如果您需要在叢集中通過MSE Ingress訪問服務,部署服務前需要為MSE Ingress Controller授予MSE的相關存取權限。
為ACK託管叢集或ACK Serverless叢集的MSE Ingress Controller授權
在ACK託管叢集或ACK Serverless叢集中,可以通過以下兩種方式為MSE Ingress Controller授權。
如果您需要在已有的ACK託管叢集或ACK Serverless叢集中使用MSE Ingress,請參考方式一完成授權。
如果您在建立ACK託管叢集或ACK Serverless叢集時就確認了要使用MSE Ingress,請參考方式二完成授權。
方式一:在組件管理中為MSE Ingress Controller完成授權
在組件管理中安裝MSE Ingress Controller的過程中會自動進行許可權校正。如果出現前置檢查失敗,您需要按照以下步驟完成授權。
將滑鼠移至前置檢查失敗提示處,單擊查看檢查報告。
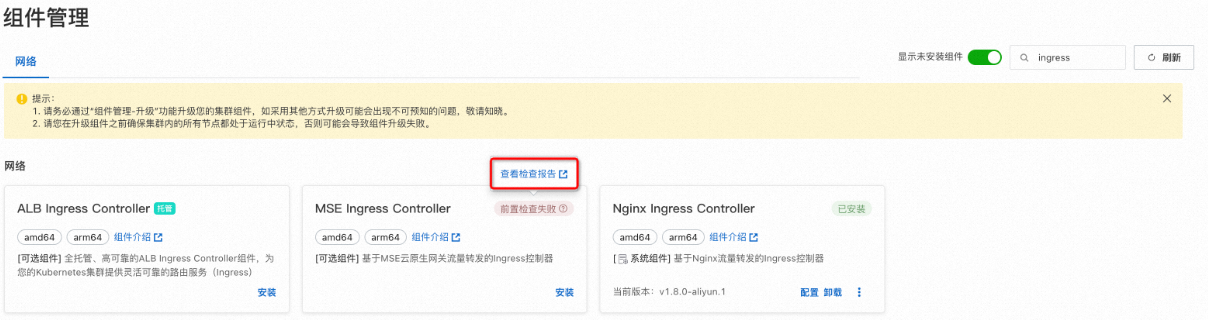
在檢查報告頁面,單擊異常下方的紅色方框,然後單擊面板中的連結。
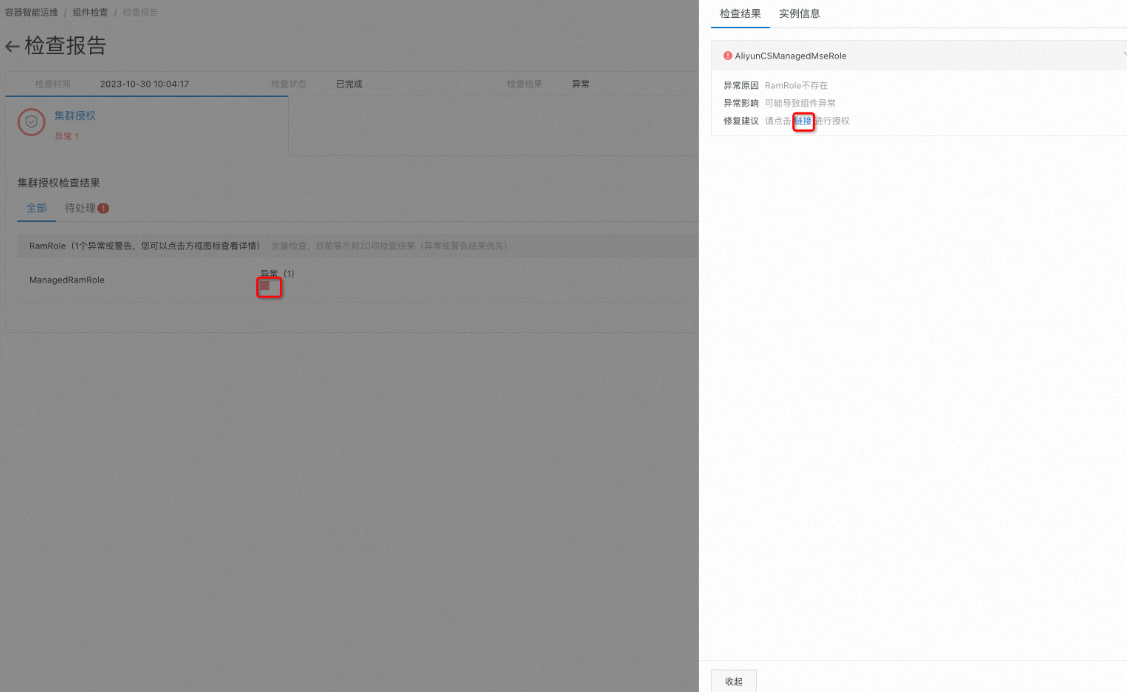
在存取控制快速授權頁面,單擊確認授權。
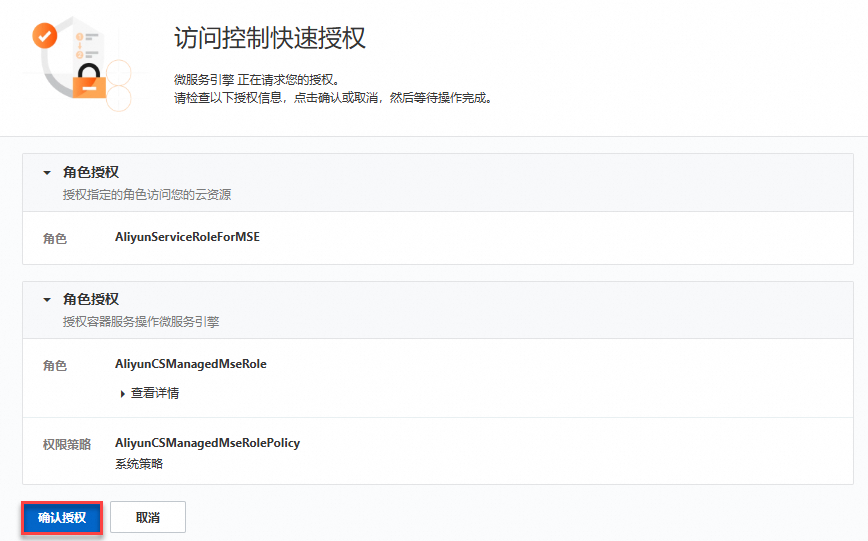
重新安裝組件。
方式二:在建立叢集時為MSE Ingress Controller完成授權
在建立叢集時安裝MSE Ingress Controller,在確認配置步驟的依賴檢查地區,查看MSE Ingress角色授權檢查的狀態是否通過。如狀態顯示未通過,則需要單擊去授權。
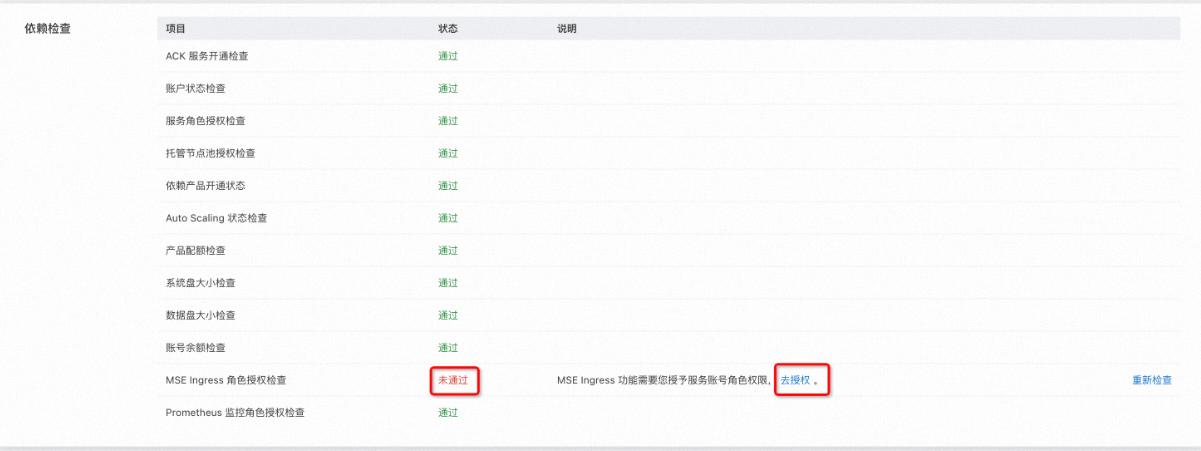
在存取控制快速授權頁面,單擊確認授權。
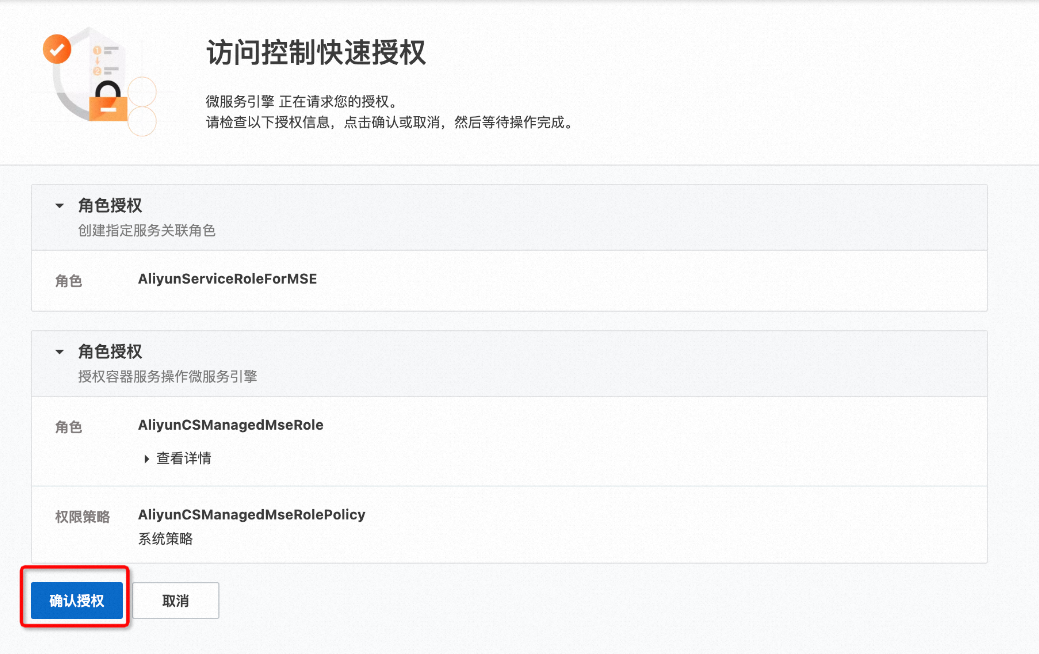
授權完成後,返回確認配置頁面,單擊重新檢查。檢查通過後單擊建立叢集。
為ACK專有版叢集中的MSE Ingress Controller授權
在左側導覽列,單擊叢集列表,然後單擊目的地組群名稱。
在叢集資訊頁面的基本資料欄的叢集資源地區,單擊Worker RAM 角色右側的連結。
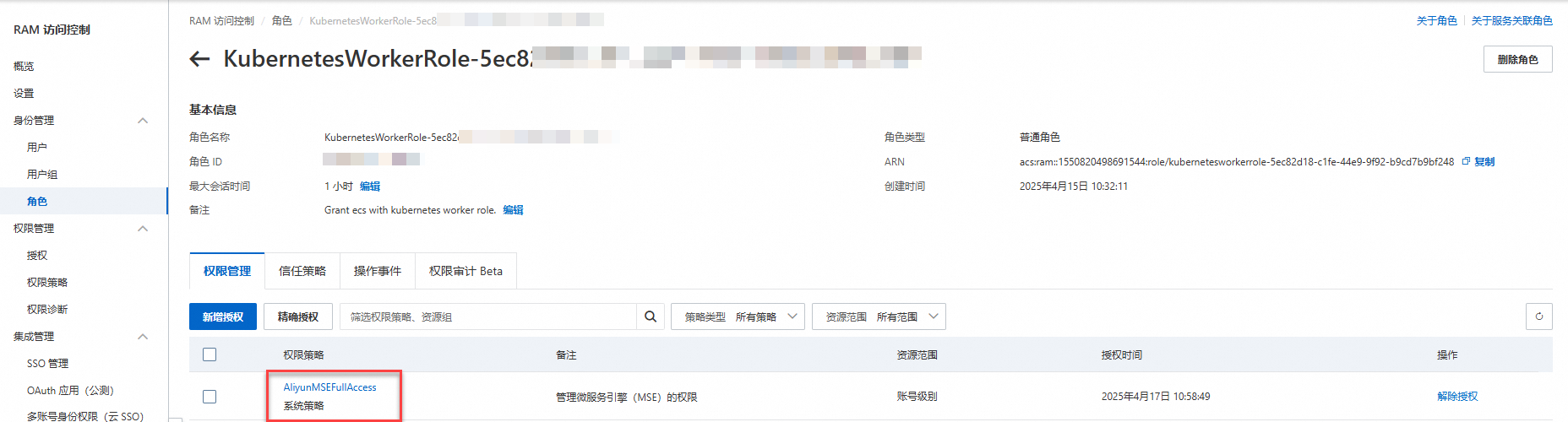
在RAM控制台,為該角色添加AliyunMSEFullAccess許可權。
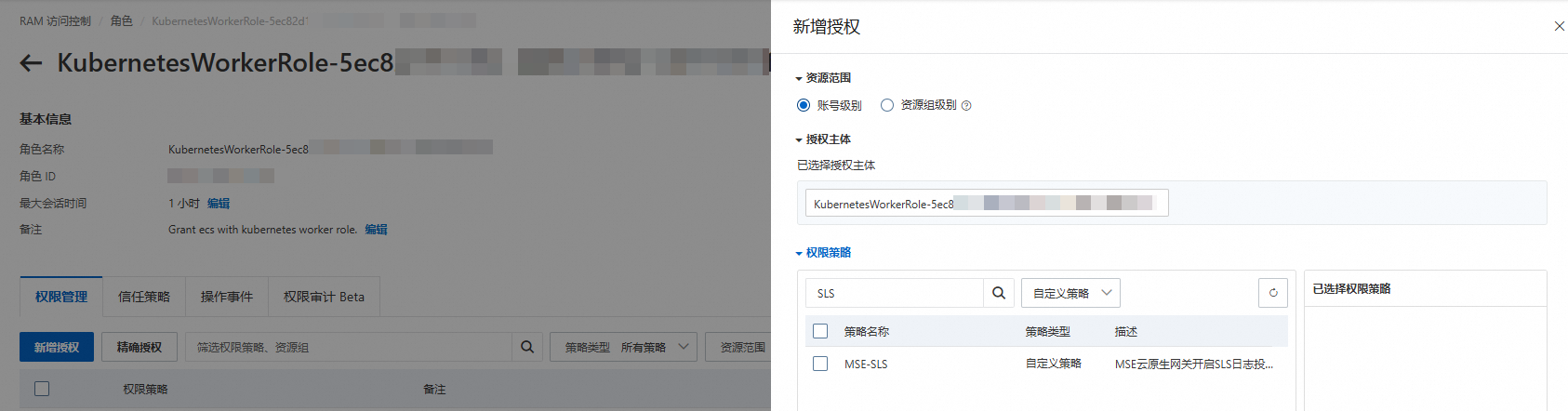
在角色頁面的許可權管理頁簽,單擊新增授權。
在新增授權頁面的權限原則地區單擊下拉框,選擇系統策略,然後在輸入欄輸入權限原則名稱進行模糊搜尋。
例如,輸入mse可以搜尋到AliyunMSEFullAccess。
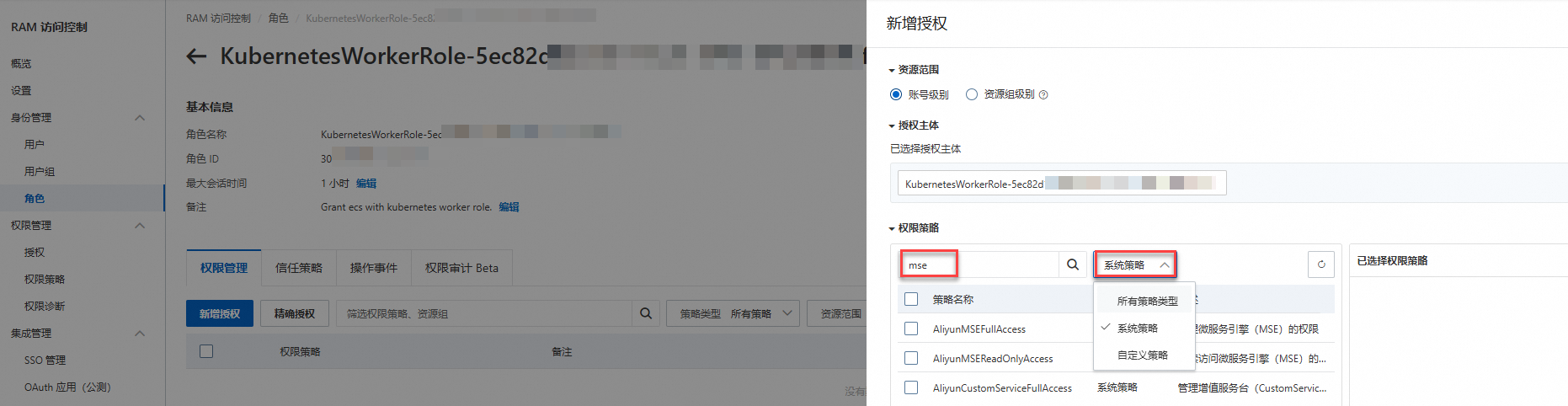
勾選權限原則名稱AliyunMSEFullAccess,然後單擊確認新增授權完成添加許可權。
您可以在下圖所示的位置查看是否已為該角色成功添加AliyunMSEFullAccess許可權。
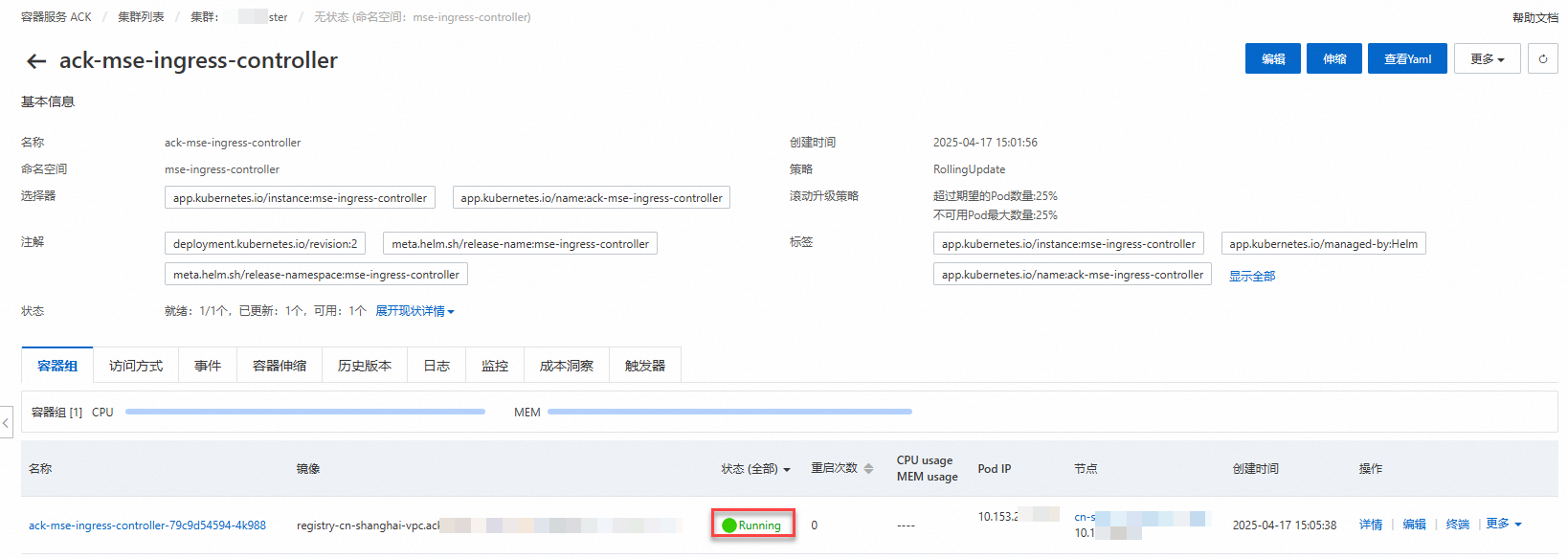
在目的地組群的命名空間mse-ingress-controller中搜尋到ack-mse-ingress-controller應用,單擊操作列下方的
 ,選擇重新部署,然後單擊確定。
,選擇重新部署,然後單擊確定。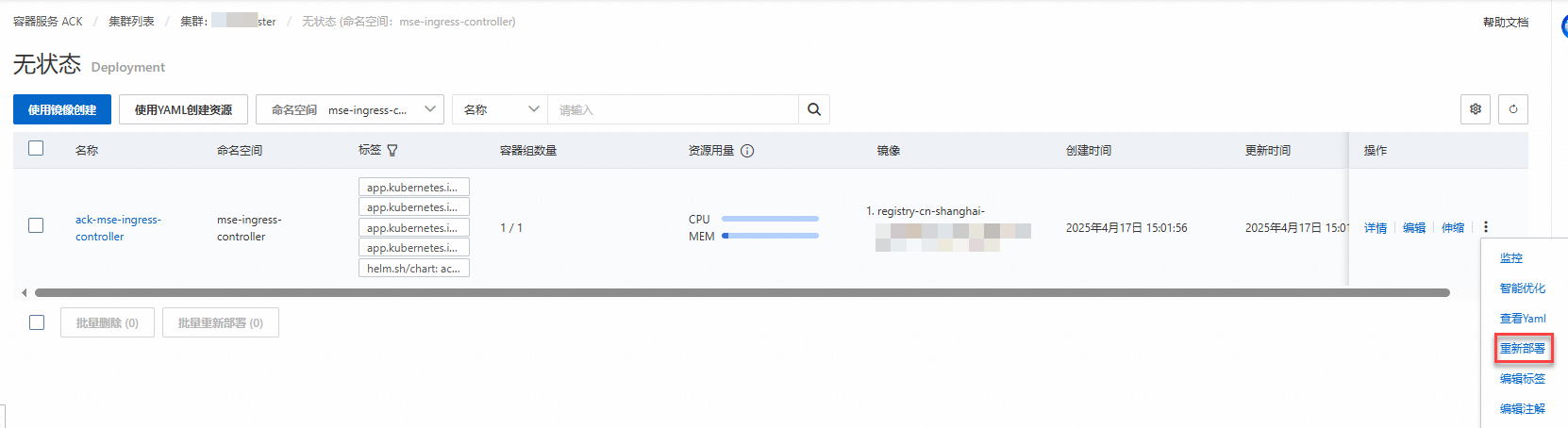
重新部署完成後,單擊ack-mse-ingress-controller應用,確認重建後的Pod處於Running狀態。
(可選)建立SLS權限原則並為叢集授予SLS相關許可權
如果您希望通過MseIngressConfig為MSE雲原生網關開啟SLS日誌投遞服務,那麼您需要為叢集資源的Worker RAM角色額外授予SLS相關許可權。
使用Resource Access Management員登入RAM控制台。
在左側導覽列,選擇。
在權限原則頁面,單擊建立權限原則。
在建立權限原則頁面,單擊指令碼編輯選項,輸入如下權限原則內容,然後單擊確定。
{ "Version": "1", "Statement": [ { "Action": [ "log:CloseProductDataCollection", "log:OpenProductDataCollection", "log:GetProductDataCollection" ], "Resource": [ "acs:mse:*:*:instance/*", "acs:log:*:*:project/*/logstore/mse_*" ], "Effect": "Allow" }, { "Action": "ram:PassRole", "Resource": "acs:ram::*:role/aliyunserviceroleforslsaudit", "Effect": "Allow" }, { "Action": "ram:CreateServiceLinkedRole", "Resource": "*", "Effect": "Allow", "Condition": { "StringEquals": { "ram:ServiceName": "audit.log.aliyuncs.com" } } } ] }在建立權限原則彈框中輸入策略名稱稱和備忘,單擊確定。
為叢集資源的Worker RAM角色授予SLS相關許可權。
在左側導覽列,單擊叢集列表,然後單擊目的地組群名稱。
在叢集資訊頁面的基本資料欄的叢集資源地區,單擊Worker RAM 角色右側的連結。
在RAM控制台,為該角色添加SLS相關許可權。
在角色頁面的許可權管理頁簽,單擊新增授權。
在新增授權頁面的權限原則地區,單擊下拉框選擇自訂策略,然後在文字框輸入權限原則名稱進行模糊搜尋。
說明SLS的權限原則名稱為您自訂的名稱。
勾選目標權限原則名稱,然後單擊確認新增授權完成授權。
為ACS叢集中的MSE Ingress Controller授權
在ACS叢集中,您可以通過以下方式為MSE Ingress Controller授權。如果您在建立ACS叢集時確認要使用MSE Ingress,請參考以下方式完成授權。
在建立叢集時安裝MSE Ingress Controller,在確認配置步驟的依賴檢查地區,查看MSE Ingress角色授權檢查的狀態是否通過。如狀態顯示不通過,則需要單擊去授權。
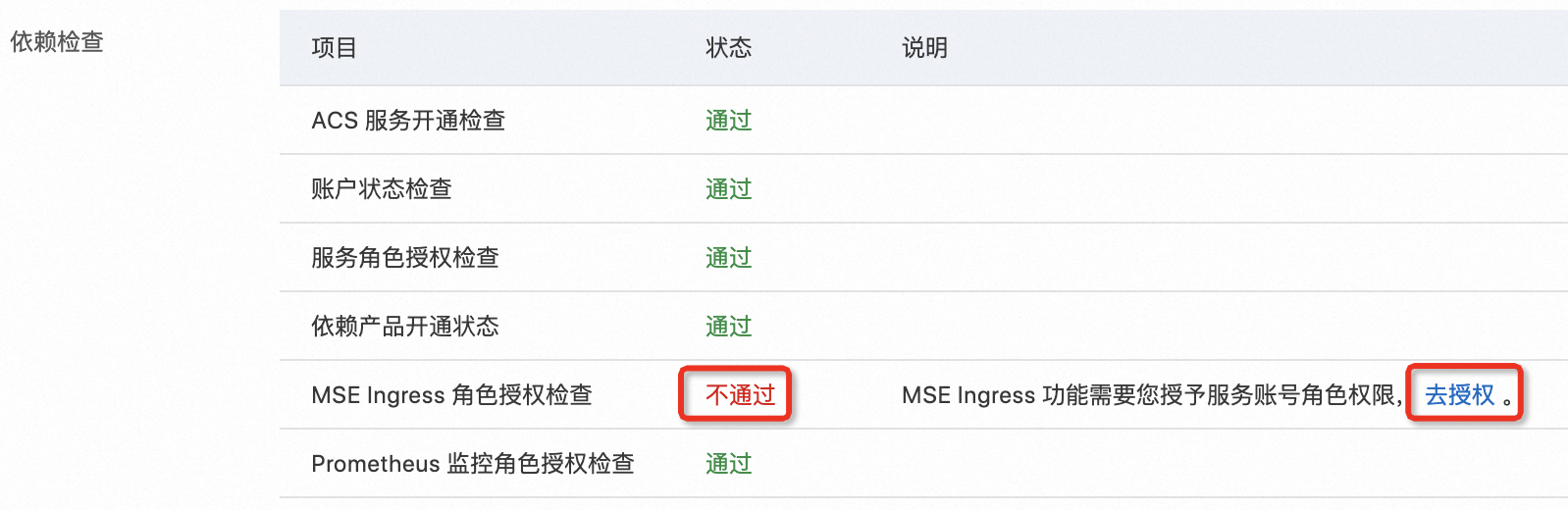
在存取控制快速授權頁面,單擊確認授權。
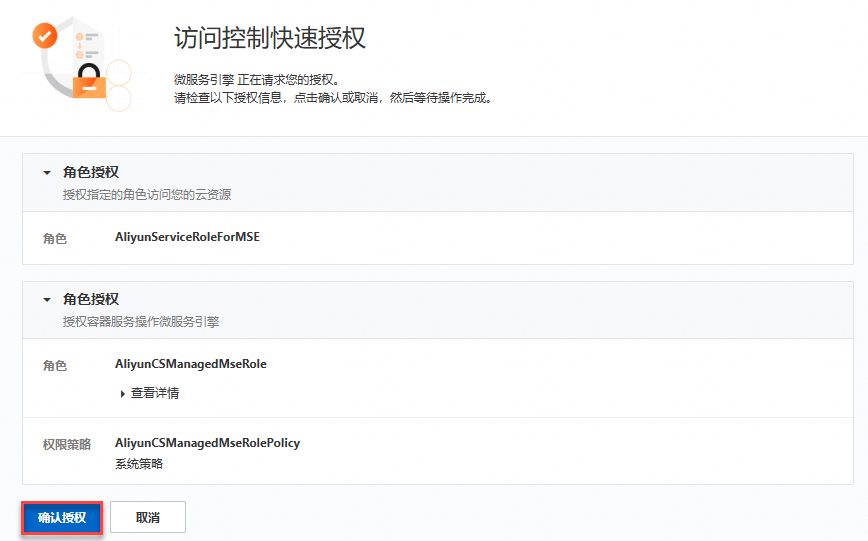
授權完成後,返回確認配置頁面,單擊重新檢查。檢查通過後單擊建立叢集。
後續操作
關於如何在Container Service叢集中通過MSE Ingress訪問服務,請參見通過MSE Ingress訪問Container Service和容器計算服務。