HTTPSリスナーを設定するときは、SSLまたはTransport Layer Security (TLS) 証明書をリスナーに関連付けて、クライアントとリスナー間の接続を暗号化する必要があります。 このトピックでは、Application Load Balancer (ALB) Ingressを使用してHTTPSリスナーの証明書を設定する方法について説明します。
証明書設定方法の比較
ALB Ingressを使用すると、自動証明書検出の設定、Kubernetes Secretsとして証明書を管理し、AlbConfigsで証明書を指定できます。 次の表は、前述の方法を比較しています。
項目 | 自動証明書検出の設定 | AlbConfigsでの証明書の指定 | 証明書をKubernetes Secretsとして管理 |
証明書ストレージ | 証明書は証明書管理サービスに保存されます。 | 証明書はKubernetes Secretsとして保存されます。 | |
証明書の発見 | 証明書は、証明書にバインドされているドメイン名に基づいて検出されます。 | 証明書は、そのIDに基づいて検出されます。 | 証明書は、証明書が格納されているシークレットに基づいて検出されます。 |
シナリオ | この方法は、Certificate Management Serviceコンソールで購入した証明書、またはCertificate Management Serviceコンソールにアップロードされた証明書に適しています。 | この方法は、クラスターで管理される証明書に適しています。 たとえば、cert-managerを使用して証明書を管理する場合、証明書をSecretsに格納できます。 | |
名前空間全体で証明書を使用する | 対応 | サポートされていません。 シークレットとして保存された証明書は、シークレットの名前空間内でのみ使用できます。 | |
証明書を更新する方法 | certificate Management Serviceコンソールで、新しい証明書をアップロードするか、元の証明書を更新する必要があります。 次に、証明書が関連付けられているIngressの設定を手動で変更する必要があります。 | 証明書が格納されているシークレットの設定を更新する必要があります。 | |
ALBインスタンスは、最大25の証明書をサポートします。 ほとんどの場合、ALBインスタンスで使用される証明書の数は、Ingressに関連付けられた証明書を含め、インスタンスのすべてのリスナーに関連付けられた証明書の総数に等しくなります。 詳細については、「ALBクォータの計算方法」をご参照ください。
異なる方法で構成された証明書の互換性
さまざまな方法で構成された証明書の互換性を次の表に示します。
証明書の設定方法 | 説明 |
証明書は自動証明書検出を使用して設定され、別の証明書はKubernetes Secretを使用して設定されます。 |
|
証明書は自動証明書検出を使用して構成され、別の証明書はAlbConfigで指定されます。両方の証明書は同じリスナーに関連付けられています。 | リスナーは、AlbConfigで指定された証明書のみを使用します。 |
証明書はKubernetes Secretを使用して設定され、別の証明書はAlbConfigで指定されます。両方の証明書は同じリスナーに関連付けられています。 | 両方の証明書が使用されます。 |
前提条件
信頼できる証明書が取得されます。 次のいずれかの方法を使用して、証明書を取得できます。
証明書管理サービスコンソールで証明書を購入します。 詳細については、「SSL証明書の購入」をご参照ください。
別の認証局 (CA) によって発行された証明書を購入します。
(オプション) 自己署名証明書を作成します。 詳細については、「自己署名証明書の作成」をご参照ください。
手順

手順1: AlbConfigでHTTPSリスナーを作成する
デフォルトでは、AlbConfigはポート80のHTTPリスナーで構成されています。 HTTPSリスナーを作成し、証明書を設定する必要があります。 証明書が設定されていない場合、HTTPSリスナーは使用できなくなり、証明書がないためにコントローラーが失敗します。 詳細については、「リスナーの作成」をご参照ください。
ACKコンソールの使用
ACKコンソールにログインします。 左側のナビゲーションウィンドウで、[クラスター] をクリックします。
[クラスター] ページで、管理するクラスターの名前をクリックします。 左側のウィンドウで、 を選択します。
[リソースオブジェクト] タブで、検索ボックスに [AlbConfig] と入力し、表示された [AlbConfig] をクリックします。
[AlbConfig] パネルで、名前がalb (デフォルト) またはその他のAlbConfigリソースを検索し、[操作] 列の [YAMLの編集] をクリックします。
[YAMLで表示] パネルで、
spec.listeners.portおよびspec.listeners.protocolフィールドを追加します。 [OK] をクリックします。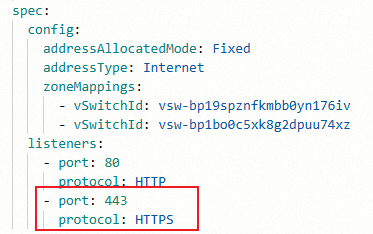
kubectlを使う
次のコマンドを実行して、
albconfig設定ファイルを編集します。kubectl edit albconfig <Albconfig_Name>ビジネス要件に基づいて設定を変更します。 Albconfigで
portパラメーターとprotocolパラメーターを設定して、対応するリスナーを作成できます。apiVersion: alibabacloud.com/v1 kind: AlbConfig metadata: name: alb spec: config: addressAllocatedMode: Fixed addressType: Internet zoneMappings: - vSwitchId: vsw-bp19sXXXXXXX176iv - vSwitchId: vsw-bp1boXXXXXXXu74xz listeners: - port: 80 protocol: HTTP - port: 443 # New field. protocol: HTTP # New field. Valid values: HTTP, HTTPS, and QUIC.
(オプション) ステップ2: 自己署名証明書の作成
次のOpenSSLコマンドを実行して、自己署名証明書を作成します。
デフォルトでは、自己署名証明書はブラウザまたはクライアントから信頼されません。 自己署名証明書を使用すると、セキュリティ警告が表示されることがあります。 この例で生成された自己署名証明書は参照用です。 運用環境では証明書を使用しないでください。
上記のコマンドラインでは、
demo.alb.ingress.topドメイン名が自己署名証明書に関連付けられています。 ドメイン名をカスタムドメイン名に置き換えることができます。
openssl genrsa -out albtop-key.pem 4096
openssl req -subj "/CN=demo.alb.ingress.top" -sha256 -new -key albtop-key.pem -out albtop.csr # Replace demo.alb.ingress.top with the domain name that you want to use.
echo subjectAltName = DNS:demo.alb.ingress.top > extfile.cnf # Replace demo.alb.ingress.top with the domain name that you want to use.
openssl x509 -req -days 3650 -sha256 -in albtop.csr -signkey albtop-key.pem -out albtop-cert.pem -extfile extfile.cnf次のコマンドを実行して、証明書と秘密鍵を表示します。
cat albtop-key.pem # The private key.cat albtop-cert.pem # The certificate.次のコマンドを実行して、Base64で証明書および秘密鍵ファイルをエンコードします。
echo -n `cat albtop-key.pem` | base64 # Encode the private key file in Base64.echo -n `cat albtop-cert.pem` | base64 # Encode the certificate file in Base64.
手順3: サンプルリソースの作成
ACKコンソールの使用
ACKコンソールにログインします。 左側のナビゲーションウィンドウで、[クラスター] をクリックします。
[クラスター] ページで、管理するクラスターの名前をクリックします。 左側のウィンドウで、 を選択します。
[YAMLから作成] をクリックします。
サンプルテンプレート: [カスタム] を選択します。
テンプレート: 次のコードをコードエディターにコピーします。 この設定ファイルは、デプロイメント、サービス、IngressClasses、およびIngressに適しています。
設定が完了したら、[作成] をクリックします。 [作成済み] メッセージが表示されます。
次の手順を実行して、展開とサービスが作成されていることを確認します。
左側のナビゲーションウィンドウで、[ワークロード]> [デプロイメント] を選択します。
https-deployという名前のデプロイが表示されます。左側のナビゲーションウィンドウで、[ネットワーク]> [サービス] を選択します。
https-svcという名前のサービスがデプロイされます。
kubectlを使う
ALB Ingressを通常どおり機能させるには、作成したAlbConfigに加えて、Deployment、Service、IngressClass、およびIngressを作成する必要があります。 次のYAMLテンプレートを使用して、上記のリソースを作成できます。
https-quickstart.yamlという名前のファイルを作成し、次の内容をファイルにコピーします。
apiVersion: networking.k8s.io/v1 kind: IngressClass metadata: name: https-ingressclass spec: controller: ingress.k8s.alibabacloud/alb parameters: apiGroup: alibabacloud.com kind: AlbConfig name: alb # Set the value to the name of the AlbConfig you created. --- apiVersion: apps/v1 kind: Deployment metadata: name: https-deploy spec: replicas: 1 selector: matchLabels: app: https-deploy template: metadata: labels: app: https-deploy spec: containers: - image: registry.cn-hangzhou.aliyuncs.com/acs-sample/old-nginx:latest imagePullPolicy: IfNotPresent name: https-deploy ports: - containerPort: 80 protocol: TCP --- apiVersion: v1 kind: Service metadata: name: https-svc spec: ports: - name: port1 port: 443 protocol: TCP targetPort: 80 selector: app: https-deploy sessionAffinity: None type: ClusterIP次のコマンドを実行して、前述のリソースを作成します。
kubectl apply -f https-quickstart.yaml
ステップ4: 証明書の設定
自動証明書検出の設定
ACKコンソールの使用
自己署名証明書を証明書管理サービスにアップロードした後、Ingress設定のtlsフィールドの証明書にバインドされているドメイン名を指定できます。 このようにして、ALB Ingressはアップロードされた証明書を自動的に検出して使用できます。
証明書管理サービスコンソールに自己署名証明書をアップロードします。 詳細については、「SSL証明書のアップロードと共有」をご参照ください。
ACKコンソールにログインします。 左側のナビゲーションウィンドウで、[クラスター] をクリックします。
[クラスター] ページで、管理するクラスターの名前をクリックします。 左側のウィンドウで、 を選択します。
[Ingress] ページで、更新するIngressを見つけ、[操作] 列の [更新] をクリックします。 [Ingressの変更] パネルで、パラメーターを設定します。 下表にパラメーターを示します。
パラメーター
説明
例
TLS設定
TLS認証を有効にするかどうかを指定します。 IngressのTLS認証を有効にできます。
ドメイン名: カスタムドメイン名を入力します。
シークレット: 使用するシークレットを選択します。
説明このパラメーターを空のままにすると、自動証明書検出が使用されます。
シークレットを作成するには、次の手順を実行します。
Secretフィールドの右側にある [作成] をクリックします。
[シークレットの作成] ダイアログボックスで、[名前] 、[証明書] 、および [キー] パラメーターを設定します。 [OK] をクリックします。
[シークレット] ドロップダウンリストから作成したシークレットを選択します。
[+ 追加] をクリックすると、さらにTLS証明書を追加できます。
ドメイン名: demo.alb.ingress.top
Secret: このパラメーターは空のままにします。
(オプション) 注釈
カスタム注釈の名前と値を入力できます。 ドロップダウンリストから名前で注釈を選択または検索することもできます。 Ingressアノテーションの詳細については、「アノテーション」をご参照ください。
[+ 注釈の追加] をクリックして注釈を追加します。 ACKは、追加できるIngressアノテーションの数を制限しません。
設定は必要ありません。
説明HTTPとHTTPSの両方のリクエストをリッスンする場合は、次の注釈を追加します。
名前:
alb.ingress.kubernetes.io/listen-ports値:
[{"HTTP": 80 },{ "HTTPS": 443}]
kubectlを使う
自己署名証明書を証明書管理サービスにアップロードした後、Ingress設定のtlsフィールドの証明書にバインドされているドメイン名を指定できます。 このようにして、ALB Ingressはアップロードされた証明書を自動的に検出して使用できます。
証明書管理サービスコンソールに自己署名証明書をアップロードします。 詳細については、「SSL証明書のアップロードと共有」をご参照ください。
次のコマンドを実行して、Ingressを変更します。
kubectl edit ingress https-ingresstlsフィールドを追加し、証明書にバインドされたドメイン名を指定します。apiVersion: networking.k8s.io/v1 kind: Ingress metadata: # annotations: # alb.ingress.kubernetes.io/listen-ports: '[{"HTTP": 80},{"HTTPS": 443}]' # Add this annotation if you want to listen for both HTTP and HTTPS requests. name: https-ingress spec: ingressClassName: https-ingressclass rules: - host: demo.alb.ingress.top # Replace demo.alb.ingress.top with the domain name that you want to use. http: paths: - backend: service: name: https-svc port: number: 443 path: / pathType: Prefix tls: # New field. -hosts: # New field. - demo.alb.ingress.top # New field. Set the value to the domain name bound to the certificate. The domain name must be the same as the domain name specified in the "rules: host" field.
証明書を秘密として管理する
ACKコンソールの使用
ACKコンソールにログインします。 左側のナビゲーションウィンドウで、[クラスター] をクリックします。
[クラスター] ページで、管理するクラスターの名前をクリックします。 左側のウィンドウで、 を選択します。
[Ingress] ページで、更新するIngressを見つけ、[操作] 列の [更新] をクリックします。 [Ingressの変更] パネルで、パラメーターを設定します。 下表にパラメーターを示します。
パラメーター
説明
例
TLS設定
TLS認証を有効にするかどうかを指定します。 IngressのTLS認証を有効にできます。
ドメイン名: カスタムドメイン名を入力します。
シークレット: 使用するシークレットを選択します。
説明このパラメーターを空のままにすると、自動証明書検出が使用されます。
シークレットを作成するには、次の手順を実行します。
Secretフィールドの右側にある [作成] をクリックします。
[シークレットの作成] ダイアログボックスで、[名前] 、[証明書] 、および [キー] パラメーターを設定します。 [OK] をクリックします。
[シークレット] ドロップダウンリストから作成したシークレットを選択します。
[+ 追加] をクリックすると、さらにTLS証明書を追加できます。
ドメイン名: demo.alb.ingress.top
シークレット: https-Secret
シークレット名: https-Secret
証明書: Base64でエンコードされていない自己署名証明書。
キー: Base64でエンコードされていない自己署名秘密キー。
(オプション) 注釈
カスタム注釈の名前と値を入力できます。 ドロップダウンリストから名前で注釈を選択または検索することもできます。 Ingressアノテーションの詳細については、「アノテーション」をご参照ください。
[+ 注釈の追加] をクリックして注釈を追加します。 ACKは、追加できるIngressアノテーションの数を制限しません。
設定は必要ありません。
説明HTTPとHTTPSの両方のリクエストをリッスンする場合は、次の注釈を追加します。
名前:
alb.ingress.kubernetes.io/listen-ports値:
[{"HTTP": 80 },{ "HTTPS": 443}]
kubectlを使う
自己署名証明書をシークレットに格納してから、Ingress設定でシークレットを指定できます。
シークレットの作成
https-secret.yamlという名前のファイルを作成し、次の内容をファイルにコピーします。 Base64で証明書と秘密鍵ファイルをエンコードする方法の詳細については、「 (オプション) 手順2: 自己署名証明書の作成」をご参照ください。
apiVersion: v1 kind: Secret metadata: name: https-secret type: kubernetes.io/tls data: tls.key: | # Base64-encoded content of the albtop-key.pem file. {base64 albtop-key.pem} tls.crt: | # Base64-encoded content of the albtop-cert.pem file. {base64 albtop-cert.pem}次のコマンドを実行して、シークレットを作成します。
kubectl apply -f https-secret.yaml
Ingressを変更します。
次のコマンドを実行して、Ingressを変更します。
kubectl edit ingress https-ingresstlsフィールドを追加し、証明書にバインドされているドメイン名と証明書が格納されているシークレットを指定します。apiVersion: networking.k8s.io/v1 kind: Ingress metadata: # annotations: # alb.ingress.kubernetes.io/listen-ports: '[{"HTTP": 80},{"HTTPS": 443}]' # Add this annotation if you want to listen for both HTTP and HTTPS requests. name: https-ingress namespace: default spec: ingressClassName: alb rules: - host: demo.alb.ingress.top # Replace demo.alb.ingress.top with the domain name that you want to use. http: paths: - backend: service: name: https-svc port: number: 443 path: / pathType: Prefix tls: # New field. - hosts: - demo.alb.ingress.top # New field. Set the value to the domain name bound to the certificate. The domain name must be the same as the domain name specified in the "rules: host" field. secretName: https-secret # New field. Create a certificate key.
AlbConfigsで証明書を指定する
ACKコンソールの使用
自己署名証明書のCertIdentifierを取得します。
自己署名証明書を証明書管理サービスにアップロードした後、AlbConfigのリスナー設定の
CertificateIdフィールドで証明書IDを指定できます。このようにして、証明書はリスナーに関連付けられます。説明リスナーが証明書に関連付けられている場合、Ingressは自動証明書検出機能を使用しなくなります。
証明書管理サービスコンソールに自己署名証明書をアップロードします。 詳細については、「SSL証明書のアップロードと共有」をご参照ください。
証明書IDを取得します。
にログインします。Certificate Management Serviceコンソール.
左側のナビゲーションウィンドウで、.
SSL証明書管理ページで、アップロード証明書の管理タブをクリックします。 アップロードした証明書を選択し、[操作] 列の [詳細] をクリックします。
[証明書の詳細] パネルで、[CertIdentifier] フィールドに証明書IDを表示できます。
証明書をAlbConfigで指定します。
ACKコンソールにログインします。 左側のナビゲーションウィンドウで、[クラスター] をクリックします。
[クラスター] ページで、管理するクラスターの名前をクリックします。 左側のウィンドウで、 を選択します。
[リソースオブジェクト] タブで、検索ボックスに [AlbConfig] と入力し、表示された [AlbConfig] をクリックします。
[AlbConfig] パネルで、名前がalb (デフォルト) またはその他のAlbConfigリソースを検索し、[操作] 列の [YAMLの編集] をクリックします。
[YAMLで表示] パネルで、次のフィールドを追加します。 表示されるダイアログボックスで、インスタンス名を変更し、[確認] をクリックします。
項目
説明
例
証明書証明書情報。
-
CertificateId証明書のCertIdentifier。ステップ1で取得できます。
756 ****-cn-hangzhou
IsDefault証明書をデフォルト証明書として設定するかどうかを指定します。
true

Ingressを変更します。
ACKコンソールにログインします。 左側のナビゲーションウィンドウで、[クラスター] をクリックします。
[クラスター] ページで、管理するクラスターの名前をクリックします。 左側のウィンドウで、 を選択します。
[Ingress] ページで、更新するIngressを見つけ、[操作] 列の [更新] をクリックします。 [Ingressの変更] パネルで、パラメーターを設定します。 下表にパラメーターを示します。
パラメーター
説明
例
注釈
カスタム注釈の名前と値を入力できます。 ドロップダウンリストから名前で注釈を選択または検索することもできます。 Ingressアノテーションの詳細については、「アノテーション」をご参照ください。
[+ 注釈の追加] をクリックして注釈を追加します。 ACKは、追加できるIngressアノテーションの数を制限しません。
名前:
alb.ingress.kubernetes.io/listen-ports値:
[{"HTTPS": 443}]説明HTTPとHTTPSの両方のリクエストをリッスンする必要がある場合は、この値を
[{"HTTP": 80 },{ "HTTPS": 443}]に置き換えます。
kubectlを使う
自己署名証明書を証明書管理サービスにアップロードした後、AlbConfigのリスナー設定のCertificateIdフィールドで証明書IDを指定できます。このようにして、証明書はリスナーに関連付けられます。
リスナーが証明書に関連付けられている場合、Ingressは自動証明書検出機能を使用しなくなります。
証明書管理サービスコンソールに自己署名証明書をアップロードします。 詳細については、「SSL証明書のアップロードと共有」をご参照ください。
証明書IDを取得します。
にログインします。Certificate Management Serviceコンソール.
左側のナビゲーションウィンドウで、.
SSL証明書管理ページで、アップロード証明書の管理タブをクリックします。 アップロードした証明書を選択し、[操作] 列の [詳細] をクリックします。
[証明書の詳細] パネルで、[CertIdentifier] フィールドに証明書IDを表示できます。
証明書をAlbConfigで指定します。
次のコマンドを実行して、AlbConfigを変更します。
kubectl edit albconfig <ALBCONFIG_NAME> # Replace <ALBCONFIG_NAME> with the name of the AlbConfig.AlbConfigのリスナー設定に
certificatesフィールドを追加し、前の手順で取得した証明書IDを指定します。apiVersion: alibabacloud.com/v1 kind: AlbConfig metadata: name: alb spec: config: addressType: Intranet name: xiaosha-alb-test listeners: - port: 80 protocol: HTTP - certificates: - CertificateId: 756****-cn-hangzhou # The ID of the certificate. IsDefault: true # Specify whether the certificate is a default one. port: 443 protocol: HTTPS次のコマンドを実行して、Ingressを変更します。
kubectl edit ingress https-ingressalb.ingress.kubernetes.io/listen-ports: '[{"HTTPS": 443}]'アノテーションを追加します。apiVersion: networking.k8s.io/v1 kind: Ingress metadata: annotations: alb.ingress.kubernetes.io/listen-ports: '[{"HTTPS": 443}]' # New field. If you want to listen for both HTTP and HTTPS requests, modify the value to '[{"HTTP": 80},{"HTTPS": 443}]'. name: https-ingress spec: ingressClassName: https-ingressclass rules: - host: demo.alb.ingress.top # Replace demo.alb.ingress.top with the domain name that you want to use. http: paths: - backend: service: name: https-svc port: number: 443 path: / pathType: Prefix
ステップ5: Verify the result
HTTPS経由でアプリケーションにアクセスし、証明書が設定されているかどうかを確認します。
次のコマンドを実行して、Ingressを照会します。
kubectl get ingress期待される出力:
NAME CLASS HOSTS ADDRESS PORTS AGE https-ingress https-ingressclass demo.alb.ingress.top alb-********.alb.aliyuncs.com 80, 443 83m[HOSTS]列と[ADDRESS]列に値を記録します。次のコマンドを実行して、ALB Ingressのバックエンドサービスにアクセスします。
demo.alb.ingress.topとalb-******* .alb.aliyuncs.comを前の手順で取得した値に置き換えます。curl -H HOST:demo.alb.ingress.top -k https://alb-********.alb.aliyuncs.com次の出力が返されると、証明書が設定されます。
old
関連ドキュメント
HTTP/3プロトコルを使用するクライアントからリクエストを受信する方法の詳細については、「HTTPS相互認証を使用してサービスセキュリティを強化する」をご参照ください。
リスナーを使用してHTTPS相互認証を有効にする方法の詳細については、「HTTPS相互認証を使用してサービスのセキュリティを強化する」をご参照ください。