アプリケーションロードバランサー(ALB)インスタンスは、データプレーンで Terway ネットワークプラグインを使用する Alibaba Cloud Container Service for Kubernetes(ACK)クラスターにアクセスするために、Service Mesh(ASM)インスタンスのイングレスゲートウェイと統合できます。この機能は、サービス管理を簡素化し、サービス間の通信のセキュリティを確保し、可観測性を向上させ、開発と O&M のワークロードを削減します。このトピックでは、ALB インスタンスとイングレスゲートウェイを統合する方法について説明します。Service Mesh
前提条件
ACK クラスターが ASM インスタンスに追加されていること。ASM インスタンスと ACK クラスターは、次の要件を満たしている必要があります。
ASM インスタンスは Enterprise Edition である必要があります。
ACK クラスター:
Terway ネットワークプラグインが使用されていること。
Cloud Controller Manager(CCM)コンポーネントが v1.9.3.313-g748f81e-aliyun 以降であること。詳細については、「CCM」をご参照ください。
ALB Ingress コントローラーがインストールされていること。詳細については、「コンポーネントの管理」をご参照ください。
デフォルトの名前空間で、自動サイドカープロキシインジェクションが有効になっていること。詳細については、「グローバル名前空間の管理」トピックの「自動サイドカープロキシインジェクションの有効化」セクションをご参照ください。
イングレスゲートウェイが作成されていること。このイングレスゲートウェイでは、[CLB インスタンスタイプ] が [プライベートアクセス] に設定され、[サービスポート] が [80] に設定されていること。詳細については、「イングレスゲートウェイの作成」をご参照ください。
手順 1: サンプルアプリケーションをデプロイする
データプレーン上のクラスターの kubeconfig ファイルの内容に基づいてクラスターに接続し、次のコマンドを実行して Bookinfo アプリケーションをデプロイします。詳細については、「ASM インスタンスに追加された ACK クラスターにアプリケーションをデプロイする」をご参照ください。
kubectl apply -f https://raw.githubusercontent.com/istio/istio/master/samples/bookinfo/platform/kube/bookinfo.yaml手順 2: Istio リソースを作成する
この例では、テスト用に Istio ゲートウェイと仮想サービスを作成します。
Istio ゲートウェイを作成します。
ASM コンソール にログインします。左側のナビゲーションペインで、 を選択します。
[メッシュ管理] ページで、ASM インスタンスの名前をクリックします。左側のナビゲーションペインで、 を選択します。
[ゲートウェイ] ページで、[作成] をクリックし、次の図に示すパラメーターを構成します。
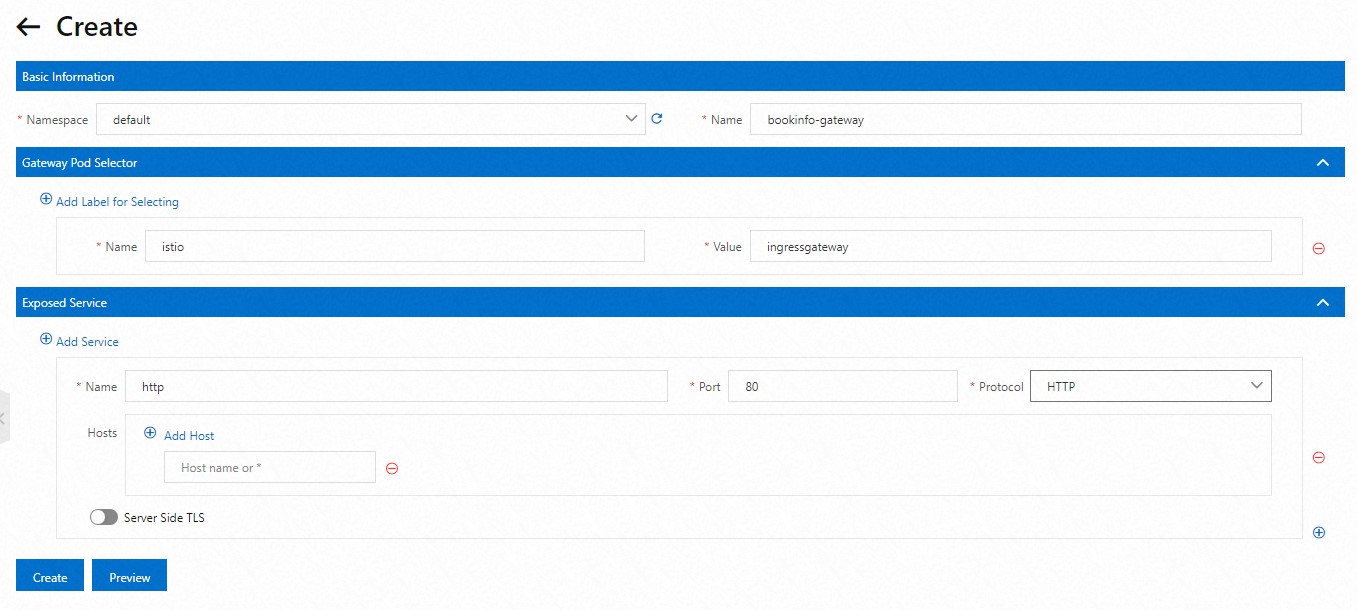
[作成] ページの下部にある、[プレビュー] をクリックして、Istio ゲートウェイの YAML ファイルを表示します。YAML ファイルの情報を確認した後、[送信] をクリックします。[作成] ページの下部にある、[作成] をクリックします。
仮想サービスを作成し、トラフィックルーティングを構成します。
ASM インスタンスの詳細ページで、左側のナビゲーションペインの を選択します。
[virtualservice] ページで、[作成] をクリックして、bookinfo-gateway ゲートウェイの仮想サービスを構成します。
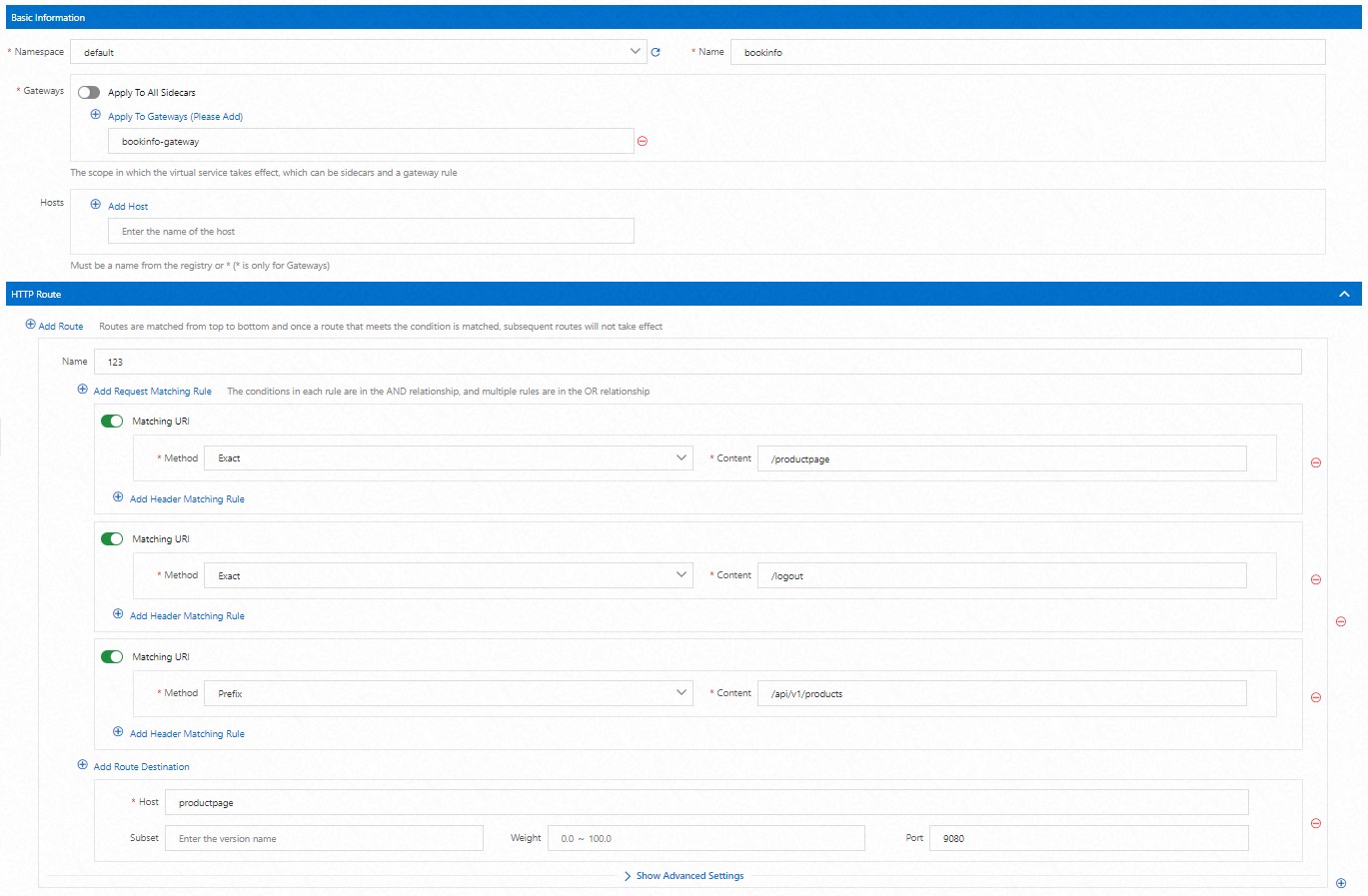
[作成] ページの下部にある [プレビュー] をクリックして、仮想サービスの YAML ファイルを表示します。YAML ファイルの情報を確認した後、[送信] をクリックします。[作成] ページの下部にある [作成] をクリックします。
手順 3: AlbConfig オブジェクトを作成する
シナリオ 1: 既存の標準 ALB インスタンスをイングレスゲートウェイと統合する必要がある場合
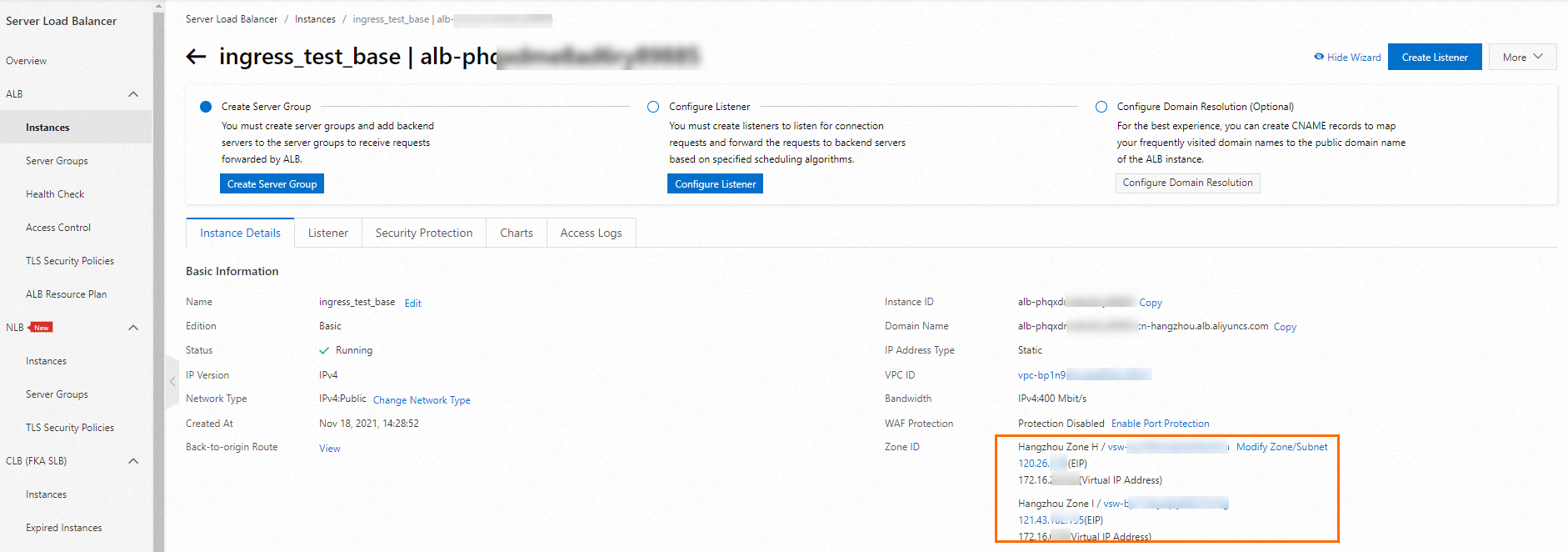
ALB コンソール で ALB インスタンスの ID を取得します。
次の内容を含む alb-demo.yaml ファイルを作成します。
config セクションの
idの値を ALB インスタンスの ID に置き換えます。apiVersion: alibabacloud.com/v1 kind: AlbConfig metadata: name: default spec: config: id: alb-xxxxx forceOverride: false次のコマンドを実行して、AlbConfig オブジェクトを作成します。
kubectl apply -f alb-demo.yaml
シナリオ 2: ALB インスタンスを作成し、イングレスゲートウェイと統合する必要がある場合
次の内容を含む alb-demo.yaml ファイルを作成します。詳細については、「ALB Ingress の作成」をご参照ください。
自動的に作成される ALB インスタンスの名前を alb-demo に設定します。
apiVersion: alibabacloud.com/v1 kind: AlbConfig metadata: name: default spec: config: name: alb-demo addressType: Internet zoneMappings: - vSwitchId: vsw-uf6ccg2a9g71hx8go**** - vSwitchId: vsw-uf6nun9tql5t8nh15****パラメーター
説明
spec.config.name作成する ALB インスタンスの名前。
addressTypeALB インスタンスがサービスを提供するために使用する IP アドレスタイプ。このパラメーターは必須です。有効な値:
Internet: ALB インスタンスはパブリック IP アドレスを使用します。Ingress のドメイン名は、ALB インスタンスのパブリック IP アドレスに解決されます。そのため、ALB インスタンスにはインターネット経由でアクセスできます。これがデフォルト値です。
Intranet: ALB インスタンスはプライベート IP アドレスを使用します。Ingress のドメイン名は、プライベート IP アドレスに解決されます。そのため、ALB インスタンスは、ALB インスタンスがデプロイされている仮想プライベートクラウド(VPC)内からのみアクセスできます。
zoneMappingsALB Ingress によって使用される vSwitch の ID。少なくとも 2 つの vSwitch ID を指定する必要があり、vSwitch は異なるゾーンにデプロイする必要があります。 vSwitch のゾーンは、ALB Ingress でサポートされている必要があります。このパラメーターは必須です。ALB Ingress でサポートされているリージョンとゾーンの詳細については、「ALB が利用可能なリージョンとゾーン」をご参照ください。vSwitch の作成方法の詳細については、「vSwitch の作成と管理」をご参照ください。
次のコマンドを実行して、AlbConfig オブジェクトを作成します。
kubectl apply -f alb-demo.yaml
手順 4: IngressClass リソースを作成する
次の内容を含む alb.yaml ファイルを作成します。
apiVersion: networking.k8s.io/v1 kind: IngressClass metadata: name: alb spec: controller: ingress.k8s.alibabacloud/alb parameters: apiGroup: alibabacloud.com kind: AlbConfig name: default scope: Cluster次のコマンドを実行して、IngressClass リソースを作成します。
kubectl apply -f alb.yaml予期される出力:
ingressclass.networking.k8s.io/alb created
手順 5: Ingress インスタンスを作成する
イングレスゲートウェイは [istio-system] 名前空間に作成されます。データプレーン上の ACK クラスターの [istio-system] 名前空間に Ingress インスタンスを作成する必要があります。ポート番号は 80 で、イングレスゲートウェイの作成時に指定したものと同じです。
次の内容を含む asm-gateway-ingress.yaml ファイルを作成します。
apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: asm-gateway-ingress namespace: istio-system spec: ingressClassName: alb rules: - http: paths: - backend: service: name: istio-ingressgateway port: number: 80 path: /* pathType: ImplementationSpecific次のコマンドを実行して、Ingress インスタンスを作成します。
kubectl apply -f asm-gateway-ingress.yaml
手順 6: イングレスゲートウェイにアクセスする
次のコマンドを実行して、Ingress インスタンスのエンドポイントをクエリします。
kubectl get ing -n istio-system予期される出力:
NAME CLASS HOSTS ADDRESS PORTS AGE asm-gateway-ingress alb * alb-xxxx.xxxx.alb.aliyuncs.com 80 18h出力には、Ingress インスタンスのエンドポイントが
alb-xxxx.xxxx.alb.aliyuncs.comと表示されます。次のいずれかの方法でイングレスゲートウェイにアクセスします。
方法 1: ブラウザーに
http://alb-xxxx.xxxx.alb.aliyuncs.com/productpageと入力して、イングレスゲートウェイにアクセスします。 alb-xxxx.xxxx.alb.aliyuncs.com は、前の手順で取得した Ingress インスタンスのエンドポイントです。方法 2: ALB コンソールにログインして ALB インスタンスのパブリック IP アドレスを取得し、それを使用してイングレスゲートウェイにアクセスします。ALB インスタンスがドメイン名にバインドされている場合は、ドメイン名を使用してイングレスゲートウェイにアクセスできます。