Higiess Enterprise Edition ゲートウェイとして、Microservices Engine (MSE) Ingress ゲートウェイは NGINX Ingress ゲートウェイと互換性があります。 オープンソースのセルフマネージド Ingress ゲートウェイのパフォーマンスと比較して、MSE Ingress ゲートウェイのパフォーマンスは 2 倍になります。 MSE Ingress ゲートウェイは、セキュリティ成熟度に基づいて、中国情報通信研究院 (CAICT) によって業界をリードする Ingress ゲートウェイとして認定されています。 MSE Ingress ゲートウェイは、低コスト、セキュリティ保護、高統合、高可用性という利点を提供します。 このトピックでは、MSE Ingress ゲートウェイを使用して Container Service for Kubernetes (ACK) クラスタおよび Container Compute Service (ACS) クラスタ内のサービスにアクセスする方法について説明します。
セキュリティ上の理由から、MSE Ingress ゲートウェイは kube-system 名前空間のサービスを公開できません。
前提条件
MSE Ingress Controller が ACK マネージドクラスター、ACK Serverless クラスタ、または ACS クラスタにインストールされています。
クラスタ内の MSE Ingress Controller に対する権限が付与されています。 クラスタが ACK マネージドクラスターまたは ACK Serverless クラスタの場合は、[リンク] をクリックして権限を付与します。 クラスタが ACS クラスタの場合は、[リンク] をクリックして権限を付与します。
バージョン V1.18 以降のクラスタが作成されています。 クラスタの作成方法の詳細については、「ACK マネージドクラスターを作成する」、「ACK Serverless クラスタを作成する」、または「ACS クラスタを作成する」をご参照ください。
説明クラスタのバージョンが V1.18 より前の場合は、クラスタをアップグレードします。 アップグレード操作の詳細については、「ACK クラスタを手動でアップグレードする」をご参照ください。
ステップ 1:MSE Ingress Controller をインストールする
ACK コンソール にログインします。 左側のナビゲーションウィンドウで、[クラスタ] をクリックします。
[クラスタ] ページで、管理するクラスタを見つけて、その名前をクリックします。 左側のナビゲーションウィンドウで、[アドオン] をクリックします。
[アドオン] ページで、検索ボックスに
mseと入力し、[MSE Ingress Controller] リソースカードの [インストール] をクリックします。
[MSE Ingress Controller のインストール] ダイアログボックスで、パラメータを設定し、[OK] をクリックします。
クラウドネイティブゲートウェイを作成するか、既存のクラウドネイティブゲートウェイを使用できます。
MSE Ingress コントローラーのインストール時に事前チェックエラーが発生した場合は、「MSE Ingress コントローラーに MSE へのアクセスを許可する」をご参照ください。
MSE Ingress Controller がインストールされると、システムは
mse-ingress-premium-{clusterid}という名前の MseIngressConfig リソースとmse-ingress-premium-{clusterid}という名前のクラウドネイティブゲートウェイを自動的に作成します。ACK コンソールに移動し、クラスターの名前を クリックします。左側のナビゲーションウィンドウで、[ワークロード] > [デプロイメント] > [カスタムリソース] を選択します。[リソースオブジェクト] タブのカスタムリソースページで、[API グループ] セクションの検索ボックスに
mseと入力し、検索アイコンをクリックしてMseIngressConfigリソース記述でゲートウェイステータスをクエリします。phaseが 3 ~ 5 分後に [Listening] に変わると、クラウドネイティブゲートウェイが作成され、実行中状態になります。ゲートウェイは、クラスター内で IngressClass が mse である Ingress リソースを自動的にリッスンします。
通常のケースでは、MseIngressConfig のゲートウェイの状態は、Pending > Running > Listening の順に変化します。 状態の説明:
Pending:クラウドネイティブゲートウェイが作成されています。 約 3 分待つ必要があります。
Running:クラウドネイティブゲートウェイが作成され、実行中です。
Listening:クラウドネイティブゲートウェイが実行中で、クラスタ内の Ingress リソースをリッスンしています。
Failed:クラウドネイティブゲートウェイが無効な状態です。 原因を特定するには、[状態] フィールドの [メッセージ] を表示できます。
重要クラスタを作成すると、MSE Ingress Controller のインストール中に MseIngressConfig リソースが自動的に作成されます。 MseIngressConfig リソースのライフサイクルは、MSE クラウドネイティブゲートウェイのライフサイクルに関連付けられています。 MseIngressConfig リソースを削除すると、関連付けられている MSE クラウドネイティブゲートウェイインスタンスも削除されます。 特に指定のない限り、MseIngressConfig リソースを削除しないでください。
MSE Ingress Controller をインストールする前に、mse という名前の IngressClass リソースがクラスタに既に存在する場合、MSE Ingress Controller のインストール中に MSE クラウドネイティブゲートウェイと関連付けられている MseIngressConfig リソースは自動的に作成されません。
MSE コンソール にログインします。
mse-ingress-premium-{clusterid}という名前のクラウドネイティブゲートウェイがリージョンに作成されていることを確認します。
ステップ 2:バックエンド サービスをデプロイする
ACK コンソール にログインします。 左側のナビゲーションウィンドウで、[クラスタ] をクリックします。
[クラスタ] ページで、目的のクラスタを見つけて名前をクリックします。 左側のウィンドウで、 を選択します。
[デプロイメント] ページで、[YAML から作成] をクリックします。 たとえば、次の YAML コードを使用して、
httpbinという名前のデプロイメントとhttpbinという名前のサービスをデプロイします。apiVersion: apps/v1 kind: Deployment metadata: name: httpbin namespace: default spec: replicas: 1 selector: matchLabels: app: httpbin template: metadata: labels: app: httpbin version: v1 spec: containers: - image: registry.cn-hangzhou.aliyuncs.com/mse-ingress/go-httpbin args: - "--version=v1" imagePullPolicy: Always name: httpbin --- apiVersion: v1 kind: Service metadata: name: httpbin namespace: default spec: ports: - port: 8080 protocol: TCP selector: app: httpbin
ステップ 3:MSE Ingress ゲートウェイを設定する
ACK コンソール にログインします。 左側のナビゲーションウィンドウで、[クラスタ] をクリックします。
[クラスタ] ページで、目的のクラスタを見つけて名前をクリックします。 左側のウィンドウで、 を選択します。
[Ingress] ページで、[Ingress の作成] をクリックします。
[Ingress の作成] ダイアログボックスで、[ゲートウェイタイプ] に [MSE Ingress] を選択し、関連付けられたバックエンド サービスとアノテーションを設定して、[OK] をクリックします。
[Ingress クラス] を mse に設定します。 ルートを設定するには、[ルール] ドロップダウンリストから [プレフィックス (プレフィックスベースの照合)] を選択し、[パス] フィールドに
/と入力して、[サービス] ドロップダウンリストからhttpbinを選択します。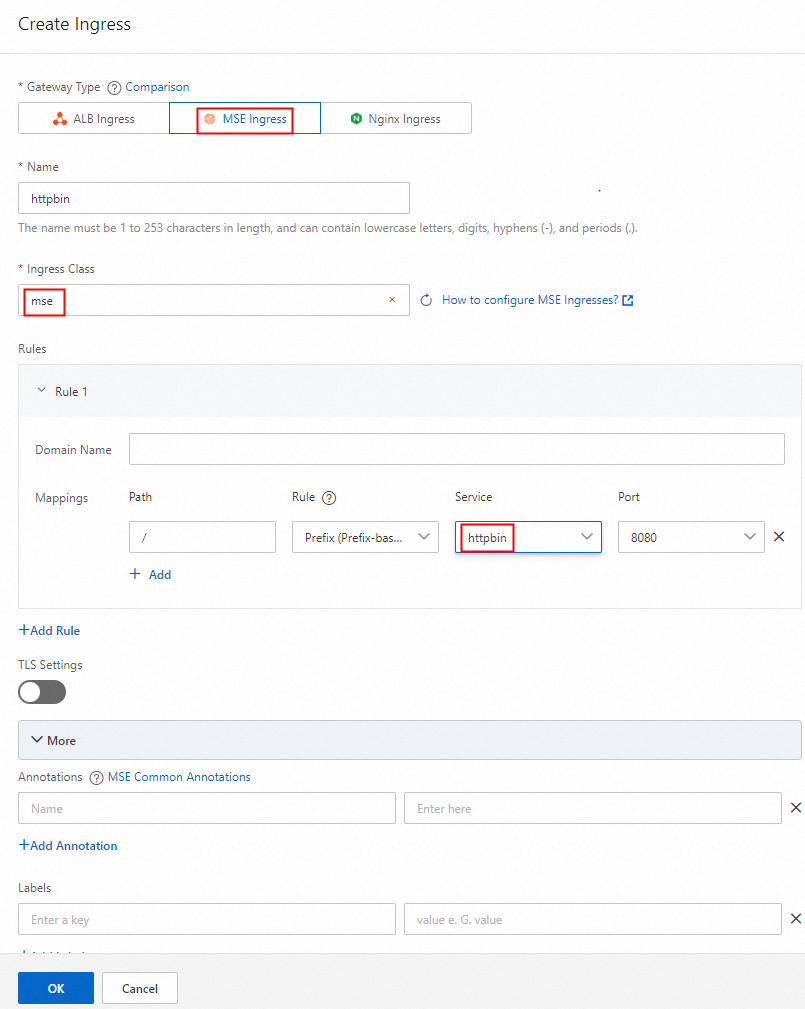
MSE コンソール にログインします。 クラウドネイティブゲートウェイにルートが設定されており、ルート名に httpbin が含まれていることを確認します。

ステップ 4:サービスにアクセスする
ACK コンソール にログインします。 左側のナビゲーションウィンドウで、[クラスタ] をクリックします。
[クラスタ] ページで、目的のクラスタを見つけて名前をクリックします。 左側のウィンドウで、 を選択します。
[Ingress] ページで、Ingress エンドポイントを表示します。

NLB ドメイン名/versionまたはゲートウェイのパブリック IP アドレス/versionの形式でパスにアクセスし、Web ブラウザ、cmd、またはその他のコマンドラインツールを使用してサービスをテストします。 たとえば、Web ブラウザのアドレスバーにnlb-b4ewsj2******.cn-hangzhou.nlb.aliyuncsslb.com/versionと入力してサービスにアクセスします。