ACK は、Terway と Flannel という 2 つのコンテナーネットワークインターフェース (CNI) プラグインを提供しています。このトピックでは、Terway と Flannel の機能と適用可能なシナリオを比較します。
Terway は Alibaba Cloud によって開発されたネットワークプラグインです。このプラグインは、Elastic Network Interface (ENI) に基づいてネットワークを構築します。Terway は、拡張 Berkeley Packet Filter (eBPF) を使用したネットワークトラフィックの高速化をサポートしています。また、Terway は、ネットワークポリシー、ポッドレベルのスイッチ、およびセキュリティグループもサポートしています。Terway は、大規模ノード、高ネットワークパフォーマンス、高セキュリティを必要とするハイパフォーマンスコンピューティング、ゲーム、マイクロサービスなどのシナリオに適しています。
Flannel は、コミュニティによって提供されるオープンソースのネットワークプラグインです。Flannel は、ACK で Alibaba Cloud の Virtual Private Cloud (VPC) を使用します。パケットは VPC ルートテーブルに基づいて転送されます。Flannel は、小規模ノード、簡素化されたネットワーク構成を必要とし、コンテナーネットワークのカスタム制御を必要としないシナリオに適しています。
コンテナーネットワークプラグインは、クラスターの作成時にインストールする必要があり、クラスターの作成後は変更できません。
Flannel を使用する場合、ALB Ingress は NodePort サービスと LoadBalancer サービスへのリクエストの転送のみをサポートし、ClusterIP サービスはサポートしていません。
項目 | Terway | Flannel |
ネットワークパフォーマンス |
| |
ノードクォータ | Terway を使用する場合、ノードの最大数は単一クラスターの容量によって異なります。
| Flannel を使用する場合、ノードの最大数は、VPC ルートテーブルのエントリ数とクラスターの容量によって異なります。 VPC ルートテーブルのエントリ: デフォルトでは 200 エントリがサポートされています。クォータの増加を申請すると、最大 1,000 エントリがサポートされます。1 つのノードは、クラスター内の 1 つのエントリに対応します。最大 1,000 ノードがサポートされています。
|
ノード上のポッド数 | ポッドは、ノードの ENI を使用します。ノード上のポッド数は、[ENI] の数や 1 ENI あたりの非公開 IPv4 アドレス の数など、ノードの仕様とメトリックによって異なります。
前の図は、[コンピューティングネストタイプ C7]、ecs.c7.4xlarge、16 vCPU 32 GiB の仕様の ECS インスタンスを示しています。
[コンピューティングネストタイプ C6] インスタンスと [コンピューティングネストタイプ C7] インスタンスは、同じ数の ENI を持っています。ただし、1 つの ENI あたりのプライベート IPv4 アドレスの数 が異なるため、[コンピューティングネストタイプ C6] では包括的 ENI モードで最大 140 個のポッドを作成できます。詳細については、「ノード上のポッドの最大数を計算する方法」をご参照ください。 | ノード上のポッドの数は、[ポッドの数] パラメーターと [ポッド CIDR ブロック] パラメーターを指定するときに設定したサブネットマスクによって異なります。
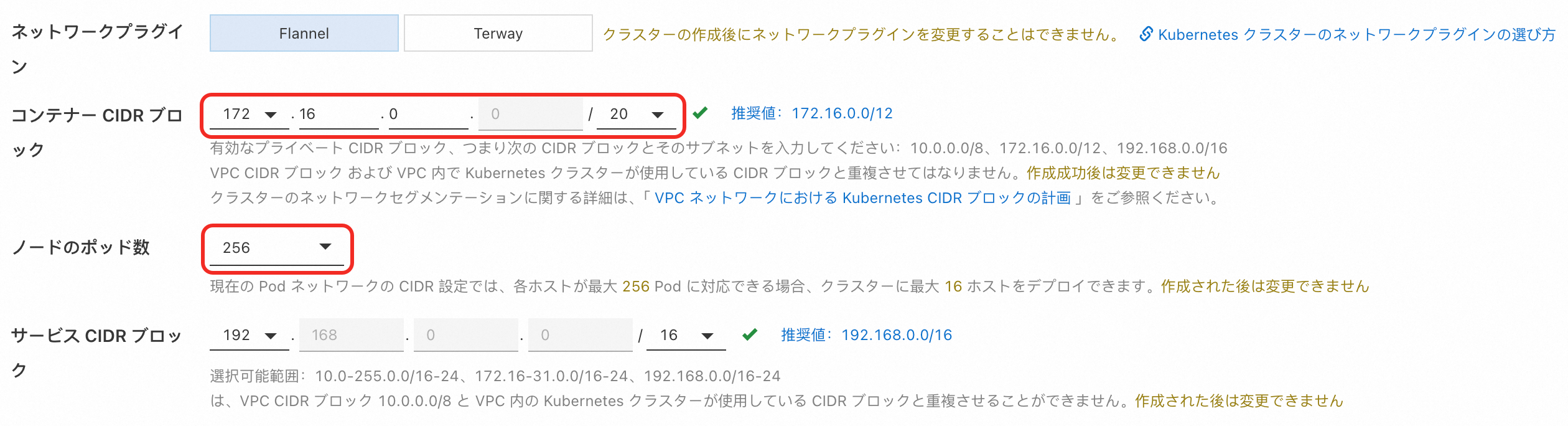
前の図は、ACK Pro クラスター 内のポッドの CIDR ブロックが 172.16.0.0/20 であることを示しています。各ノードは最大 256 個のポッドを実行できます。ACK Pro クラスターには最大 16 個のノードをデプロイできます。 重要 Flannel を構成した後、ノードの最大数を変更することはできません。 |
ポッド CIDR ブロック |
|
|
ネットワークセキュリティ |
|
|
IPv4/IPv6 デュアルスタック | IPv4/IPv6 デュアルスタックがサポートされています。 | IPv4/IPv6 デュアルスタックはサポートされていません。 説明 ACK で使用される Flannel プラグインは、Alibaba Cloud 環境に適応するように変更されており、オープンソースコミュニティとは同期されていません。Flannel のリリースノートの詳細については、「Flannel」をご参照ください。 |
ポッドの固定 IP アドレス | 各ポッドに静的 IP アドレスを指定できます。 | 各ポッドに静的 IP アドレスを指定することはできません。 |
セッション維持 | SLB インスタンスのバックエンドサーバーはポッドに直接接続し、セッション維持機能に依存して、バックエンドポッドが変更された場合でもサービスが中断されないようにします。 | SLB インスタンスのバックエンドサーバーは、NodePort を使用してポッドに接続します。ポッドが変更されるとトラフィックが中断され、サービスの再試行が発生する可能性があります。 |
複数クラスター間のアクセス | セキュリティグループルールで関連ポートが開いている場合、異なるクラスター内のポッドが通信できます。 | サポートされていません。 |
ポッド送信元 IP アドレスの保持 | ポッドが VPC 内の他のエンドポイントにアクセスするために使用する送信元 IP アドレスはすべて、ポッド IP アドレスです。これにより、監査が容易になります。 | ポッドが VPC 内の別のエンドポイントにアクセスする場合、送信元 IP アドレスはノード IP アドレスです。ポッド IP アドレスは保持できません。 |
次の手順
クラスターを作成した後、ポッド CIDR ブロック、サービス CIDR ブロック、またはノード CIDR ブロックを変更することはできません。上記の CIDR ブロックは、クラスターにデプロイできるポッド、サービス、およびノードの最大数を制限します。異なるリソース間で論理ネットワーク分離を有効にする場合は、リソースの CIDR ブロックが互いに重複しないようにしてください。これにより、アクセス制御とカスタムルートを構成することもできます。Kubernetes クラスターを作成する前に CIDR ブロックを計画することをお勧めします。詳細については、「ACK マネージドクラスターのネットワーク計画」をご参照ください。
CIDR ブロックを計画した後:
Terway を使用する場合は、クラスターの作成時に Terway をインストールします。詳細については、「Terway を使用する」をご参照ください。
Flannel を使用する場合は、クラスターの作成時に Flannel をインストールします。詳細については、「Flannel を使用する」をご参照ください。
参考資料
クラスター内のノード数の制限方法とクォータの増加方法の詳細については、「クォータと制限」をご参照ください。
コンテナーネットワークを使用する際のよくある質問については、「コンテナーネットワークに関するよくある質問」をご参照ください。