本文以RAM使用者為例介紹如何授權。
操作步驟
使用阿里雲帳號登入RAM控制台。
建立自訂的權限原則。
在左側導覽列,選擇。
在权限策略頁面,單擊创建权限策略。
在创建权限策略頁面,單擊指令碼編輯頁簽。
說明RAM提供可視化編輯和指令碼編輯方式來建立權限原則。建立KMS資源的自訂權限原則時,您需要使用指令碼編輯方式,可視化編輯方式僅支援選擇KMS的全部資源和全部操作。
編輯權限原則指令碼,然後單擊繼續編輯基本資料。
編寫KMS權限原則指令碼時,您需要自訂授權語句,包括效果(Effect)、操作(Action)、資源(Resource)以及條件(Condition,可選項)。更多資訊,請參見附錄:KMS支援的資源(Resource)、操作(Action)、條件(Condition)。
說明關於權限原則文法結構的詳情,請參見權限原則文法和結構。
輸入權限原則名稱和備忘資訊,根據頁面提示檢查並最佳化權限原則內容。
單擊確定。
授予RAM使用者自訂的權限原則。
在左側導覽列,選擇。
在用户頁面,找到目標RAM使用者,在操作列單擊添加許可權。
在新增授權面板,完成如下配置,然後單擊確認新增授權。
配置項
說明
資源範圍
選擇許可權在當前阿里雲帳號生效或者在指定資源群組內生效。目前KMS還未支援資源群組功能,請選擇整個雲帳號。
授權主體
需要授權的RAM使用者。系統自動填入您選擇的RAM使用者,您也可以手動添加其他RAM使用者。
權限原則
根據使用情境選擇自訂的權限原則。
附錄:KMS支援的資源(Resource)、操作(Action)、條件(Condition)
資源(Resource)
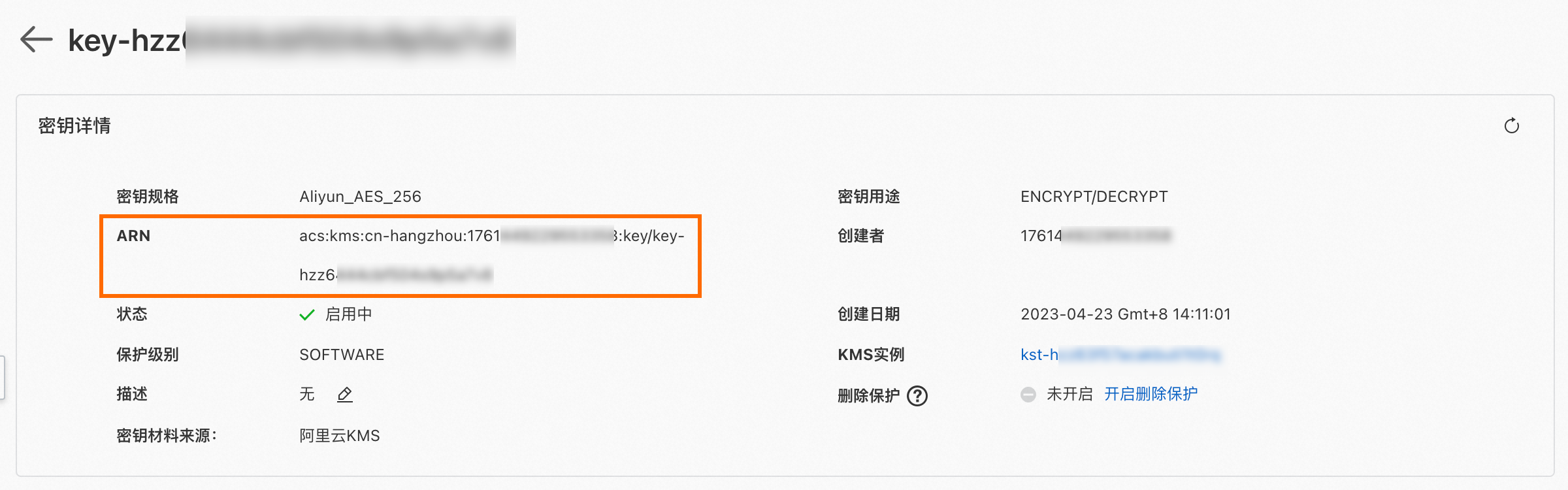
KMS定義的資源類型包括抽象密鑰容器、抽象憑據容器、抽象別名容器、密鑰、憑據、別名,您可以通過以下方式擷取資源對應的資源名稱ARN(Aliyun Resource Names),用於RAM權限原則的Resource元素。例如,查看密鑰的ARN:
登入Key Management Service控制台,在頂部功能表列選擇地區後,在左側導覽列單擊。
在用户主密钥頁簽,定位到目標密鑰,單擊操作列的详情,在密鑰詳情頁面擷取ARN。
 不同資源類型對應的ARN格式不同,具體資訊,如下表所示。說明
不同資源類型對應的ARN格式不同,具體資訊,如下表所示。說明請將
${region}和${account}替換為您實際的地區和阿里雲帳號,您也可以根據需求縮小資源範圍。${region}支援萬用字元*,表示所有支援的地區。資源類型
ARN
抽象密鑰容器
acs:kms:${region}:${account}:key
抽象憑據容器
acs:kms:${region}:${account}:secret
抽象別名容器
acs:kms:${region}:${account}:alias
密鑰
acs:kms:${region}:${account}:key/${key-id}
說明密鑰資源的ARN支援萬用字元*。例如:
acs:kms:${region}:${account}:key/*:表示對應地區和帳號下的所有密鑰。acs:kms:*:${account}:key/*:表示對應帳號下所有地區的所有密鑰。
憑據
acs:kms:${region}:${account}:secret/${secret-name}
說明憑據資源的ARN支援以下兩種通配方式:
acs:kms:${region}:${account}:secret/*:表示對應地區和帳號下的所有憑據。acs:kms:${region}:${account}:secret/prefix*:表示對應地區和帳號下憑據名稱首碼為prefix的所有憑據。
別名
acs:kms:${region}:${account}:alias/${alias-name}
操作(Action)
針對每一個需要進行存取控制的介面,KMS都定義了用於RAM權限原則的操作(Action),通常為kms:<api-name>。
操作DescribeRegions不需要進行存取控制,只要請求可以通過認證校正,即可調用。調用者可以是阿里雲帳號、RAM使用者或RAM角色。
以下表格列出了KMS介面的對應RAM權限原則操作,以及介面所訪問的資源類型。
請將${region}和${account}替換為您實際的地區和阿里雲帳號,您也可以根據需求縮小資源範圍。${region}支援萬用字元*,表示所有支援的地區。