このトピックでは、Resource access Management (RAM) ユーザーまたは必要な権限を持たないRAMロールを使用して、Alibaba Cloudリソースにアクセスする際のアクセス拒否エラーのトラブルシューティング方法について説明します。
問題の説明
デフォルトでは、RAMユーザーやRAMロールなどのRAM IDには操作権限がありません。 RAM IDは、IDに必要な権限が明示的に付与された後にのみクラウドリソースにアクセスできます。 RAM IDの権限付与効果は、許可または拒否です。 RAM IDがAlibaba Cloudリソースに対して操作を実行すると、操作が明示的に拒否または暗黙的に拒否された場合、システムはアクセス拒否エラーを報告します。 暗黙の拒否は、RAM IDが明示的に許可されていないことを示します。
コンソールアクセスモードでのアクセス拒否エラー:
権限拒否OpenAPIアクセスモードでのアクセス拒否エラー:
NoPermission、Forbidden.RAM、NotAuthorized
解決策
コンソールアクセス
Alibaba Cloud管理コンソールで操作を実行し、必要な権限がない場合、システムはエラーの原因と詳細を含む次のエラーを報告します。 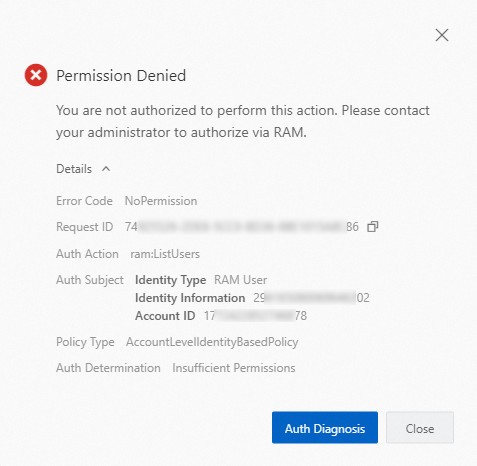
エラーをトラブルシューティングするには、次の手順を実行します。
オペレーターを特定します。
Auth Subjectパラメーターは、演算子の詳細を提供します。
IDタイプ: RAMユーザー、RAMロール、およびシングルサインオン (SSO) IDを含む、演算子のIDタイプ。 SSOはIDフェデレーションとも呼ばれます。
ID情報: ID。 オペレータがRAMユーザの場合、ユーザのIDが表示される。 演算子がRAMロールの場合、ロールの名前とセッション名 (
RoleName:RoleSessionNameなど) が表示されます。 演算子がSSO IDの場合、IdPのタイプと名前 (saml-provider/AzureADなど) が表示されます。アカウントID: 現在のIDが属するAlibaba CloudアカウントのID。
オペレータの必要な権限を特定します。
Auth Actionパラメーターは、オペレーターが実行する権限を持たない操作を提供します。 操作に基づいて権限を確認または付与できます。
アクセス拒否エラーの原因となるポリシーの種類を特定します。
[ポリシータイプ] パラメーターは、アクセス拒否エラーの原因となるポリシーのタイプを提供します。 ポリシーは、制御ポリシー、セッションポリシー、ロール固有の信頼ポリシー (ロールポリシーを想定) 、またはアカウントまたはリソースグループレベルのIDベースのポリシーです。 詳細については、「ポリシー評価プロセス」をご参照ください。
ポリシーを調整する方法は、ポリシータイプによって異なります。
コントロールポリシーに基づいて操作が拒否された場合は、リソースディレクトリの管理アカウントに連絡して、必要な権限を付与する必要があります。 コントロールポリシーは、リソースディレクトリ内のメンバーに付与される権限を指定します。 制御ポリシーの決定は、単一のアカウント内で行われる決定よりも高い優先度を有する。
セッションポリシーに基づいて操作が拒否された場合は、アカウント管理者に連絡して、AssumeRole操作を呼び出して、オペレータにアタッチされているセッションポリシーを確認する必要があります。
ロール固有の信頼ポリシーに基づいて操作が拒否された場合は、アカウント管理者に連絡して、オペレーターが想定するRAMロールの信頼ポリシーを確認する必要があります。
IDベースのポリシーに基づいて操作が拒否された場合は、アカウント管理者に連絡して、オペレーターのIDにアタッチされているポリシーを確認する必要があります。
アクセス拒否エラーの原因が暗黙的拒否か明示的拒否かを確認してください。
暗黙的な拒否: エラーメッセージは、現在の操作を実行する権限がないことを示し、Auth Determinationパラメーターに
[不十分な権限]が表示されます。 この場合、アカウント管理者に連絡して必要な権限を付与する必要があります。 アカウント管理者は、Auth Actionパラメーターで示される操作をAllowステートメントに追加できます。Explicit deny: エラーメッセージは、現在の操作が明示的に拒否され、Auth Determinationパラメーターに
Explicit Denyが表示されます。 この場合、アカウント管理者に連絡して、付与された権限を確認し、Auth Actionパラメーターで示される操作がDenyステートメントに含まれているかどうかを確認する必要があります。説明ポリシーがコントロールポリシーの場合、Auth Actionパラメーターで示される操作がAllowステートメントに含まれていない場合でも、Explicit Denyが返されます。
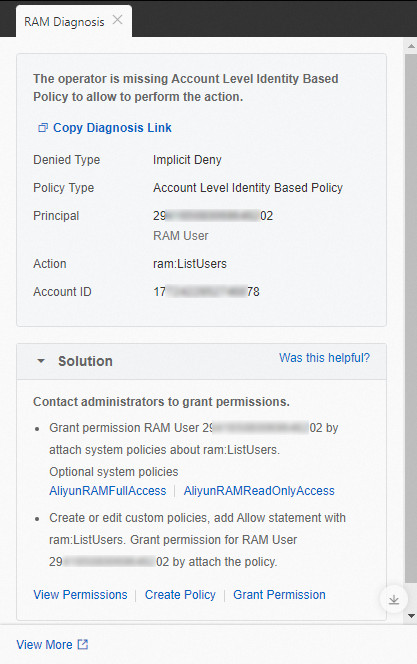
サービスが権限診断をサポートしている場合は、エラーメッセージの [認証診断] をクリックして、エラーの原因と解決策を表示できます。
OpenAPIアクセス
Alibaba Cloud SDK、CLI、またはOpenAPI Explorerを使用してサービスにアクセスすると、アクセス拒否エラーが発生する可能性があります。 返されたエラーには、エラーの詳細が含まれます。 次の図は、OpenAPI Explorerを使用してサービスにアクセスしたときに返されるアクセス拒否エラーを示しています。 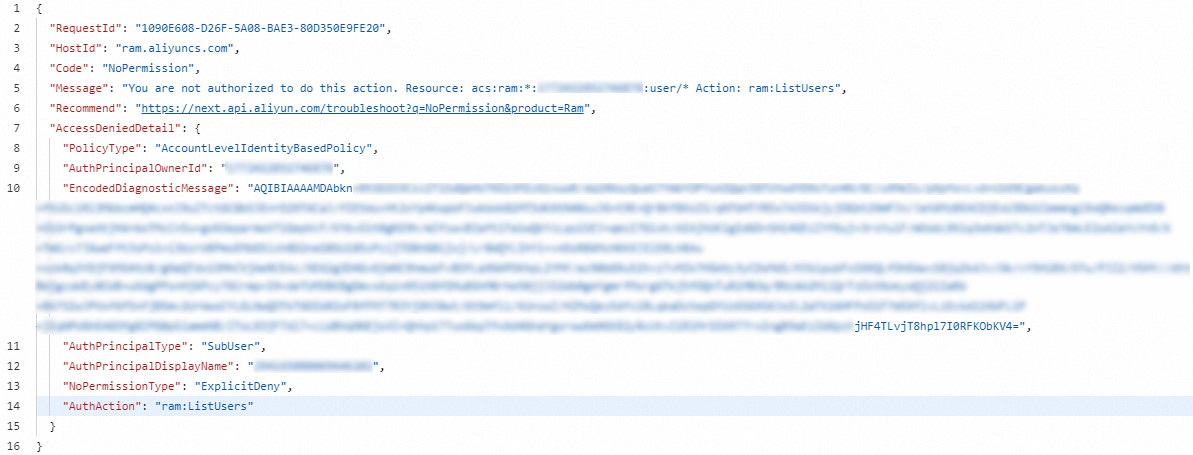
エラーのAccessDeniedDetailフィールドは、エラーの詳細を提供します。 エラーをトラブルシューティングするには、次の手順を実行します。
オペレーターを特定します。
AuthPrincipalType: 演算子のIDタイプ。 SubUserはRAMユーザー、AssumedRoleUserはRAMロール、FederatedはSSO IDを示します。
AuthPrincipalDisplayName: ID。 オペレータがRAMユーザの場合、ユーザのIDが表示される。 演算子がRAMロールの場合、ロールの名前とセッション名 (
RoleName:RoleSessionNameなど) が表示されます。 演算子がSSO IDの場合、IdPのタイプと名前 (saml-provider/AzureADなど) が表示されます。AuthPrincipalOwnerId: 現在のIDが属するAlibaba CloudアカウントのID。
オペレータの必要な権限を特定します。
AuthActionフィールドは、オペレーターが実行する権限を持たない操作を提供します。 操作に基づいて権限を確認または付与できます。
アクセス拒否エラーの原因となるポリシーの種類を特定します。
PolicyTypeフィールドは、アクセス拒否エラーの原因となるポリシーのタイプを提供します。 ポリシーは、制御ポリシー、セッションポリシー、ロール固有の信頼ポリシー (ロールポリシーを想定) 、またはアカウントまたはリソースグループレベルのIDベースのポリシーです。 詳細については、「ポリシー評価プロセス」をご参照ください。
ポリシーを調整する方法は、ポリシータイプによって異なります。
コントロールポリシーに基づいて操作が拒否された場合は、リソースディレクトリの管理アカウントに連絡して、必要な権限を付与する必要があります。 コントロールポリシーは、リソースディレクトリ内のメンバーに付与される権限を指定します。 制御ポリシーの決定は、単一のアカウント内で行われる決定よりも高い優先度を有する。
セッションポリシーに基づいて操作が拒否された場合は、アカウント管理者に連絡して、AssumeRole操作を呼び出して、オペレータにアタッチされているセッションポリシーを確認する必要があります。
ロール固有の信頼ポリシーに基づいて操作が拒否された場合は、アカウント管理者に連絡して、オペレーターが想定するRAMロールの信頼ポリシーを確認する必要があります。
IDベースのポリシーに基づいて操作が拒否された場合は、アカウント管理者に連絡して、オペレーターのIDにアタッチされているポリシーを確認する必要があります。
アクセス拒否エラーの原因が暗黙的拒否か明示的拒否かを確認してください。
Implicit deny: NoPermissionTypeフィールドに
ImplicitDenyが表示されます。 この場合、アカウント管理者に連絡して必要な権限を付与する必要があります。 アカウント管理者は、AuthActionフィールドで示される操作をAllowステートメントに追加できます。Explicit deny: NoPermissionTypeフィールドに
ExplicitDenyが表示されます。 この場合、アカウント管理者に連絡して、付与された権限を確認し、AuthActionフィールドで示される操作がDenyステートメントに含まれているかどうかを確認する必要があります。説明ポリシーがコントロールポリシーの場合、AuthActionフィールドで示される操作がAllowステートメントに含まれていない場合でも、ExplicitDenyが返されます。
サービスがアクセス許可診断をサポートしている場合、EncodedDiagnosticMessageで提供される情報をアカウント管理者と共有できます。 次に、アカウント管理者はRAMコンソールの [トラブルシューティング] ページに移動してエラーのトラブルシューティングを行うことができます。 アカウント管理者は、ram:DecodeDiagnosticMessage権限を持っている必要があります。