如果您的業務部署在阿里雲Serverless環境中,可使用Security Center的Serverless安全檢測功能,確保Serverless架構下資產的安全。該功能支援對Serverless資產進行常見的威脅警示檢測、漏洞掃描、基準風險檢查。本文介紹Security Center如何接入Serverless資產並為Serverless資產提供安全防護功能。
功能介紹
支援防護的資產執行個體
通過託管版與專有版容器叢集ACK、ACK Serverless叢集建立的Elastic Container Instance (ECI)。
通過Container Compute Service (ACS)建立的ECI執行個體資產。
Serverless App Engine (SAE)的ECI執行個體資產。
重要從業務運行穩定性考量,SAE的執行個體規格低於或等於0.5核的執行個體暫不支援接入及掃描。
Platform for AI (PAI)的靈駿智算資源。
支援的安全能力
Security Center為Serverless資產提供以下安全能力。
威脅警示檢測:支援檢測並處理Serverless資產中存在的常見安全威脅,例如發現後門(WebShell)檔案、異常網路連接、進程異常行為等。支援的具體檢查項,請參見CWPP(雲工作負載)安全警示概述。
漏洞掃描:您可以在頁面,單擊已支援漏洞下的數字,前往支援檢測的漏洞列表面板,查看支援檢測的漏洞列表。
對於應用漏洞,僅支援掃描,不支援修複。應用漏洞是針對您伺服器上安裝的軟體進行掃描後發現的風險,需要您根據漏洞詳情中的修複建議,手動對軟體應用進行升級或配置修改,排除安全隱患。
基準風險檢查:支援檢測並處理Serverless資產的存在的基準檢查風險項,例如Kubernetes(ECI) Pod 國際通用安全最佳實務基準檢查的限制以root運行容器和禁止配置具有核心功能的容器等。支援的具體基準檢查內容,請參見基準檢查內容。
Security Center對於接入的Serverless資產根據容器運行時狀態劃分為不同的執行個體類型,對應支援的安全能力有如下區別。
執行個體類型 | 支援的安全能力 |
Elastic Container Instance |
|
RunD容器執行個體 | 威脅警示檢測 |
計費說明
北京時間2024年07月31日及之後,Serverless安全防護功能停止公測,不再支援免費試用Serverless安全防護功能。如果使用者需要使用Serverless安全防護功能,需要通過控制台開通Serverless資產隨用隨付。具體操作,請參見本文2. 開通隨用隨付。
開始計費
開通Serverless資產並完成授權後,Serverless防護採用隨用隨付按月累計的階梯計費模式。
計費方式:已授權的伺服器核心數×實際防護時間長度。其中防護時間長度計算單位為秒,僅在用戶端線上狀態下計算時間。
計費周期:按自然日進行結算,T+1出賬。
價格:按月累計用量執行階梯價格,具體價格如下表。
重要開通首月計費周期為開通當天至當月月底,次月起統一按自然月計算(每月1日至月底)。
月累計使用量(核/秒,按計費周期統計)
價格(美元/核/秒)
費用計算公式(U為一天內使用量,單位為核/秒)
區間1:0~200,000,000
0.000003
0.000003×U(美元)
區間2:200,000,001~1,000,000,000
0.000002
0.000002×(U-200,000,000)+0.000003×200,000,000(美元)
區間3:1,000,000,001~9,999,999,999,999
0.0000015
0.0000015×(U-1,000,000,000)+0.000002×800,000,000+0.000003×200,000,000(美元)
例如,您的帳號下已綁定Security Center用戶端的Serverless資產有20,000核,每天的費用計算方式如下:
在計費周期開始的第一天,按月累計使用量為20,000×86400=1,728,000,000核/秒,其中0~200,000,000核/秒命中區間1,200,000,001~1,000,000,000核/秒命中區間2,1,000,000,001~1,728,000,000核/秒命中區間3。
按照命中區間的單價進行階梯計費,當日計費公式為:0.000003(區間1單價)×200,000,000+0.000002(區間2單價)×800,000,000+0.0000015(區間3單價)×(1,728,000,000-1,000,000,000)=3292(美元)。
每月計費周期第二天至當前計費周期結束(即月底),均按照區間3單價計費。
每天計費公式為:0.0000015(區間3單價)×(20,000×86400)=2592(美元)。
停止計費
在以下情境中,阿里雲會立即停止對綁定授權的Serverless資產的安全檢測,同時停止計費。
停止所有Serverless資產的計費:
在Security Center控制台的總覽頁面的隨用隨付服務地區,關閉Serverless資產對應的開關。
在Security Center控制台的頁面上方,單擊停止使用。
當前阿里雲帳號欠費。
停止指定Serverless資產的計費:
在Security Center控制台的頁面,解除綁定指定資產的綁定授權。具體操作,請參見本文3.2 綁定或解除綁定授權資產。
1. 為待防護的ECI Pod安裝並啟動Security Center用戶端
對於託管版與專有版容器叢集ACK、ACK Serverless叢集、ACS叢集建立的ECI資產,必須完成安裝並啟動Security Center用戶端,才能使用Security Center提供的Serverless安全防護能力。
您可以通過以下方式安裝並啟動ECI Pod的Security Center用戶端。
ACK Serverless叢集的ECI Pod啟動用戶端
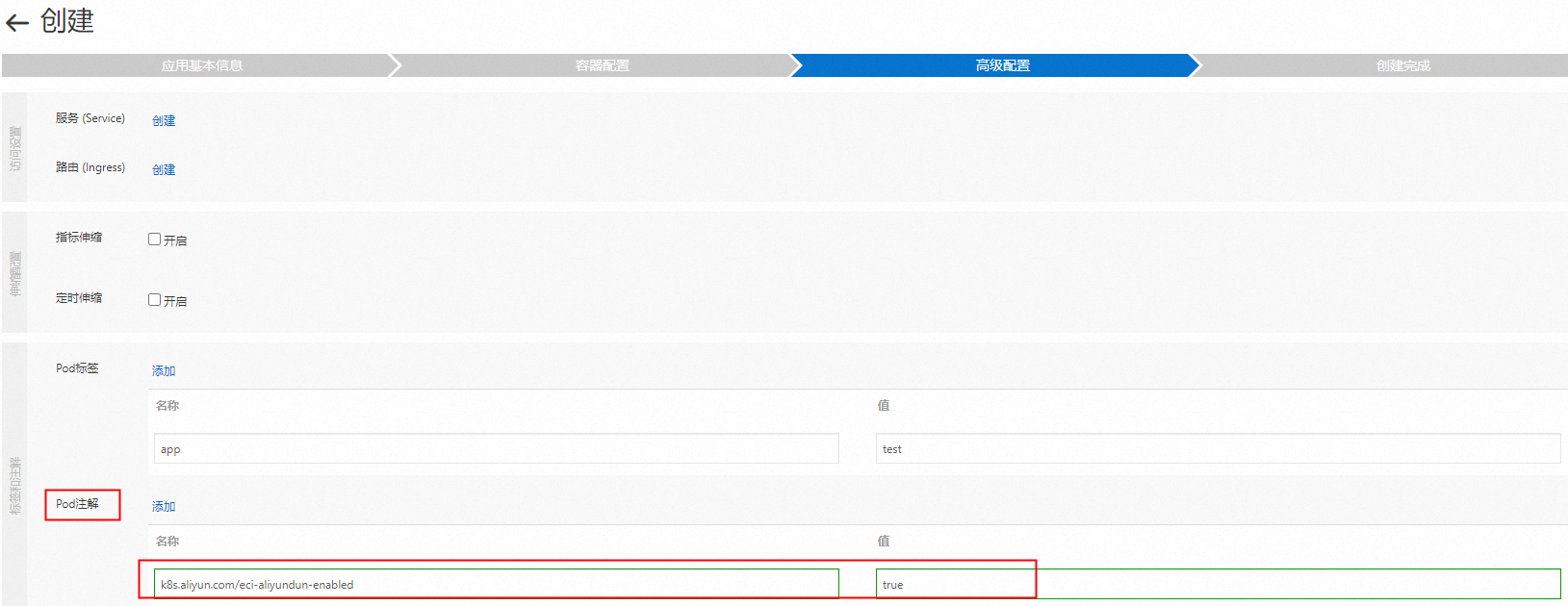
在Container Service管理主控台的目的地組群管理頁面的左側導覽列,選擇,單擊使用YAML建立資源,在YAML模板的spec > template > metadata下增加annotations參數配置,並將其設定為k8s.aliyun.com/eci-aliyundun-enabled: "true"。
建立的YAML模板樣本:
apiVersion: apps/v1 # for versions before 1.8.0 use apps/v1beta1
kind: Deployment
metadata:
name: nginx-deployment-basic
labels:
app: nginx
spec:
replicas: 2
selector:
matchLabels:
app: nginx
template:
metadata:
annotations:
k8s.aliyun.com/eci-aliyundun-enabled: 'true'
labels:
app: nginx
spec:
# nodeSelector:
# env: test-team
containers:
- name: nginx
image: nginx:1.7.9 # replace it with your exactly <image_name:tags>
ports:
- containerPort: 80
resources:
limits:
cpu: "500m"如果使用鏡像建立資源,可在進階配置中添加Pod註解:k8s.aliyun.com/eci-aliyundun-enabled=true。資源建立的具體操作,請參見使用鏡像建立無狀態應用。
託管版與專有版容器叢集ACK的ECI Pod啟動用戶端
託管版與專有版容器叢集ACK的ECI Pod啟動用戶端
登入Container Service管理主控台,進入對應版本的叢集管理頁面,部署ack-virtual-node組件,將Pod調度到ECI上運行。具體操作,請參見將Pod調度到ECI上運行。
在Container Service管理主控台的叢集管理頁面左側導覽列,選擇,然後單擊使用YAML建立資源,在YAML模板的
metadata下增加annotations參數配置,並將其設定為k8s.aliyun.com/eci-aliyundun-enabled: "true",在spec > containers下配置環境變數env,設定容器類型為ECI_CONTAINER_TYPE = sidecar。建立的YAML模板樣本:
apiVersion: v1 kind: Pod metadata: name: test-aegis-alinux2-lifsea-x86 labels: eci: "true" annotations: k8s.aliyun.com/eci-aliyundun-enabled: "true" spec: containers: - name: sidecar image: registry-vpc.cn-shanghai.aliyuncs.com/eci_open/centos:7 command: - /bin/sh - -c args: - sleep inf env: - name: ECI_CONTAINER_TYPE value: sidecar - name: nginx image: registry-vpc.cn-shanghai.aliyuncs.com/eci_open/centos:7 command: - /bin/sh - -c args: - sleep inf
ACS叢集的ECI Pod啟動用戶端
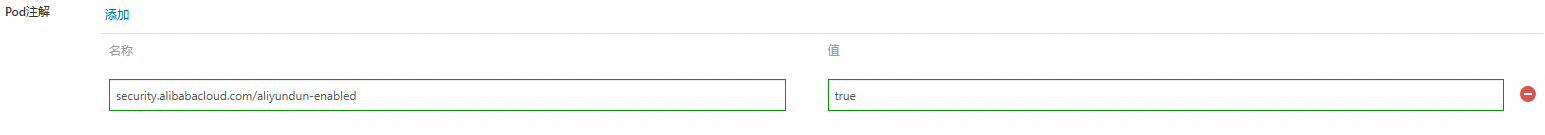
在容器計算服務控制台的目的地組群管理頁面的左側導覽列,選擇,單擊使用YAML建立資源,在YAML模板的spec > template > metadata下增加annotations參數配置,並將其設定為security.alibabacloud.com/aliyundun-enabled: 'true'。具體內容,請參見ACS Pod執行個體概述和使用YAML建立。
YAML模板樣本:
apiVersion: apps/v1 # for versions before 1.8.0 use apps/v1beta1
kind: Deployment
metadata:
name: nginx-deployment-basic
labels:
app: nginx
spec:
replicas: 2
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
alibabacloud.com/compute-class: general-purpose
alibabacloud.com/compute-qos: default
annotations:
security.alibabacloud.com/aliyundun-enabled: 'true'
spec:
# nodeSelector:
# env: test-team
containers:
- name: nginx
image: anolis-registry.cn-zhangjiakou.cr.aliyuncs.com/openanolis/nginx:1.14.1-8.6 # replace it with your exactly <image_name:tags>
ports:
- containerPort: 80
resources:
limits:
cpu: "500m"如果使用鏡像建立資源,可在進階配置中添加Pod註解:security.alibabacloud.com/aliyundun-enabled=true。資源建立的具體操作,請參見使用鏡像建立。
2. 開通隨用隨付
新購開通Serverless資產防護
免費版和申請試用的使用者,可以通過購買Security Center隨用隨付執行個體方式,開通Serverless資產防護能力。
訪問Security Center購買頁並使用您的阿里雲帳號登入。
在購買頁面,選擇購買方式為隨用隨付,單擊Serverless資產的是。
單擊自訂按需綁定,在授權管理對話方塊中,您可選擇全量綁定或自訂綁定,配置目標Serverless資產的防護授權。
重要如果未進行自訂綁定,則預設全量綁定,且開啟新增資產自動綁定。
仔細閱讀並選中Security Center服務合約,單擊立即下單。
Security Center會自動接入當前阿里雲帳號下狀態為運行中的Serverless資產(ECI執行個體和SAE應用),並根據授權管理配置,綁定授權目標Serverless資產。
新增開通Serverless資產防護
已購買Security Center執行個體的付費版(防病毒版、進階版、企業版和旗艦版)的使用者,可以新增開通Serverless資產防護能力。
在左側導覽列,選擇。在控制台左上方,選擇需防護資產所在的地區:中國或全球(不含中國)。
在Serverless資產頁面,單擊立即開通。
您也可以在總覽頁面右側的隨用隨付服務地區,開啟Serverless資產開關。
在確認對話方塊中,您可單擊自訂按需綁定,配置目標Serverless資產的防護授權,單擊確定。
重要如果未進行自訂綁定,按照以下邏輯綁定授權Serverless資產:
如果是首次開通,則預設全量綁定,且開啟新增資產自動綁定。
如果不是首次開通,則預設自動綁定授權給上一次開通該功能已綁定授權的Serverless資產。如果上一次開通該功能綁定授權的ECI執行個體和SAE應用為0,則預設全量綁定,且開啟新增資產自動綁定。
如果當前帳號已欠費,且欠費前已開通Serverless資產功能,使用者結清當前帳號欠費賬單後,預設綁定之前已綁定授權的Serverless資產。
在確認對話方塊中,選中我已閱讀並同意Security Center(隨用隨付)使用者協議,然後單擊立即開通。
3. 管理綁定授權的資產
綁定授權:Security Center用戶端線上且授權綁定的Serverless資產,才能使用Security Center提供的Serverless安全防護能力。
解除綁定授權:對不需要防護的Serverless資產,可以執行解除綁定授權操作。
3.1. 同步最新資產
開通Serverless資產的防護功能後,對於已接入Security Center的資產執行個體和建立的資產執行個體,都需要先同步最新Serverless資產資訊,確認待防護的資產執行個體已安裝啟動Security Center用戶端。
在頁面,單擊同步最新資產。
Security Center會拉取最新的Serverless資產資訊,重新整理資產列表。
說明同步最新資產資訊需要1分鐘時間,請您耐心等待。
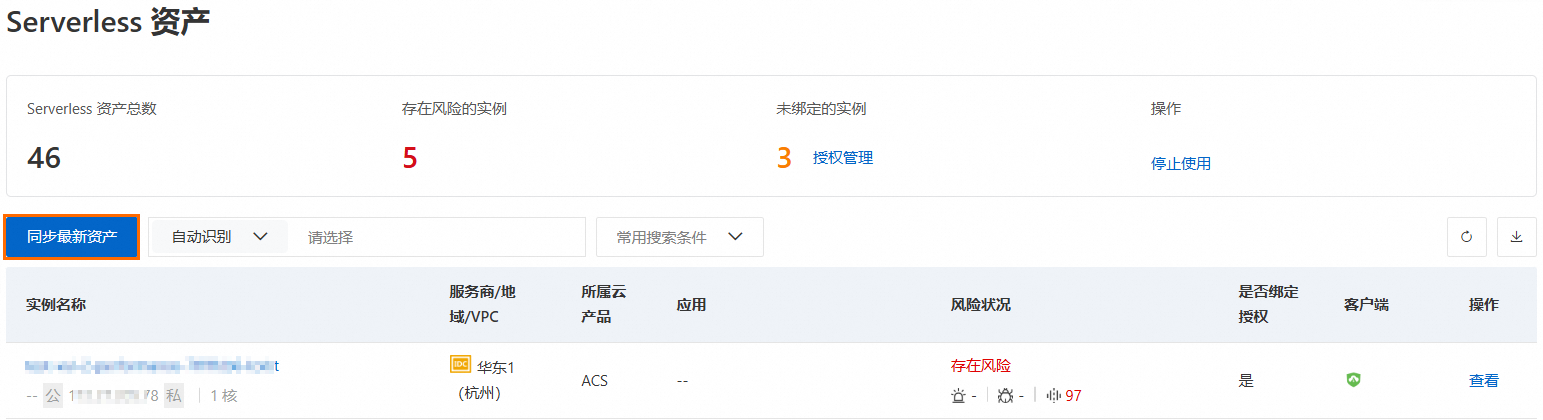
在頁面的資產列表中找到目標Serverless資產,查看用戶端列表徵圖顏色。
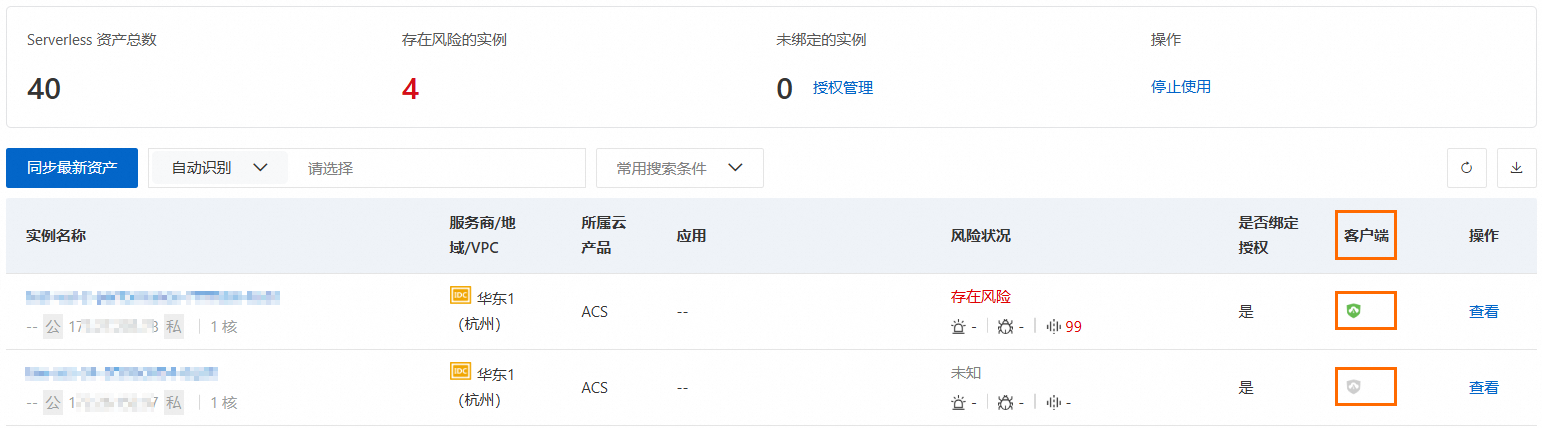
綠色:表示用戶端線上運行中,綁定授權後,可使用Serverless安全防護功能。
灰色:表示用戶端因未安裝或網路不穩定等其他因素不線上。綁定授權後,不支援使用安全防護功能。
請參考上文的1. 為待防護的ECI Pod安裝並啟動Security Center用戶端,檢查並安裝對應資產的Security Center用戶端,完成資產執行個體重啟。
建立或重啟Serverless資產執行個體後,在頁面,單擊同步最新資產,同步最新資產資訊到Security Center。
3.2. 綁定或解除綁定授權資產
為目標資產執行個體啟動Security Center用戶端線上後,您可以為目標資產綁定授權,以使用Serverless安全防護功能。如果您開通功能時選擇了全量綁定,也可以對不需要防護的資產解除綁定授權。
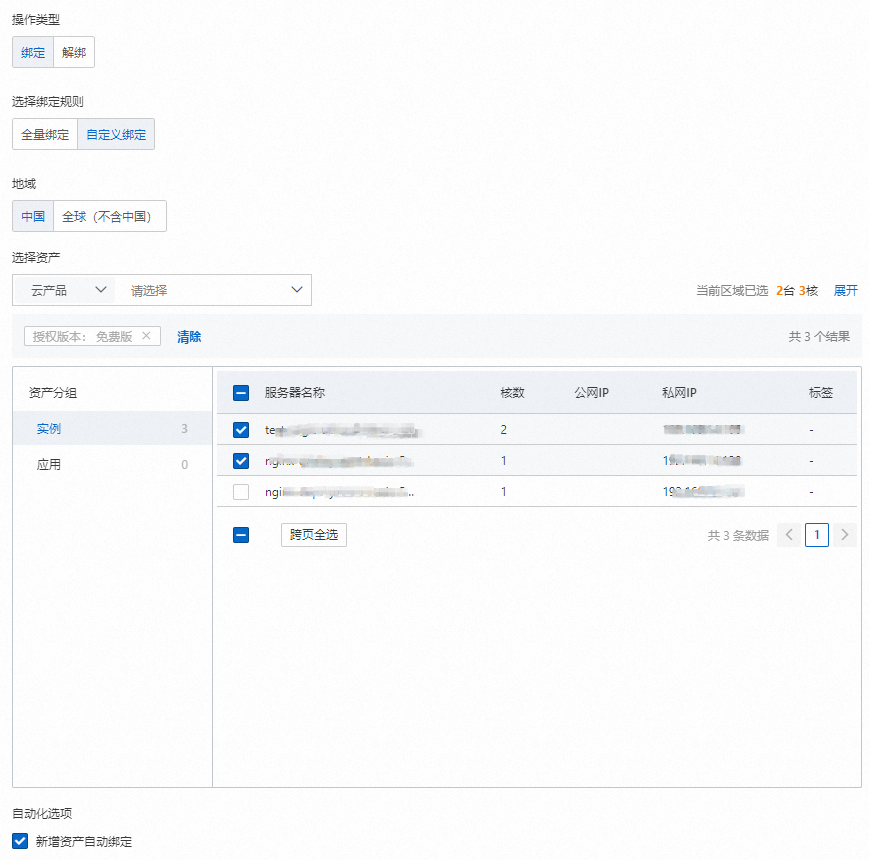
在頁面,單擊資產列表上方未綁定的執行個體下的授權管理。
在授權管理對話方塊中,選擇操作類型(綁定或解除綁定),根據頁面提示選擇目標Serverless資產,然後單擊確定。
如需自動綁定新增的Serverless資產,可選中新增資產自動綁定。
4. 查看並處理安全風險
Serverless資產接入Security Center並完成綁定授權後,Security Center會為該執行個體即時開啟安全威脅警示檢測,漏洞掃描和基準風險檢查會按照漏洞或基準的掃描周期執行檢查。您可以前往漏洞管理或基準風險檢查頁面,查看最新檢查時間。
以下介紹查看Serverless資產安全風險狀態的具體步驟。
在頁面的資產列表中,找到目標資產,如果對應风险状况列顯示存在風險,表示該資產中檢測出了警示、漏洞或基準風險。
單擊目標資產名稱或該資產對應操作列的查看,可查看該資產的詳細風險資訊。
單擊安全警示數、漏洞風險數或配置風險數卡片,可以查看對應的風險檢查項列表。
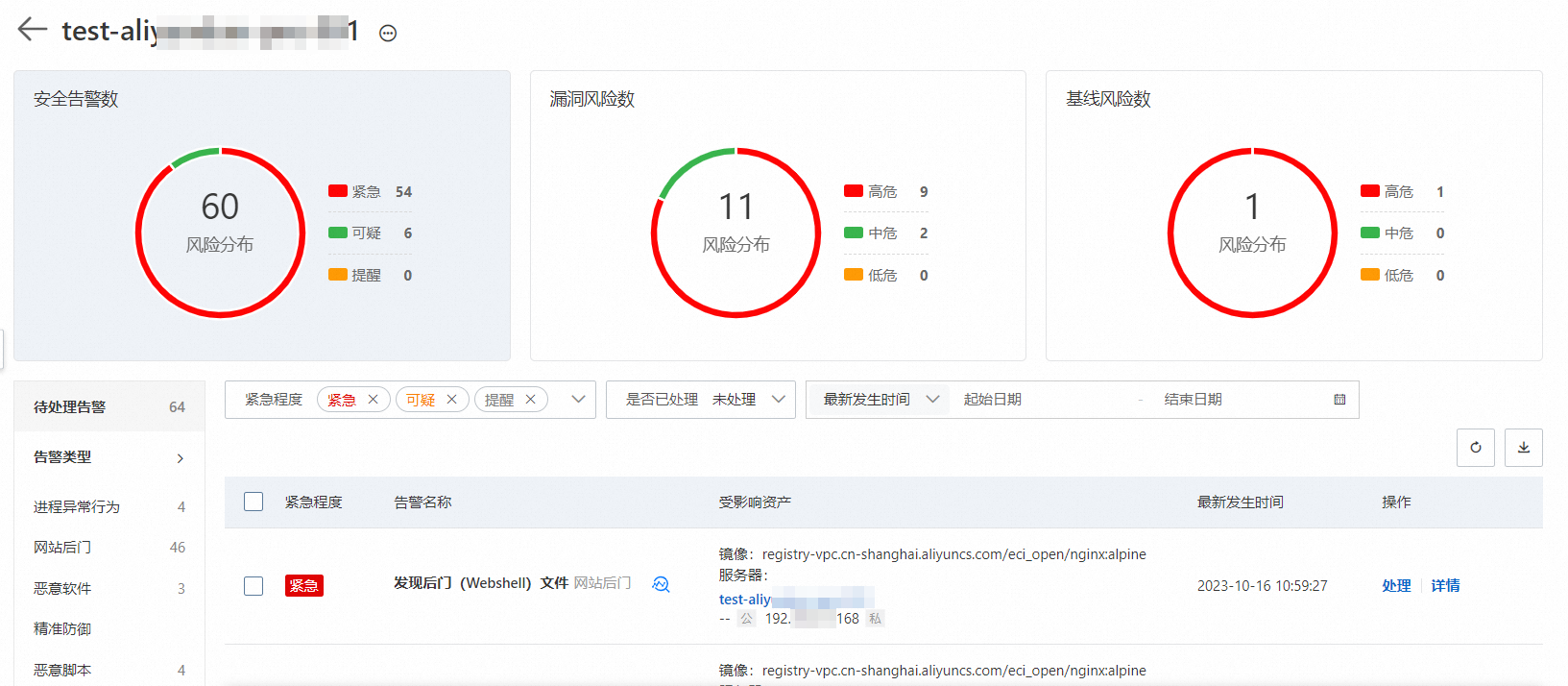
處理安全警示。
單擊目標警示對應操作列的詳情,查看警示的詳細資料,判斷警示是否為真實存在的風險。
判斷完成後,單擊目標警示操作列的處理,如果為真實存在的風險,選擇隔離處理方式;如果無需處理或需忽略本次警示,選擇加白名單、忽略或我已手工處理等處理方式。
處理漏洞風險。
單擊漏洞風險數卡片,查看該資產中檢測出的漏洞。
漏洞為可被駭客利用的薄弱點,建議您及時處理已檢測出的漏洞。應用漏洞不支援一鍵修複,建議您根據漏洞詳情中的說明自行修複漏洞。具體操作,請參見查看和處理漏洞。
處理基準風險。
單擊配置風險數卡片,查看該資產中檢測出的基準風險。單擊目標風險操作列的詳情,查看風險詳情和加固建議,並判斷是否需要處理該基準風險,並根據判斷結果處理該風險,或對該風險加白名單。
Security Center僅支援修複部分基準檢查項風險問題,如果風險詳情頁面的風險處理列表顯示修複按鈕,表示該風險項支援在Security Center修複,您可以在Security Center直接修複基準風險問題。