This topic describes how to connect a third-party SD-WAN appliance to a transit router to establish network communication between data centers and virtual private clouds (VPCs).
Example
A third-party SD-WAN appliance is used in this topic. The information about the third-party SD-WAN appliance is for reference only. Alibaba Cloud does not guarantee or make other form of commitments to the performance and reliability of the third-party tools, or the potential impacts of using these tools.
A company has two data centers (IDC1 and IDC2) and a VPC (VPC1) in the China (Shanghai) region, and another VPC (VPC2) in the China (Hangzhou) region. It now needs to enable communication among IDC1, IDC2, VPC1, and VPC2. A solution that the company proposes is to use a third-party SD-WAN appliance to connect IDC1 and IDC2 to Alibaba Cloud, and implement access control on the third-party SD-WAN appliance to ensure security. In addition, it wants to enable automatic route advertisement and learning between Alibaba Cloud and the data centers to reduce O&M workload.
To achieve these goals, the company can connect the third-party SD-WAN appliance to a transit router by creating a VPN attachment. The data centers can use the third-party SD-WAN appliance and transit router to communicate with the VPCs that are connected to the transit router. Furthermore, Border Gateway Protocol (BGP) is enabled for the transit routers, the third-party SD-WAN appliance, IDC1, and IDC2, which allows for automatic route advertisement and learning.
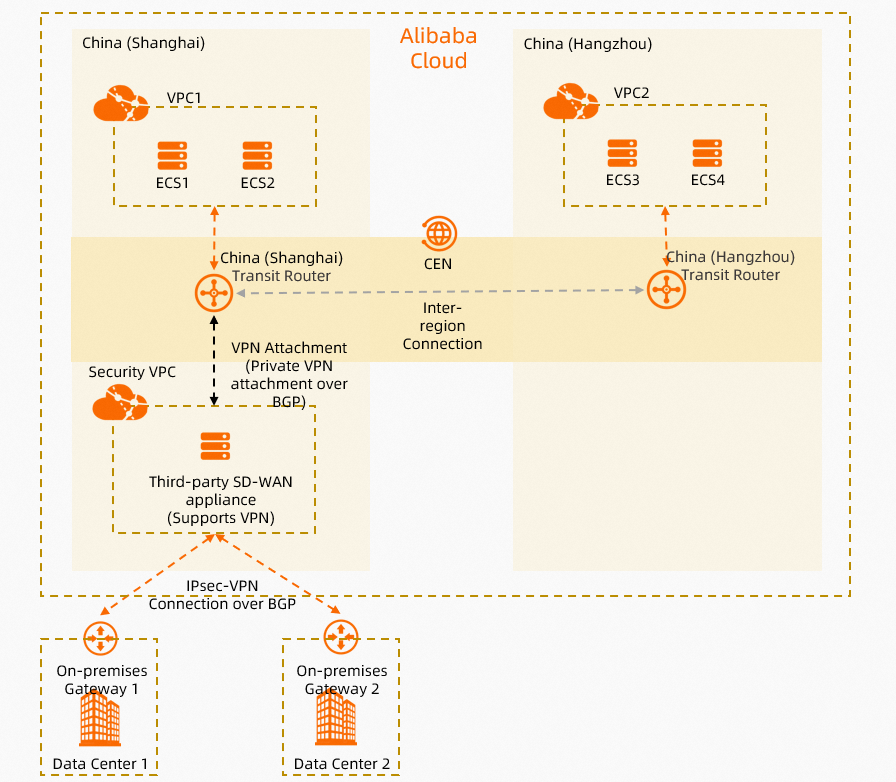
Network planning
Network requirements
Create an Elastic Compute Service (ECS) instance in a VPC, such as the security VPC in this topic. Then, deploy a third-party SD-WAN appliance on the ECS instance by installing the corresponding image.
In this example, the image FortiGate V6.2.4 is installed on the ECS instance in the security VPC.
Connect the third-party SD-WAN appliance to the transit router by creating a VPN attachment that uses a Private VPN gateway.
Enable BGP between the third-party SD-WAN appliance and transit router to allow automatic route advertisement and learning.
Create an IPsec-VPN connection between the third-party SD-WAN appliance and IDC1 and between the third-party SD-WAN appliance and IDC2. This way, IDC1 and IDC2 can connect to Alibaba Cloud.
Use Auto Discovery VPN (ADVPN) to create a full mesh of IPsec-VPN connections between the third-party SD-WAN appliance and IDC1 and IDC2. For more information about ADVPN, see Fortinet Documents Library.
The third-party SD-WAN appliance and the two on-premises gateway devices (On-premises Gateway 1 and On-premises Gateway 2) all use BGP. After an internal BGP (iBGP) neighbor relationship is established, routes are automatically advertised and learned.
Both On-premises Gateway 1 and On-premises Gateway 2 are from Fortinet and have the image FortiGate V6.2.4 installed.
CIDR blocks
Make sure that the CIDR blocks do not overlap with each other.
Table 1. Basic CIDR block configurations
Resource | CIDR block and IP address |
Service VPC (VPC1) |
|
Service VPC (VPC2) |
|
Security VPC |
|
IDC1 |
|
IDC2 |
|
Table 2. BGP configurations
Resource | BGP autonomous system number (ASN) | Local BGP IP address | Peer BGP IP address |
BGP configuration between the third-party SD-WAN appliance and transit router | |||
IPsec-VPN connection | 65531 | 169.254.20.1 | 169.254.20.2 |
Third-party SD-WAN appliance | 65534 | 169.254.20.2 | 169.254.20.1 |
BGP configuration between the third-party SD-WAN appliance and IDC1 | |||
IDC1 | 65534 | 169.254.10.10 | 169.254.10.1 |
Third-party SD-WAN appliance | 65534 | 169.254.10.1 | 169.254.10.10 |
BGP configuration between the third-party SD-WAN appliance and IDC2 | |||
IDC2 | 65534 | 169.254.10.11 | 169.254.10.1 |
Third-party SD-WAN appliance | 65534 | 169.254.10.1 | 169.254.10.11 |
Prerequisites
Make sure that the following prerequisites are met before you begin:
A service VPC (VPC1) and a security VPC are created in the China (Shanghai) region. A service VPC (VPC2) is created in the China (Hangzhou) region. ECS instances are deployed in the VPCs to run workloads. For more information, see Create a VPC with an IPv4 CIDR block.
Deploy workloads on the ECS instances in VPC1 and in VPC2 based on your business requirements.
Install the image that is used to deploy the third-party SD-WAN appliance on the ECS instance in the security VPC. In this example, the image FortiGate V6.2.4 is used. Make sure that the third-party SD-WAN appliance is assigned a public IP address. You can purchase the image from Alibaba Cloud Marketplace. For more information, see Alibaba Cloud Marketplace images.
A Cloud Enterprise Network (CEN) instance is created. For more information, see Create a CEN instance.
Procedures
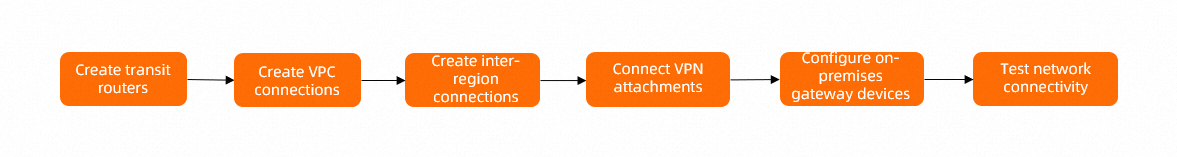
Step 1: Create transit routers
Before you can use a CEN instance to connect data centers to VPCs, you must deploy transit routers in the China (Shanghai) and China (Hangzhou) regions, and assign CIDR blocks to the transit router in the China (Shanghai) region.
Log on to the CEN console.
On the Instances page, select the CEN instance that you created in Prerequisites, and click the CEN instance ID.
On the tab, click Create Transit Router.
In the Create Transit Router dialog box, configure the parameters and click OK. The following table describes the parameters.
The following table lists only the parameters that are closely related to this topic. Other parameters are kept at their default value. For more information, see Transit router CIDR blocks.
Parameter
Description
China (Shanghai)
China (Hangzhou)
Region
Select the region where you want to create the transit router.
In this example, China (Shanghai) is selected.
In this example, China (Hangzhou) is selected.
Edition
The edition of the transit router.
The transit router edition that is supported in the selected region is automatically displayed.
Enable Multicast
Specify whether to enable multicast.
The default setting is used in this example. Multicast is disabled.
Name
Enter a name for the transit router.
In this example, TR-Shanghai is entered.
In this example, TR-Hangzhou is entered.
TR CIDR Block
Specify a CIDR block for the transit router.
You can specify a custom CIDR block. The CIDR block works in a similar way as the CIDR block of the loopback interface on a router. IP addresses within the CIDR block can be assigned to IPsec-VPN connections . For more information, see Transit router CIDR blocks.
In this example, 10.10.10.0/24 is entered.
No CIDR block is specified in this example.
Step 2: Connect the VPCs to the transit routers
To allow the data centers to communicate with the VPCs by using the transit routers, connect VPC1, the security VPC, and VPC2 to the transit router in the desired region.
On the Instances page, select the CEN instance that you created in Prerequisites, and click the CEN instance ID.
On the tab, find the transit router instance that you created in Step 1, and click Actions in the Create Connection column.
On the Connection with Peer Network Instance page, configure the VPC connection based on the following information, and then click OK.
The following table lists only the parameters that are closely related to this topic. Other parameters are kept at their default value. For more information, see Transit router CIDR blocks.
Parameter
Description
Service VPC (VPC1)
Security VPC
Service VPC (VPC2)
Instance Type
Select the type of network instance.
In this example, VPC is selected.
In this example, VPC is selected.
In this example, VPC is selected.
Region
Select the region of the network instance.
In this example, China (Shanghai) is selected.
In this example, China (Shanghai) is selected.
In this example, China (Hangzhou) is selected.
Transit Router
The transit router in the selected region is automatically displayed.
Resource Owner UID
Specify whether the network instance belongs to the current Alibaba Cloud account.
In this example, Current Account is selected.
In this example, Current Account is selected.
In this example, Current Account is selected.
Billing Method
The billing method of the VPC connection. Default value: Pay-as-you-go. For more information about the billing rules of transit routers, see Billing rules.
Connection Name
Enter a name for the VPC connection.
In this example, Service VPC1 connection is entered.
In this example, Security VPC connection is entered.
In this example, Service VPC2 connection is entered.
Network Instance
Select a network instance.
In this example, VPC1 is selected.
In this example, the security VPC is selected.
In this example, VPC2 is selected.
vSwitch
Select the vSwitches that are deployed in the zones of the transit router.
If the Enterprise Edition transit router is deployed in a region that supports only one zone, select a vSwitch in the zone.
If the Enterprise Edition transit router is deployed in a region that supports multiple zones, select at least two vSwitches. The two vSwitches must be in different zones. The two vSwitches support zone-disaster recovery to ensure uninterrupted data transmission between the VPC and the transit router.
We recommend that you select a vSwitch in each zone to reduce network latency and improve network performance because data can be transmitted over a shorter distance.
Make sure that each selected vSwitch has at least one idle IP address. If the VPC does not have a vSwitch in the zone supported by the TR or the vSwitch does not have an idle IP address, create a new vSwitch in the zone. For more information, see Create and manage a vSwitch.
In this example, vSwitch 1 in Shanghai Zone F and vSwitch 2 in Shanghai Zone G are selected.
In this example, vSwitch 1 in Shanghai Zone F and vSwitch 2 in Shanghai Zone G are selected.
In this example, vSwitch 1 in Hangzhou Zone I and vSwitch 2 in Hangzhou Zone H are selected.
Advanced Configuration
Specify whether to enable the advanced features.
In this example, the default settings are used. The advanced features are enabled.
In this example, the default settings are used. The advanced features are enabled.
In this example, the default settings are used. The advanced features are enabled.
Step 3: Create an inter-region connection
As VPC1 and the security VPC are deployed in the same region, they can communicate with each other by default. The transit routers to which VPC1 and VPC2 are attached are in different regions. Therefore, VPC1 and the security VPC cannot communicate with VPC2. To enable communication between them, you must create an inter-region connection between the transit routers deployed in China (Hangzhou) and China (Shanghai).
On the CEN Instance page, find the CEN instance you want to manage, and click the ID.
On the tab, click Allocate Bandwidth for Inter-region Communication.
On the Connect with Peer Network Instance page, configure the following parameters, and then click OK.
Set the parameters by referring to the following table and keep other parameters at their default values. For more information, see Create an inter-region connection.
Parameter
Description
Instance Type
Select Inter-region Connection.
Region
Select the region to be connected.
In this example, China (Hangzhou) is chosen.
Transit Router
The ID of the transit router in the selected region is automatically displayed.
Connection Name
Enter a name for the inter-region connection.
In this example, Inter-region connection is entered.
Peer Region
Select the other region to be connected.
In this example, China (Shanghai) is selected.
Transit Router
The ID of the transit router in the selected region is automatically displayed.
Bandwidth Plan
The following modes are supported:
Allocate from Bandwidth Plan: Allocate bandwidth from the purchased bandwidth plan.
Pay-by-data Transfer: Charged by traffic used by the inter-region connection.
In this example, Pay-by-data Transfer is selected.
Bandwidth
Specify a bandwidth value for the inter-region connection. Unit: Mbit/s.
Default Link Type
Use the default link type.
Advanced Configuration
Keep the default value, with all advanced features enabled.
Step 4: Create VPN attachments
After you complete the preceding steps, VPC1, VPC2, and the security VPC can communicate with each other. However, the transit routers and the security VPC cannot learn routes from the data centers. To enable the third-party SD-WAN appliance to learn routes, you must create a VPN attachment between the third-party SD-WAN appliance and the transit routers, and between the third-party SD-WAN appliance and the data centers. Then, the third-party SD-WAN appliance can advertise routes to the transit routers over the VPN attachment.
Log on to the VPN Gateway console.
Create a customer gateway.
Before you can create VPN attachments between the third-party SD-WAN appliance and the transit routers, you must deploy a customer gateway and register the third-party SD-WAN appliance on Alibaba Cloud.
In the left-side navigation pane, choose .
In the top navigation bar, select the region of the customer gateway.
Select the region in which the third-party SD-WAN appliance is deployed. In this example, China (Shanghai) is selected.
On the Customer Gateway page, click Create Customer Gateway.
In the Create Customer Gateway panel, configure the parameters, and click OK.
The following table lists only the parameters that are closely related to this topic. You can keep other parameters at their default value. For more information, see Create and manage a customer gateway.
Parameter
Description
Customer gateway
Name
Enter a name for the customer gateway.
In this example, Customer-Gateway is entered.
IP Address
Enter the IP address that the third-party SD-WAN appliance uses to create the VPN attachments.
In this example, the private IP address 172.16.0.15 of the third-party SD-WAN appliance is entered.
ASN
Enter the BGP ASN used by the third-party SD-WAN appliance.
In this example, 65534 is entered.
Create an IPsec-VPN connection.
After you create a customer gateway, you need to create an IPsec-VPN connection on Alibaba Cloud. The transit routers use the IPsec-VPN connection to connect to the third-party SD-WAN appliance.
In the left-side navigation pane, choose .
In the top menu bar, select the region of the IPsec-VPN connection.
The IPsec-VPN connection and the customer gateway must be created in the same region. In this example, China (Shanghai) is selected.
On the IPsec-VPN connection page, click Create IPsec-VPN Connection.
On the Create IPsec-VPN Connection page, configure the parameters for the IPsec-VPN connection and click OK. The following table describes the parameters.
Creating an IPsec-VPN connection incurs charges. For more information about the billing of IPsec-VPN connections, see Billing description.
Parameter
Description
IPsec-VPN connection
Name
Enter a name for the IPsec-VPN connection.
In this example, IPsec connection is entered.
Associated Resource
Select the type of network resource to be associated with the IPsec-VPN connection.
In this example, CEN is selected.
Gateway Type
Select the type of gateway used by the IPsec-VPN connection.
In this example, Private is selected.
The security VPC is already connected to the transit router. The third-party SD-WAN appliance can connect to the transit router over a private network connection.
CEN Instance ID
Select a CEN instance.
In this example, the CEN instance that you created in Prerequisites is selected.
Transit Router
Select the transit router that you want to associate with the IPsec-VPN connection.
The transit router in the region of the IPsec-VPN connection is automatically selected.
Zone
Select the zone in which the IPsec-VPN connection is created. Make sure that the IPsec-VPN connection is created in a zone that supports transit routers.
In this example, Shanghai Zone F is selected.
Routing Mode
Select a routing mode.
In this example, Destination Routing Mode is selected.
Effective Immediately
Specify whether to immediately start IPsec negotiations. Valid values:
Yes: immediately starts IPsec negotiations after the configurations take effect.
No: starts negotiations when traffic is detected.
In this example, Yes is selected.
Customer Gateway
Select the customer gateway to be associated with the IPsec-VPN connection.
In this example, Customer-Gateway is selected.
Pre-shared Key
Enter a pre-shared key that is used to authenticate the on-premises gateway devices.
The key must be 1 to 100 characters in length, and can contain digits, letters, and the following special characters:
~ ` ! @ # $ % ^ & * ( ) _ - + = { } [ ] \ | ; : ' , . < > / ?. The key cannot contain spaces.If you do not specify a pre-shared key, the system randomly generates a 16-character string as the pre-shared key. After an IPsec-VPN connection is created, you can click Edit in the Actions column of the IPsec-VPN connection to view the pre-shared key that is generated for the IPsec-VPN connection. For more information, see the Modify an IPsec-VPN connection section of this topic.
ImportantThe IPsec-VPN connection and peer gateway device must use the same pre-shared key. Otherwise, the system cannot establish an IPsec-VPN connection.
In this example, fddsFF123**** is entered.
Enable BGP
Specify whether to enable BGP. By default, BGP is disabled.
In this example, BGP is enabled.
Local ASN
Enter the ASN of the IPsec-VPN connection. Default value: 45104. Valid values: 1 to 4294967295.
In this example, 65531 is entered.
Encryption Setting
Specify custom encryption configurations, including IKE configurations and IPsec configurations.
Configure the following parameters. Keep other parameters at default values.
In the IKE Configurations, select des as the Encryption Algorithm.
In the IPsec Configurations, select des as the Encryption Algorithm.
NoteYou need to select encryption parameters based on the on-premises gateway device to ensure that the encryption configurations for the IPsec connection are the same as those for the on-premises gateway device.
BGP Configuration
Tunnel CIDR Block
Enter the CIDR block that is used for IPsec tunneling.
The CIDR block must fall within 169.254.0.0/16. The mask of the CIDR block must be 30 bits in length.
The CIDR block must fall into 169.254.0.0/16. The subnet mask of the CIDR block must be 30 bits in length. The CIDR block cannot be 169.254.0.0/30, 169.254.1.0/30, 169.254.2.0/30, 169.254.3.0/30, 169.254.4.0/30, 169.254.5.0/30, or 169.254.169.252/30.
In this example, 169.254.20.0/30 is entered.
Local BGP IP address
Enter a BGP IP address for the IPsec-VPN connection.
This IP address must fall within the CIDR block of the IPsec tunnel.
In this example, 169.254.20.1 is entered.
Advanced Settings
Enable or disable the advanced features for the IPsec-VPN connection.
In this example, the advanced features are enabled.
After the IPsec-VPN connections are created, the system assigns a gateway IP address to each IPsec-VPN connection. The gateway IP address is an endpoint on the Alibaba Cloud side of the IPsec-VPN connection. You can view the gateway IP address on the details page of the IPsec-VPN connection, as shown in the following figure.
 Note
NoteThe system assigns gateway IP addresses to IPsec-VPN connections only after you associate the IPsec-VPN connections with transit routers. If the Associated Resource type of the IPsec-VPN connection is set to Not Bound or VPN Gateway when you create the IPsec-VPN connection, the system does not assign a gateway IP address to the IPsec-VPN connection.
After a private IPsec-VPN connection is associated with a transit router, the system automatically advertises the gateway IP address of the IPsec-VPN connection to the route table of the transit router.
Download the configurations of the IPsec-VPN connection peer.
Return to the IPsec-VPN Connections page, find the IPsec-VPN connection that you created, and click Download Peer Configuration in the Actions column.
Add VPN and BGP configurations on the third-party SD-WAN appliance.
After you create the IPsec-VPN connections, add VPN and BGP configurations on the third-party SD-WAN appliance based on the IPsec peer configurations and the following steps to create a VPN attachment between the third-party SD-WAN appliance and transit routers:
NoteIn this example, a FortiGate firewall of v6.2.4 is used as an example. As the commands may vary with software versions, you can consult the firewall vendor or refer to their documents based on your actual environment. For more configuration examples, see On-premises gateway device configuration examples.
The following content contains third-party product information, which is only for reference. Alibaba Cloud does not guarantee or make any form of commitments to the performance and reliability of these products, or the potential impacts of operations performed by using these products.
Open the command-line interface (CLI) on the third-party SD-WAN appliance.
Add configurations of IPsec-VPN phase 1 negotiation for the third-party SD-WAB appliance (IKE settings).
# Add the IPsec-VPN phase 1 configuration for tunnel 1 config vpn ipsec phase1-interface edit "to_aliyun_test1" set interface "port1" # Use port1 to establish a VPN connection to the transit router. set ike-version 2 set peertype any set net-device disable set proposal des-sha1 # Configure the phase 1 encryption algorithm and authentication algorithm. The settings must be consistent with the phase 1 configuration (IKE configuration) on the IPsec-VPN connection side. set localid-type address # Specify the format of the local ID as an IP address, which must be consistent with the format of the Remote ID on the Alibaba Cloud IPsec-VPN connection. set dhgrp 2 # Configure the phase 1 DH group. The settings must be consistent with the phase 1 configuration (IKE configuration) on the IPsec-VPN connection side. set remote-gw 192.168.168.1 # Specify the IP address of the peer of the third-party SD-WAN appliance, which is the gateway IP address of the IPsec-VPN connection. set psksecret fddsFF123**** # Specify the pre-shared key of the tunnel. The pre-shared key on the Alibaba Cloud IPsec-VPN connection side and the third-party SD-WAN appliance side must be consistent. next endAdd configurations of IPsec-VPN phase 2 negotiation for the third-party SD-WAS appliance (IPsec settings).
# Add the IPsec-VPN phase 2 configuration for the tunnel config vpn ipsec phase2-interface edit "to_aliyun_test1" set phase1name "to_aliyun_test1" # Associate the tunnel with the phase1-interface. set proposal des-sha1 # Configure the phase 2 encryption algorithm and authentication algorithm. The settings must be consistent with the phase 2 configuration (IPsec configuration) on the IPsec-VPN connection side. set dhgrp 2 # Configure the phase 2 DH group. The settings must be consistent with the phase 2 configuration (IPsec configuration) on the IPsec-VPN connection side. set auto-negotiate enable set keylifeseconds 86400 # Configure the security association lifetime. next endConfigure BGP IP addresses for the tunnel interface.
config system interface edit "to_aliyun_test1" set ip 169.254.20.2 255.255.255.255 # Configure the BGP IP address of the tunnel interface. set type tunnel # Specify the tunnel port type. set remote-ip 169.254.20.1 255.255.255.255 # Specify the peer BGP IP address of the tunnel. set interface "port1" # Associate the tunnel with port1. next endConfigure firewall policies.
config firewall policy edit 1 set name "forti_to_aliyun1" # Configure the security policy from the third-party SD-WAN appliance to Alibaba Cloud. set srcintf "port1" # The source interface is port1. set dstintf "to_aliyun_test1" # The destination interface is the VPN connection tunnel interface. set srcaddr "all" # Match traffic from all source CIDR blocks. set dstaddr "all" # Match traffic to all destination CIDR blocks. set action accept # Allow traffic. set schedule "always" set service "ALL" next edit 2 set name "aliyun_to_forti1" # Configure the security policy from Alibaba Cloud to the third-party SD-WAN appliance. set srcintf "to_aliyun_test1" # The source interface is the VPN connection tunnel interface. set dstintf "port1" # The destination interface is port1. set srcaddr "all" # Match traffic from all source CIDR blocks. set dstaddr "all" # Match traffic to all destination CIDR blocks. set action accept # Allow traffic. set schedule "always" set service "ALL" next endConfigure BGP dynamic routing.
config router bgp set as 65534 set router-id 172.16.0.15 config neighbor edit "169.254.20.1" # Specify the peer BGP neighbor of the tunnel. set remote-as 65531 next end config network edit 1 set prefix 172.16.0.0 255.255.0.0 # Advertise the CIDR block in the security VPC that needs to communicate with other networks. next end end
Step 5: Configure the on-premises gateway devices
You need to add VPN and BGP configurations on On-premises Gateway 1, On-premises Gateway 2, and the third-party SD-WAN appliance. Then, On-premises Gateway 1, On-premises Gateway 2, and the third-party SD-WAN appliance can establish IPsec-VPN connections among each other and enable IDC1 and IDC2 to communicate with the VPCs and IDC1 to communicate with IDC2. You can refer to the following configuration examples.
Use Auto Discovery VPN (ADVPN) to create a full mesh of IPsec-VPN connections between the third-party SD-WAN appliance and IDC1 and IDC2. For more information about ADVPN, see Fortinet Documents Library.
In this example, a FortiGate firewall of v6.2.4 is used as an example. As the commands may vary with software versions, you can consult the firewall vendor or refer to their documents based on your actual environment. For more configuration examples, see On-premises gateway device configuration examples.
Third-party SD-WAN appliance
Make sure that UDP ports 500 and 5000 on the third-party SD-WAN appliance allow access from the public IP addresses of On-premises Gateway 1 and On-premises Gateway 2. For more information, see Add a security group rule.
Open the CLI on the third-party SD-WAN appliance.
Run the following command to add the IPsec-VPN phase 1 configuration.
config vpn ipsec phase1-interface edit "HUB" # Specify the third-party SD-WAN appliance as the hub. set type dynamic set interface "port1" # Use port1 to establish an IPsec-VPN connection to the data centers. set ike-version 2 # Specify IKEv2. set peertype any set net-device disable # Disable this feature. set proposal des-sha1 # Configure the phase 1 encryption algorithm and authentication algorithm. set add-route disable # Disable automatic route adding. set dpd on-idle set wizard-type hub-fortigate-auto-discovery set auto-discovery-sender enable # Enable this feature on the hub to receive and send spoke-to-spoke tunneling information. set network-overlay enable set network-id 1 set psksecret fddsFF456**** # Specify the pre-shared key. set dpd-retryinterval 60 next endRun the following command to add the IPsec-VPN phase 2 configuration.
config vpn ipsec phase2-interface edit "HUB" set phase1name "HUB" set proposal des-sha1 # Configure the phase 2 encryption algorithm and authentication algorithm. next endRun the following command to configure the IPsec-VPN tunnel IP address.
config system interface edit "HUB" set vdom "root" set ip 169.254.10.1 255.255.255.255 # Configure the tunnel IP address. set allowaccess ping set type tunnel # Specify the tunnel port type. set remote-ip 169.254.10.254 255.255.255.0 # Specify the peer IP address of the tunnel. set interface "port1" # Associate the tunnel with port1. next endImportant169.254.10.254 is a reserved IP address that is not used by spokes. An IPsec-VPN tunnel is a point-to-point tunnel. However, an ADVPN tunnel uses a hub-spoke distribution model. Therefore, you cannot set remote-ip to the IP address of a spoke.
Run the following command to configure security policies on the third-party SD-WAN appliance to allow communication between the data centers and between the data centers and Alibaba Cloud.
config firewall policy edit 7 set name "HUB_to_SPOKE" set srcintf "port1" "HUB" "to_aliyun_test1" # The source interfaces are port1, HUB, and to_aliyun_test1. set dstintf "HUB" "port1" "to_aliyun_test1" # The destination interfaces are port1, HUB, and to_aliyun_test1. set action accept # Allow traffic. set srcaddr "all" # Match traffic from all source CIDR blocks. set dstaddr "all" # Match traffic to all destination CIDR blocks. set schedule "always" set service "ALL" next endRun the following command to add BGP configurations.
config router bgp set as 65534 # Specify 65534 as the BGP ASN of the third-party SD-WAN appliance. config neighbor-group # Enable the neighbor-group attribute. edit "HUB_group" set next-hop-self enable set remote-as 65534 # Specify the peer BGP ASN. set additional-path send set route-reflector-client enable # Enable the route reflector feature and specify the third-party SD-WAN appliance as the route reflector. next end config neighbor-range edit 1 set prefix 169.254.10.0 255.255.255.0 # Specify that BGP neighbors who match the prefix list 169.254.10.0/24 can establish iBGP neighbor relationship with the hub. set neighbor-group "HUB_group" next end end
On-premises Gateway 1
Open the CLI on the on-premises Gateway 1.
Configure a default route to enable on-premises Gateway 1 to reach the public IP address of the third-party SD-WAN appliance.
# Example: Port1 interface is associated with the public IP address 121.XX.XX.211. Set the default route to the Port1 gateway. config router static edit 1 set device "port1" set distance 5 set gateway 192.168.100.253 next end # To check the routing information, execute the command below. FortiGate-VM64-KVM # get router info routing-table all S* 0.0.0.0/0 [5/0] via 192.168.100.253, port1Run the following command to configure phase 1 of the IPsec-VPN.
config vpn ipsec phase1-interface edit "hz_sp" set interface "port1" # Establish IPsec-VPN connection via port1 to the third-party SD-WAN appliance. set ike-version 2 # Use IKEv2. set peertype any set net-device disable # Disable net-device feature. set proposal des-sha1 # Set phase 1 encryption and authentication algorithms. set localid "hzoffice1" set dpd on-idle set wizard-type spoke-fortigate-auto-discovery set auto-discovery-receiver enable # Enable auto-discovery receiver for spoke-to-spoke tunneling. set network-overlay enable set network-id 1 set remote-gw 42.XX.XX.129 # Define the public IP address of the hub. set psksecret fddsFF456**** # Enter the pre-shared key, matching the hub's key. set add-route disable # Turn off automatic route addition. next endEnter the following command to add phase 2 configuration for the IPsec-VPN.
config vpn ipsec phase2-interface edit "hz_sp" set phase1name "hz_sp" set proposal des-sha1 # Define phase 2 encryption and authentication algorithms. set auto-negotiate enable # Activate auto-negotiation. next endUse the command below to specify the IP address for the IPsec-VPN tunnel.
config system interface edit "hz_sp" set vdom "root" set ip 169.254.10.10 255.255.255.255 # Assign the tunnel IP address. set allowaccess ping set type tunnel # Designate the interface as a tunnel. set remote-ip 169.254.10.254 255.255.255.0 # Define the tunnel's peer IP address. set interface "port1" # Link the tunnel to port1. next end config system interface # Create a loopback interface to represent a client in IDC1. edit "loopback" set vdom "root" set ip 192.168.254.100 255.255.255.0 set allowaccess ping set type loopback next endRun the following command to establish security policies on on-premises Gateway 1, which enables communication between data centers and between data centers and Alibaba Cloud.
config firewall policy edit 3 set name "hz_sp_remote" # Set the security policy for IDC1. set srcintf "hz_sp" "loopback" "port1" # Source interfaces include port1, hz_sp, and loopback. set dstintf "loopback" "hz_sp" "port1" # Destination interfaces include port1, hz_sp, and loopback. set action accept # Permit the traffic flow. set srcaddr "all" # Allow all source CIDR blocks. set dstaddr "all" # Allow all destination CIDR blocks. set schedule "always" set service "ALL" next endRun the following command to add BGP configurations.
config router bgp set as 65534 # Define the BGP ASN for on-premises Gateway 1. set network-import-check disable # Turn off route advertisement validation. config neighbor edit "169.254.10.1" # Initiate iBGP relationship with the third-party SD-WAN appliance. set remote-as 65534 # Set the BGP ASN for the third-party SD-WAN appliance. set additional-path receive next end config network edit 1 set prefix 192.168.254.100 255.255.255.255 # Advertise the client address in IDC1 for VPC and IDC2 connectivity. next end end
On-premises Gateway 2
Open the CLI on the On-premises Gateway 2.
Add a default route to enable On-premises Gateway 1 to access the public IP address of the third-party SD-WAN appliance.
# Example: Port1 is associated with public IP 121.XX.XX.78. Set the default route to the Port1 gateway. config router static edit 1 set device "port1" set distance 5 set gateway 192.168.99.253 next end # To check the routing information, execute: FortiGate-VM64-KVM # get router info routing-table all S* 0.0.0.0/0 [5/0] via 192.168.99.253, port1Run this command to configure IPsec-VPN phase 1 parameters.
config vpn ipsec phase1-interface edit "hz_sp1" set interface "port1" # Establish IPsec-VPN via port1 to the SD-WAN appliance. set ike-version 2 # Use IKEv2. set peertype any set net-device disable # Disable net-device. set proposal des-sha1 # Set phase 1 encryption and authentication algorithms. set localid "hzoffice2" set dpd on-idle set wizard-type spoke-fortigate-auto-discovery set auto-discovery-receiver enable # Enable auto-discovery for spoke-to-spoke tunneling. set network-overlay enable set network-id 1 set remote-gw 42.XX.XX.129 # Define the hub's public IP. set psksecret fddsFF456**** # Enter the matching pre-shared key. set add-route disable # Turn off automatic route addition. next endRun the following command to set up IPsec-VPN phase 2 parameters.
config vpn ipsec phase2-interface edit "hz_sp1" set phase1name "hz_sp1" set proposal des-sha1 # Set phase 2 encryption and authentication algorithms. set auto-negotiate enable # Enable auto-negotiation. next endUse this command to assign the IPsec-VPN tunnel IP address:
config system interface edit "hz_sp1" set vdom "root" set ip 169.254.10.11 255.255.255.255 # Set the tunnel IP address. set allowaccess ping set type tunnel # Define tunnel interface type. set remote-ip 169.254.10.254 255.255.255.0 # Specify the tunnel's peer IP address. set interface "port1" # Link the tunnel to port1. next end config system interface # Create a loopback for a simulated IDC2 client. edit "loopback" set vdom "root" set ip 192.168.100.104 255.255.255.0 set allowaccess ping set type loopback endRun the following command to configure security policies on On-premises Gateway 2, which enable communication between data centers and between data centers and Alibaba Cloud.
config firewall policy edit 3 set name "hz_sp1_remote" # Set the IDC2 security policy. set srcintf "hz_sp1" "loopback" "port1" # Source interfaces: port1, hz_sp1, loopback. set dstintf "loopback" "hz_sp1" "port1" # Destination interfaces: port1, hz_sp1, loopback. set action accept # Permit traffic flow. set srcaddr "all" # Include all source CIDR blocks. set dstaddr "all" # Include all destination CIDR blocks. set schedule "always" set service "ALL" next endRun the following command to add BGP configurations.
config router bgp set as 65534 # Assign the BGP ASN for On-premises Gateway 2. set network-import-check disable # Turn off route advertisement verification. config neighbor edit "169.254.10.1" # Set up iBGP with the SD-WAN appliance. set remote-as 65534 # Define the appliance's BGP ASN. set additional-path receive next end config network edit 1 set prefix 192.168.254.104 255.255.255.255 # Advertise the IDC2 client address for VPC and IDC1 connectivity. next end end
Step 6: Test the connectivity
After you complete the preceding steps, the data centers are connected to the VPCs. This step shows how to test network connectivity among the data centers and the VPCs.
Before running the connectivity tests, make sure that you understand the security group rules for the ECS instances in the VPCs and the access control policies in the data centers. Ensure that these rules and policies permit communication among the data centers, between the data centers and ECS instances, and among the ECS instances. For more information about security group rules, see View security group rules and Add a security group rule.
Test the connectivity between IDC1 and VPC1, VPC2, and IDC2.
Open the CLI in the IDC1 client.
Run the ping command from the client to test connectivity with ECS1 in VPC1, ECS1 in VPC2, and a client in IDC2.
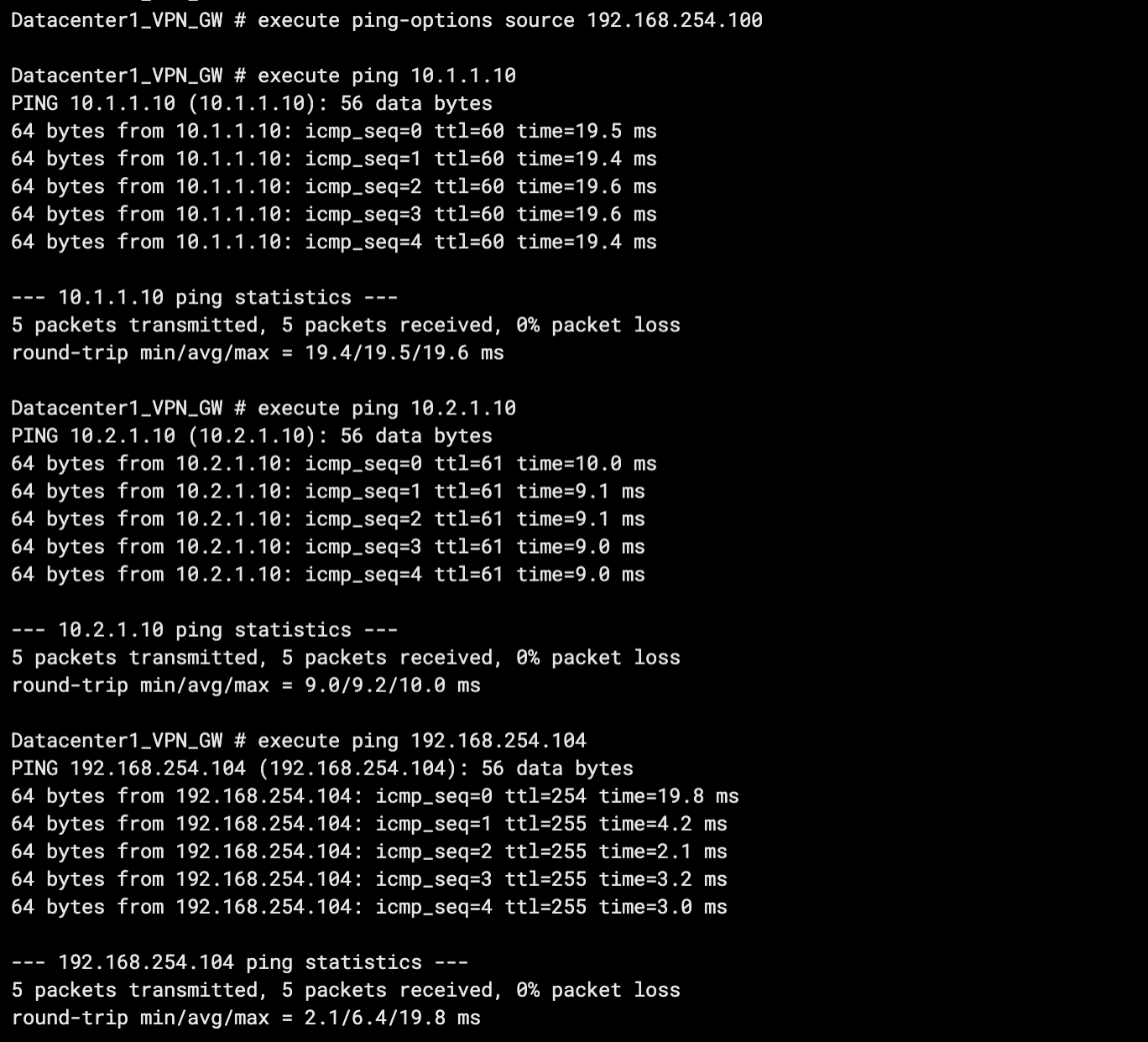 As shown in the preceding figure, if IDC1 gets returned messages, it means IDC1 can access resources in VPC1, VPC2, and IDC2.
As shown in the preceding figure, if IDC1 gets returned messages, it means IDC1 can access resources in VPC1, VPC2, and IDC2.
Test the connectivity between IDC2 and VPC1, VPC2, and IDC1.
Open the CLI of the client in IDC2.
Run the ping command from the client to test connectivity with ECS1 in VPC1, ECS1 in VPC2, and a client in IDC1.
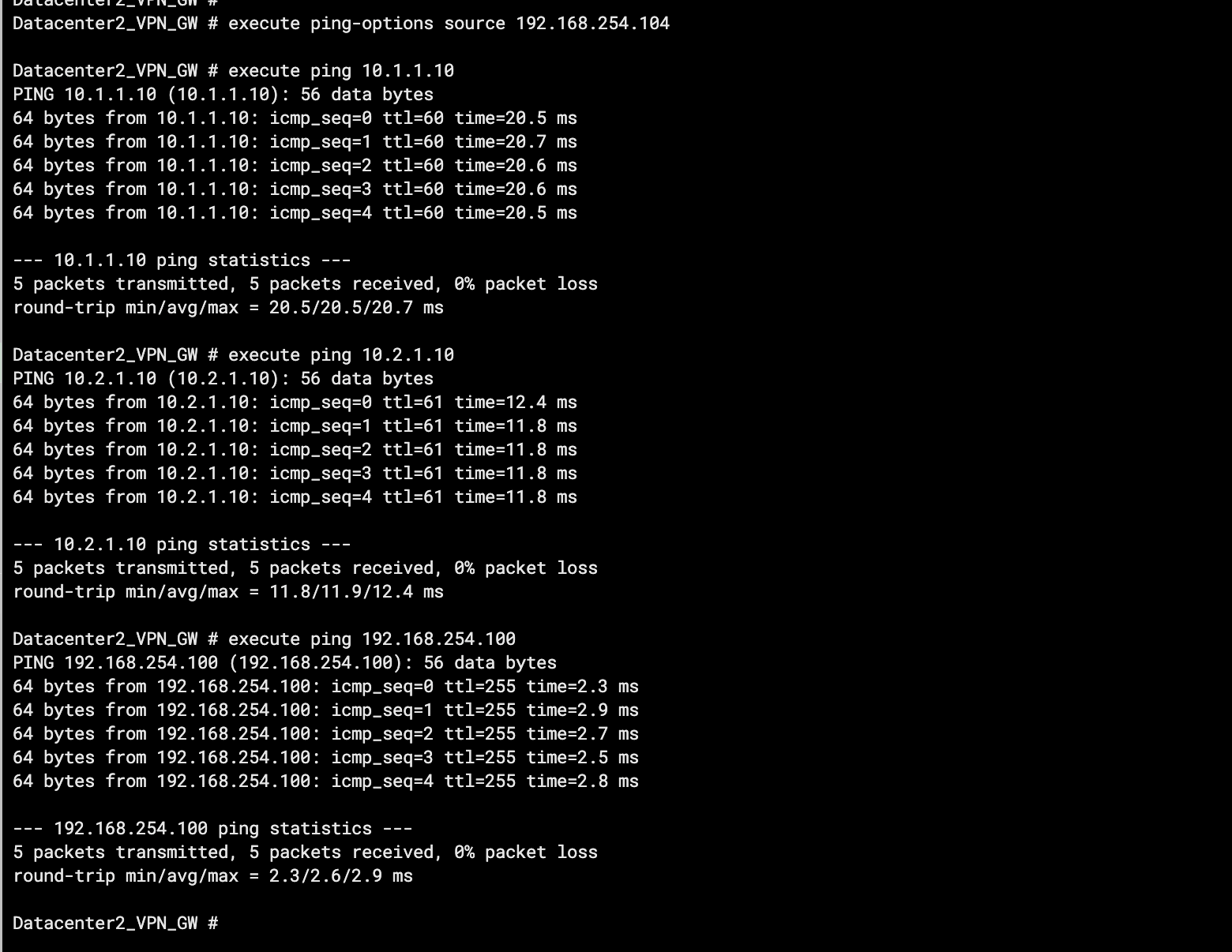 As shown in the preceding figure, if IDC2 gets the returned messages, it means IDC2 can access resources in VPC1, VPC2, and IDC1.
As shown in the preceding figure, if IDC2 gets the returned messages, it means IDC2 can access resources in VPC1, VPC2, and IDC1.
Test the connectivity between VPC1 and two IDCs.
Log on to the ECS1 instance in VPC1. For more information, see ECS remote connection guide.
Run the ping command on the ECS1 instance to test connectivity with clients in IDC1 and IDC2.
ping <IP address of the IDC client>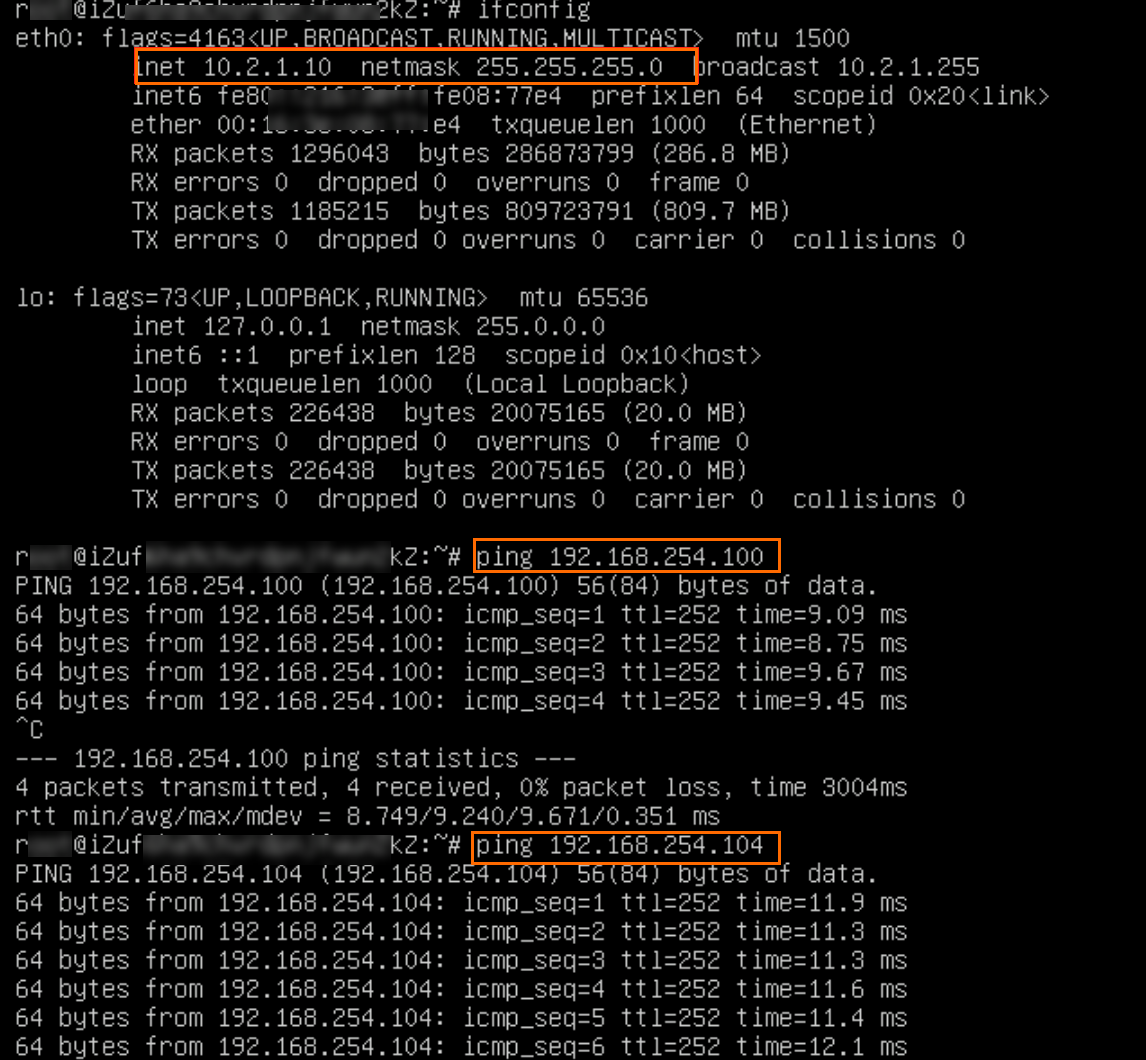
The preceding figure indicates that VPC1 can access resources in IDC1 and IDC2, as the ECS1 instance gets returned messages.
Test the connectivity between VPC2 and two IDCs.
Log on to the ECS1 instance in VPC2. For more information, see the ECS remote connection guide.
Run the ping command on the ECS1 instance to test connectivity with clients in IDC1 and IDC2.
ping <IP address of the IDC client>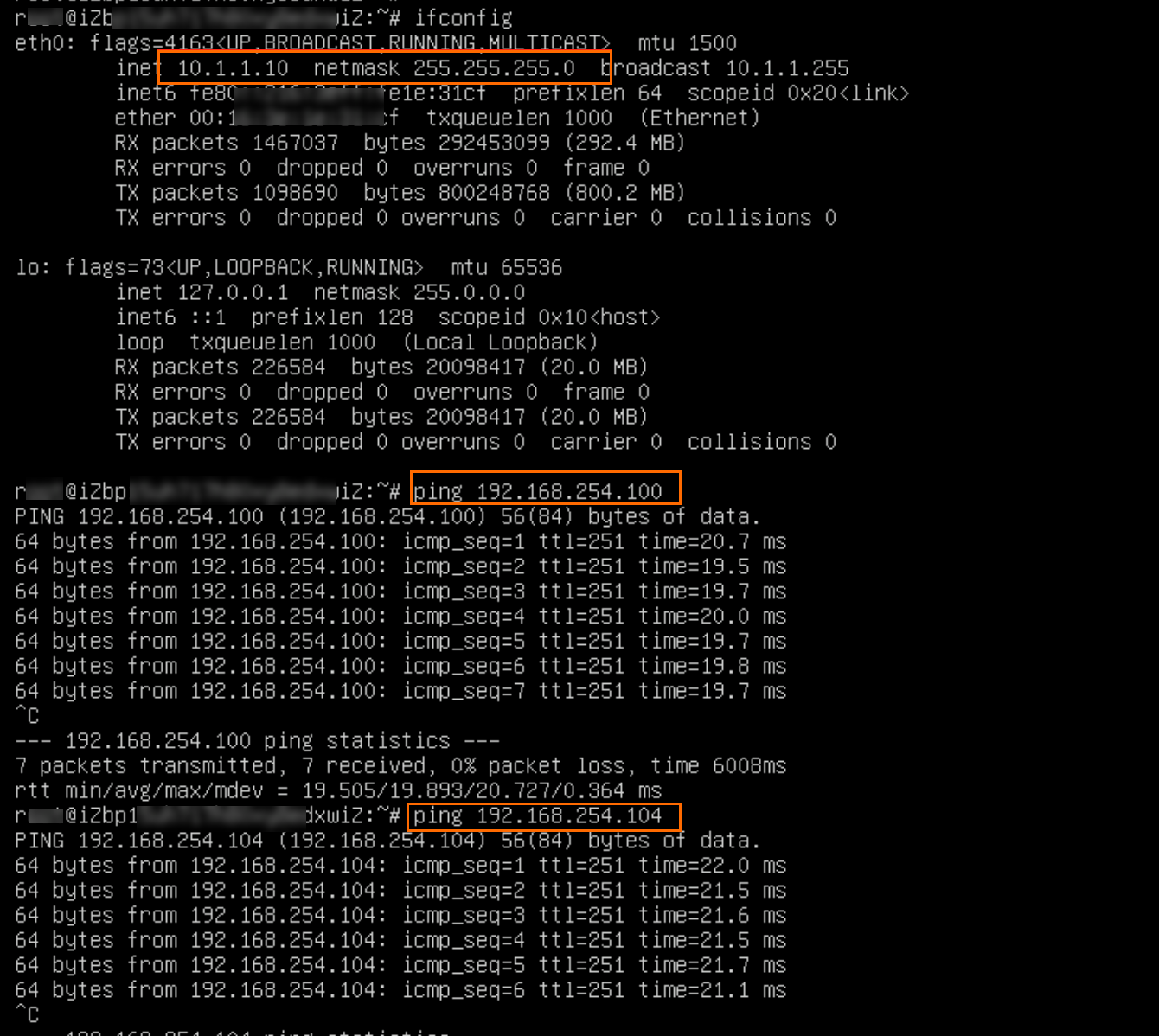
The preceding figure indicates that VPC2 can access resources in IDC1 and IDC2, as the ECS1 instance gets returned messages.
Test the connectivity between VPC1 and VPC2.
Log on to the ECS1 instance in VPC1. For more information, consult the ECS remote connection guide.
Run the ping command on the ECS1 instance to test connectivity with the ECS1 instance in VPC2.
ping <IP address of the ECS instance>
The preceding figure shows that ECS1 in VPC1 can access resources in VPC2, as the ECS1 instance gets returned messages.
Log on to the ECS1 instance in VPC2. For more information, see the ECS remote connection guide.
Run the ping command on the ECS1 instance to test connectivity with the ECS1 instance in VPC1.
ping <IP address of the ECS instance>
The preceding figure indicates that VPC2 can access resources in VPC1, as the ECS1 instance gets the returned messages.