This topic describes how to troubleshoot access denied errors when you access Alibaba Cloud resources by using a Resource Access Management (RAM) user or a RAM role that does not have the required permissions.
Problem description
By default, RAM identities, such as RAM users and RAM roles, do not have operation permissions. RAM identities can access cloud resources only after the identities are explicitly granted the required permissions. The authorization effect for a RAM identity can be Allow or Deny. When a RAM identity performs an operation on Alibaba Cloud resources, the system reports an access denied error if the operation is explicitly denied or implicitly denied. An implicit deny indicates that a RAM identity is not explicitly authorized.
Access denied error in Console Access mode:
Permission DeniedAccess denied errors in OpenAPI Access mode:
NoPermission,Forbidden.RAM, andNotAuthorized
Solution
Console Access
If you perform operations in the Alibaba Cloud Management Console and you do not have the required permissions, the system reports the following error that contains the cause and details of the error. 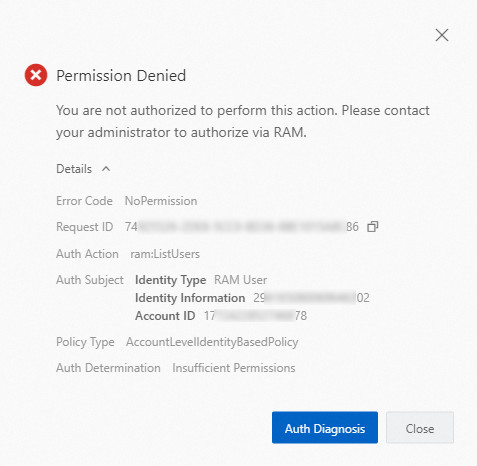
To troubleshoot the error, perform the following steps:
Identify the operator.
The Auth Subject parameter provides the details of the operator.
Identity Type: the identity type of the operator, including RAM users, RAM roles, and single sign-on (SSO) identities. SSO is also known as identity federation.
Identity Information: the identity. If the operator is a RAM user, the ID of the user is displayed. If the operator is a RAM role, the name and session name of the role are displayed, such as
RoleName:RoleSessionName. If the operator is an SSO identity, the type and name of the IdP are displayed, such assaml-provider/AzureAD.Account ID: the ID of the Alibaba Cloud account to which the current identity belongs.
Identify the required permissions of the operator.
The Auth Action parameter provides the operation that the operator does not have permissions to perform. You can check or grant permissions based on the operation.
Identify the type of the policy that causes the access denied error.
The Policy Type parameter provides the type of the policy that causes the access denied error. The policy can be a control policy, session policy, role-specific trust policy (Assume Role Policy), or identity-based policy at the account or resource group level. For more information, see Policy evaluation process.
The method to adjust the policy varies based on the policy type.
If the operation is denied based on a control policy, you must contact the management account of your resource directory to grant the required permissions. A control policy specifies the permissions that are granted to members in a resource directory. The decision of a control policy has a higher priority than the decision made within a single account.
If the operation is denied based on a session policy, you must contact the account administrator to check the session policy that is attached to the operator by calling the AssumeRole operation.
If the operation is denied based on a role-specific trust policy, you must contact the account administrator to check the trust policy of the RAM role that the operator assumes.
If the operation is denied based on an identity-based policy, you must contact the account administrator to check the policy that is attached to the identity of the operator.
Check whether the cause of the access denied error is an implicit deny or explicit deny.
Implicit deny: The error message indicates that you are not authorized to perform the current operation, and the Auth Determination parameter displays
Insufficient Permissions. In this case, you must contact the account administrator to grant the required permissions. The account administrator can add the operation indicated by the Auth Action parameter to the Allow statement.Explicit deny: The error message indicates that the current operation is explicitly denied, and the Auth Determination parameter displays
Explicit Deny. In this case, you must contact the account administrator to check the granted permissions and check whether the operation indicated by the Auth Action parameter is included in the Deny statement.NoteIf the policy is a control policy, Explicit Deny is returned even if the operation indicated by the Auth Action parameter is not included in the Allow statement.
If your service supports permission diagnostics, you can click Auth Diagnosis in the error message to view the cause of and solution to the error.
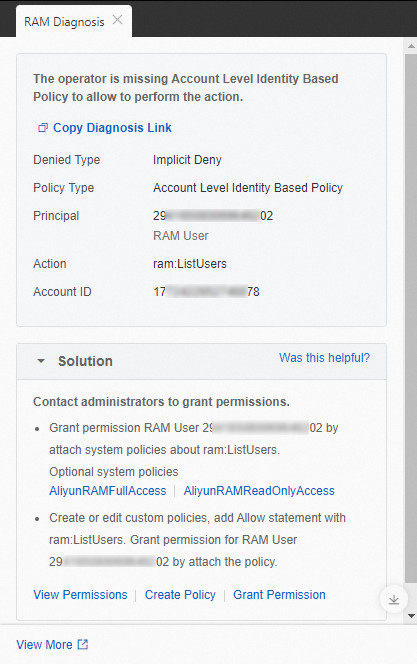
OpenAPI Access
If you access a service by using an Alibaba Cloud SDK, a CLI, or OpenAPI Explorer, you may encounter an access denied error. The returned error includes the details of the error. The following figure shows an access denied error that is returned when OpenAPI Explorer is used to access a service. 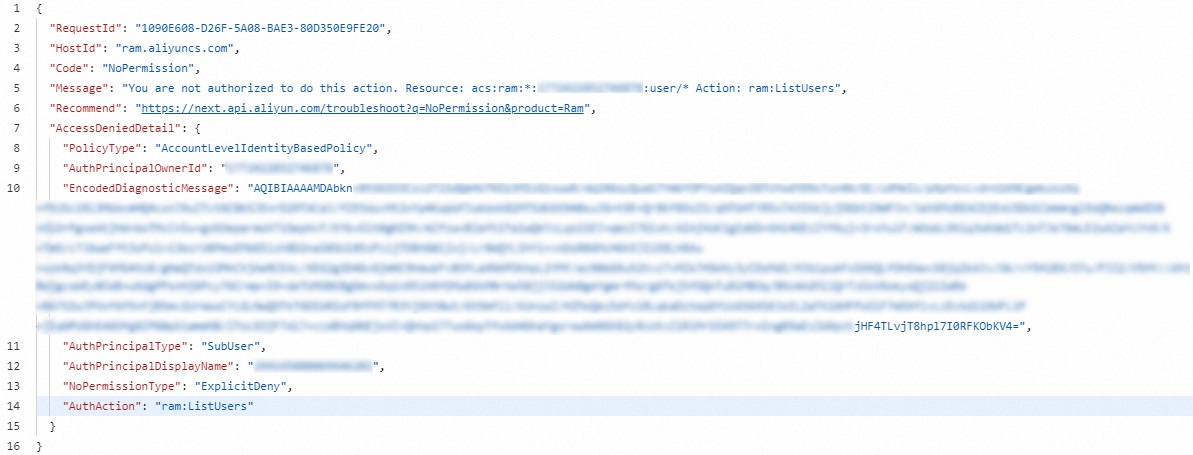
The AccessDeniedDetail field in the error provides the details of the error. To troubleshoot the error, perform the following steps:
Identify the operator.
AuthPrincipalType: the identity type of the operator. SubUser indicates a RAM user, AssumedRoleUser indicates a RAM role, and Federated indicates an SSO identity.
AuthPrincipalDisplayName: the identity. If the operator is a RAM user, the ID of the user is displayed. If the operator is a RAM role, the name and session name of the role are displayed, such as
RoleName:RoleSessionName. If the operator is an SSO identity, the type and name of the IdP are displayed, such assaml-provider/AzureAD.AuthPrincipalOwnerId: the ID of the Alibaba Cloud account to which the current identity belongs.
Identify the required permissions of the operator.
The AuthAction field provides the operation that the operator does not have permissions to perform. You can check or grant permissions based on the operation.
Identify the type of the policy that causes the access denied error.
The PolicyType field provides the type of the policy that causes the access denied error. The policy can be a control policy, session policy, role-specific trust policy (Assume Role Policy), or identity-based policy at the account or resource group level. For more information, see Policy evaluation process.
The method to adjust the policy varies based on the policy type.
If the operation is denied based on a control policy, you must contact the management account of your resource directory to grant the required permissions. A control policy specifies the permissions that are granted to members in a resource directory. The decision of a control policy has a higher priority than the decision made within a single account.
If the operation is denied based on a session policy, you must contact the account administrator to check the session policy that is attached to the operator by calling the AssumeRole operation.
If the operation is denied based on a role-specific trust policy, you must contact the account administrator to check the trust policy of the RAM role that the operator assumes.
If the operation is denied based on an identity-based policy, you must contact the account administrator to check the policy that is attached to the identity of the operator.
Check whether the cause of the access denied error is an implicit deny or explicit deny.
Implicit deny: The NoPermissionType field displays
ImplicitDeny. In this case, you must contact the account administrator to grant the required permissions. The account administrator can add the operation indicated by the AuthAction field to the Allow statement.Explicit deny: The NoPermissionType field displays
ExplicitDeny. In this case, you must contact the account administrator to check the granted permissions and check whether the operation indicated by the AuthAction field is included in the Deny statement.NoteIf the policy is a control policy, ExplicitDeny is returned even if the operation indicated by the AuthAction field is not included in the Allow statement.
If your service supports permission diagnostics, you can share the information provided in EncodedDiagnosticMessage with the account administrator. Then, the account administrator can go to the Troubleshoot page of the RAM console to troubleshoot the error. The account administrator must have the ram:DecodeDiagnosticMessage permission.