Security Center通過即時檢測GitHub平台公開原始碼中存在的阿里雲帳號或RAM使用者的存取金鑰AccessKey(以下簡稱:AK)資訊,可識別出AK是否泄露,並提供相應的警示,建議您及時查看並處理外泄的AK事件。本文介紹AK泄露檢測的原理及如何處理泄露事件。
功能原理
Security CenterAK泄露檢測功能支援即時檢測GitHub平台公開原始碼(多為企業員工私自上傳並不小心公開)中是否含有AK資訊,在發現AK泄露時向您發送通知,協助您及時探索資料外泄的風險。
目前Security Center僅支援檢測Github平台中的AK泄露,不支援其他平台。
企業員工如果將不可公開的公司源碼上傳至GitHub等平台,可能會導致阿里雲帳號的AK資訊在外網環境泄露,AK泄露可能會讓您失去該帳號下所有資源的控制權。
只有AccessKey ID和AccessKey Secret(以下簡稱SK)同時泄露時,該存取金鑰才可以被第三方利用。Security Center在檢測到阿里雲帳號或RAM使用者的AK資訊泄露時,會根據SK是否有效,採用不同的方式向對應的阿里雲帳號發送通知,支援的通知方式如下:
AK泄露檢測頁面警示:只要檢測到AK泄露,無論SK是否有效,都會提供警示。
控制台彈框提示:在檢測到泄露的SK資訊有效時,您訪問阿里雲控制台首頁或多數雲產品控制台時會彈框提示。
根據通知設定發送警示通知:只有檢測到泄露的SK資訊有效時,才會根據您設定的通知方式(站內信、郵件)發送通知。

設定AK泄露警示通知
Security Center支援對AK泄露情報提供警示通知,通知的方式包括郵件、站內信。
Security Center預設開啟AK泄露警示通知。您也可以根據需要,在Security Center控制台通知設定頁面簡訊/郵件/站內信郵件/站內信頁簽中,自訂訪問金鑰洩漏資訊的通知方式。設定後,您只能通過已選中的方式收到通知。具體操作,請參見通知設定。
由於AK泄露風險安全風險高,為了能及時接收到通知,建議您選中所有通知方式。
預設情況下,僅帳號連絡人會收到通知。需要其他連絡人收到通知時,您可以參考下述步驟新增連絡人...。
在基本接收管理頁面地區,修改訊息接收人。

修改此處的訊息接收人後,會對Security Center其他通知項同時生效。同時也會對DDoS和Web Application Firewall等產品的訊息通知項生效。
處理AK泄露事件
收到AK泄露警示通知後,表示您阿里雲帳號或RAM使用者的AK和SK資訊已外泄。請第一時間處理AK泄露事件。處理完成後,請在Security Center控制台對該AK警示事件進行處理。具體操作如下:
在左側導覽列,選擇。
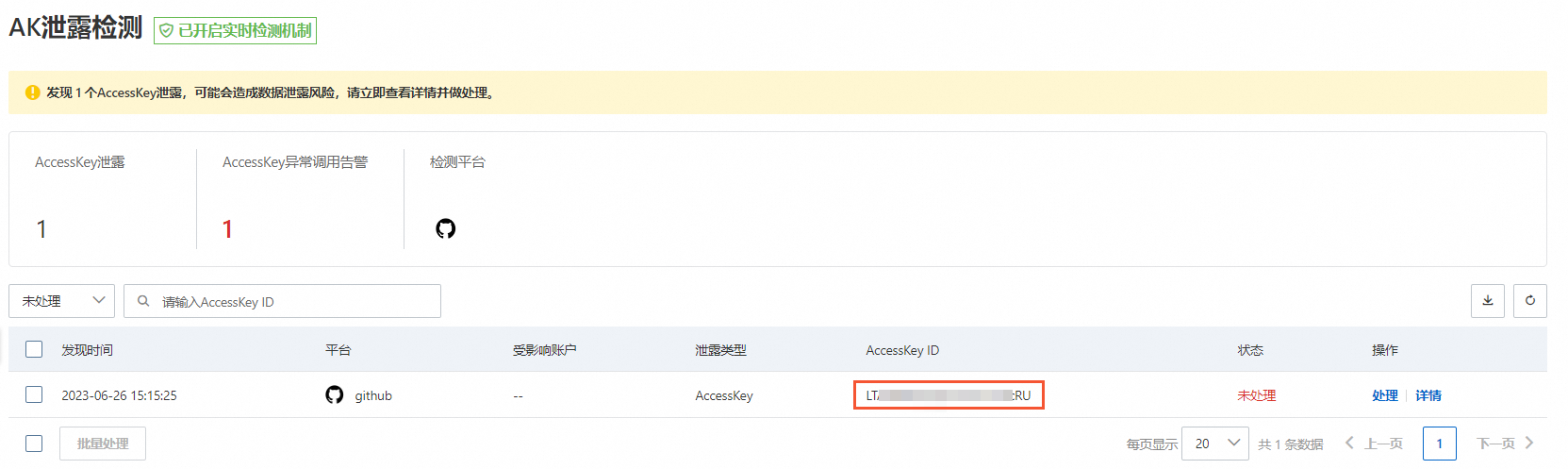
在AK洩露檢測頁面,查看並處理AK泄露事件。
查看AccessKey泄露檢測詳情
您可以在AK泄露檢測列表中,選擇一個檢測記錄,單擊其操作列的詳情,查看詳細的情報資訊。單擊檔案詳情地區的使用者名稱、檔案名稱、倉庫名等連結,可以跳轉GitHub對應頁面,查看AK資訊泄露的源頭。
處理檢測出的AK泄露事件
Security Center不支援自動處理或一鍵處理AK泄露事件,您需要手動處理完AK泄露事件後,再前往Security Center控制台標註AK泄露處理狀態。手動處理AK泄露事件的方法如下:
聯絡相關人員刪除或隱藏GitHub相關內容。
在確保核心業務不受影響的前提下,即不再需要使用該AccessKey通過API訪問阿里雲資源時,刪除或禁用已泄露的AccessKey,啟用新的AccessKey。具體操作,請參見刪除RAM使用者的AccessKey和禁用RAM使用者的AccessKey。
手動處理完AK泄露事件後,您需要在AK泄露檢測列表中定位到具體事件,單擊其操作列的處理,選擇AK事件處理方式,並單擊立即處理。
處理方式包含手動刪除、手動禁用 AK、加白名單三種。
說明您針對該AK泄露已處理了所有的AK泄露來源、並手動確認處理方式後,該AK泄露事件的狀態會變為已處理。
如果選擇加入白名單處理,該檢測項處理狀態變為白名單,並進入已處理列表。
需要恢複檢測時,您可從已處理列表進入AK泄露詳情頁,進行取消白名單操作。
查看AK調用記錄
通過查看AK調用記錄,可以確定在AK泄露後AK是否被攻擊者利用過,以瞭解AK泄露的影響範圍。下文介紹通過Action Trail服務按照時間軸查看AK呼叫事件的操作步驟。
如何需要從AK訪問的雲產品角度查看調用記錄,您可以使用Action Trail的AccessKey審計功能。具體操作,請參見查詢AccessKey日誌。
在Security Center控制台AK洩露檢測頁面,擷取需要查看的AccessKey ID。
在左側導覽列,選擇。
在頂部導覽列選擇您想查詢事件的地區。
選擇類型為AccessKey ID,輸入待查詢的AccessKey ID,並選取查詢時間段。
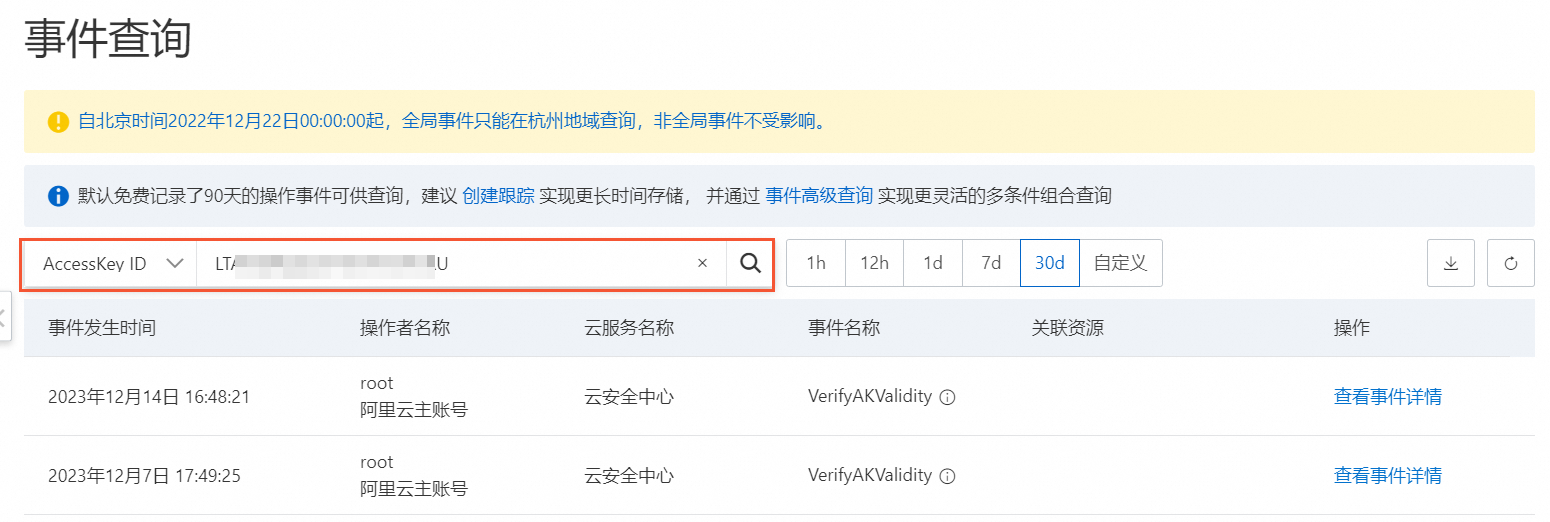
查看該AccessKey ID的呼叫事件列表,單擊目標事件操作列的查看事件詳情,可查看事件的詳細記錄資訊。
關於管控事件參數的更多資訊,請參見管控事件結構定義。
持續關注AK異常調用
及時處理了AK泄露事件後,建議您持續關注AK調用異常,防止類似事件的發生,以及在泄露發生時快速響應,縮小事件影響範圍。下述內容提供了三種不同的方式,您可以根據實際需要選擇。
從攻擊視角監測AK異常調用
Security Center根據多年沉澱的安全攻防經驗和大模型,可以檢測常見的AK調用異常,例如調用AK的IP地址在近期發起過攻擊行為、該IP在雲上批量調用多個使用者的AK、調用的API較為敏感且該AK出現過泄露等。下文介紹在Security Center控制台查看AK異常調用警示的具體操作。
在左側導覽列,選擇。在控制台左上方,選擇需防護資產所在的地區:中國內地或非中國內地。
將警示類型選擇為雲產品威脅檢測,查看是否存在AK異常調用警示。
如果存在AK異常調用警示,您需要查看警示詳情,及時確認該AK調用是否為正常行為。
(可選)配置安全警示通知。
您可以在Security Center控制台系統設定>通知設定頁面,配置安全警示的通知方式,以便能及時收到AK調用異常警示。免費版僅支援配置站內信通知方式。具體操作,請參見通知設定。
監測阿里雲帳號調用AK等異常
Action Trail服務提供了內建警示,可監控阿里雲帳號調用AK及AK異常調用。您可以在Action Trail控制台啟用內建警示AK使用的異常頻率警示和Root帳號AK使用檢測,以便能在出現AK異常調用時收到通知。具體操作,請參見設定事件警示。
基於歷史行為檢測AK異常調用
Action Trail服務提供的審計事件洞察(Insights事件)功能,可以基於歷史行為分析調用率異常的AK,及時發現異常行為。開通並查看Insights事件的具體操作,請參見通過Action Trail控制台查詢Insights事件。
使用建議
不使用阿里雲帳號(主帳號)AccessKey。
避免直接將AccessKey資訊寫入程式碼到代碼中,可通過配置環境變數的方法管理AccessKey。更多資訊,請參見憑據的安全使用方式情節。
使用私人的Github代碼倉庫來管理代碼,或搭建企業內部的代碼託管系統,防止原始碼和敏感資訊泄露。