本文介紹應用程式通過SDK接入時可能遇到的問題。
問題列表
訪問KMS執行個體時出現no such host或not known報錯
問題描述
應用程式通過KMS執行個體SDK(Go)訪問KMS執行個體時:返回
kst-xxx.cryptoservice.kms.aliyuncs.com: no such host。應用程式通過KMS執行個體SDK(Java)訪問KMS執行個體時:返回
kst-xxx.cryptoservice.kms.aliyuncs.com: nodename nor servname provided, or not known。
問題原因
購買KMS執行個體後,該執行個體是您獨享的密鑰管理和憑據管理服務,僅可從您已配置關聯的VPC中訪問。
解決方案
如果應用程式所在VPC和KMS執行個體在同一個地區,請將該VPC和KMS執行個體關聯。具體操作,請參見同地區多VPC訪問KMS執行個體。
關於KMS執行個體關聯了哪些VPC,請參見查看KMS執行個體詳情。
如果應用程式所在VPC和KMS執行個體在不同地區,請將該VPC和KMS執行個體所在VPC之間的網路打通。
通過應用存取點訪問KMS執行個體時,出現Forbidden.NoPermission報錯
問題描述
訪問KMS執行個體時,返回的錯誤描述或SDK異常訊息中包含:Forbidden.NoPermission : This operation is forbidden by permission system.
解決方案
應用存取點的權限原則中,RBAC許可權和允許訪問資源中未配置要使用的密鑰或憑據的許可權。具體操作,請參見建立應用存取點。
擷取憑據值時出現This operation for key-xxxxxx is forbidden by permission system報錯
問題描述
擷取憑據值時,KMS返回的錯誤描述或SDK異常訊息中包含:This operation for key-xxxxxx is forbidden by permission system。
以下是KMS執行個體SDK(Java)異常資訊樣本:
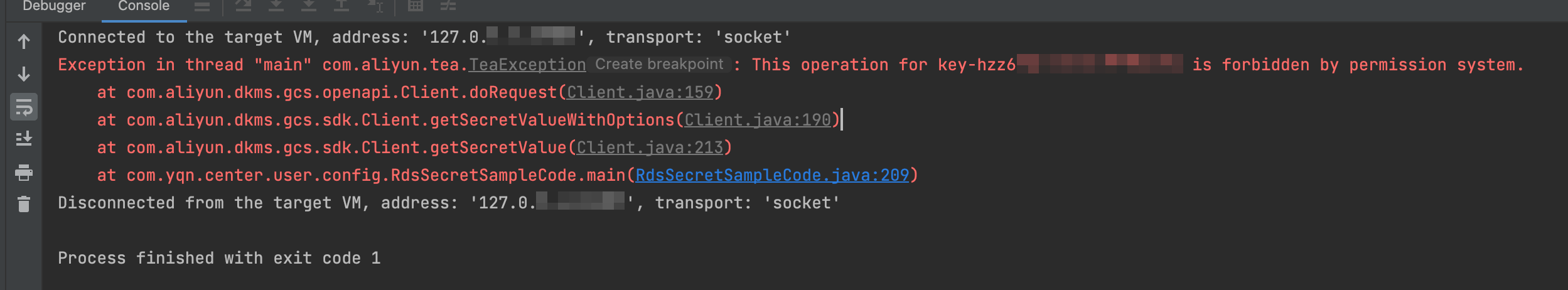
問題原因
應用程式缺少使用該密鑰進行解密的許可權。
建立憑據時需要選擇同一個KMS執行個體下的祕密金鑰加密憑據值。應用程式向KMS請求擷取憑據時,需要使用對應的密鑰解密憑據值,因此應用程式不僅要具有使用憑據的許可權,還需要具有使用對應密鑰進行解密的許可權。
解決方案
情境一:通過應用存取點AAP(ClientKey) 訪問KMS
編輯應用存取點的權限原則,為應用程式增加使用密鑰解密的許可權。
登入Key Management Service控制台,在頂部功能表列選擇地區後,在左側導覽列單擊。
單擊目標應用存取點名稱,進入应用接入点详情頁面。
單擊權限原則操作列的编辑,完成如下配置項的設定後,單擊更新。
RBAC权限:增加勾選CryptoServiceKeyUser。
允许访问的资源:在可选资源地區選取項目密鑰,單擊
 表徵圖。或單擊已选资源後的
表徵圖。或單擊已选资源後的 表徵圖添加密鑰,格式為key/key id(例如key/key-hzz6xxxxxx)。
表徵圖添加密鑰,格式為key/key id(例如key/key-hzz6xxxxxx)。
情境二:通過RAM使用者的AccessKey或RAM角色訪問KMS
編輯RAM權限原則,為應用程式增加使用密鑰解密的許可權。
登入RAM控制台。
在左側導覽列,選擇。
找到您的RAM使用者或RAM角色綁定的權限原則,單擊權限原則名稱。
在策略內容頁簽,單擊修改策略內容,在
Statement中增加如下指令碼後單擊繼續編輯基本資料,然後單擊確定。{ "Effect": "Allow", "Action": "kms:Decrypt", "Resource": "acs:kms:${region}:${account}:key/keyId-example" }關於權限原則的更多資訊,請參見Key Management Service自訂權限原則參考。
訪問或使用密鑰時出現Forbidden.KeyNotFound報錯
原因:通常是因為請求中指定的地區、密鑰ID或別名,與加密時使用的參數不符。
解決方案:確保解密操作所使用的地區、密鑰ID或別名,與加密時完全一致。
調用KMS介面時出現UnsupportedOperation報錯
網路訪問配置錯誤
原因:應用程式調用KMS執行個體中建立的密鑰進行密碼運算時,使用了阿里雲SDK。
解決方案:
登入Key Management Service控制台,在頂部功能表列選擇地區後,在左側導覽列單擊。
在執行個體列表中,單擊目標執行個體ID,在詳情頁面的RD多账号地區,開啟公網訪問開關。
說明當KMS執行個體共用給多個阿里雲帳號時,可針對每個帳號設定公網存取權限。
在基本信息頁簽,查看公網地址。

密鑰類型使用錯誤
原因:應用程式通過SDK調用密碼運算介面(Encrypt、Decrypt或GenerateDataKey)時,使用了服務密鑰。
解決方案:應用程式進行密碼運算時,應直接使用使用者主要金鑰(CMK),而非由其他雲產品代管的服務密鑰。
密鑰演算法與API不匹配
情境一:加解密與資料密鑰產生
調用產生資料密鑰GenerateDataKey介面時,使用者主要金鑰(CMK)的密鑰演算法為RSA、ECC非對稱演算法。
解決方案:請確保使用者主要金鑰(CMK)的密鑰演算法是AES對稱演算法,且密鑰用途為ENCRYPT/DECRYPT。
情境二:簽名與驗簽
訪問KMS執行個體時出現unable to find valid certification path to requested target報錯
可能原因一:下載CA認證時,未選擇正確的KMS執行個體
登入Key Management Service控制台,在頂部功能表列選擇地區後,在左側導覽列單擊。
在实例管理頁面,單擊获取实例CA证书下的下载。
在获取实例CA证书對話方塊中選擇執行個體ID,單擊下载並妥善保管。
CA認證下載後檔案名稱預設為PrivateKmsCA_kst-******.pem,後續會整合到SDK中用於驗證KMS執行個體服務的SSL認證是否真實有效。
可能原因二:SDK安裝包的版本不正確
建議您安裝最新版本的SDK,各SDK的開原始碼倉庫地址:
KMS執行個體的網域名稱無法解析
問題描述
在KMS執行個體所屬的VPC或已關聯的VPC中,應用無法訪問KMS執行個體的網域名稱。例如ping kst-hzz62****.cryptoservice.kms.aliyuncs.com,無法解析網域名稱,提示訊息中包含 "cannot resolve"。
解決方案
請您檢查伺服器的DNS配置是否為預設的100.100.2.136/100.100.2.138。詳細資料,請參見使用PrivateZone需要修改伺服器的DNS配置麼。
應用訪問KMS執行個體時提示ClientKey口令不正確
問題描述
通過KMS執行個體SDK(Java)訪問KMS執行個體時:返回
java.io.IOException: keystore password was incorrect。通過KMS執行個體SDK(PHP)訪問KMS執行個體時:返回
Could not decrypt the privateKey of clientKey, the password is incorrect,or it is not a valid pkcs12。通過KMS執行個體SDK(Go)訪問KMS執行個體時:返回
panic: pkcs12: decryption password incorrect。通過KMS執行個體SDK(Python)訪問KMS執行個體時:返回
OpenSSL.crypto.Error: [('PKCS12 routines', '', 'mac verify failure')]。
問題原因
ClientKey口令(password)不正確。
解決方案
ClientKey口令格式是否滿足要求,不滿足時您需要重新建立ClientKey。具體操作,請參見建立ClientKey。
ClientKey口令格式:8~64位,[0-9] [a-z] [A-Z] [~!@#$%^&*?_-] ,需要滿足兩種類型。
如果通過檔案讀取ClientKey口令,口令檔案應該只是文字檔,只包含一行密碼內容。檔案內容不要包括分行符號,定位字元等不滿足密碼格式的特殊符號。
應用訪問KMS執行個體時返回HTTP 413狀態代碼
所有請求參數使用Protocol Buffers編碼後(即Request Body),內容長度不能超過3 MB,超過後服務端會拒絕處理並返回HTTP 413狀態代碼。
加解密操作:建議單次使用對稱金鑰加解密的資料不超過6 KB,單次使用非對稱金鑰加解密的資料不超過1 KB,超過後請使用信封加密。
簽名驗簽操作:簽名訊息較大時,建議您的應用在本地對訊息產生摘要後,再調用Sign/Verify介面進行簽名或驗簽。
應用訪問KMS執行個體時提示UnknownHostException
問題描述
應用程式通過KMS執行個體SDK(Java)訪問KMS執行個體時:返回Caused by: java.net.UnknownHostException: kst-hzz664da459rvtjtd****.cryptoservice.kms.aliyuncs.com。
解決方案
請確認您應用的環境是否和KMS執行個體VPC網路打通。
如果應用程式的VPC和KMS執行個體在同一地區,請將該VPC綁定到KMS執行個體。具體操作,請參見同地區多VPC訪問KMS執行個體。其他情境您可以參考如下方案。
跨VPC互聯的解決方案
您可以通過使用雲企業網CEN(Cloud Enterprise Network)、VPN網關、VPC對等串連或者私網串連(PrivateLink)這幾種方案實現VPC之間的私網互連。關於這幾種跨VPC互聯解決方案的特點、介紹以及配置方法,請參見VPC互連。
VPC如何串連公網
您可以通過ECS執行個體固定公網IP、Elastic IP Address、NAT Gateway或者負載平衡使Virtual Private Cloud中的雲資源可以訪問公網或被公網訪問。具體操作,請參見公網訪問。
VPC如何串連IDC
您可以通過VPN網關、Express Connect物理專線或Smart Access Gateway將本機資料中心和雲上專用網路打通,構建混合雲。具體操作,請參見VPC串連本機資料中心/其他雲。
請確認是否正確配置了KMS VPC網域名稱解析設定。網域名稱解析設定,請參見內網DNS解析簡介。
安卓端是否支援使用KMS的憑據管理功能
目前不支援安卓端使用憑據管理功能。
KMS的端點(Endpoint)無法訪問
通常是因為在使用SDK訪問KMS時,未啟用HTTPS協議。
為了確保您的資料安全,KMS的端點(Endpoint)僅支援HTTPS協議。因此在使用SDK訪問KMS的端點(Endpoint)時,請執行如下代碼確保KMS已啟用HTTPS協議。
req.setProtocol(ProtocolType.HTTPS);本地IDC無法通過網域名稱訪問KMS執行個體
問題描述
本地IDC與阿里雲VPC進行網路打通,在不做任何配置情況下,本地IDC無法通過PrivateZone配置的網域名稱kms.aliyuncs.com訪問KMS執行個體。
解決方案
在專線路由器上,把100.100.2.136/100.100.2.138這兩段路由允許存取,確保本地IDC可以ping通100.100.2.136/100.100.2.138。專線路由器配置問題可諮詢您的網路PDSA,也可參考相關文檔:雲上雲下網路互連、通過物理專線實現本地IDC與雲上VPC互連、添加和管理路由條目、本地IDC通過專線使用訊息佇列RocketMQ版處理訊息。
重要如果您的IDC不是阿里雲企業網或專線網路,路由器配置需要諮詢您的供應商。
修改本地DNS主設定檔named.conf,將KMS網域名稱(kms.aliyuncs.com)轉寄給雲DNS來進行查詢。設定檔可參考如下:
zone "kms.aliyuncs.com" { type forward; forwarders { 100.100.2.136;100.100.2.138;}; };說明不同的DNS軟體在配置路由轉寄上略有差異,您可根據軟體操作指南完成配置。
ACK通過ack-secret-manager同步KMS憑據時提示QPS Limit Exceeded
問題原因
同步KMS憑據的調用規模較大時 ,會觸發KMS的限流策略,從而發生同步憑據失敗問題。
解決方案
ack-secret-manager的0.5.2版本已修複該問題,請升級至0.5.2及以上版本,建議您升級到最新版本。
通過專屬網關調用OpenAPI進行密碼運算時提示“MissingParamter”
問題描述
使用阿里雲SDK通過專屬網關調用OpenAPI進行密碼運算時,返回MissingParamter AParamter x-kms-acccesskeyid does not exist in http header or body "$430c76cd-******。
問題原因
KMS執行個體的鏡像版本低於3.0.0版本。通過專屬網關調用OpenAPI進行密碼運算,KMS執行個體的鏡像版本需要為3.0.0及以上。
解決方案
請在实例管理頁面的執行個體詳情中查看鏡像版本,單擊升级版本升級KMS執行個體的鏡像版本。詳細介紹,請參見升級KMS執行個體的鏡像版本。
第三方ISV通過專屬網關訪問KMS時,存在認證校正問題
為解決自我簽署憑證引起的認證校正問題,您可以為KMS執行個體開啟公網訪問,使第三方ISV通過共用網關訪問KMS,共用網關是從受信任的憑證授權單位擷取簽署憑證。
登入Key Management Service控制台,在頂部功能表列選擇地區後,在左側導覽列單擊。
在執行個體列表中,單擊目標執行個體ID,在詳情頁面的RD多账号地區,開啟公網訪問開關。
說明當KMS執行個體共用給多個阿里雲帳號時,可針對每個帳號設定公網存取權限。
在基本信息頁簽,查看公網地址。
