雲原生網關和後端服務所在的節點分別處於不同安全性群組內。您可以通過設定安全性群組規則為雲原生網關授予訪問後端服務的許可權。
背景資訊
安全性群組是一種虛擬防火牆,用於控制安全性群組內ECS執行個體和ENI網卡的入流量和出流量,從而提高ECS執行個體的安全性。安全性群組具備狀態檢測和資料包過濾能力,您可以基於安全性群組的特性和安全性群組規則的配置在雲端劃分安全域,詳情請參見安全性群組概述。
您在購買雲原生網關時需要選擇VPC和安全性群組類型(建議與後端服務所在安全性群組類型一致),根據您選擇的安全性群組類型,雲原生網關會建立相應託管安全性群組管理網關的執行個體節點。因為雲原生網關和後端服務所在的節點分別處於不同安全性群組內,需要您在後端服務的安全性群組內為雲原生網關授予必要的連接埠範圍存取權限。
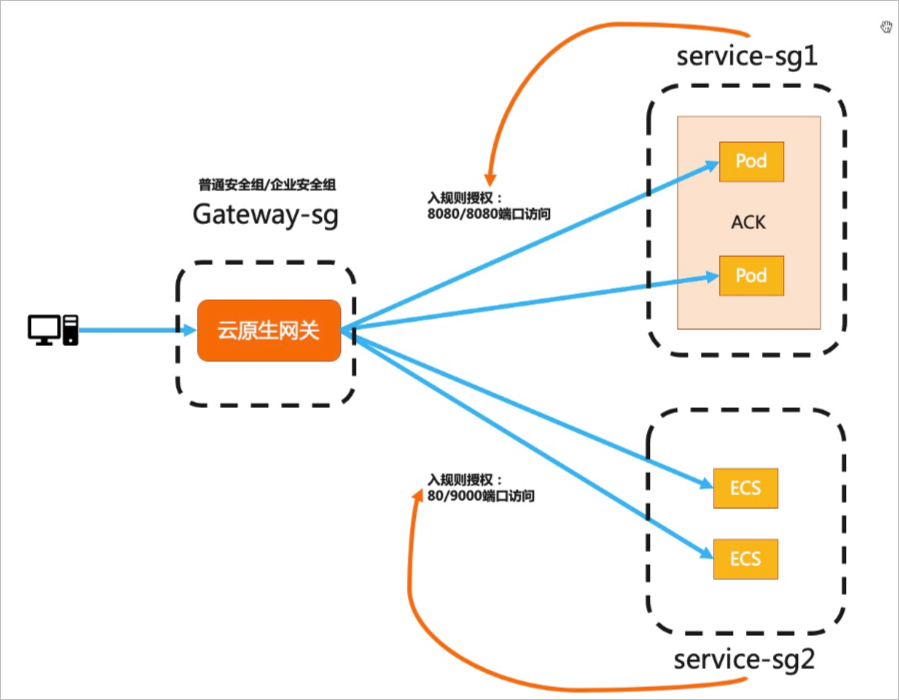
步驟一:擷取目標服務所在節點的安全性群組
雲原生網關關聯的上遊服務,主要包括容器部署和ECS部署。您可以通過以下方式擷取安全性群組ID。
目標服務部署在Container ServiceACK託管叢集
登入Container Service管理主控台,在左側導覽列選擇叢集列表。
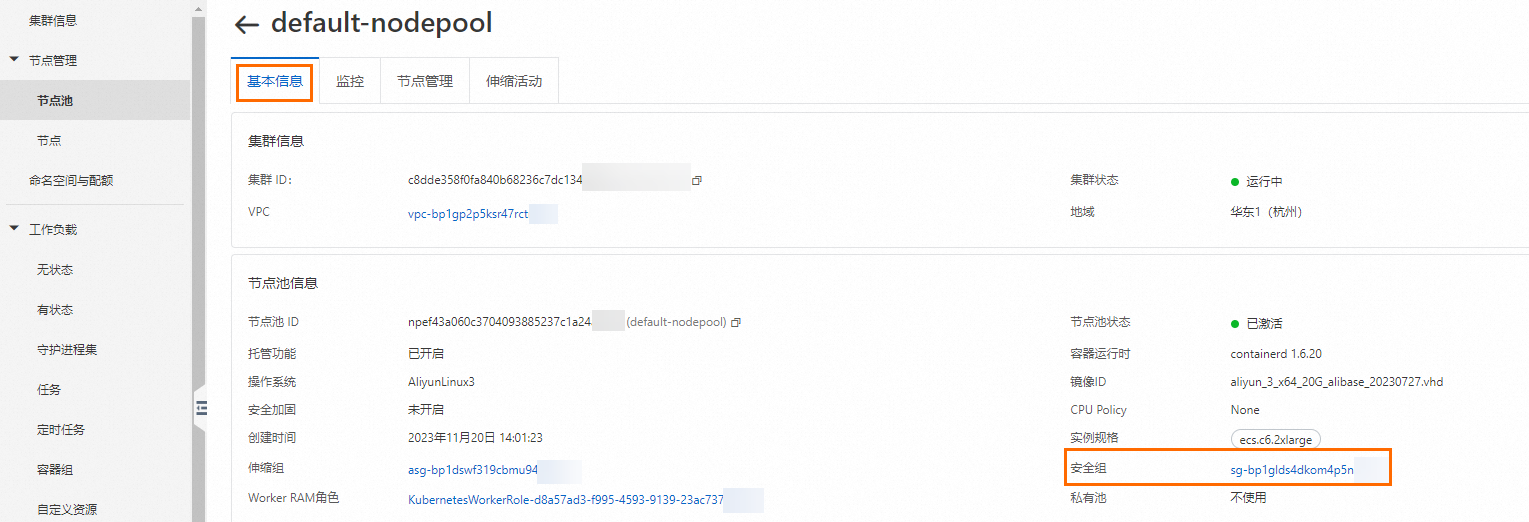
在叢集列表頁面,單擊目的地組群名稱,然後在左側導覽列,選擇。
在節點池頁面,單擊目標節點,然後單擊基本資料頁簽,擷取安全性群組的ID。
目標服務部署在Container ServiceACK Serverless 叢集
登入Container Service管理主控台,在左側導覽列選擇叢集列表。
在叢集列表頁面,單擊目的地組群名稱,然後單擊基本資料,在基本資料頁簽,擷取安全性群組ID。

目標服務部署在ECS
登入ECS管理主控台。
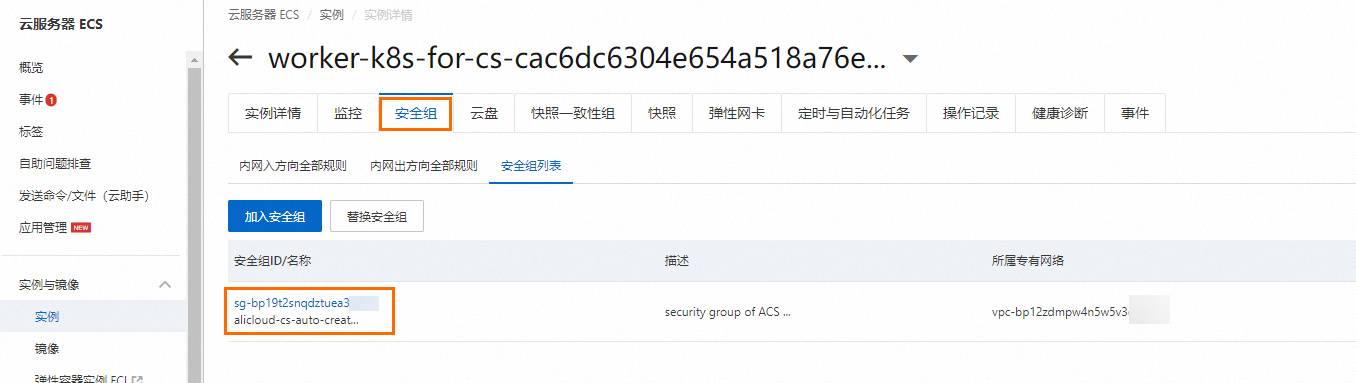
在左側導覽列,選擇。
在執行個體頁面,單擊目標服務所部署的ECS執行個體,然後單擊安全性群組頁簽,擷取安全性群組的ID。
步驟二:添加安全性群組授權規則
登入MSE網關管理主控台。
在左側導覽列,選擇云原生网关 > 网关列表,並在頂部功能表列選擇地區。
在网关列表頁面,單擊目標網關名稱。在左側導覽列單擊基本概览,然後單擊安全组授权頁簽。
單擊授权安全组,在SecurityGroup ID列的文字框中,粘貼步驟一中擷取的安全性群組ID,選擇相應的安全性群組。
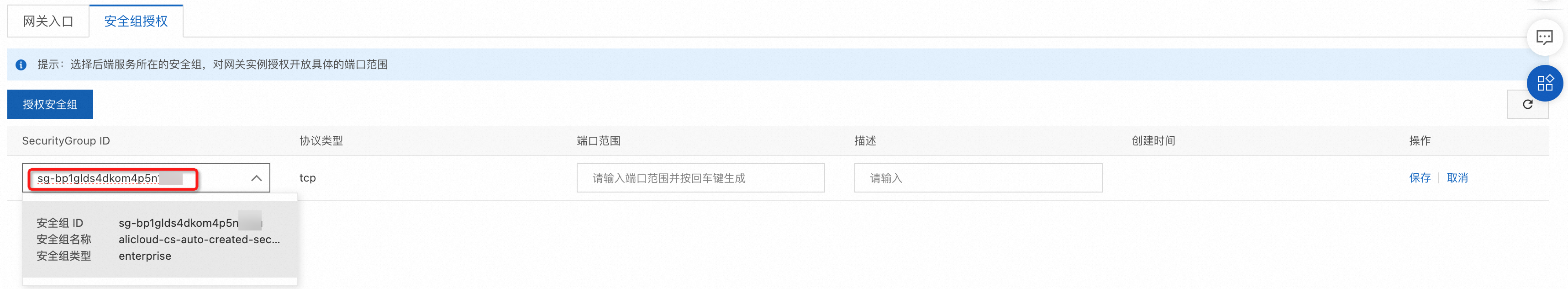
輸入安全性群組授權的連接埠範圍:起始值/終止值。
可以輸入多個連接埠範圍,每輸入一個連接埠範圍單擊斷行符號,即可生效。
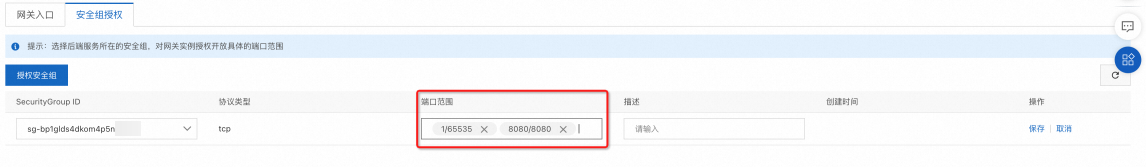
單擊儲存。
雲原生網關會產生對應的規則。
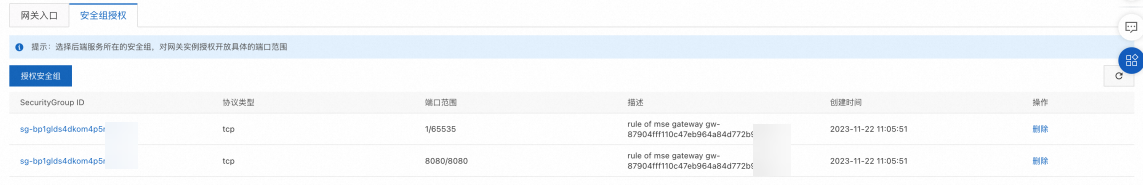
同時目標節點所在的安全性群組中也會看到在雲原生網關建立的安全性群組規則。
刪除安全性群組授權規則
登入MSE網關管理主控台。
在左側導覽列,選擇云原生网关 > 网关列表,並在頂部功能表列選擇地區。
在网关列表頁面,單擊目標網關名稱。
在左側導覽列基本概览,單擊授权安全组頁簽,然後單擊操作列下方的删除,單擊确定。
預設只刪除雲原生網關的安全性群組規則,如需將目標節點所在安全性群組的規則一併刪除,您還需要勾選串聯刪除該安全性群組內的上述入方向規則。
常見問題
問題一:安全性群組已經授權,為什麼服務還是訪問不通?
您可以按照如下步驟自助排查:
首先需要確認您的目標服務所部署的節點是否正確。
有可能存在服務部署在了A節點上,但是給B節點所在的安全性群組授權。
您的目標節點是否設定了多個安全性群組。
如果是多個安全性群組,建議給每個安全性群組都授權。
問題二:安全性群組已經授權,之前網關訪問服務是通的,現在突然間不通了,是什麼原因?
您可以按照如下步驟自助排查:
首先確認您的服務本身沒有問題。
您可以對同一安全性群組內的其他節點使用
curl命令檢查服務的連通性。確認您發布的服務對外暴露的連接埠是否有變更。
例如以前連接埠為8080,在雲原生網關只給8080連接埠授權了,之後又將連接埠變更為8081,這時需要重新調整雲安全性群組授權規則連接埠。為了避免這種情況發生,建議您在配置安全性群組授權時擴大連接埠範圍,可以將範圍選成1/65535。