(Internet Content Provider)備案,且接入WAF防護期間備案資訊是有效。
說明中國內地WAF執行個體會定期檢查所防護網域名稱備案資訊的有效性。如果網域名稱備案資訊已到期,WAF會按照相關法律法規要求,對網域名稱執行未備案治理,治理方式包括但不限於停止轉寄網站請求、清除備案失效的網域名稱配置等。
如果該網站部署在阿里雲上,您需要在阿里雲進行ICP備案。
如果該網站沒有部署在阿里雲上,您可以聯絡阿里雲或其他雲廠商進行ICP備案。
添加網域名稱
登入Web Application Firewall控制台,在頂部功能表列,選擇WAF執行個體的資源群組和地區(中國內地、非中國內地)。
在左側導覽列,選擇。
在網域名稱列表頁簽,單擊網站接入。
說明進入添加網域名稱頁面後,接入模式預設為Cname接入。
填寫網站資訊,單擊下一步。
配置項
說明
網域名稱
填寫要防護的網域名稱,包括精確網域名稱(例如www.aliyundoc.com)或萬用字元網域名稱(例如*.aliyundoc.com)。僅支援填寫一個網域名稱。
如果您是首次添加該網域名稱,需要驗證是否擁有該網域名稱的歸屬權。通過後,才能添加網域名稱。
說明萬用字元網域名稱不僅可以匹配所有同層級的子網域名稱,還能匹配不同層級的子網域名稱。例如,
*.aliyundoc.com能夠匹配www.aliyundoc.com、example.aliyundoc.com、www.example.aliyundoc.com等多級網域名稱。二級萬用字元網域名稱能夠匹配對應的二級主網域名稱,例如,
*.aliyundoc.com能夠匹配aliyundoc.com。三級萬用字元網域名稱不能匹配對應的三級主網域名稱,例如,
*.example.aliyundoc.com不能匹配example.aliyundoc.com。如果防護對象中同時存在精確網域名稱和能夠匹配該精確網域名稱的萬用字元網域名稱,精確網域名稱的防護規則和轉寄配置優先生效。
防護資源
選擇要使用的防護資源類型。可選項:
公用叢集:預設選擇。
獨享叢集:使用獨享版WAF執行個體時,支援該選項。獨享叢集支援定製化業務需求。更多資訊,請參見獨享叢集最佳實務。
混合雲叢集:使用混合雲接入時,選擇該選型。更多資訊,請參見網站接入(混合雲WAF)。
協議類型
選擇網站使用的協議類型。可選項:
伺服器位址
設定網站的來源站點伺服器位址,支援IP地址格式和網域名稱(如CNAME)格式。完成接入後,WAF將過濾後的訪問請求轉寄到此處設定的伺服器位址。設定說明:
IP地址格式:填寫來源站點的公網IP地址。需要為公網可達的IP地址。
支援填寫多個IP地址,每填寫一個IP地址,按斷行符號進行確認。最多支援添加20個來源站點IP。
說明如果設定了多個IP地址,WAF將在這些地址間自動進行健全狀態檢查和負載平衡。
非中國內地WAF執行個體僅支援配置IPv4地址。中國內地WAF執行個體支援如下配置方式:
同時配置IPv4和IPv6地址
如果開啟IPv4/IPv6回源協議跟隨,則來自IPv6地址的請求將被轉寄到IPv6來源站點,來自IPv4地址的請求將被轉寄到IPv4來源站點。如果不開啟IPv4/IPv6回源協議跟隨,則不做區分,執行混合回源(即IPv4和IPv6請求都有可能回源到IPv4或IPv6來源站點)。
重要使用IPv6回源時,您必須確保網站接入列表中網域名稱的IPv6狀態為已開啟。更多資訊,請參見開啟IPv6防護。
只配置IPv4地址
IPv4和IPv6請求都將通過IPv4回源,即WAF將請求轉寄到您設定的IPv4來源站點地址。
只配置IPv6地址
IPv4和IPv6請求都將通過IPv6回源,即WAF將請求轉寄到您設定的IPv6來源站點地址。
網域名稱(如CNAME)格式:填寫伺服器回源網域名稱,例如Object Storage Service的CNAME等。
使用網域名稱格式時,支援IPv4回源,即WAF會將用戶端請求轉寄到回源網域名稱解析出來的IPv4地址。
重要伺服器回源網域名稱不應和要防護的網站網域名稱相同。
如果您的來源站點伺服器位址為OSS網域名稱,則完成網站接入後,您必須前往OSS控制台中為該OSS網域名稱綁定自訂網域名。具體操作,請參見綁定自訂網域名。
伺服器連接埠
添加網站使用的轉寄服務連接埠。
WAF通過此處添加的連接埠為網站提供流量的接入與轉寄服務,網站網域名稱的業務流量只通過已添加的服務連接埠進行轉寄。對於未添加的連接埠,WAF不會轉寄任何該連接埠的訪問請求流量到來源站點伺服器,因此這些連接埠的啟用不會對來源站點伺服器造成任何安全威脅。
重要網站資訊中設定的協議類型和伺服器連接埠必須是來源站點伺服器提供Web業務的協議和連接埠,不支援連接埠轉換。例如,來源站點伺服器提供Web服務的是80連接埠和HTTP協議,網域名稱配置也必須是一致的,設定其他連接埠則無法正常轉寄。
預設連接埠:
HTTP:80連接埠,選中HTTP協議後預設設定。
HTTPS或HTTP2:443連接埠,選中HTTPS協議後預設設定。
自訂連接埠:在HTTP連接埠輸入框、HTTPS連接埠輸入框輸入連接埠並按斷行符號進行添加。單擊查看可選範圍可以查詢所有支援使用的連接埠。
負載平衡演算法
設定了多個來源站點伺服器位址時,選擇多來源站點伺服器間的負載平衡演算法。可選項:
IP hash:將來自同一個用戶端的請求經過負載平衡轉寄到同一個來源站點,適用於需要保持使用者會話一致性的情境,可能存在負載不均衡的情況。
輪詢(預設):將用戶端的請求依次按序從來源站點列表中選擇來源站點進行回源,適用於多來源站點且對來源站點負載均勻要求較高的情境。
Least time:通過智能DNS解析能力和升級後的Least-time回源演算法,保證業務流量從接入防護節點到轉寄回來源站點伺服器整個鏈路的時延最短。
說明Least time僅在開通智能負載平衡後支援使用。更多資訊,請參見智能負載平衡。
設定生效後,WAF將根據設定的負載平衡演算法向多個來源站點地址分發回源請求,實現負載平衡。
WAF前是否有七層代理(高防/CDN等)
啟用流量標記
設定是否啟用WAF流量標記功能。
流量標記表示WAF在轉寄用戶端請求到來源站點伺服器時,在要求標頭中添加或修改由您指定的自訂欄位,用於標記該請求經過WAF轉寄,記錄該請求的用戶端真實源IP或真實源連接埠。
選中啟用流量標記後,您需要設定標記欄位。
重要請不要填寫標準的HTTP頭部欄位(例如User-Agent等),否則會導致標準頭部欄位內容被自訂的欄位值覆蓋。
如果攻擊者在網域名稱接入WAF前,已擷取來源站點IP資訊,並通過購買其他WAF執行個體,將請求回源到目標來源站點時,您可以啟用流量標記並設定標記欄位。當來源站點接收到請求後,建議對該欄位進行校正。如果存在指定標記欄位,則允許訪問。
標記欄位分為以下類型:
單擊新增標記,可以增加標記欄位。最多支援設定5個標記欄位。
回源逾時配置
資源群組
從資源群組列表中選擇該網域名稱所屬資源群組。
說明您可以使用資源管理服務建立資源群組,根據業務部門、專案等維度對雲資源進行分組管理。更多資訊,請參見建立資源群組。
如果步驟4填寫的網域名稱所對應的泛解析網域名稱已被其他使用者配置,需要按照提示對話方塊提供的記錄類型、網域名稱、記錄值資訊,配置TXT解析記錄。
例如,如果您使用了阿里雲的Alibaba Cloud DNS,可登入Alibaba Cloud DNS控制台,並根據提示對話方塊提供的資訊,配置TXT解析記錄。具體操作,請參見添加解析記錄。
修改DNS解析。
根據頁面提示修改網域名稱的DNS解析,將網站網域名稱解析到WAF進行防護,完成後單擊下一步。更多資訊,請參見修改網域名稱DNS。
添加完成。
根據頁面提示設定允許存取WAF回源IP段,完成後單擊完成,返回網站列表,返回網站接入頁面。更多資訊,請參見允許存取WAF回源IP段。
上傳HTTPS認證
如果您在步驟4添加協議類型時,選擇HTTPS,您必須在WAF控制台上傳與該網站網域名稱關聯的HTTPS認證,且認證必須正確、有效,才能保證WAF正常防護網站的HTTPS協議訪問請求。
上傳的HTTPS認證支援以下方式:
手動上傳認證:您需要提前準備好網站的認證檔案和私密金鑰檔案。
需要準備的認證相關內容如下(上傳時請確保認證有完整的憑證鏈結):
*.crt(公開金鑰檔案)或*.pem(認證檔案)
*.key(私密金鑰檔案)
選擇已有認證:您可以直接從數位憑證管理服務的已有認證中選擇與網域名稱關聯的認證。更多資訊,請參見數位憑證管理服務。
申請新認證。
登入Web Application Firewall控制台,在頂部功能表列,選擇WAF執行個體的資源群組和地區(中國內地、非中國內地)。
在左側導覽列,選擇。
在網域名稱列表中定位到要操作的網域名稱,單擊來源站點資訊列下的
 表徵圖。說明
表徵圖。說明只有在添加網域名稱時選擇了HTTPS協議類型,來源站點資訊列下才會出現
 表徵圖。
表徵圖。在上傳認證(或更新認證)對話方塊,選擇一種上傳方式上傳HTTPS認證。
說明如果您已經上傳過認證,則顯示更新認證對話方塊。更新認證對話方塊中的配置內容和上傳認證對話方塊一致。
手動上傳:填寫認證名稱,並將與網域名稱關聯的認證檔案和私密金鑰檔案的常值內容分別複製粘貼到認證檔案和私密金鑰檔案。
關於認證檔案的說明如下:
如果認證是PEM、CER、CRT格式,您可以使用文字編輯器直接開啟認證檔案並複製其中的常值內容。
如果認證是除PEM、CER、CRT外的其他格式,例如PFX、P7B等,您需要將認證檔案轉換成PEM格式後,才可以使用文字編輯器開啟並複製其中的常值內容。關於認證格式的轉換方法,請參見HTTPS認證轉換成PEM格式。
請確保上傳完整的憑證鏈結。如果網域名稱關聯了多個認證檔案,您需要先將認證檔案中的常值內容拼接合并,再粘貼到認證檔案。
選擇已有認證:從認證列表選擇要上傳的認證。
認證列表羅列了SSL認證服務中已簽發的認證,您可以從列表中選擇與當前網域名稱關聯的認證。單擊Apsara Stack Security-認證服務,可以跳轉到SSL認證管理主控台管理憑證。
申請新認證:單擊立即申請,跳轉到數位憑證管理服務的購買認證頁面為網域名稱快速申請認證。
按照頁面提示為網域名稱配置認證後,已配置認證將預設上傳到WAF。
說明快速申請認證僅支援申請收費型DV認證。如果您需要申請其他類型的認證,請前往SSL認證購買頁面進行操作。更多資訊,請參見購買正式認證。
單擊確定。
後續配置
完成網域名稱接入流程後,網站訪問流量將經過WAF保護,您還需要完善以下配置,才能更好地防護網站安全。
配置類型 | 說明 | 相關文檔 |
網站防護配置 | WAF包含多種防護檢測模組,協助網站應對不同類型的安全威脅,其中規則防護引擎和CC安全防護模組預設開啟,分別用於防禦常見的Web應用攻擊(例如SQL注入、XSS跨站、WebShell上傳等)和CC攻擊,其他防護模組需要您手動開啟並配置具體防護規則。 | |
警示配置 | 通過配置警示規則,您可以使WAF在網站請求流量中檢測到攻擊事件、異常流量時,向您發送警示通知,協助您及時掌握業務的安全狀態。 | |
Log Service配置 | 通過啟用Log Service,您可以使WAF採集並儲存網站業務的日誌資料,供您進行業務查詢與分析。WAFLog Service預設儲存180天內的網站全量日誌,協助您滿足等保合規要求。 |
相關操作
查看和管理已接入的網域名稱
成功添加網域名稱後,您可以在網站接入頁面的網域名稱列表中查看已接入的網域名稱並根據需要執行以下操作:
上傳HTTPS認證:如果網站支援HTTPS協議,請務必確保在WAF上傳正確的認證和私密金鑰,保證正常防護HTTPS業務流量。您可以在來源站點資訊列下單擊
 上傳網域名稱的HTTPS認證和私密金鑰。
上傳網域名稱的HTTPS認證和私密金鑰。更多資訊,請參見上傳HTTPS認證。
開啟IPv6防護:如果網站有IPv6協議業務流量需要防護,您可以在快捷操作列下為網域名稱開啟IPv6開關。
更多資訊,請參見開啟IPv6防護。
開啟Log Service:在快捷操作列下為網域名稱開啟Log Service後,WAFLog Service將採集網站的全量日誌,支援用作查詢分析、儀錶盤展示、設定警示等功能。更多資訊,請參見快速使用WAFLog Service
說明Log Service是WAF提供的增值服務,必須開通後才能使用。更多資訊,請參見步驟一:開通WAFLog Service。
設定防護資源:在快捷操作列下單擊防護資源後的
 ,為網域名稱設定防護資源。
,為網域名稱設定防護資源。支援的防護資源類型包括:
共用叢集共用IP(預設)
共用叢集獨享IP:關於獨享IP的介紹,請參見網域名稱獨享資源套件。
共用叢集全域負載平衡防護:關於全域負載平衡的介紹,請參見智能負載平衡。
獨享叢集:關於獨享叢集的介紹,請參見設定獨享叢集。
查看攻擊監控報表:單擊攻擊監控列下的查看報表,跳轉到安全報表頁面,查看網域名稱的防護報表。更多資訊,請參見WAF安全報表。
設定防護策略:單擊操作列下的防護配置,跳轉到網站防護頁面,設定Web安全、Bot 管理、存取控制/限流防護模組的防護策略。更多資訊,請參見網站防護配置概述。
編輯網域名稱:單擊操作列下的編輯,修改網站資訊,例如協議類型、伺服器位址、伺服器連接埠等。不支援修改網域名稱。
刪除網域名稱:單擊操作列下的刪除,刪除網域名稱。
警告在刪除網域名稱前,請將網域名稱DNS解析回伺服器來源站點IP。否則,在刪除網域名稱後,網域名稱的流量將無法正常轉寄。
網域名稱接入WAF後,需保證網域名稱備案資訊的有效性。為符合相關法律法規要求,WAF會對已接入的網域名稱進行定期輪詢檢查。若ICP備案到期後未及時續期,導致已接入WAF的網域名稱處於未備案狀態,WAF會自動停止網域名稱轉寄。此時,您需要進行如下操作:
完成網域名稱的ICP備案。
訪問網站接入頁面,在網域名稱列表頁簽,單擊已完成ICP備案的網域名稱操作列的再次接入防護。
管理網域名稱ICP備案
網域名稱接入WAF後,需保證網域名稱備案資訊的有效性。WAF會對已接入的網域名稱進行定期輪詢檢查,若ICP備案到期後未及時續期,導致已接入WAF的網域名稱處於未備案狀態,WAF會自動停止網域名稱轉寄。此時,您需要進行如下操作:
完成網域名稱的ICP備案。
訪問網站接入頁面,在網域名稱列表頁簽,單擊已完成ICP備案的網域名稱操作列的再次接入防護。
如何查看已接入網域名稱的DNS狀態?
您可以在接入列表查看網域名稱的DNS狀態,快速識別DNS解析異常的風險網域名稱,並根據控制台提示的異常原因,修改DNS解析設定。
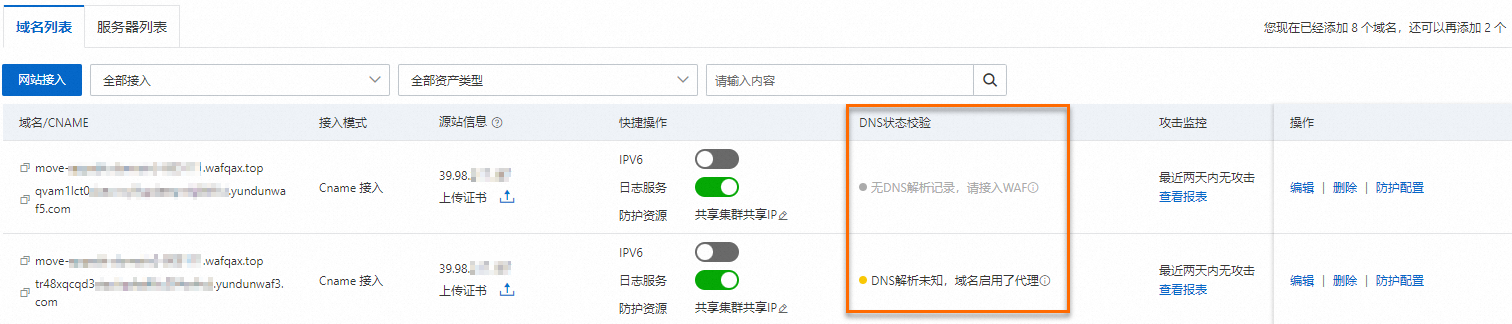
DNS狀態 | 處理操作 |
DNS解析正常 | 網域名稱DNS正常解析到WAF,無需操作。 |
DNS解析異常,使用A記錄接入 | 需要刪除接入網域名稱的A記錄,重新添加CNAME記錄,並將記錄值指向WAF提供的CNAME地址。具體操作,請參見修改網域名稱DNS解析設定。 |
DNS解析異常,使用錯誤的WAF IP | 需要刪除接入網域名稱的A記錄,重新添加CNAME記錄,並將記錄值指向WAF提供的CNAME地址。具體操作,請參見修改網域名稱DNS解析設定。 |
DNS解析異常,使用錯誤的CNAME地址 | 需要將CNAME記錄中的記錄值修改為WAF提供的CNAME地址。具體操作,請參見修改網域名稱DNS解析設定。 |
DNS解析未知,網域名稱啟用了代理 | WAF前啟用了七層代理,需要檢查代理配置的來源站點地址是否為WAF提供的CNAME地址,若確認正確則可以忽略此警示。 |
DNS校正逾時 | 單擊 |
無DNS解析記錄,請接入WAF | 需要添加CNAME記錄,記錄值填寫WAF提供的CNAME地址。具體操作,請參見修改網域名稱DNS解析設定。 |
DNS未解析到WAF,請接入WAF | 需要修改CNAME記錄,記錄值填寫WAF提供的CNAME地址。具體操作,請參見修改網域名稱DNS解析設定。 |
DNS解析正常(網域名稱錯誤啟用代理配置) | 網域名稱DNS正常解析到WAF,但錯誤開啟了前端代理功能,當WAF前不存在CDN、高防等七層代理時,需將WAF前是否有七層代理(高防/CDN等)選擇為否。 |
常見問題
請參見WAF3.0常見問題中的網站接入配置問題。
