當您購買Cloud Firewall按量版後,您可以使用Cloud Firewall的攻擊防護、存取控制策略等功能為您的公網資產進行安全防護。本文介紹Cloud Firewall按量版的完整使用流程(包括接入資產防護、配置防護策略、查看防護效果等),協助您更快地使用Cloud Firewall按量版。
使用流程
前提條件
您已經購買了Cloud Firewall按量版。具體操作,請參見購買Cloud Firewall服務。
步驟一:開啟Cloud Firewall防護
購買Cloud Firewall按量版後,首次登入Cloud Firewall控制台時,系統彈出資產接入對話方塊,您可以單擊自动全量接入公网资产或手动一键接入公网资产,快速接入需要防護的資產。
如果您在購買Cloud Firewall按量版時,選中了自动接入资产保护,後續新增的資產將自動接入Cloud Firewall防護。如果您未啟用自动接入资产保护,您可以在頁面,手動開啟新增資產防護。具體操作,請參見互連網邊界防火牆。

步驟二:配置攻擊防護(IPS)能力
(可選)配置防護規則
Cloud Firewall內建了威脅檢測引擎(IPS),可以對惡意流量入侵活動和常規攻擊行為即時警示或攔截,一般針對木馬後門等惡意檔案、攻擊payload請求行為進行檢測和防護,並提供精準的威脅檢測虛擬補丁,智能阻斷入侵風險。其檢測的運行原理包括利用威脅情報、入侵檢測規則、智能模型演算法識別、虛擬補丁的方式多方位進行檢測。更多資訊,請參見IPS配置。
威脅引擎運行模式分為觀察模式(僅警示)、攔截模式(警示且自動阻斷攻擊payload),針對不同的攻擊類型,Cloud Firewall威脅引擎設計了不同的策略。攔截模式的適用情境如下:
分類 | 適用情境 | 特點 | 樣本 |
寬鬆模式 | 防護粒度較粗,主要覆蓋低誤判規則,適合業務對誤判要求高的情境。 | 明確漏洞利用關鍵字、關鍵參數,有明顯的攻擊報文和行為,無誤判可能性。 | Struts 2遠程代碼執行(CVE-2018-11776)、Spark REST API未授權訪問(CVE-2018-11770)、Jenkins遠程命令執行(CVE-2018-1000861)。 |
中等模式 | 防護粒度介於寬鬆和嚴格之間,適合日常營運的常規規則情境。 | 涉及每種攻擊類型,綜合利用各類漏洞利用分析方式,即為常規規則,基本無誤判的可能性。 | Oracle WebLogic Server遠程代碼執行(CVE-2020-2551)、Microsoft WindowsRDP Client遠程代碼執行(CVE-2020-1374)、SMBv1拒絕服務的攻擊(CVE-2020-1301)。 |
strict 模式 | 防護粒度最精細,主要覆蓋基本全量規則,相比中等規則群組可能誤判更高,適合對安全防護漏報要求高的情境。 | 棧溢出、緩衝區溢位等高危害性,其中絕大部分四層漏洞,需經過協議分析、關鍵字匹配、多次跳轉、關鍵字位移等攻擊確認。 | Squid Proxy HTTP Request Processing緩衝區溢位(CVE-2020-8450)、Nginx 0-Length Headers Leak拒絕服務(CVE-2019-9516)、Oracle WebLogic |
修改防護配置時,建議您優先開啟觀察模式,通過試運行一段時間,分析資料誤攔截情況後,再開啟防護攔截模式功能。
更多入侵防禦使用實踐,請參見:
查看防護結果
您可以在Cloud Firewall控制台的頁面,查看Cloud Firewall對資產的入侵攔截情況,包括攔截流量的源IP、目的IP、阻斷應用、阻斷來源和阻斷事件詳情等。更多資訊,請參見入侵防禦。

步驟三:查看網路流量分析
通過流量分析,您可以即時查看主機發生的主動外聯、公網暴露的詳細資料,進行流量可視化管理,排查異常流量。
主動外聯(出向流量)
您可以通過主動外聯活動頁面展示雲上資產外聯網域名稱、外聯IP資訊,結合情報標籤和訪問詳情及日誌,可對出方向存取控制策略進行查漏補缺。具體操作,請參見主動外聯。
公網暴露(入向流量)
您也可以查看流量公網暴露的雲上開放的服務、連接埠、公網IP地址和雲產品資訊,結合開放公網IP資訊和推薦的智能策略可加強入方向存取控制策略安全水位。具體操作,請參見公網暴露。
流量分析是配置存取控制策略的基礎。建議您在配置存取控制策略前全面瞭解您資產的流量情況。
步驟四:配置存取控制策略
配置存取控制策略
如果您未配置任何策略,Cloud Firewall預設允許存取所有流量。您可以自訂建立互連網邊界防火牆的存取控制策略,實現精細化管控公網資產和互連網之間的未授權訪問。
互連網邊界防火牆存取控制策略的配置方法,請參見配置互連網邊界存取控制策略。
存取控制策略的配置情境樣本,例如只允許公網流量訪問指定連接埠的策略(入方向)、只允許主機訪問指定網域名稱的策略(出方向)、不同VPC內某些ECS之間禁止訪問等,請參見存取控制策略配置樣本。
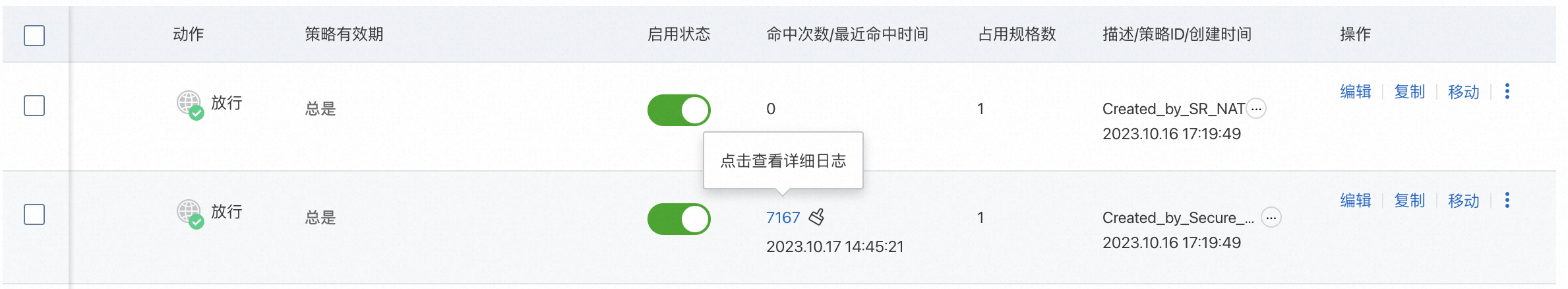
查看存取控制策略命中情況
存取控制策略配置完成後,預設情況下策略立即生效。您可以進入Cloud Firewall控制台的頁面,在存取控制策略列表的叫用次數/最近命中时间列,查看存取控制策略的命中情況。更多資訊,請參見配置互連網邊界存取控制策略。
步驟五:配置警示通知
您可以通過設定警示通知,在出現資產攻擊風險、新增資產等情況時,及時收到通知,以便您瞭解資產狀態,及時處理異常問題,保障資產安全。關於Cloud Firewall支援設定的警示類型以及如何設定,請參見警示通知。
步驟五:查看隨用隨付賬單
Cloud Firewall按量版以天為單位計費,每天18:00統計前一天的費用並進行結算。您可以通過查詢隨用隨付版的賬單詳情,瞭解隨用隨付的明細。
在左側導覽列,選擇。
在账单管理頁面,查看隨用隨付流量使用明細,包括保護的資產資料統計、已開通的防護功能、防護資產的流量資料。
單擊查看账单详情,查看詳細的賬單明細。具體操作,請參見明細賬單。