複数のユーザーが企業内のリソースに同時にアクセスできるようにするには、複数の Resource Access Management (RAM) ユーザーを作成し、最小権限の原則に基づいて RAM ユーザーに権限を付与します。 これにより、複数のユーザーが Alibaba Cloud アカウントのパスワードまたは AccessKey ペアを共有することを防ぎ、企業のセキュリティリスクを軽減します。 このトピックでは、RAM ユーザーとして CloudOps Orchestration Service (OOS) テンプレートを実行する方法について説明します。
シナリオ
ある企業が複数の Elastic Compute Service (ECS) インスタンスを購入しました。 2 つの ECS インスタンスには TagKey:TagValue というタグが付けられ、グループに追加されています。 スタッフ A には、OOS でテンプレート T を実行するための RAM ユーザー subUser1ForOOS を割り当てる必要があります。 テンプレート T は、TagKey:TagValue のタグが付いた ECS インスタンスでシェルコマンドを実行するために使用されます。 スタッフ A には、テンプレート T を読み取りおよび実行するための権限と、TagKey:TagValue のタグが付いた ECS インスタンスを管理するためにテンプレート T で指定された RunCommand などの API オペレーションを呼び出すための権限を付与する必要があります。
ポリシーの説明
上記の要件を満たすには、ポリシーに OOS リソースと ECS リソースに対する権限を含める必要があります。
OOS 関連の権限: テンプレートを実行およびクエリするための権限。
ECS 関連の権限:
TagKey:TagValueのタグが付いた ECS インスタンスを管理するためにテンプレート T で指定された API オペレーションを呼び出すための権限。
上記のポリシーを作成したら、スタッフ A に割り当てられた RAM ユーザーまたはスタッフ A と同じ職務を持つユーザーグループにポリシーをアタッチします。
手順
ステップ 1: ECS インスタンスにタグを追加する
左側のナビゲーションウィンドウで、 を選択します。
上部のナビゲーションバーで、ECS インスタンスが存在するリージョンを選択します。

ECS インスタンスを見つけ、[アクション] 列で を選択します。
[タグの設定] ダイアログボックスで、[タグキー] と [タグ値] を設定し、[OK] をクリックします。
この例では、タグキーは
TagKeyに設定され、タグ値はTagValueに設定されています。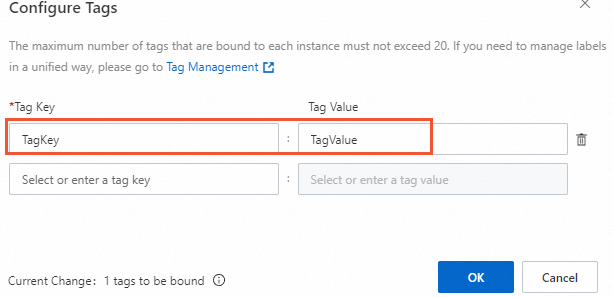
ステップ 2: RAM ユーザーを作成し、RAM ユーザーに権限を付与する
RAM コンソール にログインし、
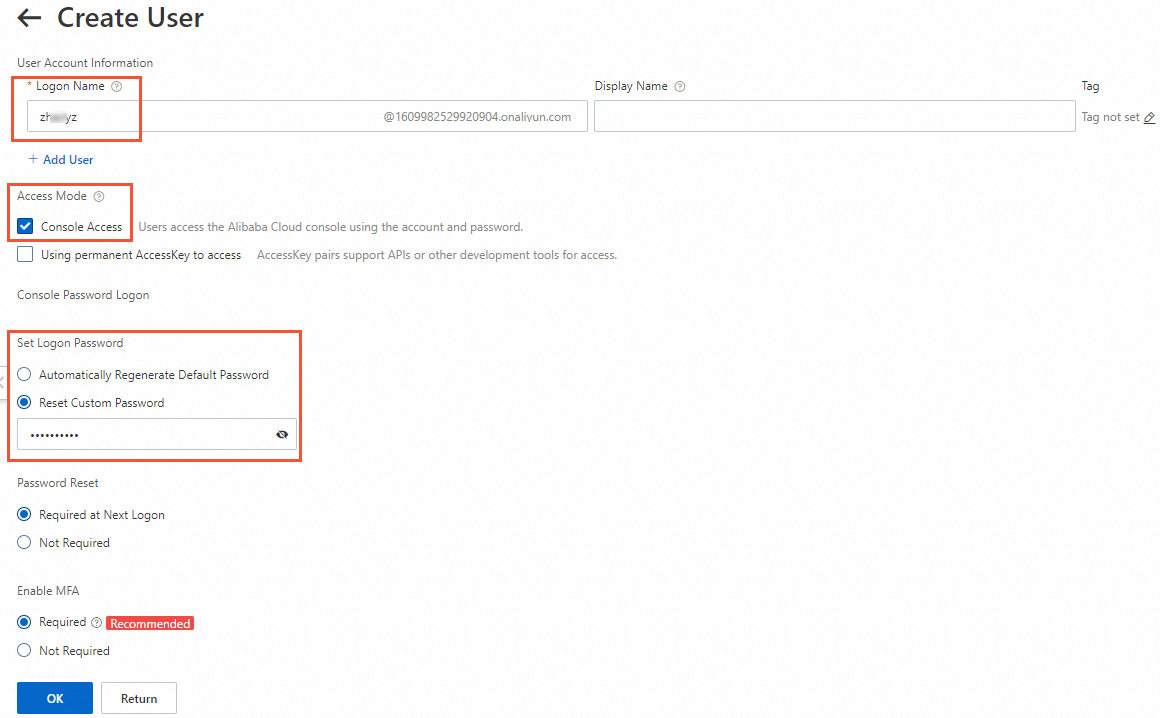
subUser1ForOOSなどの RAM ユーザーを作成します。次の表に主要なパラメーターを示します。 詳細については、「RAM ユーザーを作成する」をご参照ください。
パラメーター
説明
[ログイン名]
RAM ユーザーの名前を入力します。 名前に使用できるのは、文字、数字、ピリオド (
.)、アンダースコア (_)、ハイフン (-) です。 名前の長さは最大 64 文字です。[アクセスモード]
パスワードを使用して Alibaba Cloud 管理コンソールにアクセスするには、[コンソールアクセス] を選択します。
[ログインパスワードの設定]
[カスタムパスワードをリセット] を選択し、カスタムパスワードを指定します。
カスタムポリシーを作成します。
を選択して、OOS 用のカスタムポリシーと ECS 用のカスタムポリシーを作成します。 詳細については、「カスタムポリシーを作成する」をご参照ください。
説明ポリシーコンテンツの
$AliyunMasterAccountID、$TagKey、$TagValue、および$RegionIDは、Alibaba Cloud アカウントの ID、ECS インスタンスに構成されたタグキーとタグ値、およびリージョン ID に置き換える必要があります。必要な権限を RAM ユーザーに付与します。
を選択して、OOS カスタムポリシーと ECS カスタムポリシーを RAM ユーザーにアタッチします。 詳細については、「RAM ユーザーに権限を付与する」をご参照ください。
ステップ 3: OOS テンプレートを実行する
RAM ユーザーとして CloudOps Orchestration Service コンソール にログインします。
左側のナビゲーションウィンドウで、 を選択します。
[パブリックテンプレート] ページで、
ACS-ECS-BulkyRunCommandテンプレートを検索し、[実行の作成] をクリックします。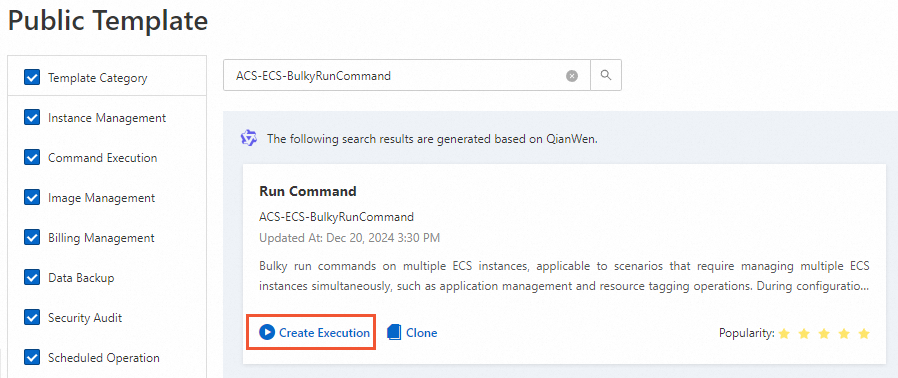
[基本情報] ステップで、テンプレート情報を確認し、[次のステップ: パラメーター設定] をクリックします。
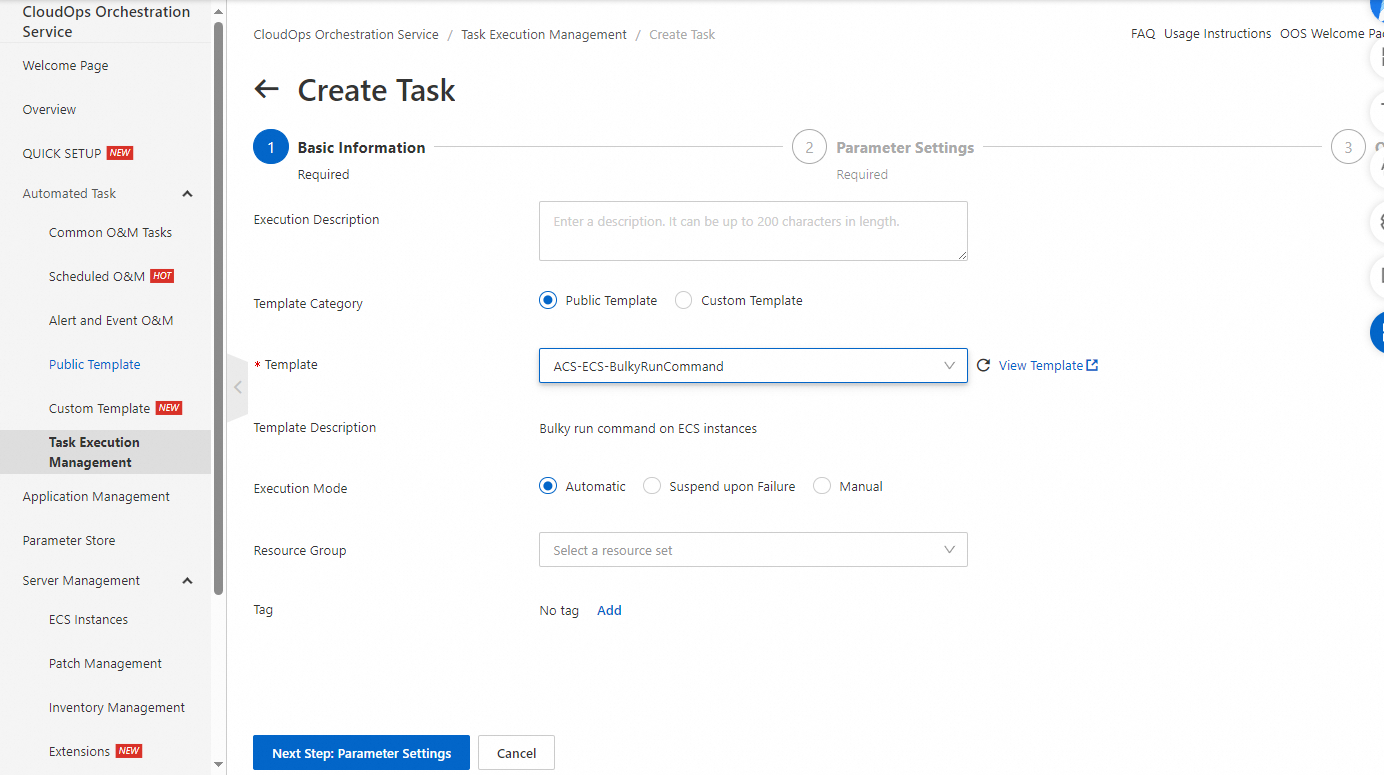
[パラメーター設定] ステップで、パラメーターを設定し、[次のステップ: OK] をクリックします。
[targetinstance] を [インスタンスタグを指定] に設定し、[タグキー] と [タグ値] を指定します。

設定を確認し、[作成] をクリックします。