企業で Active Directory (AD) ドメインを使用してユーザーアカウントを管理している場合は、Elastic Desktop Service (EDS) Enterprise をサービスプロバイダー (SP) として、Active Directory フェデレーションサービス (AD FS) を ID サービスプロバイダー (IdP) として使用できます。Security Assertion Markup Language (SAML) は、SP と IdP が相互にメタデータファイルを交換してシングルサインオン (SSO) を実装するためのプロトコルベースです。このトピックでは、実装について詳しく説明します。
背景情報
シングルサインオン (SSO) は、1 回のサインオンで複数の信頼できるアプリケーションシステムに効率的にアクセスできる安全な通信テクノロジーです。SSO は、ID フェデレーションに基づいてログインを実装します。
SSO シナリオでは、次の用語がよく使用されます。
ID プロバイダー (IdP): 外部 ID プロバイダーのメタデータを含むエンティティ。IdP は、ID 管理サービスを提供し、ユーザー名やパスワードなどのユーザー ID 情報を収集および保存し、ユーザーログイン時にユーザー ID を検証します。
一般的な IdP:
オンプレミス IdP: Microsoft Active Directory フェデレーションサービス (AD FS) や Shibboleth などのオンプレミスアーキテクチャを使用します。
クラウド IdP: Azure AD、Google Workspace、Okta、OneLogin。
サービスプロバイダー (SP): IdP との信頼関係に基づいて、IdP の ID 管理機能を使用してユーザーに特定のサービスを提供するアプリケーション。OpenID Connect (OIDC) など、Security Assertion Markup Language (SAML) プロトコルに準拠していない特定の ID システムでは、SP は IdP の依拠当事者です。
SAML 2.0: 企業向けのユーザー ID 認証の標準プロトコル。SP と IdP 間の通信の技術実装の 1 つです。SAML は、企業が SSO を実装するために使用するデファクトスタンダードです。
EDS Enterprise コンソールで企業 AD オフィスネットワークを作成して AD システムに接続すると、EDS Enterprise システムは AD システム情報を収集します。そうしたくない場合は、EDS Enterprise コンソールで AD ユーザーと同じ情報を持つ簡便アカウントを作成して SSO を実装できます。
企業 AD オフィスネットワーク が作成され、AD システムに接続されている場合は、AD ユーザーを設定して SSO を実装します。詳細については、「AD FS を使用して Elastic Desktop Service の AD ユーザー向けに SSO を実装する」をご参照ください。
準備
EDS Enterprise コンソールで簡便アカウントを作成するには、次のいずれかの方法を選択します。
手動入力: ユーザー情報を入力して、簡便アカウントを 1 つずつ作成します。この方法は、ユーザー数が少ないシナリオに適しています。
重要ユーザー情報を入力するときは、作成する簡便アカウントのユーザー名が AD ユーザーのユーザー名と同じであることを確認してください。ユーザー名は大文字と小文字を区別しません。
一括入力: .csv ファイルを使用してユーザー情報をインポートし、複数の簡便アカウントを一度に作成します。この方法は、ユーザー数が多いシナリオに適しています。
一括入力方式を使用する場合は、次の手順を実行して有効な .csv ファイルを準備します。
AD ドメインサーバーに AD ユーザー情報を含む .csv ファイルを作成します。
既存のユーザー情報がフォーマット要件を満たしているかどうかを確認します。
重要AD ユーザーのユーザー名は、EDS Enterprise 簡便アカウントのユーザー名の形式要件を満たしている必要があります。そうでない場合、AD ユーザーに対応する簡便アカウントを作成できません。詳細については、「簡便ユーザーの命名規則」をご参照ください。
PowerShell で
Get-ADUserコマンドを実行して、AD ユーザーを含む .csv ファイルをエクスポートします。コマンドのパラメーターを変更して、ビジネス要件に基づいて .csv ファイルをエクスポートできます。たとえば、すべての AD ユーザー情報を含む .csv ファイルをエクスポートして特定のパスに保存する場合は、次のコマンドを実行します。
Get-ADUser -filter * | export-csv <File path> -Encoding utf8ファイルを
C:\Usersディレクトリに保存し、ファイル名を test.csv にする場合は、次のコマンドを実行します。Get-ADUser -filter * |export-csv C:\Users\test.csv -Encoding utf8
スプレッドシートソフトウェアを使用してファイルを開き、簡便アカウントのユーザー名規則に基づいてユーザー情報のフォーマットを変更してから、ファイルを保存します。
ユーザー情報を変更する場合は、次のユーザー名規則に注意してください。
フォーマット:
ユーザーがアクティブ化した簡便ユーザー: 1 列目はユーザー名、2 列目はメールアドレス、3 列目は電話番号です。3 列目はオプションです。
管理者がアクティブ化した簡便ユーザー: 1 列目はユーザー名、2 列目はメール、3 列目は電話番号、4 列目はパスワードです。2 列目と 3 列目はオプションです。
エクスポートされた .csv ファイルでは、SamAccountName 列はユーザー名列と見なされ、UserPrincipalName 列はメールアドレス列と見なされます。AD ユーザーの実際のメールアドレスが UserPrincpleName 列で指定されたものと異なる場合は、現在のメールアドレスを新しいメールアドレスに置き換えます。
ステップ 1: 簡便アカウントを作成する
EDS Enterprise コンソール にログインします。
左側のナビゲーションウィンドウで、 を選択します。
[ユーザーと組織] ページで、[ユーザー] タブをクリックし、[ユーザーの作成] をクリックします。次のいずれかの方法を使用して簡便アカウントを作成します。
手動作成
[手動入力] タブをクリックし、必要に応じて次のパラメーターを設定して、[ユーザーの作成] をクリックします。
パラメーター
必須
説明
ユーザータイプ
はい
簡便アカウントのタイプ。有効な値: ユーザーがアクティブ化 および 管理者がアクティブ化。
ユーザー名
はい
簡便アカウントのユーザー名。3 ~ 25 文字で、英字または数字で始まる必要があります。小文字、数字、ハイフン(-)、アンダースコア(_)、およびピリオド(.)を含めることができます。ユーザー名は、数字のみで構成したり、オペレーティングシステムで予約されている組み込みユーザー名と一致したりすることはできません。詳細については、「簡便ユーザーの命名規則」をご参照ください。
表示名
いいえ
簡便アカウントの表示名。識別のために使用され、エンドユーザーには表示されません。
連絡先情報 (メールアドレス)
はい
クラウドコンピューターの割り当て、ログイン情報、初期パスワード、パスワードリセットアラートなどの通知を受信するために指定されたメールアドレス。指定するメールアドレスが有効であることを確認してください。
親組織
いいえ
簡便アカウントが属する組織。この手順で組織を選択するか、アカウントを作成した後に簡便アカウントを組織に追加できます。
パスワード
はい
ユーザータイプ パラメーターを 管理者がアクティブ化 に設定した場合、このパラメーターは必須です。パスワードは 10 文字以上で、大文字、小文字、数字、特殊文字 (スペースを除く) のうち少なくとも 3 種類を含める必要があります。
パスワードの有効期間
いいえ
パスワードの有効期間。デフォルトでは、パスワードは永続的に有効です。7 ~ 365 日の有効期間を入力することもできます。パスワードの有効期限が切れると、ログインを進める前にパスワードを変更する必要があります。
ロックオン
ユーザータイプ パラメーターを 管理者がアクティブ化 に設定した場合、このパラメーターは必須です。簡便アカウントがロックされると、エンドユーザーはそのアカウントを使用して Alibaba Cloud Workspace 端末 にログインできなくなります。
管理者権限の付与
いいえ
備考
いいえ
簡便アカウントに関する補足情報。
一括作成
[一括入力] タブをクリックし、必要に応じて次のパラメーターを設定して、[閉じる] をクリックします。
パラメーター
必須
説明
アカウントの所有権
はい
簡便アカウントのタイプ。有効な値: ユーザーがアクティブ化 および 管理者がアクティブ化。
パスワードの有効期間
いいえ
パスワードの有効期間。デフォルトでは、パスワードは永続的に有効です。7 ~ 365 日の有効期間を入力することもできます。パスワードの有効期限が切れると、ログインを進める前にパスワードを変更する必要があります。
ロックオン
いいえ
ユーザータイプ パラメーターを 管理者がアクティブ化 に設定した場合、このパラメーターは必須です。簡便アカウントがロックされると、エンドユーザーはそのアカウントを使用して Alibaba Cloud Workspace 端末 にログインできなくなります。
管理者権限の付与
いいえ
簡便アカウントにローカル管理者権限を付与するかどうかを指定します。デフォルトでは、[管理者権限の付与] パラメーターは [はい] に設定されています。簡便アカウントにローカル管理者権限を付与したくない場合は、[いいえ] を選択します。
説明ローカル管理者権限を持つ簡便アカウントを使用して、クラウドコンピューターにソフトウェアをインストールしたり、システム設定を変更したりできます。
ローカル管理者権限の変更は、クラウドコンピューターの再起動後に有効になります。
ファイルのアップロード
はい
[ダウンロード] をクリックして、ユーザー情報をインポートするためのテンプレートをダウンロードします。テンプレートを開き、テンプレートで提供されている形式でユーザー情報を入力して、テンプレートを保存します。
ユーザーがアクティブ化したユーザーアカウントをインポートする場合は、テンプレートの 1 列目に
Username、2 列目にEmailを指定します。管理者がアクティブ化したユーザーアカウントをインポートする場合は、テンプレートの 1 列目に
Username、4 列目にPasswordを指定します。インポートする簡便アカウントごとに組織を指定する場合は、テンプレートの
OrgId列に組織 ID を入力します。OrgIdの値を取得するには、次の図に示すように、組織構造にカーソルを合わせます。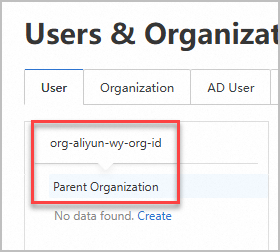
[ローカルファイルのアップロード] をクリックし、アカウント情報を含むテンプレートを選択します。システムは自動的にデータをインポートします。
テンプレートが EDS Enterprise コンソールにインポートされると、[ユーザーの作成] パネルに簡便アカウントの作成を確認するメッセージが表示されます。[アカウントの表示] をクリックして、インポートされたデータ項目を確認します。インポートが失敗した場合は、テンプレートのアカウント情報が有効な形式であるかどうかを確認します。
[閉じる] をクリックします。
簡便アカウントを作成した後、[ユーザー] タブでアカウント情報を表示できます。簡便アカウントは [標準] 状態です。
説明簡便アカウントが作成されたとき、システムは通知を送信しません。クラウドコンピューターまたは 多対多共有 を簡便アカウントに割り当てると、システムは指定されたメールアドレスに通知を送信します。
ステップ 2: EDS Enterprise コンソール で AD FS を信頼できる SAML IDP として設定する
AD FS の IdP メタデータファイルを取得し、オンプレミスデバイスにダウンロードします。
IdP メタデータファイルの URL:
https://<AD FS サーバー>/FederationMetadata/2007-06/FederationMetadata.xml。<AD FS サーバー>は、AD FS サーバーのドメイン名または IP アドレスを示します。IdP メタデータファイルを EDS Enterprise コンソールにアップロードします。
EDS Enterprise コンソール にログインします。
左側のナビゲーションウィンドウで、 を選択します。
上部ナビゲーションバーの左上隅で、リージョンを選択します。
[オフィスネットワーク] ページで、SSO を有効にする オフィスネットワーク を見つけ、オフィスネットワーク ID をクリックします。
オフィスネットワークオフィスネットワークの詳細ページで、 セクションの右上隅にある [表示]その他の情報 をクリックし、[SSO] をオンにします。
[ファイルのアップロード] をクリックし、[IdP メタデータ] の横にある IdP メタデータファイルをアップロードします。
ステップ 3: AD FS で EDS Enterprise を信頼できる SAML SP として設定する
Elastic Desktop Service (Enterprise Edition) コンソールでメタデータファイルを取得します。
EDS Enterprise コンソール にログインします。
左側のナビゲナビゲーションウィンドウで、 を選択します。
[オフィスネットワーク (旧称ワークスペース)] ページで、SSO を有効にするオフィスネットワークを見つけ、オフィスネットワーク ID をクリックします。
オフィスネットワークの詳細ページの左側のナビゲーションウィンドウで、[その他] タブをクリックします。
[その他] タブで、[アプリケーションメタデータ] の右側にある [アプリケーションメタデータファイルのダウンロード] をクリックします。
ダウンロードされたメタデータファイルは、ローカルコンピューターのダウンロードフォルダに自動的に保存されます。
EDS Enterprise の SP メタデータファイルを AD FS にアップロードします。
AD FS のサーバーにログインし、サーバーマネージャーを開きます。
右上隅で、 を選択します。
[AD FS] ウィンドウの左側のナビゲーションウィンドウで、 を選択します。
右側の [アクション] セクションで、[依拠当事者信頼の追加] をクリックします。
プロンプトに従って後続の操作を完了します。
[データソースの選択] ステップで、[ファイルから依拠当事者に関するデータをインポートする] を選択し、EDS Enterprise の SP メタデータファイルをインポートします。次のステップではデフォルト設定を保持します。
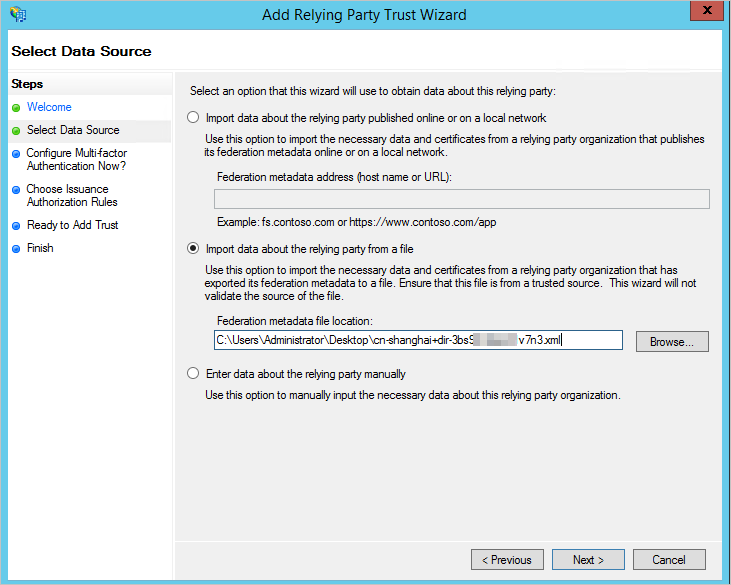
依拠当事者信頼の要求発行ポリシーを変更し、EDS Enterprise の SAML アサーション属性を設定します。
依拠当事者信頼のリストで、前の手順で追加した依拠当事者信頼を右クリックし、[要求発行ポリシーの編集] を選択します。
表示されるダイアログボックスで、[ルールの追加] をクリックします。
要求規則を設定します。
要求規則を設定する場合は、次の項目に注意してください。
[ルールの種類の選択] ステップで、[要求ルールのテンプレート] ドロップダウンリストから [受信要求の変換] を選択します。
[要求規則の設定] ステップで、[受信要求の種類] ドロップダウンリストから [UPN] を選択し、[送信要求の種類] ドロップダウンリストから [名前 ID] を選択します。
ステップ 4: SSO が設定されているかどうかを確認する
この例では、Alibaba Cloud Workspace の Windows クライアント V7.2.2 を使用しています。
Windows クライアント を開き、ページの上部にある [Enterprise Edition] を選択し、プライバシーポリシーの横にあるチェックボックスをオンにして、受信したログイン資格情報から組織 ID または オフィスネットワーク ID を入力し、 アイコンをクリックします。
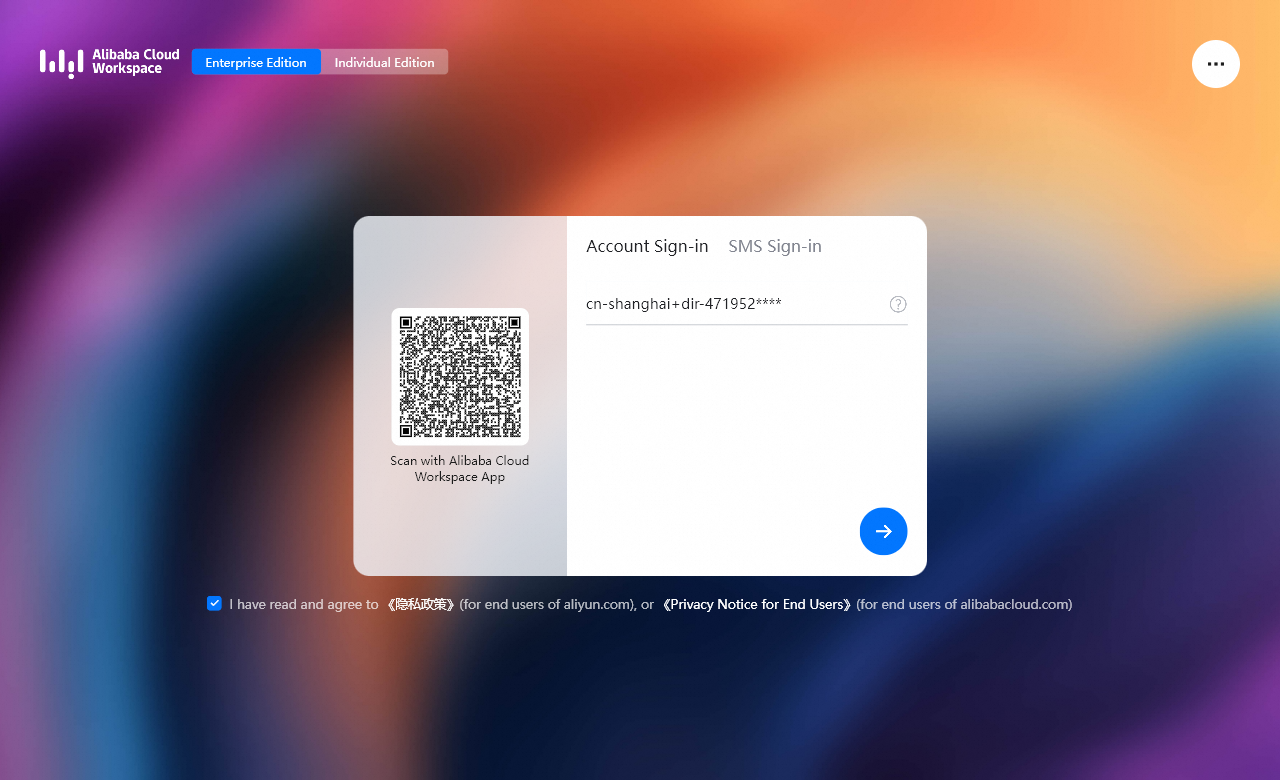
AD FS ログインページで、前のセクションで作成した簡便アカウントのユーザー名を入力します。次に、AD FS システムがユーザー ID を検証します。
ID 検証に合格すると、クライアントにログインした後に目的のクラウドコンピューターを見つけることができます。次に、クラウドコンピューターのカードにポインターを置き、[開始] と [クラウドコンピューターに接続] をクリックしてクラウドコンピューターを使用します。