雲上資產的錯誤配置(如儲存桶公用讀取)或安全性漏洞,可能引發資料泄露、服務中斷等嚴重安全事件。雲安全態勢管理(CSPM)通過自動化安全檢查,持續發現並管理阿里雲、多雲環境及自建Kubernetes(K8s)叢集中的配置風險,並提供修複建議,以提升資產的整體安全性與合規性。本文旨在介紹如何將各類雲資產接入Security Center,以啟用配置風險檢查功能。
適用範圍
支援的檢查項:
提供部分免費基礎配置檢查項。
說明僅檢測、驗證免費,修複仍需開通付費服務。
啟用全部雲產品配置風險檢查項,需購買雲安全態勢管理付費服務(訂用帳戶或隨用隨付)。更多說明,請參見功能計費詳解。
支援的雲平台:
阿里雲
第三方雲平台:AWS、Azure、華為雲、騰訊雲、火山雲。
容器環境:自建Kubernetes叢集。
查看支援檢查的雲產品
目前,Security Center支援接入阿里雲和第三方雲平台中的資產進行雲安全態勢管理,可以在Security Center控制台查看支援接入和檢查的阿里雲產品、第三方雲平台及其雲產品。
訪問Security Center控制台-風險治理-雲安全態勢管理,在頁面左側頂部,選擇需防護資產所在的地區:中國內地或非中國內地。
在雲產品配置風險頁簽的檢查項列表上方,選擇雲產品,單擊阿里云或第三方雲平台(例如腾讯云、AWS),可以分別查看Security Center目前支援接入的雲產品列表。
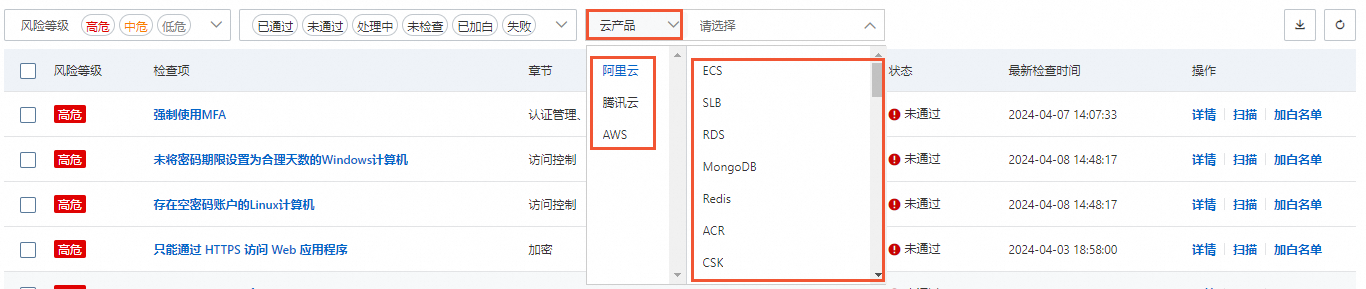
接入阿里雲產品
Security Center會自動同步當前阿里雲帳號下的雲產品,無需手動操作。
接入第三方雲平台資產
雲安全態勢管理提供跨雲平台資產的配置檢查能力,將AWS、Azure、華為雲、騰訊雲、火山雲等第三方雲產品接入Security Center,即可實現統一的雲產品配置掃描與風險管理。配置步驟參考如下。
詳細參考文檔,請參見三方雲配置參考文檔。
步驟一:在第三方雲平台建立訪問憑證
AWS
建立IAM使用者並授權:登入AWS IAM控制台,建立一個新的IAM使用者。為該使用者附加
ReadOnlyAccess和IAMReadOnlyAccess兩個系統策略。建立並記錄存取金鑰:為新建立的使用者產生一個存取金鑰(Access Key),並妥善記錄Access Key ID和Secret Access Key。
華為雲
建立使用者組並授權:登入華為雲控制台,進入使用者組頁面,建立一個新的使用者組。為該使用者組附加
Tenant Guest和IAM ReadOnlyAccess兩個系統策略。建立使用者並記錄存取金鑰:建立一個新的IAM使用者,並將其加入上一步建立的使用者組。為該使用者建立一個存取金鑰,並妥善記錄Access Key Id和Secret Access Key。
腾讯云
建立子帳號並授權:登入騰訊雲控制台,進入使用者列表頁面,建立一個新的子帳號。為該子帳號關聯
CloudResourceReadOnlyAccess和QcloudCamReadOnlyAccess兩個系統策略。建立並記錄API密鑰:在子帳號詳情的API密鑰管理頁面,建立一個新的API密鑰,並妥善記錄SecretId和SecretKey。
Azure
註冊應用程式:登入Azure控制台,進入應用註冊服務,註冊一個新的應用程式。記錄其應用程式(用戶端)ID和目錄(租戶)ID。
建立用戶端密碼:在新註冊的應用中,進入認證和密碼頁面,建立一個新的用戶端密碼,並妥善記錄其值。
分配角色:進入訂閱服務,選擇您的訂閱,然後在“存取控制”中為新註冊的應用程式指派讀者 (Reader) 角色。
火山雲
建立子帳號並授權:登入火山引擎控制台,進入使用者頁面,建立一個新的子帳號。為該使用者附加
IAMReadOnlyAccess和ECSReadOnlyAccess兩個系統策略。建立並記錄存取金鑰:在建立使用者時,確保啟用了編程訪問。建立完成後,妥善記錄Access Key ID和Secret Access Key。
步驟二:在Security Center完成接入
訪問Security Center控制台-系統設定-功能設定,在頁面左側頂部,選擇需防護資產所在的地區:中國內地或非中國內地。
在頁簽,單擊新增授权。
在接入云外资产面板,選擇配置方案並根據提示將上一步擷取的訪問憑證填入相應輸入框中。
配置審計日誌(可選):如果需要使用雲安全態勢管理(CSM)的日誌審計功能,還需配置相關內容。
說明三方需提供對應的Kafka服務,目前僅腾讯云和AWS支援配置審計日誌。
接入K8s自建叢集
步驟一:接入叢集
此步驟將在叢集中建立必要的認證和服務賬戶,以便Security CenterAgent可以安全地與叢集通訊。
在頁面,單擊右上方的策略管理,然後在策略管理面板的容器叢集接入配置頁簽,單擊自建集群接入。
說明如果當前執行個體版本為旗艦版,也可以在頁面,單擊自建集群接入。
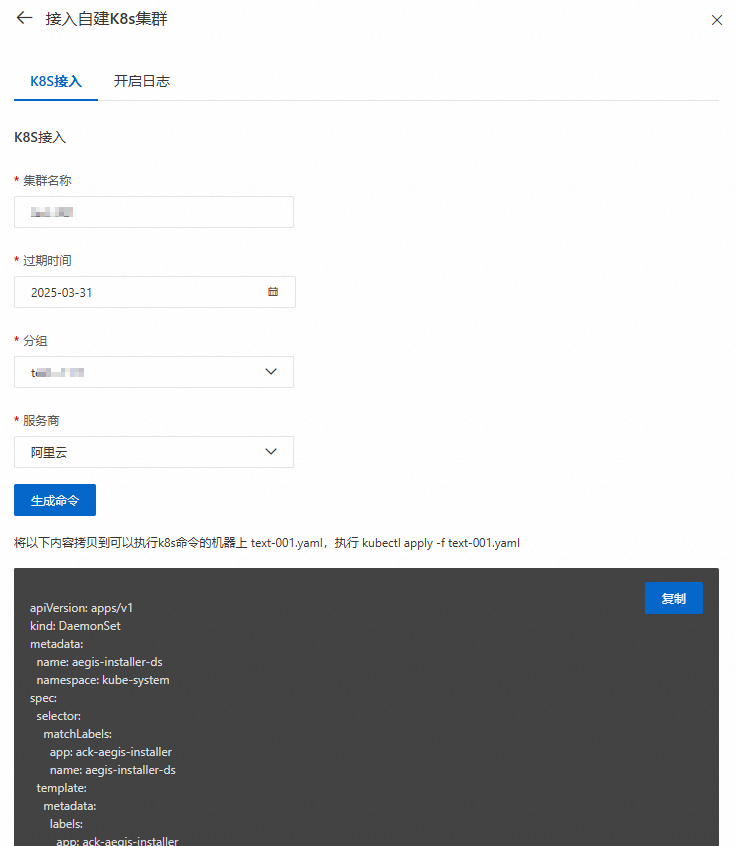
在接入自建K8s集群面板完成K8s接入配置後,單擊產生命令。
登入叢集所在伺服器,建立
text-001.yaml檔案,將產生的命令拷貝到該檔案中儲存。執行以下命令:
# 應用接入配置 kubectl apply -f text-001.yaml
步驟二:安裝檢查組件
此步驟將在叢集中部署檢查組件Agent,用於執行配置掃描任務。
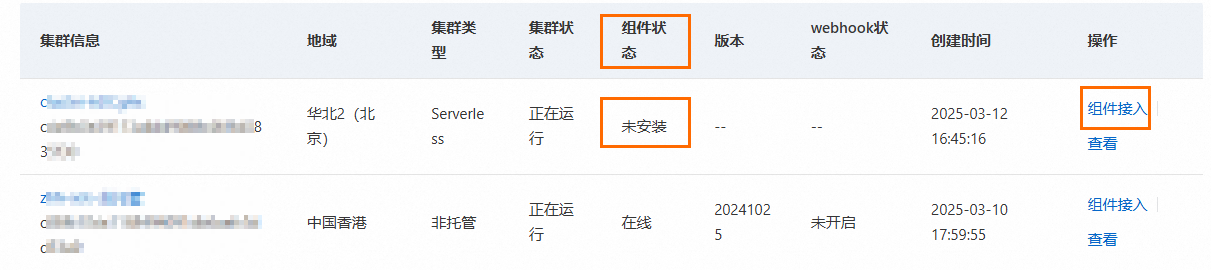
返回容器叢集接入配置頁簽的叢集列表中,找到剛剛接入的叢集,其組件狀態為未安裝。單擊操作列的組件接入。
在掃描組件接入面板,複製產生的命令,然後登入叢集所在伺服器,將產生的命令拷貝到
deploy.yaml檔案中儲存。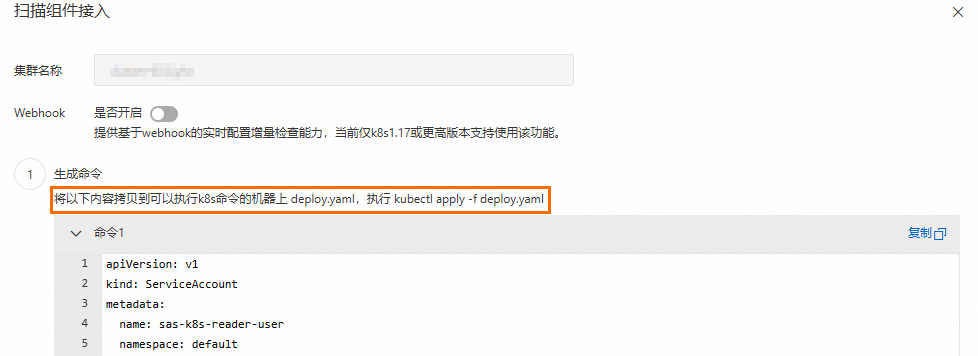
執行以下命令:
# 部署檢查組件 kubectl apply -f deploy.yaml(可選)啟用Webhook進行增量檢查:如果希望在叢集資源(如Pod)發生變更時自動觸發增量檢查,可以啟用Webhook功能。
警告開啟Webhook功能,目前僅支援Pod的增量檢查。若Webhook功能未正確配置或發生異常,可能會影響叢集資源的建立。
在掃描組件接入面板,複製Webhook相關的命令後,登入叢集所在伺服器,將產生的命令拷貝到
webhook.yaml檔案中儲存。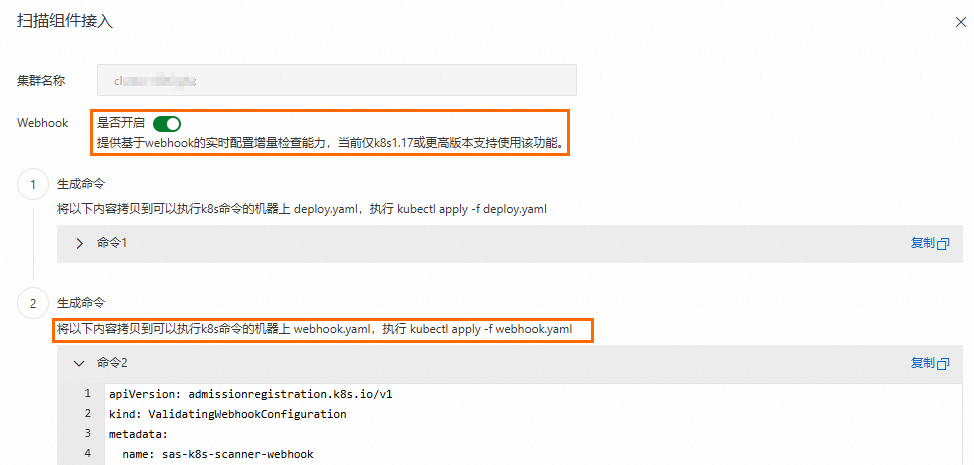
執行以下命令部署組件:
# 部署檢查組件 kubectl apply -f webhook.yaml
步驟三:驗證安裝
在叢集伺服器上,執行以下命令,檢查Agent Pod是否正常運行。
說明預期結果是Agent相關的Pod狀態為
Running。# 請將 <agent-namespace> 替換為實際部署 Agent 的命名空間 kubectl get pods -n <agent-namespace>在Security Center控制台的容器叢集接入配置列表中,在叢集列表中查看組件狀態為線上,表示組件安裝成功。
同步最新資產
若配置接入時設定了自動同步(如多雲配置開啟雲產品同步頻率),系統將自動同步新增雲產品或產品配置更新。
也可以在Security Center控制台手動在雲產品或容器叢集接入配置,單擊同步最新资产。
計費說明
資產接入:將雲產品資產接入Security Center的操作本身不產生費用。
配置檢查:雲安全態勢管理付費功能的計量單位時授權數。對一個資產執行個體成功執行一次操作(掃描、驗證或修複)時,消耗一個授權數。更多說明,請參見功能計費詳解。
配額與限制
功能限制:日誌審計功能目前僅支援騰訊雲和AWS上。
K8s接入限制:
版本限制:
訂用帳戶服務:購買旗艦版版本服務或單獨購買雲安全態勢管理增值服務。
隨用隨付服務:開通主機及容器安全或雲安全態勢管理後付費功能。
地區限制:
自建K8s叢集網路類型為VPC時,僅支援接入華東1(杭州)、華北2(北京)、華東2(上海)、華南1(深圳)和中國香港地區。
自建K8s叢集網路類型為公網時,無地區限制。