本文為您介紹在首次使用ACK時,如何通過Terraform開通Container ServiceACK並進行Container Service角色的授權。
本教程所含範例程式碼支援一鍵運行,您可以直接運行代碼。一鍵運行
前提條件
由於阿里雲帳號(主帳號)具有資源的所有許可權,一旦發生泄露將面臨重大風險。建議您使用RAM使用者,並為該RAM使用者建立AccessKey,具體操作方式請參見建立RAM使用者和建立AccessKey。
為運行Terraform命令的RAM使用者綁定以下最小權限原則,以擷取管理本樣本所涉及資源的許可權。更多資訊,請參見為RAM使用者授權。
該權限原則允許RAM使用者建立、查看和刪除RAM角色,並支援對RAM角色權限原則的管理。
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": [ "ram:GetRole", "ram:ListRoles", "ram:AttachPolicyToRole", "ram:ListPoliciesForRole", "ram:CreateRole", "ram:DetachPolicyFromRole", "ram:DeleteRole" ], "Resource": "*" } ] }準備Terraform運行環境,您可以選擇以下任一方式來使用Terraform。
在Terraform Explorer中使用Terraform:阿里雲提供了Terraform的線上運行環境,您無需安裝Terraform,登入後即可線上使用和體驗Terraform。適用於零成本、快速、便捷地體驗和調試Terraform的情境。
Cloud Shell:阿里雲Cloud Shell中預裝了Terraform的組件,並已配置好身份憑證,您可直接在Cloud Shell中運行Terraform的命令。適用於低成本、快速、便捷地訪問和使用Terraform的情境。
在本地安裝和配置Terraform:適用於網路連接較差或需要自訂開發環境的情境。
使用的資源
alicloud_ack_service:自動開通Container ServiceACK。
alicloud_ram_role:建立一個RAM角色。
alicloud_ram_role_policy_attachment:為RAM角色綁定其他許可權。
alicloud_ram_roles:根據指定的過濾條件,返回阿里雲帳號中RAM角色的列表。
步驟一:開通Container ServiceACK
在建立ACK叢集前您需要開通Container Service。
建立一個工作目錄,並在該工作目錄中建立名為main.tf的設定檔,然後將以下代碼複製到main.tf中。
// 開通Container ServiceACK。 data "alicloud_ack_service" "open" { enable = "On" type = "propayasgo" }執行如下命令,初始化Terraform運行環境。
terraform init返回資訊如下,Terraform初始化成功。
Terraform has been successfully initialized! You may now begin working with Terraform. Try running "terraform plan" to see any changes that are required for your infrastructure. All Terraform commands should now work. If you ever set or change modules or backend configuration for Terraform, rerun this command to reinitialize your working directory. If you forget, other commands will detect it and remind you to do so if necessary.執行如下命令,開通Container ServiceACK。
terraform apply在執行過程中,根據提示輸入
yes並按下Enter鍵,等待命令執行完成,若出現以下資訊,則表示Container ServiceACK開通成功。You can apply this plan to save these new output values to the Terraform state, without changing any real infrastructure. Do you want to perform these actions? Terraform will perform the actions described above. Only 'yes' will be accepted to approve. Enter a value: yes Apply complete! Resources: 0 added, 0 changed, 0 destroyed.
步驟二:授權角色
首次登入Container Service for Kubernetes時,需要為服務帳號授予系統服務角色,具體步驟如下。
在
main.tf設定檔中增加如下授權模板。// 所需RAM角色。 variable "roles" { type = list(object({ name = string policy_document = string description = string policy_name = string })) default = [ { name = "AliyunCSManagedLogRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集的日誌組件使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedLogRolePolicy" }, { name = "AliyunCSManagedCmsRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集的CMS組件使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedCmsRolePolicy" }, { name = "AliyunCSManagedCsiRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集的儲存群組件使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedCsiRolePolicy" }, { name = "AliyunCSManagedCsiPluginRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集的儲存群組件使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedCsiPluginRolePolicy" }, { name = "AliyunCSManagedCsiProvisionerRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集的儲存群組件使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedCsiProvisionerRolePolicy" }, { name = "AliyunCSManagedVKRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "ACK Serverless叢集的VK組件使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedVKRolePolicy" }, { name = "AliyunCSServerlessKubernetesRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集預設使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSServerlessKubernetesRolePolicy" }, { name = "AliyunCSKubernetesAuditRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集審計功能使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSKubernetesAuditRolePolicy" }, { name = "AliyunCSManagedNetworkRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集網路組件使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedNetworkRolePolicy" }, { name = "AliyunCSDefaultRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集操作時預設使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSDefaultRolePolicy" }, { name = "AliyunCSManagedKubernetesRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集預設使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedKubernetesRolePolicy" }, { name = "AliyunCSManagedArmsRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集Arms外掛程式使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedArmsRolePolicy" }, { name = "AliyunCISDefaultRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "Container Service(CS)智能營運使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCISDefaultRolePolicy" }, { name = "AliyunOOSLifecycleHook4CSRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"oos.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集擴縮容節點池依賴OOS服務,OOS使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunOOSLifecycleHook4CSRolePolicy" }, { name = "AliyunCSManagedAutoScalerRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集的Auto Scaling組件使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedAutoScalerRolePolicy" } ] } // 查詢RAM角色列表 data "alicloud_ram_roles" "roles" { policy_type = "Custom" name_regex = "^Aliyun.*Role$" } locals { # 提取所有所需RAM角色name all_role_names = [for role in var.roles : role.name] # 提取已存在的RAM角色name created_role_names = [for role in data.alicloud_ram_roles.roles.roles : role.name] # 計算補集:即找出還未建立的所需RAM角色 complement_names = setsubtract(local.all_role_names, local.created_role_names) # 待建立的RAM角色 complement_roles = [for role in var.roles : role if contains(local.complement_names, role.name)] } // 建立角色。 resource "alicloud_ram_role" "role" { for_each = { for r in local.complement_roles : r.name => r } name = each.value.name document = each.value.policy_document description = each.value.description force = true } // 角色關聯絡統許可權。 resource "alicloud_ram_role_policy_attachment" "attach" { for_each = { for r in local.complement_roles : r.name => r } policy_name = each.value.policy_name policy_type = "System" role_name = each.value.name depends_on = [alicloud_ram_role.role] }說明在樣本中,variable表示作為參數提供給Terraform使用的輸入變數。本樣本中參數值請參見附錄,其中,服務角色是必選參數,可選角色請根據實際情況選擇。
建立執行計畫,並預覽變更。
terraform plan執行如下命令應用執行計畫,為您的帳號進行角色授權。
terraform apply在執行過程中,根據提示輸入
yes並按下Enter鍵,等待命令執行完成,若出現以下資訊,則表示授權完成。Apply complete! Resources: 2 added, 0 changed, 0 destroyed.驗證結果。
執行terraform show命令
您可以使用以下命令查詢Terraform已建立的資來源詳細資料:
terraform show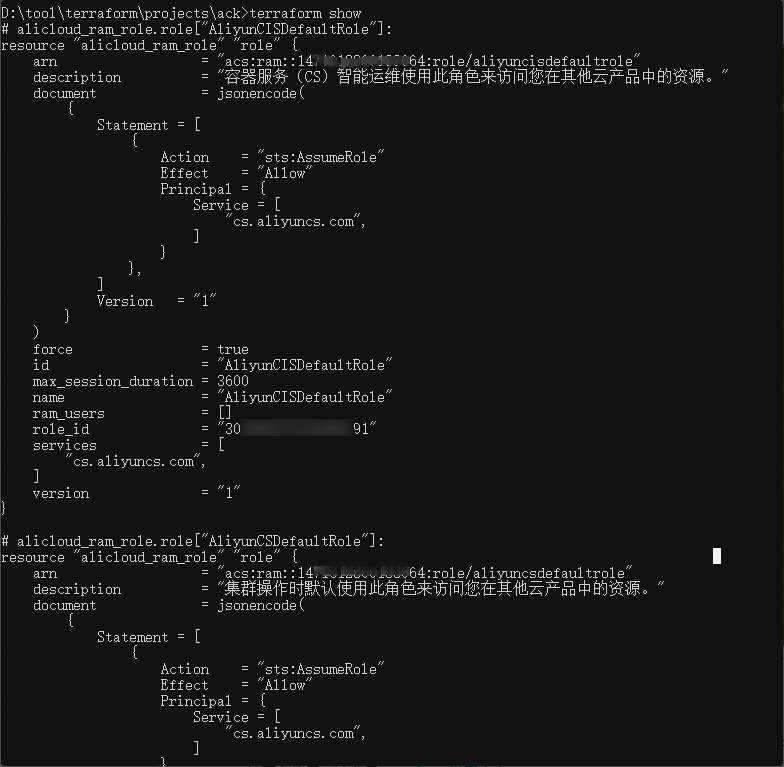
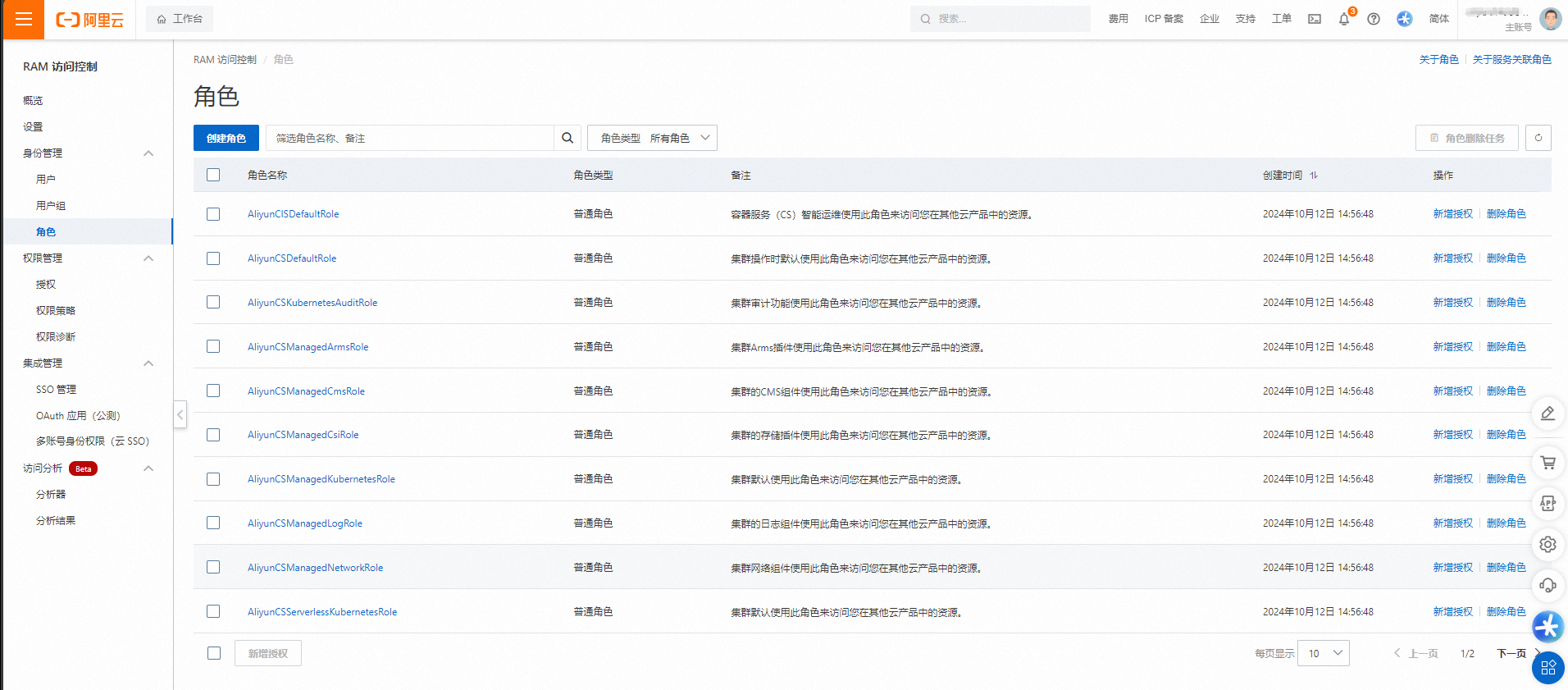
登入RAM控制台
登入RAM控制台,查看已建立的角色。
清理資源
當您不再需要上述通過Terraform建立或管理的資源時,請運行以下命令以釋放資源。關於terraform destroy的更多資訊,請參見常用命令。
terraform destroy完整樣本
本教程所含範例程式碼支援一鍵運行,您可以直接運行代碼。一鍵運行
範例程式碼
附錄
服務角色
AliyunCSManagedLogRole
說明:
ACK託管叢集、ACK Edge叢集和ACK Serverless叢集的日誌組件使用該角色訪問您在SLS服務中的資源。
授權碼:
{ name = "AliyunCSManagedLogRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集的日誌組件使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedLogRolePolicy" }
AliyunCSManagedCmsRole
說明:
ACK託管叢集、ACK Edge叢集和ACK Serverless叢集的監控組件使用該角色訪問您在CMS、SLS服務中的資源。
授權碼:
{ name = "AliyunCSManagedCmsRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集的CMS組件使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedCmsRolePolicy" }
AliyunCSManagedCsiRole
說明:
ACK託管叢集、ACK Edge叢集和ACK Serverless叢集的儲存群組件使用該角色訪問您在ECS、NAS、OSS等服務中的資源。
授權碼:
{ name = "AliyunCSManagedCsiRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集的儲存外掛程式使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedCsiRolePolicy" }
AliyunCSManagedCsiPluginRole
說明:
ACK託管叢集、ACK Edge叢集和ACK Serverless叢集的儲存群組件(新版csi-plugin組件)使用該角色訪問您在ECS服務中的資源。
授權碼:
{ name = "AliyunCSManagedCsiPluginRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "ACK託管叢集、ACK Edge叢集和ACK Serverless叢集的儲存群組件(新版csi-plugin組件)使用該角色訪問您在ECS服務中的資源。" policy_name = "AliyunCSManagedCsiPluginRolePolicy" }
AliyunCSManagedCsiProvisionerRole
說明:
ACK託管叢集、ACK Edge叢集和ACK Serverless叢集的儲存群組件(新版csi-provisioner組件)使用該角色訪問您在ECS、NAS、OSS服務中的資源。
授權碼:
{ name = "AliyunCSManagedCsiProvisionerRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "ACK託管叢集、ACK Edge叢集和ACK Serverless叢集的儲存群組件(新版csi-provisioner組件)使用該角色訪問您在ECS、NAS、OSS服務中的資源。" policy_name = "AliyunCSManagedCsiProvisionerRolePolicy" }
AliyunCSServerlessKubernetesRole
說明:
ACK Edge叢集和ACK Serverless叢集使用該角色來訪問您在ECS、VPC、SLB、Private Zone等服務中的資源。
授權碼:
{ name = "AliyunCSServerlessKubernetesRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集預設使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSServerlessKubernetesRolePolicy" }
AliyunCSKubernetesAuditRole
說明:
ACK託管叢集、ACK Edge叢集和ACK Serverless叢集的審計功能組件使用該角色來訪問您在SLS服務中的資源。
授權碼:
{ name = "AliyunCSKubernetesAuditRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集審計功能使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSKubernetesAuditRolePolicy" }
AliyunCSManagedNetworkRole
說明:
ACK託管叢集、ACK Edge叢集和ACK Serverless叢集的網路組件使用該角色訪問您在ECS、VPC服務中的資源。
授權碼:
{ name = "AliyunCSManagedNetworkRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集網路組件使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedNetworkRolePolicy" }
AliyunCSDefaultRole
說明:
Container Service Kubernetes 版在管控操作中使用該角色訪問您在ECS、VPC、SLB、ROS、ESS等服務中的資源。
授權碼:
{ name = "AliyunCSDefaultRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集操作時預設使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSDefaultRolePolicy" }
AliyunCSManagedKubernetesRole
說明:
ACK託管叢集和ACK Edge叢集使用該角色訪問您在ECS、VPC、SLB、ACR等服務中的資源。
授權碼:
{ name = "AliyunCSManagedKubernetesRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集預設使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedKubernetesRolePolicy" }
AliyunCSManagedArmsRole
說明:
ACK Edge叢集和ACK Serverless叢集的應用即時監控組件使用該角色訪問您在ARMS服務中的資源。
授權碼:
{ name = "AliyunCSManagedArmsRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集Arms外掛程式使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedArmsRolePolicy" }AliyunCISDefaultRole
說明:
ACK容器智能營運平台將使用該角色訪問您在ECS、VPC、SLB等服務中的資源,為您提供診斷和巡檢等服務。
授權碼:
{ name = "AliyunCISDefaultRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "Container Service(CS)智能營運使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCISDefaultRolePolicy" }
可選角色
AliyunCSManagedAcrRole
說明:
ACK託管叢集、ACK Edge叢集和ACK Serverless叢集的免密組件鏡像拉取使用該角色訪問您在ACRContainer Registry中的資源。
授權碼:
{ name = "AliyunCSManagedAcrRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集的鏡像拉取免密外掛程式使用該角色訪問您在ACRContainer Registry中的資源。" policy_name = "AliyunCSManagedAcrRolePolicy" }
AliyunCSManagedNlcRole
說明:
ACK託管叢集和ACK Edge叢集的節點生命週期控制器使用該角色訪問您的ECS和ACK節點池資源。
授權碼:
{ name = "AliyunCSManagedNlcRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集託管節點池控制組件使用該角色訪問您的ECS和ACK節點池資源。" policy_name = "AliyunCSManagedNlcRolePolicy" }
AliyunCSManagedAutoScalerRole
說明:
ACK託管叢集、ACK Edge叢集和ACK Serverless叢集的Auto Scaling組件使用該角色訪問您在ESS和ECS服務中的資源。
授權碼:
{ name = "AliyunCSManagedAutoScalerRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集的Auto Scaling組件使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunCSManagedAutoScalerRolePolicy" }
AliyunCSManagedSecurityRole
說明:
ACK託管叢集、ACK Edge叢集和ACK Serverless叢集的落盤加密和憑據管理組件使用該角色訪問您在KMS服務中的資源。
授權碼:
{ name = "AliyunCSManagedSecurityRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集的落盤加密外掛程式使用該角色訪問您在KMS服務中的資源。" policy_name = "AliyunCSManagedSecurityRolePolicy" }
AliyunCSManagedCostRole
說明:
ACK託管叢集、ACK Edge叢集和ACK Serverless叢集的成本分析組件使用該角色訪問您在賬單管理API、ECS和ECI服務中的資源。
授權碼:
{ name = "AliyunCSManagedCostRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集的成本分析組件使用該角色訪問您在賬單管理API、ECS和ECI服務中的資源。" policy_name = "AliyunCSManagedCostRolePolicy" }
AliyunCSManagedNimitzRole
說明:
ACK Edge叢集的管控組件使用該角色訪問您在Smart Access Gateway、VPC和雲企業網CEN服務中的資源。
授權碼:
{ name = "AliyunCSManagedNimitzRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "ACK靈駿叢集的網路組件使用該角色訪問您在智能計算靈駿服務中的資源。" policy_name = "AliyunCSManagedNimitzRolePolicy" }
AliyunCSManagedBackupRestoreRole
說明:
ACK託管叢集、ACK Edge叢集和ACK Serverless叢集的備份中心服務元件使用該角色訪問您在Cloud Backup服務和OSS服務中的資源。
授權碼:
{ name = "AliyunCSManagedBackupRestoreRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集的備份中心組件使用該角色訪問您在雲備份(Cloud Backup)服務和OSS服務中的資源。" policy_name = "AliyunCSManagedBackupRestoreRolePolicy" }
AliyunCSManagedEdgeRole
說明:
ACK Edge叢集的管控組件使用該角色訪問您在Smart Access Gateway、VPC和雲企業網CEN服務中的資源。
授權碼:
{ name = "AliyunCSManagedEdgeRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "ACK Edge叢集的管控組件使用該角色訪問您在Smart Access Gateway、VPC和雲企業網CEN服務中的資源。" policy_name = "AliyunCSManagedEdgeRolePolicy" }
AliyunOOSLifecycleHook4CSRole
說明:
系統營運管理OOS使用該角色訪問您在Container Service Kubernetes 版、ECS、PolarDB等服務中的資源。
授權碼:
{ name = "AliyunOOSLifecycleHook4CSRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"oos.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "叢集擴縮容節點池依賴OOS服務,OOS使用此角色來訪問您在其他雲產品中的資源。" policy_name = "AliyunOOSLifecycleHook4CSRolePolicy" }
相關文檔
Terraform介紹,請參見Terraform產品介紹。
ROS提供了Terraform託管服務,因此您可以直接在ROS控制台部署Terraform模板。詳細操作,請參見建立Terraform類型資源棧。