記憶體馬是一種僅在記憶體中執行,不寫入硬碟的惡意程式,其能夠隱蔽地進行攻擊,同時躲避常規的病毒檢測手段。應用防護的RASP(Runtime Application Self-Protection)技術通過分析記憶體資料可以即時檢測記憶體馬,並支援對記憶體馬注入和記憶體馬執行過程進行攔截。本文介紹如何使用記憶體馬防禦功能。
前提條件
已將Java應用接入應用防護,且應用執行個體狀態為已授權。具體操作,請參見接入應用防護。
記憶體馬檢測和攔截邏輯
記憶體馬防禦功能支援檢測應用分組已授權執行個體中是否存在記憶體馬、記憶體馬注入和執行調用等行為。該功能通過以下檢測引擎實現防禦能力:
記憶體馬檢測:通過掃描記憶體分析是否存在惡意代碼,協助使用者發現隱藏在記憶體中的威脅,並在控制台展示記憶體馬檢測警示。通過為應用分組開啟記憶體馬檢測開關,可以啟用該引擎。
記憶體馬注入:即時監測與攔截記憶體馬攻擊的動態,包括檢測記憶體馬的注入和執行行為。當應用分組的檢測類型包括記憶體馬注入時,可以啟用該檢測引擎。應用分組的防護模式設為監控時,引擎將僅對檢測到的威脅上報警示而不執行阻斷。而在防護模式為防護時,該引擎將主動阻斷可疑的調用行為,並提供相應的警示資訊。面對種類繁多的中介軟體,該引擎提供了兩種記憶體馬攻擊攔截方式。
記憶體馬注入過程攔截:RASP通過監控敏感API函數,能夠即時監控攻擊者通過執行運算式、還原序列化等方式注入記憶體馬的行為,在攻擊執行注入記憶體馬過程中即可進行阻斷,記憶體馬無法注入應用上下文。
記憶體馬執行攔截:當記憶體馬成功注入並嘗試在系統記憶體中運行時,RASP通過結合深度學習與行為識別技術來檢測程式的執行過程。該技術通過與已知惡意特徵資料庫進行對比,能夠準確識別並阻止記憶體馬的啟用和執行,同時確保不干擾正常的業務操作。因此,即便記憶體馬被植入系統,攻擊者也無法通過它達成惡意目的。
查看並處理記憶體馬警示
應用防護功能預設為所有應用分組開啟記憶體馬檢測。將應用接入應用防護後,您可以參考下述步驟查看並處理記憶體馬警示。
登入Security Center控制台。在控制台左上方,選擇需防護資產所在的地區:中國或全球(不含中國)。
在左側導覽列,選擇。
在應用防護頁面的記憶體馬防禦頁簽下,設定需查看的應用分組和時間範圍。
查看記憶體馬警示趨勢、内存马类型分布和記憶體馬警示列表。
記憶體馬檢測警示:展示記憶體馬檢測引擎檢測出的靜態記憶體馬檔案。以下是記憶體馬檢測警示處理狀態的說明:
未處理:表示記憶體馬檢測引擎已檢測到該記憶體馬檔案,您需要儘快手動處理該警示。
自動處理已阻斷:表示記憶體馬注入引擎已檢測到導致警示的記憶體馬檔案的運行,並阻斷了對應記憶體馬的運行行為。RASP可精準防禦該記憶體馬,後續該記憶體馬的運行行為也會被阻斷,您可以稍後再通過重啟應用清除記憶體馬檔案。
未處理已監控:表示記憶體馬注入引擎已檢測到導致警示的記憶體馬檔案的運行,根據應用分組的防護模式設定未阻斷對應記憶體馬的運行行為。您可以通過一鍵開啟防護,為對應的應用分組開啟記憶體馬防護能力。
下述內容是對警示活躍和失活狀態的說明:
活躍:觸發警示的應用執行個體狀態為線上。
失活:觸發警示的應用執行個體狀態為離線。
記憶體馬注入警示:展示記憶體馬注入模型檢測出的警示事件。
單擊目標警示操作列的詳情,查看檢測出的記憶體馬警示的詳細資料和警示分析,分析是否需要處理記憶體馬警示。
在詳細資料頁簽,如需查看記憶體中啟動並執行Java程式的原始碼,您需要開啟反編譯Java文件開關。關閉該開關後,Security Center不會展示反編譯代碼。
警示分析頁簽通過使用AI大模型為您提供了記憶體中啟動並執行代碼的解析結果,以及被認定存在記憶體馬的確切依據等資訊,使您更精準地評估當前檢測到的記憶體馬是否確實構成實質性威脅,從而提升您的安全判斷力與響應效率。
重要您需要開啟反編譯Java文件開關,才能查看警示分析頁簽中的內容。警示分析功能會分析反編譯後的Java檔案。
處理記憶體馬警示。
手動處理記憶體馬:在業務低峰期,重啟應用清除記憶體馬。處理完成後,在控制台將處理方式設定為标记已处理。
一鍵開啟防護:將警示伺服器所在的應用分組的防護模式切換為防護。切換為防護後,後續該應用分組中檢測出的記憶體馬注入或執行行為均會被自動攔截。
忽略:如果無需處理當前警示,您可以在控制台將處理方式設定為忽略。
加白名單:前往攻击告警頁簽,單擊目標記憶體馬注入警示操作列的處理,將該警示加入白名單。具體操作,請參見將警示加入白名單。
說明記憶體馬檢測警示不支援加入白名單。
開啟或關閉記憶體馬防禦
應用防護以應用分組為單位控制記憶體馬防禦的開啟或關閉。您可以參考下文開啟或關閉應用分組的記憶體馬防禦。
登入Security Center控制台。在控制台左上方,選擇需防護資產所在的地區:中國或全球(不含中國)。
在左側導覽列,選擇。
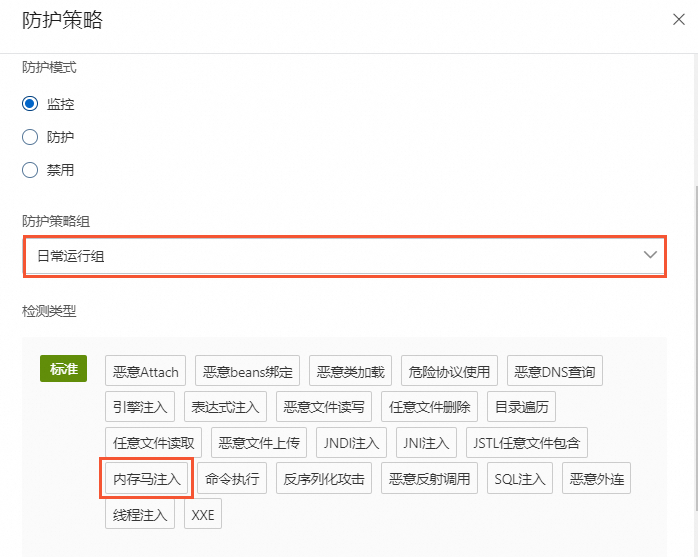
在應用防護頁面的应用配置頁簽,單擊目標應用分組操作列的防護策略。
在防護策略面板的防護策略頁簽下,選擇或取消選擇檢測類型包含記憶體馬注入的防護策略組。
選擇包含檢測類型記憶體馬注入的防護策略後,會開啟記憶體馬注入引擎的檢測。防護模式為監控時,只上報警示不執行阻斷操作。防護模式為防護時,上報警示並阻斷記憶體馬注入或調用行為。
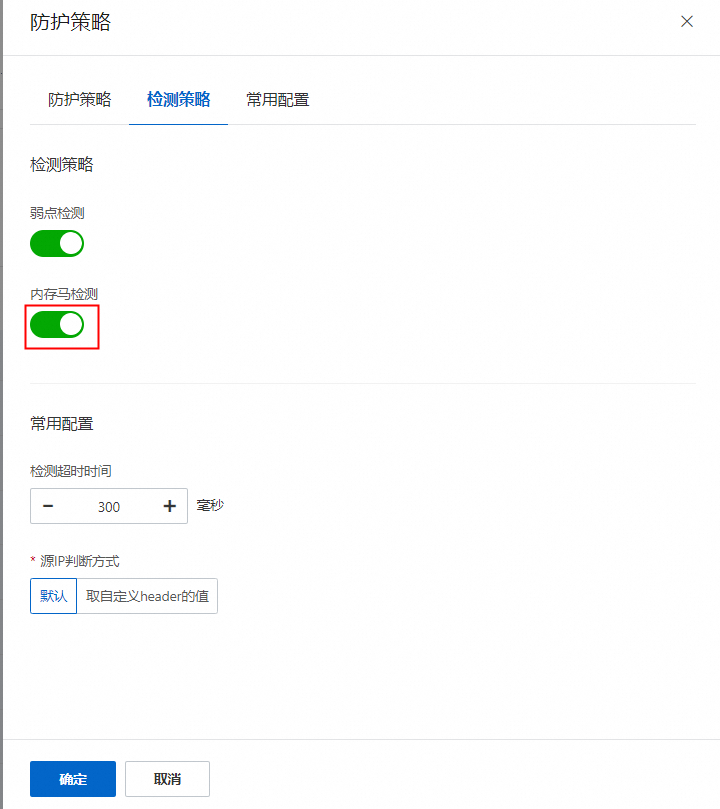
在防護策略面板的檢測策略頁簽下,開啟或關閉內存馬檢測開關,並單擊確定。
開啟記憶體馬檢測開關後,會為該應用分組開啟記憶體馬檢測。