Container Service for Kubernetes ( ACK ) は、ポッド間、ACK クラスターとインターネット間、およびロードバランサーサービスとインターネット間の接続の問題など、一般的なネットワークの問題のトラブルシューティングに役立つネットワーク診断機能を提供します。 このトピックでは、ネットワーク診断機能の仕組みと、この機能を使用して一般的なネットワーク接続の問題をトラブルシューティングする方法について説明します。
ネットワーク診断機能を使用すると、ACK はクラスター内の各ノードでデータ収集プログラムを実行し、診断結果を収集します。 ACK は、システムログおよびシステムバージョン、負荷、Docker、Kubelet などの操作情報から主要なエラーメッセージを収集します。 データ収集プログラムは、ビジネス情報や機密データを収集しません。
前提条件
ACK マネージドクラスターが作成されている。
ネットワーク診断の概要
ACK コンソールのネットワーク診断機能を使用すると、障害のある接続の送信元 IP アドレスと宛先 IP アドレス、宛先ポート、およびプロトコルを指定して、接続を迅速に診断できます。 ネットワーク診断機能を使用するために、コンテナネットワークアーキテクチャ、ネットワークプラグイン、またはシステムカーネルメンテナンスに関する知識は必要ありません。
ネットワーク診断機能は、オープンソースの KubeSkoop プロジェクトに基づいて開発されています。 KubeSkoop は、さまざまなネットワークプラグインとサービスとしてのインフラストラクチャ ( IaaS ) プロバイダー向けの Kubernetes ネットワーク診断ツールです。 KubeSkoop を使用して、Kubernetes クラスターの一般的なネットワークの問題を診断し、拡張バークレーパケットフィルター ( eBPF ) を使用してカーネルのクリティカルパスを監視および分析できます。 このトピックでは、ネットワーク診断のみを紹介します。 詳細な監視と分析の詳細については、「KubeSkoop を使用したネットワークの問題のトラブルシューティング」をご参照ください。
ネットワーク診断機能の仕組み
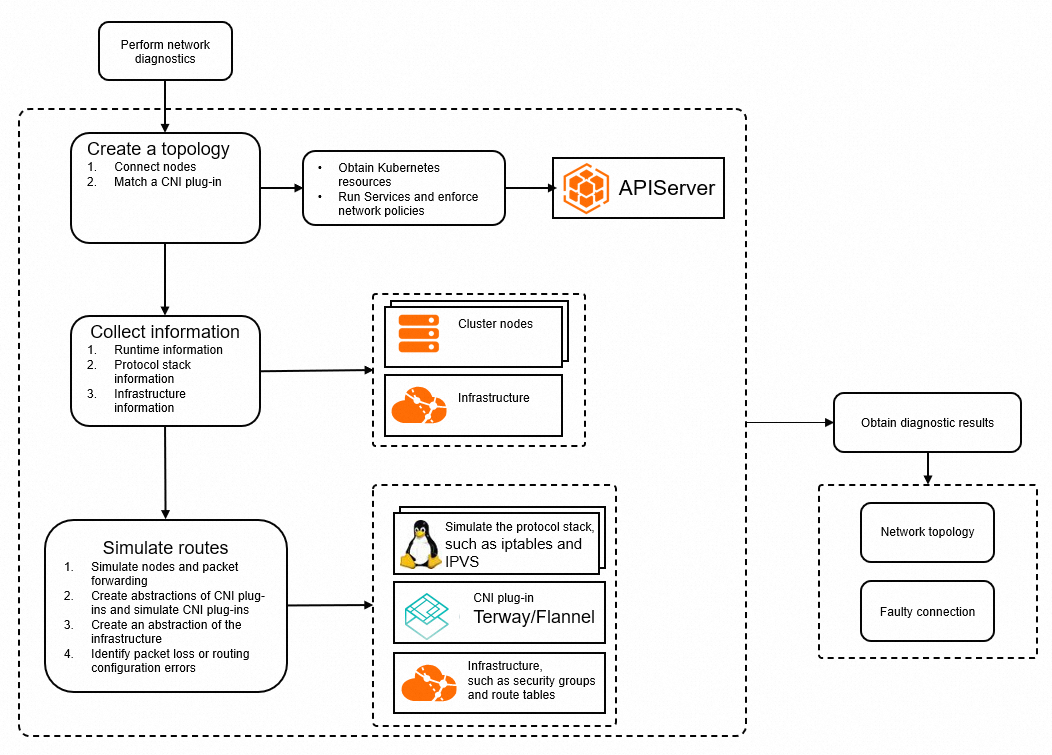
トポロジーの作成:この機能は、指定したネットワーク情報と ACK クラスターから収集された情報 (ポッド、ノード、サービス、およびネットワークポリシーに関する情報を含む) に基づいて、トポロジーを自動的に作成します。
情報の収集:ネットワーク診断機能は、ランタイム、ネットワークスタック、およびネットワークインフラストラクチャに関する情報を収集します。 この情報は、ネットワークのトラブルシューティングと分析に使用されます。
ネットワークルートのシミュレーション:ネットワーク診断機能は、Elastic Compute Service ( ECS ) インスタンスでコマンドを実行するか、ACK クラスターにコレクターポッドをデプロイして、診断対象のノードまたはコンテナのネットワークスタック情報 (ネットワークデバイス、sysctl、iptables、IPVS など) を収集します。 さらに、この機能は、クラウド内のルートテーブル、セキュリティグループ、および NAT ゲートウェイに関する情報も収集します。 システムは、収集された情報を想定されるネットワーク構成と比較して、ネットワーク構成の問題を特定します。 たとえば、システムは iptables とルートをシミュレートし、ネットワークデバイスの状態を確認し、クラウド内のルートテーブルとセキュリティグループルールを確認します。
診断結果の取得:ネットワーク診断機能は、実際のネットワーク構成を想定される構成と比較し、ネットワークトポロジー内の異常なノードとネットワークの問題をハイライトします。
ネットワーク診断機能の操作
制限事項
診断対象のポッドは、実行中状態である必要があります。
外部アクセス用のロードバランサーサービスは、レイヤー 4 クラシックロードバランサー ( CLB ) インスタンスのみをサポートし、バックエンドポッドの数は 10 以下である必要があります。
ACK Serverless クラスターと仮想ノードは、ネットワーク診断をサポートしていません。
手順
ACK コンソールにログインします。 左側のナビゲーションウィンドウで、[クラスター] をクリックします。
[クラスター] ページで、診断するクラスターの名前をクリックします。 左側のナビゲーションウィンドウで、 を選択します。
[診断] ページで、[ネットワーク診断] をクリックします。 [ネットワーク診断] ページで、[診断] をクリックします。
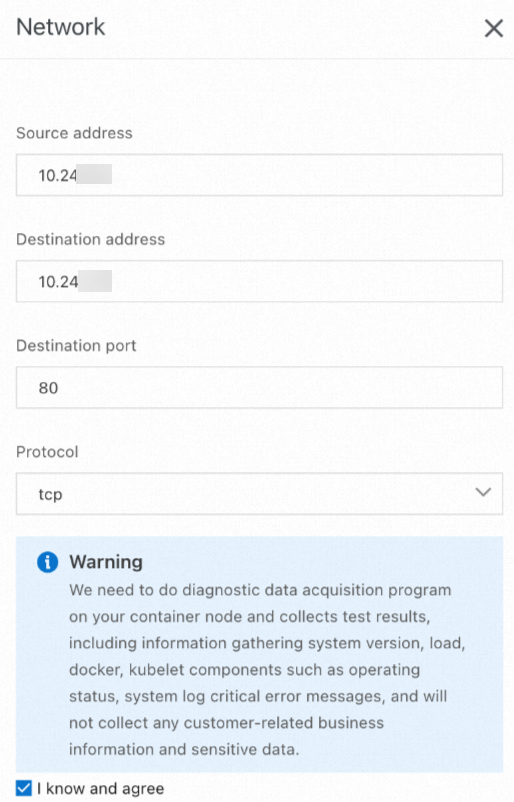
[ネットワーク] パネルで、[送信元アドレス]、[宛先アドレス]、[宛先ポート]、および [プロトコル] を指定し、警告を読んで [了解しました] を選択し、[診断の作成] をクリックします。
パラメーターの詳細については、「一般的なネットワークの問題診断のパラメーター」をご参照ください。
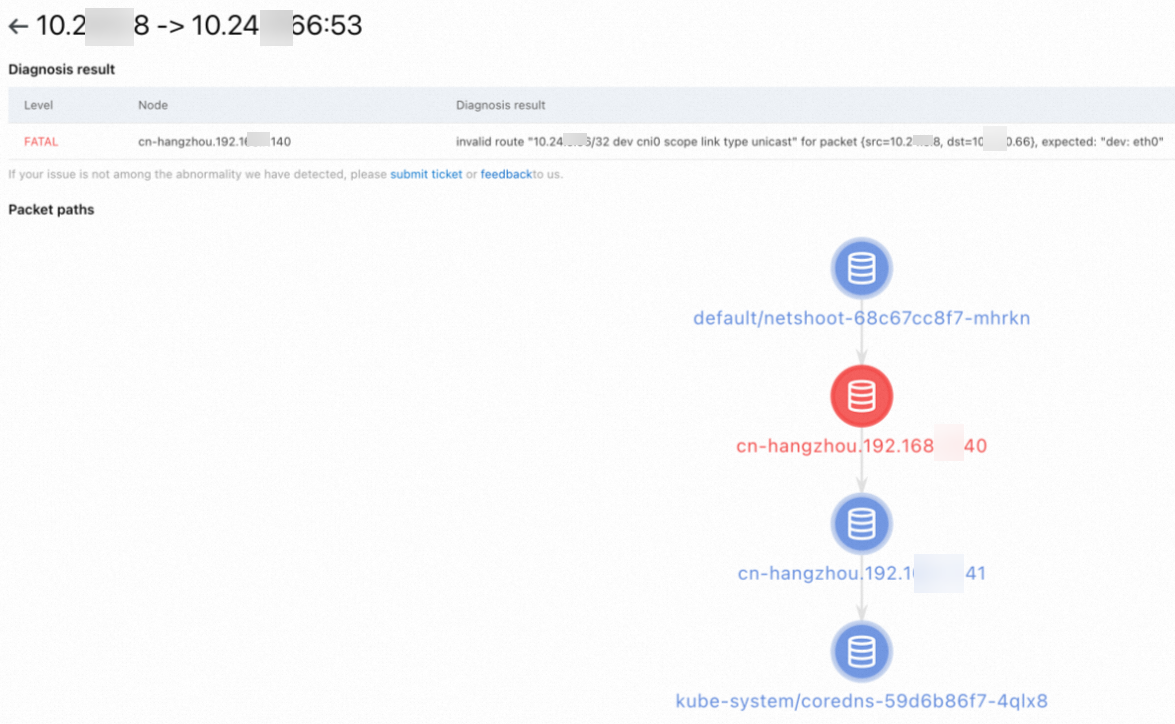
[診断結果] ページで、診断結果を表示できます。 [パケットパス] セクションには、診断されたすべてのノードが表示されます。
異常なノードはハイライト表示されます。 一般的な診断結果の詳細については、「一般的な診断結果と解決策」をご参照ください。
一般的なネットワークの問題診断のパラメーター
シナリオ 1:ポッドとノード間のネットワークを診断する
ネットワーク診断機能を使用して、ポッド間またはポッドとノード間のネットワークを診断できます。 次の表にパラメーターを示します。
パラメーター | 説明 |
送信元アドレス | ポッドまたはノードの IP アドレス。 |
宛先アドレス | 別のポッドまたはノードの IP アドレス。 |
宛先ポート | 診断対象のポート。 |
プロトコル | 診断対象のプロトコル。 |
シナリオ 2:ポッドとサービス間またはノードとサービス間のネットワークを診断する
サービスのクラスター IP を指定して、ノードまたはポッドがサービスにアクセスできるかどうかを確認し、サービスのネットワーク構成を確認できます。 次の表にパラメーターを示します。
パラメーター | 説明 |
送信元アドレス | ポッドまたはノードの IP アドレス。 |
宛先アドレス | サービスのクラスター IP 。 |
宛先ポート | 診断対象のポート。 |
プロトコル | 診断対象のプロトコル。 |
シナリオ 3:DNS 解決を診断する
宛先アドレスがドメイン名の場合、送信元アドレスと宛先アドレス間の接続を確認するだけでなく、クラスター内の DNS サービスも確認する必要があります。 ネットワーク診断機能を使用して、ポッドが kube-system ネームスペースの kube-dns サービスにアクセスできるかどうかを確認できます。
次のコマンドを実行して、kube-system ネームスペースの kube-dns サービスのクラスター IP をクエリします。
kubectl get svc -n kube-system kube-dns予期される出力:
kube-dns ClusterIP 172.16.XX.XX <none> 53/UDP,53/TCP,9153/TCP 6d
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE出力は、kube-dns サービスのクラスター IP が 172.16.XX.XX であることを示しています。 kube-dns サービスのクラスター IP を宛先アドレスとして指定し、他のパラメーターを構成します。
パラメーター | 説明 |
送信元アドレス | ポッドまたはノードの IP アドレス。 |
宛先アドレス | kube-dns サービスのクラスター IP 。 |
宛先ポート | 53 |
プロトコル | udp |
シナリオ 4:ポッドまたはノードとインターネット間のネットワークを診断する
ネットワーク診断機能を使用して、ポッドまたはノードとパブリック IP アドレス間のネットワークを診断できます。 宛先アドレスがドメイン名の場合、ドメイン名にマップされているパブリック IP アドレスを取得する必要があります。 次の表にパラメーターを示します。
パラメーター | 説明 |
送信元アドレス | ポッドまたはノードの IP アドレス。 |
宛先アドレス | パブリック IP アドレス。 |
宛先ポート | 診断対象のポート。 |
プロトコル | 診断対象のプロトコル。 |
シナリオ 5:インターネットとロードバランサーサービス間のネットワークを診断する
ロードバランサーサービスへの外部アクセスが失敗した場合、パブリック IP アドレスを送信元アドレスとして指定し、ロードバランサーサービスの外部 IP アドレスを宛先アドレスとして指定して、接続を診断できます。 次の表にパラメーターを示します。
パラメーター | 説明 |
送信元アドレス | パブリック IP アドレス。 |
宛先アドレス | ロードバランサーサービスの外部 IP アドレス。 |
宛先ポート | 診断対象のポート。 |
プロトコル | 診断対象のプロトコル。 |
一般的な診断結果と解決策
診断結果 | 説明 | 解決策 |
ポッドコンテナ…の準備ができていません | ポッド内のコンテナの準備ができていません。 | ポッドのヘルスステータスを確認し、ポッドを修正します。 |
ネットワークポリシー…は…からのパケットを拒否します | パケットはネットワークポリシーによってブロックされています。 | ネットワークポリシーを変更します。 |
…でリッスンしているプロセスはありません | コンテナ内またはノード上のリスナープロセスは、現在のプロトコルを使用してポートをリッスンしていません。 | リスナープロセスが正常に実行されているかどうかを確認し、ポートやプロトコルなど、ネットワーク診断のパラメーターを確認します。 |
ホストへのルートがありません…/パケット…の無効なルート… | ルートが見つからないか、ルートが目的の宛先を指していません。 | ネットワークプラグインが正常に動作しているかどうかを確認します。 |
…は同じセキュリティグループを持っていません | 2 つの ECS インスタンスは異なるセキュリティグループを使用しています。 パケットは破棄される可能性があります。 | 同じセキュリティグループを使用するように ECS インスタンスを構成します。 |
セキュリティグループ…はパケット…を許可しません | パケットは ECS インスタンスのセキュリティグループによってブロックされています。 | 指定された IP アドレスからのパケットを受け入れるようにセキュリティグループルールを変更します。 |
| ルートテーブルには、宛先アドレスを指すルートが含まれていません。 | 宛先アドレスがパブリック IP アドレスの場合、インターネット NAT ゲートウェイの構成を確認します。 |
| ルートテーブル内のルートは、目的の宛先アドレスを指していません。 | 宛先アドレスがパブリック IP アドレスの場合、インターネット NAT ゲートウェイの構成を確認します。 |
NAT ゲートウェイ…に snat エントリがありません | 目的の SNAT エントリがインターネット NAT ゲートウェイに見つかりません。 | インターネット NAT ゲートウェイの SNAT 構成を確認します。 |
ポート…のバックエンド…ヘルスステータス、「正常」ではありません | CLB インスタンスの一部のバックエンドポッドがヘルスチェックに合格していません。 | 目的のバックエンドポッドが CLB インスタンスに関連付けられているかどうか、および関連付けられたバックエンドポッドで実行されているアプリケーションが正常かどうかを確認します。 |
slb …のリスナーポート…が見つかりません | リスニングポートが CLB インスタンスに見つかりません。 | ロードバランサーサービスの構成と、ポートやプロトコルなど、ネットワーク診断のパラメーターを確認します。 |
…ポート…のロードバランサーのステータスが「実行中」ではありません | CLB インスタンスのリスナーが実行中状態ではありません。 | リスニングポートが正常かどうかを確認します。 |
サービス…に有効なエンドポイントがありません | サービスにエンドポイントがありません。 | サービスのラベルセレクターが想定どおりに機能しているかどうか、サービスのエンドポイントが存在するかどうか、およびエンドポイントが正常かどうかを確認します。 ロードバランサーサービスへの内部アクセスの詳細については、「クラスター内から CLB インスタンスにアクセスできない」をご参照ください。 |