このトピックでは、RAM (Resource Access Management) ユーザーに権限を付与する方法について説明します。
手順
Alibaba Cloud アカウントを使用して、RAM コンソールにログインします。
カスタムポリシーを作成します。
左側のナビゲーションウィンドウから、 を選択します。
ポリシー ページで ポリシーの作成 をクリックします。
ポリシーの作成 ページで、[JSON] タブをクリックします。
説明RAMは、ポリシーを作成するためのビジュアル編集モードとドキュメント編集モードを提供します。 Key Management Service (KMS) リソースのカスタムポリシーを作成するときは、ドキュメント編集モードを使用する必要があります。 ビジュアル編集モードを使用する場合、すべてのKMSリソースとすべての操作のみを選択できます。
ポリシードキュメントを変更し、[次へ] をクリックしてポリシー情報を編集します。
KMSポリシードキュメントを編集するときは、カスタム権限付与ステートメントを指定する必要があります。 ステートメントには、Effect、Action、Resource、およびConditionの要素が含まれます。 Condition要素はオプションです。 詳細については、「付録: サポートされているリソース、アクション、および条件」をご参照ください。
説明RAMポリシーの構文と構造の詳細については、「ポリシー構造と構文」をご参照ください。
ポリシー名と説明を指定します。 次に、プロンプトに従ってポリシードキュメントを確認して最適化します。
[OK] をクリックします。
カスタムポリシーをRAMユーザーにアタッチします。
左側のナビゲーションペインで、 を選択します。
ユーザー ページで、カスタムポリシーをアタッチするRAMユーザーを見つけ、[操作] 列の [権限の追加] をクリックします。
[権限付与] パネルでパラメーターを設定し、[権限付与] をクリックします。
パラメーター
説明
リソーススコープ
権限を有効にするスコープ。 KMSはリソースグループ機能をサポートしていません。 [アカウント] を選択する必要があります。
プリンシパル
権限を付与するRAMユーザー。 Principalパラメーターは、特定のRAMユーザーに自動的に設定されます。 別のRAMユーザーを指定できます。
ポリシー
ビジネス要件に基づいてカスタムポリシーを選択します。
付録: サポートされるリソース、アクション、および条件
リソース
KMSは、キーコンテナー、シークレットコンテナー、エイリアスコンテナー、キー、シークレット、エイリアスのリソースタイプを定義します。 リソースのAlibaba Cloud Resource Name (ARN) に基づいて、RAMポリシーでResource要素を設定できます。 次の例では、キーリソースのARNが照会されます。
KMS コンソールにログインします。 上部のナビゲーションバーで、リージョンを選択します。 左側のナビゲーションウィンドウで、 を選択します。
キー タブで、ARNを照会するキーを見つけ、操作 列の 詳細 をクリックします。 詳細ページで、キーのARNを表示できます。
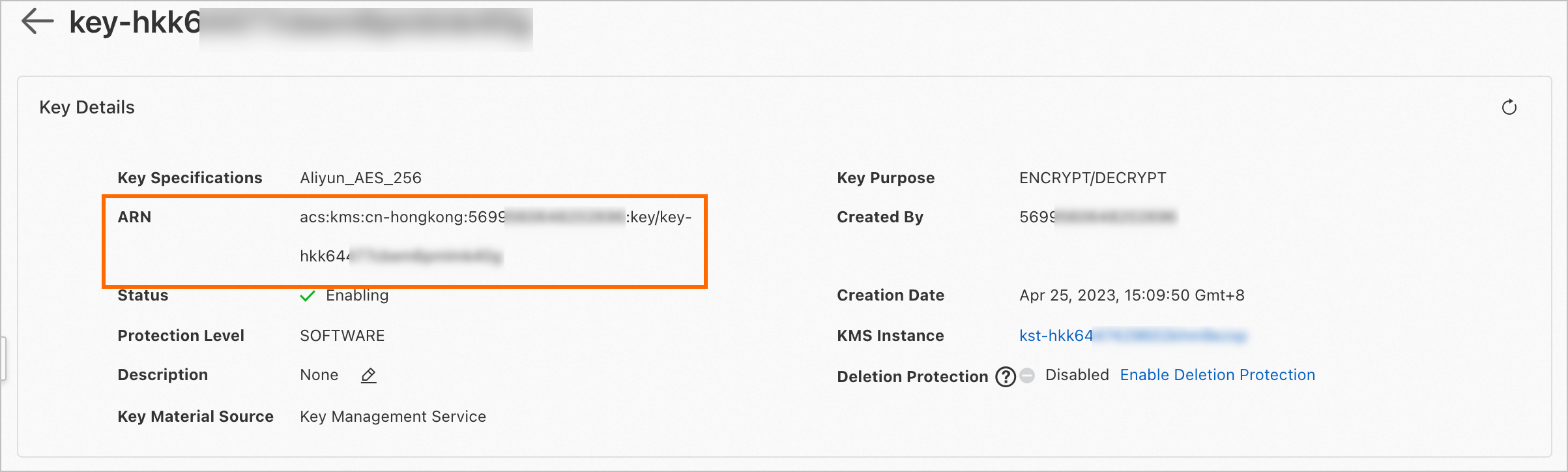 次の表に、さまざまなリソースタイプのARN形式を示します。 説明
次の表に、さまざまなリソースタイプのARN形式を示します。 説明${region}と${account}を実際のリージョンとAlibaba Cloudアカウントに置き換えます。 ビジネス要件に基づいてリソースの範囲を絞り込むこともできます。${region}は、アスタリスク (*) ワイルドカード文字をサポートしています。リソースタイプ
ARN
キーコンテナー
acs:kms :${ region }:${ account}: キー
秘密のコンテナ
acs:kms :${ region }:${ account}:secret
Aliasコンテナ
acs:kms :${ region }:${ account}: エイリアス
Key
acs:kms :${ region }:${ account}:key/${key-id}
説明キーリソースのARNは、アスタリスク (*) ワイルドカード文字をサポートしています。 例:
acs:kms :${ region }:${ account}:key/*: アカウント内のリージョン内のすべてのキーを指定します。acs:kms:* :${ account}:key/*: アカウント内のすべてのリージョンのすべてのキーを指定します。
シークレット
acs:kms :${ region }:${ account}:secret/${secret-name}
説明秘密リソースのARNは、アスタリスク (*) ワイルドカード文字をサポートします。
acs:kms :${ region }:${ account}:secret/*: アカウント内のリージョンのすべてのシークレットを指定します。acs:kms :${ region }:${ account}:secret/prefix *: アカウント内のリージョンでprefixで始まるすべてのシークレットを指定します。
Alias
acs:kms :${ region }:${ account}:alias/${alias-name}
Action
KMSは、アクセス制御を必要とする各API操作のアクションを定義します。 RAMポリシーでは、アクションはkms:<api-name> 形式です。
DescribeRegions操作では、アクセス制御は必要ありません。 この操作は、Alibaba Cloudアカウント、RAMユーザー、またはRAMロールがRAM認証に合格した後に呼び出すことができます。 RAM認証に合格した後のAlibaba Cloudアカウント、RAMユーザー、またはRAMロール。
次の表に、各API操作に対応するRAMアクションとリソースタイプを示します。
${region} と ${account} を実際のリージョンとAlibaba Cloudアカウントに置き換えます。 ビジネス要件に基づいてリソースの範囲を絞り込むこともできます。 ${region} は、アスタリスク (*) ワイルドカード文字をサポートしています。
Condition
Condition要素は、ポリシーが有効になるために必要な条件を指定します。 この要素はオプションです。 RAMポリシーに条件キーを追加して、KMSへのアクセスを管理できます。 RAM認証は、追加された条件が満たされた場合にのみ成功します。
共通条件キーの使用: 条件キーは
acs:<condition-key>形式です。 たとえば、acs:CurrentTimeを使用して、RAMポリシーの有効期間を指定できます。詳細については、「ポリシー要素」をご参照ください。
Alibaba Cloudサービスに固有の条件キーを使用する: 条件キーは
kms:<condition-key>形式です。 KMSでサポートされているAlibaba Cloudサービス固有の条件キーの詳細については、「Condition keys」をご参照ください。