您將公網IP資產添加到DDoS原生防護執行個體進行防護後,可以通過攻擊分析頁面查詢資產上發生的DDoS攻擊事件記錄和詳情,實現攻擊防護流程的透明化,提升防護分析體驗。本文介紹如何查看攻擊事件詳情。
前提條件
已購買DDoS原生防護執行個體。具體操作,請參見購買DDoS原生防護執行個體。
已將要防護的公網IP資產添加為DDoS原生防護執行個體的防護對象。具體操作,請參見防護對象。
操作步驟
登入流量安全產品控制台。
在左側導覽列,選擇。
在攻击分析頁面,選取查詢事件範圍,查詢相關的攻擊記錄。
說明如果當前阿里雲帳號配置了統一帳號管理功能,且為管理帳號,還支援您選擇帳號範圍。
所有帳號:查看管理帳號和成員帳號下的公網IP資產受到的DDoS攻擊事件,公網IP資產需要已添加為管理帳號的執行個體的防護對象。
單個成員帳號:查看該成員帳號下的公網IP資產受到的DDoS攻擊事件,公網IP資產需要已添加為管理帳號的執行個體的防護對象。
關於統一帳號管理功能的詳細介紹,請參見多帳號統一管理。
最多允許查詢最近6個月內的攻擊事件。
攻击类型:目前僅支援流量型攻擊。
攻击目标:表示被攻擊的公網IP資產。
起止时间:表示本次攻擊的開始時間和結束時間。
事件歸屬:表示公網IP資產歸屬於哪個阿里雲帳號。
攻击峰值:包含攻擊流量的頻寬峰值(單位:bps)和攻擊報文的包轉寄率峰值(單位:pps)。
查看攻擊事件詳情。
您可以單擊某個攻擊事件記錄後的查看详情,前往事件詳情頁面(如下圖所示),查看事件詳情並執行相關操作。
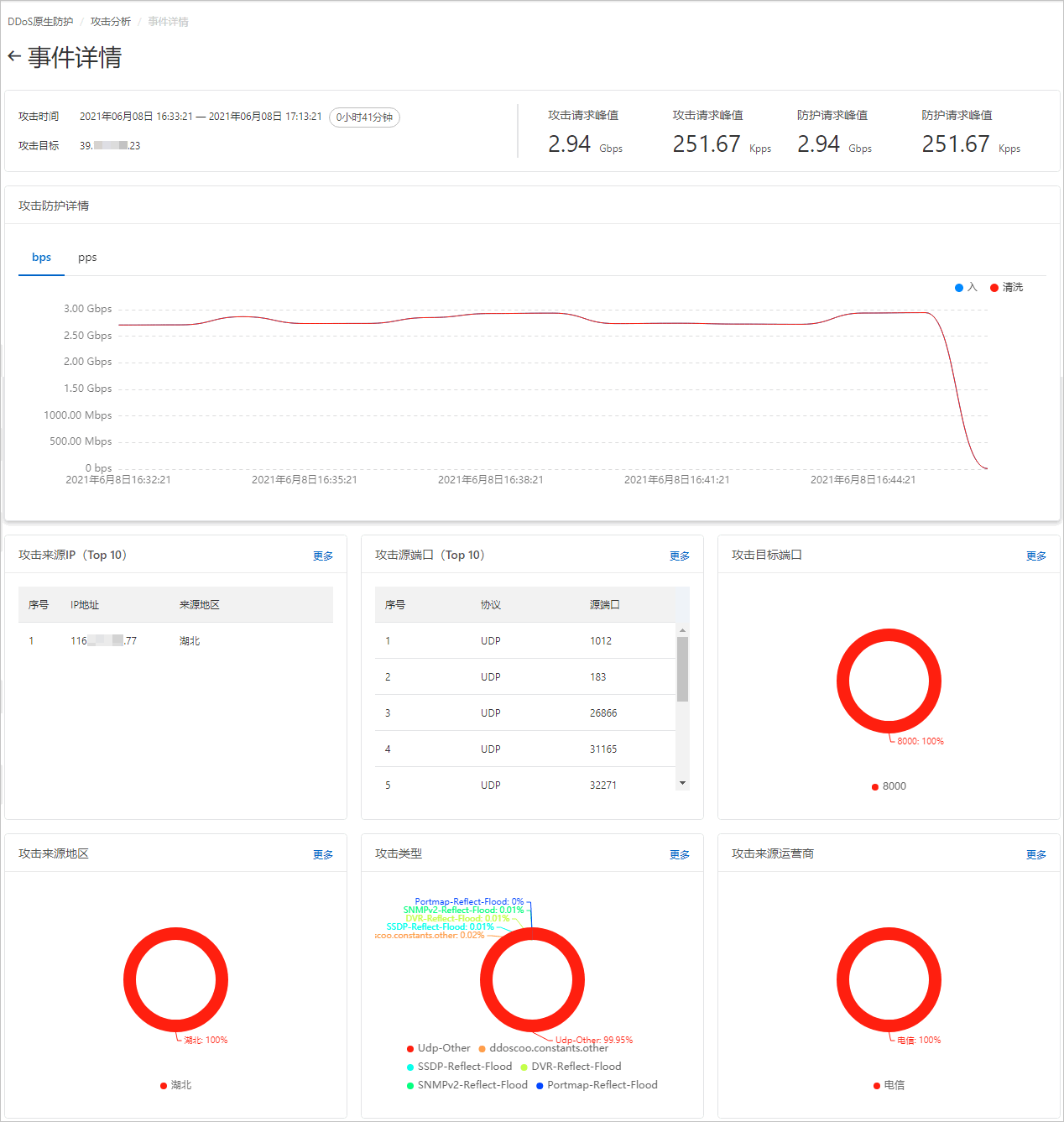
事件詳情頁麵包含以下內容:
頁面上方展示了攻击时间、攻击目标、攻擊流量bps峰值和清洗流量bps峰值資訊。
攻擊流量bps峰值表示原生防護執行個體檢測到的攻擊頻寬的峰值(單位:bps)和攻擊報文的包轉寄率峰值(單位:pps),清洗流量bps峰值表示經原生防護執行個體清洗的攻擊頻寬的峰值(單位:bps)和攻擊報文的包轉寄率峰值(單位:pps)。
攻击防护详情:展示了攻擊期間,入方向流量和清洗流量的頻寬變化趨勢圖(單位:bps)、入方向報文和清洗報文的包轉寄率變化趨勢圖(單位:pps)。
攻擊來源IP:展示了請求來源IP地址清單和對應的來源地區。列表顯示Top 10請求來源IP,單擊更多可以查看Top 100請求來源IP的資訊。
說明該資料包含攻擊請求和正常業務請求。
攻擊源連接埠(Top 10):展示了請求來源連接埠及對應的協議列表。列表顯示Top 10源連接埠,單擊更多可以查看Top 100源連接埠的資訊。
說明該資料包含攻擊請求和正常業務請求。
攻击目标端口:展示了請求目標連接埠的分布圖,單擊更多可以查看不同目標連接埠的請求佔比資料。
說明該資料包含攻擊請求和正常業務請求。
攻击来源地区:展示了攻擊流量的來源地區分布圖,單擊更多可以查看不同來源地區的請求佔比資料。
攻击类型:展示了攻擊流量的類型分布圖,單擊更多可以查看不同攻擊類型的請求佔比資料。
攻击来源运营商:展示了攻擊流量的來源電訊廠商分布圖,單擊更多可以查看不同電訊廠商的請求佔比資料。