本文介紹如何使用RDS PostgreSQL一鍵上雲功能,將公網PostgreSQL資料庫或其他雲廠商的PostgreSQL執行個體遷移至RDS。
背景
RDS PostgreSQL基於使用者VPC的網路構建,一鍵上雲功能預設支援通過內網將其他資料庫遷移到RDS PostgreSQL,如需將公網上的PostgreSQL資料庫遷移上雲,還需配置公網NAT Gateway並綁定Elastic IP Address(EIP)。
本文介紹為RDS PostgreSQL執行個體配置公網NAT Gateway並綁定Elastic IP Address(EIP),使一鍵上雲功能具備公網上雲的能力。
該方法在實現公網一鍵上雲的同時,能夠確保RDS PostgreSQL執行個體的網路安全。
公網NAT Gateway中配置SNAT條目,使RDS PostgreSQL執行個體可以訪問互連網,但不通過NAT Gateway對互連網提供服務。NAT Gateway、SNAT相關資訊,請參見使用公網NAT GatewaySNAT功能訪問互連網。
應用情境
公網自建PostgreSQL資料庫上雲。
其他雲廠商PostgreSQL執行個體(例如:Google Cloud SQL、Amazon RDS for PostgreSQL等)遷移至RDS PostgreSQL。
說明其他雲廠商可能存在自研定製的PostgreSQL外掛程式,如在遷移過程中出現外掛程式不相容報錯,請提交工單處理。
前提條件
RDS PostgreSQL執行個體需要滿足以下條件:
源執行個體與目標執行個體大版本相同,當前支援PostgreSQL 10或以上版本。
說明如果源執行個體版本低於PostgreSQL10,請先自行升級大版本後,再進行一鍵上雲操作。
如果源執行個體與目標執行個體大版本不同,則無法通過上雲評估檢查,不能進行遷移上雲。
目標執行個體為主執行個體,唯讀執行個體不支援一鍵上雲。
目標執行個體的儲存類型為雲端硬碟。
目標執行個體為空白,無資料,可用儲存空間大於等於源執行個體中資料大小的總和。
說明如果目標執行個體中存在資料,則無法通過上雲評估檢查,不能進行遷移上雲,請備份資料後清空執行個體或購買新執行個體。
使用限制
無。
影響
無影響。
注意事項
遷移上雲任務期間,請確保源執行個體可以被正常訪問,請勿執行重啟等操作,如果源執行個體閃斷或HA切換,將導致上雲任務失敗。
費用
RDS PostrgreSQL需要配置公網NAT Gateway並綁定Elastic IP Address(EIP),該操作涉及相關費用,詳情請參見公網NAT Gateway計費。
操作步驟
步驟一:配置NAT Gateway並綁定Elastic IP Address
本步驟為RDS PostgreSQL執行個體的VPC網路綁定公網IP,使RDS PostgreSQL可以訪問具備公網地址的自建資料庫或其他雲廠商資料庫。
配置前請確保RDS執行個體所在的VPC網路未配置NAT Gateway,未綁定其他公網IP,否則可能出現連通性問題。
訪問RDS執行個體列表,在上方選擇地區,然後單擊目標執行個體ID。
在左側導覽列單擊資料庫連接,然後在網路類型後單擊VPC網路的連結。
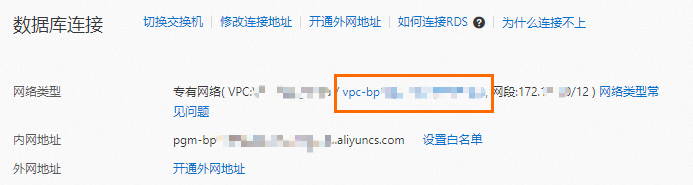
在專用網路管理主控台中,選擇資源管理頁簽,在公網訪問服務地區,單擊立即建立。
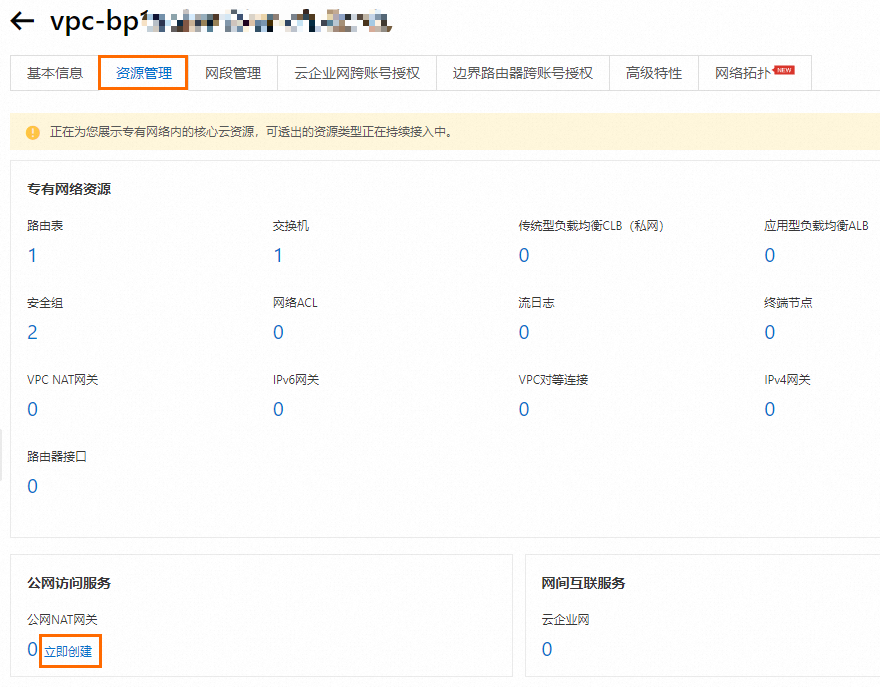
在公網NAT Gateway建立頁,配置如下關鍵參數,其他參數保持預設。
參數
說明
取值樣本
Elastic IP Address
如果您已有Elastic IP Address,則選擇已有即可。本文選擇新購Elastic IP Address。
新購Elastic IP Address
頻寬峰值
按需選擇頻寬峰值,本文介紹一鍵上雲,可調整頻寬峰值為最大,避免頻寬節流設定造成的遷移緩慢。
200Mbps
單擊立即購買。
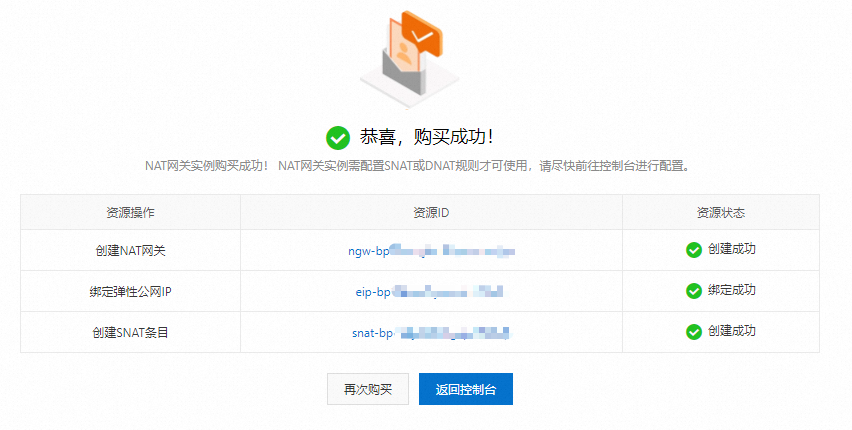
確認參數配置無誤後,勾選服務合約,單擊確認訂單。
如果出現如下頁面,即表示建立公網NAT Gateway成功,同時已綁定Elastic IP Address,配置了SNAT條目。
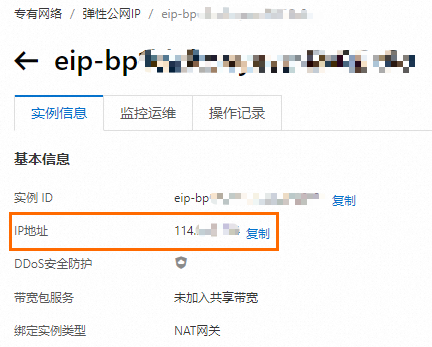
單擊Elastic IP Address的資源ID,即可在Elastic IP Address執行個體資訊頁,查看公網IP地址。
步驟二:自建資料庫或其他雲廠商執行個體配置
自建PostgreSQL資料庫配置
- 重要
pg_hba.conf檔案中配置的IP地址為步驟一中
RDS PostgreSQL執行個體綁定的Elastic IP Address/32。
其他雲廠商PostgreSQl執行個體配置
修改wal_keep_segments或wal_keep_size參數取值,具體操作請參見各雲廠商官方文檔。
查看pg_wal目錄下所能保留的過去記錄檔段的最小大小,防止全量備份完成之後由於源執行個體wal日誌被移除導致需要重新備份。
wal_keep_segments:適用於PostgreSQL 10、11、12,建議設定大於等於4096。
wal_keep_size:適用於PostgreSQL 13、14和15,建議設定大於等於65536。
建立遷移帳號。
CREATE USER migratetest CREATEROLE REPLICATION LOGIN PASSWORD '123456'; GRANT pg_monitor TO migratetest;說明上述命令中的帳號(
migratetest)和密碼(123456)僅為樣本,請根據實際需要修改。開啟公網串連並配置安全性群組或白名單,允許步驟一中RDS PostgreSQL執行個體綁定的Elastic IP Address訪問資料庫,具體操作請參見各雲廠商官方文檔。
重要請確保其他雲廠商的PostgreSQL執行個體已開放了ICMP協議,您可以使用
ping <其他雲廠商的PostgreSQL執行個體公網串連地址>命令查看。
步驟三:上雲評估
訪問RDS執行個體列表,在上方選擇地區,然後單擊目標執行個體ID。
在左側導覽列單擊一鍵上雲/容災搭建,單擊可行性評估頁簽。
在設定精靈的選擇情境與源端類型步驟中,選擇情境為遷移上雲,並選擇源端為自建執行個體或者其他執行個體,單擊下一步。
在目標執行個體配置步驟中,單擊下一步。
在源執行個體配置步驟中,勾選所有選項後,單擊下一步。
在發起可行性評估步驟中,設定如下參數。
參數
取值說明
迁移任务名
系統自動產生,無需修改。
源端 VPC IP/DNS
公網自建PostgreSQL資料庫:配置為部署資料庫的伺服器公網IP。
其他雲廠商的PostgreSQL執行個體:配置為其他雲廠商PostgreSQL執行個體的公網串連地址。
源实例Port
公網自建PostgreSQL資料庫:資料庫連接埠,可通過
netstat -a | grep PGSQL命令查看。其他雲廠商的PostgreSQL執行個體:前往各雲廠商管理主控台查看。
用户名
步驟二中建立的遷移帳號和密碼。
密码
單擊建立可行性評估任務。
遷移評估完成後,您可以在可行性評估頁面的遷移上雲列表查看遷移評估任務的狀態。
只有状态為成功,您才能進行迁移上云。
如果状态為失败,請單擊操作列的查看报告,根據報錯進行處理,常見報錯請參見解讀上雲評估報告。
說明其他雲廠商可能存在自研定製的PostgreSQL外掛程式,如在遷移過程中出現外掛程式不相容報錯,請提交工單處理。
處理報錯後,您可以單擊操作列的重新评估,重新開始評估任務。
步驟四:遷移上雲
只有上雲評估狀態為成功時,才能執行本步驟。
訪問RDS執行個體列表,在上方選擇地區,然後單擊目標執行個體ID。
在左側導覽列單擊一鍵上雲/容災搭建,切換至迁移上云頁簽,單擊建立遷移上雲任務。
在创建迁移上云任务視窗中,從关联评估任务列表中選擇步驟三中已成功的上雲評估任務。
選擇关联评估任务後,其他參數將會自動擷取,無需配置。
單擊发起迁移上云,系統將自動啟動上雲任務。
警告遷移上雲任務期間,請確保源執行個體可以被正常訪問,請勿執行重啟等操作,如果源執行個體閃斷或HA切換,將導致上雲任務失敗。
上雲切換。
在遷移上雲任務中,您可以單擊上云阶段列的連結,查看當前上雲任務進度。
當上雲階段為增量同步時,可單擊操作列的上云切换,將RDS PostgreSQL提升為主庫,正式提供服務。
在切换上云視窗,根據上雲鬚知提示,設定源執行個體唯讀或應用停止寫入。
設定源執行個體唯讀:
-- 設定資料庫唯讀 ALTER SYSTEM SET default_transaction_read_only=on; -- 重新載入參數配置使修改生效 SELECT pg_reload_conf(); -- 中斷所有現有會話 SELECT pg_terminate_backend(pid) FROM pg_stat_activity WHERE usename not in ('replicator', 'monitor', 'pgsql', 'aurora') AND pid != pg_backend_pid();選中所有複選框,單擊立即切换,等待遷移完成。