アクセス制御が必要なシナリオでは、ポッドのIPアドレスをApsaraDB RDSホワイトリストに動的に追加するか、またはIPアドレスをホワイトリストから削除してアクセス制御を微調整する必要があります。 これを行うには、ack-kubernetes-webhook-injectorコンポーネントを使用してポッドにアノテーションを追加します。 このトピックでは、ack-kubernetes-webhook-injectorをインストールし、コンポーネントを使用してAlibaba Cloudサービスのポッドホワイトリストを動的に設定する方法について説明します。 このトピックでは、Alibaba Cloudサービスの内部エンドポイントにアクセスするようにack-kubernetes-webhook-injectorを設定する方法についても説明します。
前提条件
Container Service for Kubernetes (ACK) マネージドクラスターが作成されます。 詳細については、「ACK管理クラスターの作成」をご参照ください。
kubectlクライアントがクラスターに接続されています。 詳細については、「クラスターのkubeconfigファイルを取得し、kubectlを使用してクラスターに接続する」をご参照ください。
クラスターはTerwayネットワークプラグインを使用します。 詳細については、「Terwayでの作業」をご参照ください。
概要
クラウドコンピューティングシナリオでは、一部のクラウドリソースへの外部アクセスを許可するようにアクセス制御ポリシーを設定する必要があります。 たとえば、Elastic Compute Service (ECS) インスタンスのServer Load Balancer (SLB) アクセスコントロールリスト (ACL) を設定するか、ApsaraDB RDSホワイトリストを設定して、指定されたクライアントIPアドレスからのアクセスを許可する必要があります。 ACKクラスターを作成するときに、クラスターノードのCIDRブロックをApsaraDB RDSホワイトリストに追加できます。 ただし、次の制限があります。
すべてのノードとポッドのIPアドレスがホワイトリストに追加されるため、ホワイトリストは粗い方法でアクセスを制御します。
クラスターの削除後、ホワイトリストは自動的に更新されません。 ホワイトリストを手動で更新する必要があります。
上記の問題を解決するために、ACKはack-kubernetes-webhook-injectorコンポーネントを提供し、ポッドのIPアドレスをApsaraDB RDSホワイトリストに動的に追加できるようにします。 ポッドが削除されると、ポッドのIPアドレスは自動的にホワイトリストから削除されます。 これにより、きめ細かいアクセス制御が可能となる。
ack-kubernetes-webhook-injectorコンポーネントは、次の機能をサポートしています。
ポッドが作成または削除されると、ポッドのIPアドレスが対応するSLB ACLに自動的に追加または削除されます。
ポッドが作成または削除されると、ポッドのIPアドレスが対応するApsaraDB for Redisホワイトリストに自動的に追加または削除されます。
ポッドが作成または削除されると、ポッドのIPアドレスが対応するApsaraDB RDSホワイトリストに自動的に追加または削除されます。
ack-kubernetes-webhook-injectorのインストール
ACKコンソールにログインします。 左側のナビゲーションウィンドウで、 を選択します。
ack-kubernetes-webhook-injectorを見つけてクリックします。 ページの右上隅にある [デプロイ] をクリックします。
表示されるパネルで、コンポーネントのクラスターと名前空間を指定し、リリース名を入力して [次へ] をクリックします。
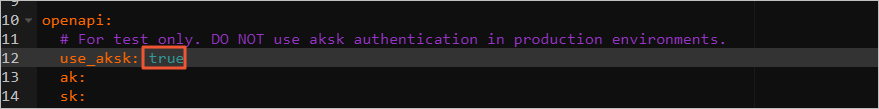
[パラメーター] ウィザードページで、
openapiセクションのakとskをAccessKeyペアに設定し、[OK] をクリックします。AccessKeyペアを取得する方法の詳細については、「AccessKeyペアの取得」をご参照ください。
ack-kubernetes-webhook-injectorを使用してポッドのIPアドレスをApsaraDB RDSホワイトリストに動的に追加する方法の例
ReplicationControllerの [Pod Spec] セクションで、ポッドのIPアドレスを追加するApsaraDB RDSホワイトリストの名前とApsaraDB RDSインスタンスのIDを指定するためのアノテーションを追加できます。 ack-kubernetes-webhook-injectorは、ポッドの作成時にポッドのIPアドレスをホワイトリストに自動的に追加し、ポッドの削除時にホワイトリストから削除します。
Annotations:
ApsaraDB RDSインスタンスのID:
ack.aliyun.com/rds_idApsaraDB RDSホワイトリストの名前:
ack.aliyun.com/white_list_name
このトピックでは、ack-kubernetes-webhook-injectorを使用してポッドホワイトリストを動的に構成する方法を示すための例として、ApsaraDB RDSホワイトリストを使用します。
次のYAMLテンプレートを使用してデプロイを作成し、注釈を追加してApsaraDB RDSホワイトリストの名前とApsaraDB RDSインスタンスのIDを指定します。
apiVersion: apps/v1 kind: Deployment metadata: labels: app: inject-test name: inject-test spec: replicas: 1 selector: matchLabels: app: inject-test template: metadata: annotations: ack.aliyun.com/rds_id: <rm-wz9nanjcud75b****> ack.aliyun.com/white_list_name: <rds_group> labels: app: inject-test spec: containers: - command: - sleep - "3600" image: alpine:latest name: inject-test次のコマンドを実行して、ポッドのIPアドレスを照会します。
kubectl --kubeconfig .kube/config_sts_test -n inject-test get pod -o wide期待される出力:
NAME READY STATUS RESTARTS AGE IP NODE inject-test-68cc8f9bbf-gj86n 1/1 Running 0 22s 172.25.0.28 cn-hangzhou.xxx出力は、ポッドのIPアドレスが172.25.0.28であることを示します。
ApsaraDB RDSコンソールにログインし、指定されたApsaraDB RDSインスタンスのホワイトリストを確認します。 ApsaraDB RDSホワイトリストを表示する方法の詳細については、「拡張IPアドレスホワイトリストの設定」をご参照ください。
手順1で作成したデプロイのポッド数を0に設定し、ApsaraDB RDSホワイトリストを再度確認します。
ポッドのIPアドレスがコンソールのApsaraDB RDSホワイトリストから削除されていることがわかります。
Alibaba Cloudサービスの内部エンドポイントへのアクセス
デフォルトでは、ack-kubernetes-webhook-injectorはAlibaba Cloudサービスのパブリックエンドポイントを使用してサービスにアクセスします。 クラスターのパブリックアクセスが無効になっている場合、サービスの内部エンドポイントを使用するようにack-kubernetes-webhook-injectorを設定できます。
一部のAlibaba Cloudサービスは、特定のリージョンで内部エンドポイントを提供しません。 OpenAPI Explorerに移動して、サービスが指定されたリージョンで内部エンドポイントを提供しているかどうかを確認できます。
ACKコンソールにログインします。 左側のナビゲーションウィンドウで、[クラスター] をクリックします。
[クラスター] ページで、管理するクラスターの名前をクリックします。 左側のウィンドウで、 を選択します。
上部のナビゲーションバーで、名前空間ドロップダウンリストからkube-systemを選択し、kubernetes-webhook-injectorのデプロイを見つけ、デプロイのアクションで詳細> YAMLで表示を選択します。
[の追加
- '-- intranet-access'][spec.template.spec.containers.comコマンド]をクリックし、[更新] をクリックします。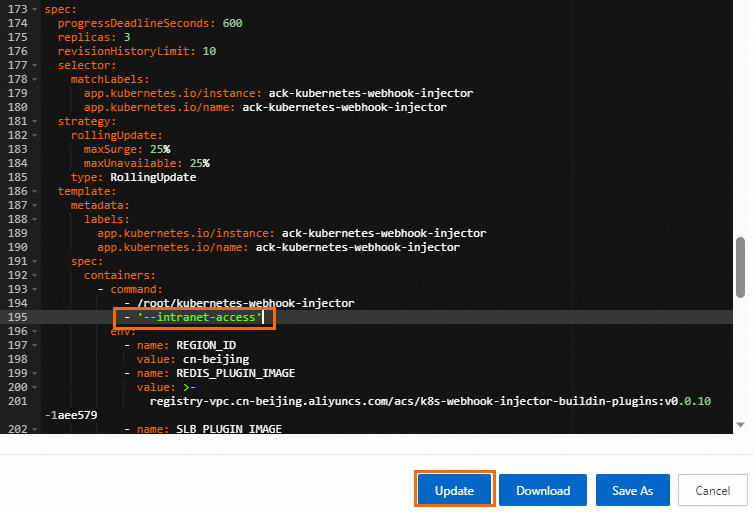
その他のアクセス制御ポリシー
ack-kubernetes-webhook-injectorは、次のアクセス制御ポリシーもサポートしています。
SLB ACL:
ack.aliyun.com/access_control_policy_id。ApsaraDB for Redisホワイトリスト:
ApsaraDB for RedisインスタンスのID: ack.aliyun.com/redis_id。
ApsaraDB for Redisホワイトリストの名前:
ack.aliyun.com/white_list_name。
ack-kubernetes-webhook-injectorのアンインストール
ack-kubernetes-webhook-injectorを使用する必要がなくなった場合は、ackが提供するリリース機能を使用して、ACK-kubernetes-webhook-injectorをアンインストールできます。 詳細については、「Helmを使用したリリースの管理」をご参照ください。 関連する設定を削除するには、次のコマンドを実行します。
kubectl -n kube-system delete secret kubernetes-webhook-injector-certs
kubectl delete mutatingwebhookconfigurations.admissionregistration.k8s.io kubernetes-webhook-injector