預設情況下,NAS只支援將檔案系統掛載到同帳號同地區同VPC下的Elastic Compute Service。當您想跨VPC掛載訪問NAS時,可以通過PrivateLink來建立兩者之間的私網串連,無需使用NAT Gateway或Elastic IP Address等公網出口。資料轉送不經過公網,可以提供更高的安全性和網路品質。本文介紹如何通過私網串連PrivateLink實現同地區跨VPC掛載訪問NAS。
功能介紹
私網串連(PrivateLink)是利用阿里雲的私人網路進行服務互動的一種方式。利用私網串連,您可以通過私人網路單向訪問部署在其他VPC中的服務,無需建立NAT Gateway(NAT Gateway)、Elastic IP Address(Elastic IP Address,簡稱EIP)等公網出口。互動資料不會經過互連網,有更高的安全性和更好的網路品質。
私網串連的終端節點服務支援將網路型負載平衡NLB(Network Load Balancer )作為服務資源。NLB接收來自用戶端的請求,並按照監聽規則將請求分發至後端伺服器。使用NLB作為終端節點服務的服務資源時,最多可以配置一個為多個可用性區域提供服務的NLB服務資源,不需要為每個可用性區域配置單獨的NLB服務資源。
情境說明
本案例介紹在同帳號同地區的VPC1執行個體下的ECS訪問VPC2執行個體下的通用型NAS NFS協議檔案系統的操作步驟。您需要在VPC2中建立NLB執行個體,該執行個體包含兩個可用性區域, 然後建立後端伺服器組S1和S2,將NAS NFS協議檔案系統執行個體的兩個訪問連接埠(111、2049)添加到NLB的後端伺服器組。建立終端節點服務,將NLB執行個體添加為服務資源。在VPC1中建立終端節點,建立成功後,終端節點與終端節點服務建立串連且狀態正常時,VPC1的ECS執行個體即可私網訪問VPC2中的NAS NFS協議檔案系統。
如果是SMB協議檔案系統,只需要建立一個後端伺服器組,並添加445訪問連接埠至NLB的後端伺服器組。
本文2個VPC網路規劃如下表所示。在您規劃網路時,選擇的VPC1和VPC2的網段可以重疊且互不影響。
屬性 | VPC1 | VPC2 |
網路執行個體所屬的地區 | 西南1(成都) | 西南1(成都) |
網路執行個體的網段規劃 |
|
|
網路執行個體交換器的可用性區域 |
|
|
使用限制
建立終端節點服務時,選擇地區需要同時支援私網串連和NLB執行個體的地區。關於私網串連和NLB執行個體支援的地區,請參見支援私網串連的地區和可用性區域和NLB支援的地區與可用性區域。
只有終端節點和終端節點服務是同可用性區域才可以建立串連,終端節點部署的可用性區域必須是終端節點服務資源部署的可用性區域的子集,因此建議終端節點服務資源部署選擇該地區下的全部或者儘可能多的可用性區域,方便被不同終端節點調用服務。
私網串連預設不支援IPv6類型的訪問,如需使用,請聯絡客戶經理申請。
僅支援通用型NAS使用PrivateLink實現同地區跨VPC掛載訪問NAS。
前提條件
您已經在西南1(成都)地區建立了VPC1和VPC2,並且在VPC1中建立了一個位於可用性區域A和可用性區域B的交換器,在VPC2中建立了一個位於可用性區域A和可用性區域B的交換器。具體操作,請參見搭建IPv4專用網路。
您已經在VPC1中建立了位於可用性區域A的ECS,作為掛載用戶端。在VPC2中建立了位於可用性區域A的通用型NAS。具體操作,請參見自訂購買ECS執行個體和建立檔案系統。
您已經在VPC1中建立了安全性群組。您可以根據自己的實際業務和安全要求配置安全性群組規則。具體操作,請參見建立安全性群組。
步驟一:建立私網類型的NLB執行個體
在頂部功能表列,選擇NLB執行個體所屬的地區。
在執行個體頁面,單擊建立網路型負載平衡。
在網路型負載平衡(隨用隨付)國際站購買頁面,根據以下資訊配置NLB執行個體,然後單擊立即購買。
配置
說明
地區
選擇執行個體所屬的地區。本文選擇西南1(成都)。
執行個體網路類型
選擇執行個體的網路類型。本文只支援選擇私網。
VPC
選擇執行個體所屬的VPC。本文選擇VPC2。
可用性區域
執行個體所在的可用性區域,需要選擇至少2個可用性區域。本文選擇成都可用性區域A以及可用性區域A下的交換器、成都可用性區域B以及可用性區域B下的交換器。
協議版本
選擇執行個體的協議版本。
IPv4:表示NLB執行個體僅支援用戶端使用IPv4地址訪問。
雙棧:表示NLB執行個體支援用戶端同時使用IPv4和IPv6地址訪問。
執行個體名稱
自訂執行個體名稱。
資源群組
選擇NLB所屬的資源群組。本文選擇預設資源群組。
服務關聯角色
首次建立NLB執行個體時,需要單擊建立服務關聯角色關聯服務角色。
步驟二:建立NLB的後端伺服器組
在左側導覽列,選擇網路型負載平衡NLB>伺服器組。
在頂部功能表列,選擇地區。
在伺服器組頁面,單擊建立伺服器組。
在建立伺服器組對話方塊中,配置以下參數,然後單擊建立。
配置
說明
伺服器群組類型
選擇伺服器組的類型。本文選擇IP類型。
伺服器組名稱
自訂伺服器組的名稱。本文輸入
S1。VPC
選擇後端伺服器組所屬的VPC。本文選擇VPC2。
選擇後端協議
選擇一種後端類型。本文選擇TCP。
選擇調度演算法
選擇一種調度演算法。本文預設加權輪詢。
開啟IPv6掛載
選擇是否開啟IPv6掛載。
選擇開啟IPv6掛載功能後,伺服器組支援掛載IPv4、IPv6類型的後端伺服器。
不開啟IPv6掛載功能時,伺服器組僅支援掛載IPv4類型的後端伺服器。
說明當伺服器組選擇的VPC未開啟IPv6功能時,預設不開啟IPv6掛載功能。
開啟串連優雅中斷
啟用串連優雅中斷後,您可以在移除後端伺服器或者健全狀態檢查失敗後,使現有串連在一定時間內正常傳輸。
串連優雅中斷逾時時間:開啟串連優雅中斷後,需輸入串連優雅中斷逾時時間。
本文選擇預設關閉。
開啟用戶端地址保持
開啟或關閉用戶端地址保持。IP類型的伺服器組不支援自動攜帶用戶端源地址,請在監聽中搭配ProxyProtocol實現源地址擷取。
開啟全連接埠轉寄
開啟或關閉全連接埠轉寄。開啟後添加後端伺服器無需指定連接埠,NLB將按照前端請求連接埠轉寄流量至後端伺服器。
說明當您的監聽開啟時,後端伺服器組需開啟該功能。
本文選擇預設關閉。
配置健全狀態檢查
開啟或關閉健全狀態檢查。本文選擇預設開啟。
當開啟健全狀態檢查後您可以單擊編輯修改健全狀態檢查相關配置。本文健全狀態檢查配置保持預設配置。
建立完成後,找到目標後端伺服器組S1,單擊目標伺服器組ID。
單擊後端伺服器頁簽,然後單擊添加IP。
在添加後端伺服器面板,輸入NAS執行個體的掛載點VIP,然後單擊下一步。
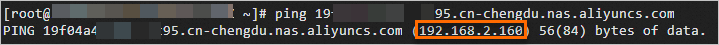
您可以直接在ECS執行個體中ping掛載點擷取掛載點VIP。樣本如下:
執行命令:
ping 19f04a4****-i****.cn-chengdu.nas.aliyuncs.com返回樣本:
設定已添加的NAS執行個體的連接埠和權重,然後單擊確定。
連接埠設定為
111,權重保持預設值。建立成功後,重複上述步驟建立後端伺服器組S2,在添加後端伺服器時,將連接埠設定為
2049。說明如果是SMB協議類型的檔案系統,只需要建立1個後端伺服器組,並將連接埠設定為
445。
步驟三:配置監聽
在左側導覽列,選擇。
在執行個體頁面,找到目標執行個體,單擊執行個體ID。
單擊監聽頁簽,在監聽頁簽單擊建立監聽。
在配置監聽設定精靈頁面,完成以下配置,然後單擊下一步。
配置
說明
選擇負載平衡協議
選擇監聽的協議類型。本文選擇TCP。
全連接埠功能
選擇是否開啟全連接埠功能。開啟全連接埠功能後,NLB可以對監聽連接埠段的所有連接埠進行監聽,並將監聽連接埠上接收到的請求直接轉寄至後端伺服器的對應連接埠。本文保持預設關閉。
監聽連接埠段
用來接收和處理請求的監聽連接埠。選擇
111。說明如果是SMB協議檔案系統,選擇
445。監聽名稱
輸入自訂監聽的名稱。
進階配置
展開進行配置。本文保持預設值。
在選擇伺服器組設定精靈,選擇步驟二中建立的後端伺服器組S1,然後單擊下一步。
重要選擇的後端伺服器組需要和監聽連接埠一一匹配,否則會無法掛載訪問NAS。
在組態稽核設定精靈,確認監聽配置資訊,然後單擊提交。
在負載平衡業務設定精靈對話方塊,單擊知道了,然後返回執行個體管理頁面。
當監聽的健全狀態檢查狀態為正常時,表示後端伺服器(NAS執行個體的VIP)可以正常處理NLB執行個體轉寄的請求了。
重複步驟4~步驟7,監聽連接埠段設定為
2049,選擇伺服器組設定精靈中配置為S2。說明如果是SMB協議檔案系統,則只需要配置445連接埠的監聽。
步驟四:建立終端節點服務
登入終端節點服務控制台。
在頂部功能表列,選擇要建立終端節點服務的地區。本文選擇西南1(成都)。
在終端節點服務頁面,單擊建立終端節點服務。
在建立終端節點服務頁面,根據以下資訊配置終端節點服務,然後單擊確定建立。
參數
描述
服務資源類型
終端節點服務下的服務資源的類型。本文選擇網路型負載平衡NLB。
選擇服務資源
選擇服務資源的可用性區域及可用性區域下的服務資源。
本文可用性區域選擇成都可用性區域A,然後單擊+添加服務資源選擇另一可用性區域成都可用性區域B。可用性區域A和可用性區域B的服務資源選擇步驟一中建立的NLB執行個體。
自動接受終端節點串連
選擇是否自動接受終端節點的串連請求。本文選擇否。
是否支援同可用性區域優先
選擇是否支援就近解析。本文選擇否。
資源群組
選擇終端節點服務所在的資源群組。
描述
輸入終端節點服務的描述資訊。
步驟五:建立終端節點
登入終端節點控制台。
在頂部功能表列,選擇要建立終端節點服務的地區。本文選擇西南1(成都)。
在終端節點頁面,單擊介面終端節點頁簽,然後單擊建立終端節點。
在建立終端節點頁面,根據以下資訊配置終端節點,然後單擊確定建立。
參數
描述
節點名稱
自訂終端節點的名稱。
終端節點類型
終端節點選擇的節點類型。本文選擇介面終端節點。
終端節點服務
選擇目標終端節點服務。
本文單擊選擇可用服務,然後選擇步驟四:建立終端節點服務建立的終端節點服務。
專用網路
選擇終端節點所屬的專用網路。本文選擇VPC1。
安全性群組
選擇要與終端節點網卡關聯的安全性群組。安全性群組可以管控VPC1到終端節點網卡的資料通訊。
說明確保安全性群組內的規則開放了用戶端對終端節點網卡的訪問。
可用性區域與交換器
選擇終端節點服務對應的可用性區域,然後選擇該可用性區域內的交換器,系統會自動在該交換器下建立一個終端節點網卡。
本文可用性區域選擇成都可用性區域A並選擇可用性區域A內的交換器,然後單擊+添加交換器選擇可用性區域成都可用性區域B並選擇可用性區域B內的交換器。
資源群組
選擇目標資源群組。
描述
輸入終端節點的描述資訊。
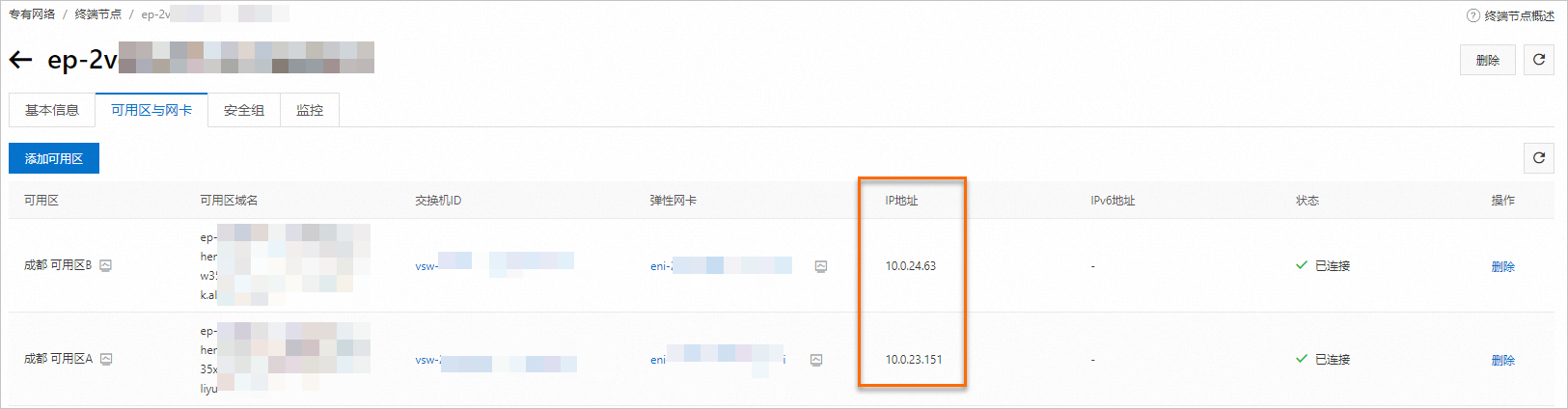
建立完終端節點後,您可以看到產生的終端節點可用性區域的網域名稱和IP。
步驟六:接受串連請求
終端節點發送串連請求後,終端節點服務需要接受終端節點的串連請求。接受後,VPC1才能通過終端節點訪問終端節點服務。
如果您在步驟四建立終端節點服務時設定自動接受串連請求,請忽略此步驟。
步驟七:掛載檔案系統
遠端連線雲端服務器。具體串連方式,請參見串連執行個體。
測試VPC1和VPC2之間的網路連通性。
本樣本使用telnet工具進行測試,測試前,請確認已安裝telnet工具。需確認步驟五產生的終端節點IP地址的網路均連通。執行命令樣本如下,請根據實際情況替換終端節點IP和轉換連接埠。
telnet 10.0.23.151 2049執行命令後,如果未返回錯誤資訊,則表示VPC1和VPC2之間的網路已連通。
掛載檔案系統。
安裝NFS用戶端,請參見安裝NFS用戶端。
說明Windows作業系統,請參見掛載SMB協議檔案系統。
掛載檔案系統。
使用步驟五產生的終端節點的任意IP地址進行掛載,掛載命令樣本如下。
sudo mount -t nfs -o vers=3,nolock,proto=tcp,rsize=1048576,wsize=1048576,hard,timeo=600,retrans=2,noresvport 10.0.23.117:/ /mnt說明Windows作業系統,請參見如下命令。
net use Z: \\10.0.23.151\myshare
後續操作
當您不在ECS執行個體中使用NAS檔案系統時,請先卸載檔案系統,然後再刪除NLB執行個體和終端節點等資源。如果您先刪除了NLB執行個體及終端節點等資源但並未卸載檔案系統時,會導致作業系統出現執行命令卡頓、無響應等異常情況。
釋放檔案系統資源
如果只是卸載掛載的檔案系統,請參見通過執行命令卸載掛載目錄。
如果是不再使用NAS儲存資料或想停止NAS服務,請參見釋放檔案系統執行個體資源。
釋放NLB資源
具體操作,請參見釋放執行個體。
釋放終端節點資源
具體操作,請參見刪除終端節點服務。
相關文檔
您還可以使用阿里雲雲企業網服務實現同地區跨VPC掛載檔案系統。具體操作,請參見通過雲企業網實現同地區跨VPC掛載NAS。
如果您需要跨地區或跨帳號掛載訪問檔案系統,請參見通過雲企業網實現跨帳號跨地區掛載NAS。
如果您需要在本機資料中心掛載訪問檔案系統,請參見本機資料中心訪問檔案系統。
如果您需要將線下資料、IDC資料、本地NAS資料、OSS資料移轉至雲上NAS檔案系統中,請參見資料移轉。