An IPsec-VPN connection in dual-tunnel mode has an active tunnel and a standby tunnel. If the active tunnel is down, the standby tunnel takes over to ensure service availability. This topic describes how to upgrade a VPN gateway to enable the dual-tunnel mode.
Background information
Before you upgrade a VPN gateway to enable the dual-tunnel mode, we recommend that you know more about the dual-tunnel mode such as the network topology and data transfer path. For more information, see Associate an IPsec-VPN connection with a VPN gateway.
Bandwidth changes after the upgrade
If your single-tunnel VPN Gateway instance has a bandwidth specification of 100 Mbps or less:
Supported IPsec-VPN tunnel mode
Peak bandwidth from the VPN Gateway instance to the data center
Peak bandwidth from the data center to the VPN Gateway instance
Before upgrade
The bandwidth specification of the VPN Gateway instance.
100 Mbps.
After upgrade
The bandwidth specification of the VPN Gateway instance.
The bandwidth specification of the VPN Gateway instance.
If your single-tunnel VPN Gateway instance has a bandwidth specification greater than 100 Mbps, the peak bandwidth remains unchanged after the upgrade and is the same as the bandwidth specification of the instance.
Supported regions and zones
The following table describes the regions and zones in which you can upgrade IPsec-VPN connections to enable the dual-tunnel mode.
You can call the DescribeVpnGatewayAvailableZones operation to query zones that support dual-tunnel IPsec-VPN connections in the specified region. If the zones listed in the table differ from the information returned by the DescribeVpnGatewayAvailableZones operation, the zones returned by the DescribeVpnGatewayAvailableZones operation shall prevail.
Region | Zone |
China (Hangzhou) | K, J, I, H, G |
China (Shanghai) | L, M, N, A, B, E, F, G |
China (Nanjing - Local Region) | A |
China (Shenzhen) | A (no longer available for purchase), C, E, D, F |
China (Heyuan) | A, B |
China (Guangzhou) | A, B |
China (Qingdao) | B, C |
China (Beijing) | F, E, H, G, A, C, J, I, L, K |
China (Zhangjiakou) | A, B, C |
China (Hohhot) | A, B |
China (Ulanqab) | A, B, C |
China (Chengdu) | A, B |
China (Hong Kong) | B, C, D |
Singapore | A, B, C |
Thailand (Bangkok) | A |
Japan (Tokyo) | A, B, C |
South Korea (Seoul) | A |
Philippines (Manila) | A |
Indonesia (Jakarta) | A, B, C |
Malaysia (Kuala Lumpur) | A, B |
UK (London) | A, B |
Germany (Frankfurt) | A, B, C |
US (Silicon Valley) | A, B |
US (Virginia) | A, B |
Mexico | A |
SAU (Riyadh - Partner Region) | A, B |
UAE (Dubai) | A |
Prerequisites
Before you upgrade a VPN gateway, make sure that the following requirements are met:
Usage notes on the upgrade process
A VPN gateway is unavailable during the upgrade process. The existing connections are interrupted. We recommend that you upgrade a VPN gateway during a network maintenance window to prevent service interruptions.
The upgrade takes about 10 minutes. During this period, the VPN gateway cannot forward traffic.
You cannot manage the VPN gateway during the upgrade process.
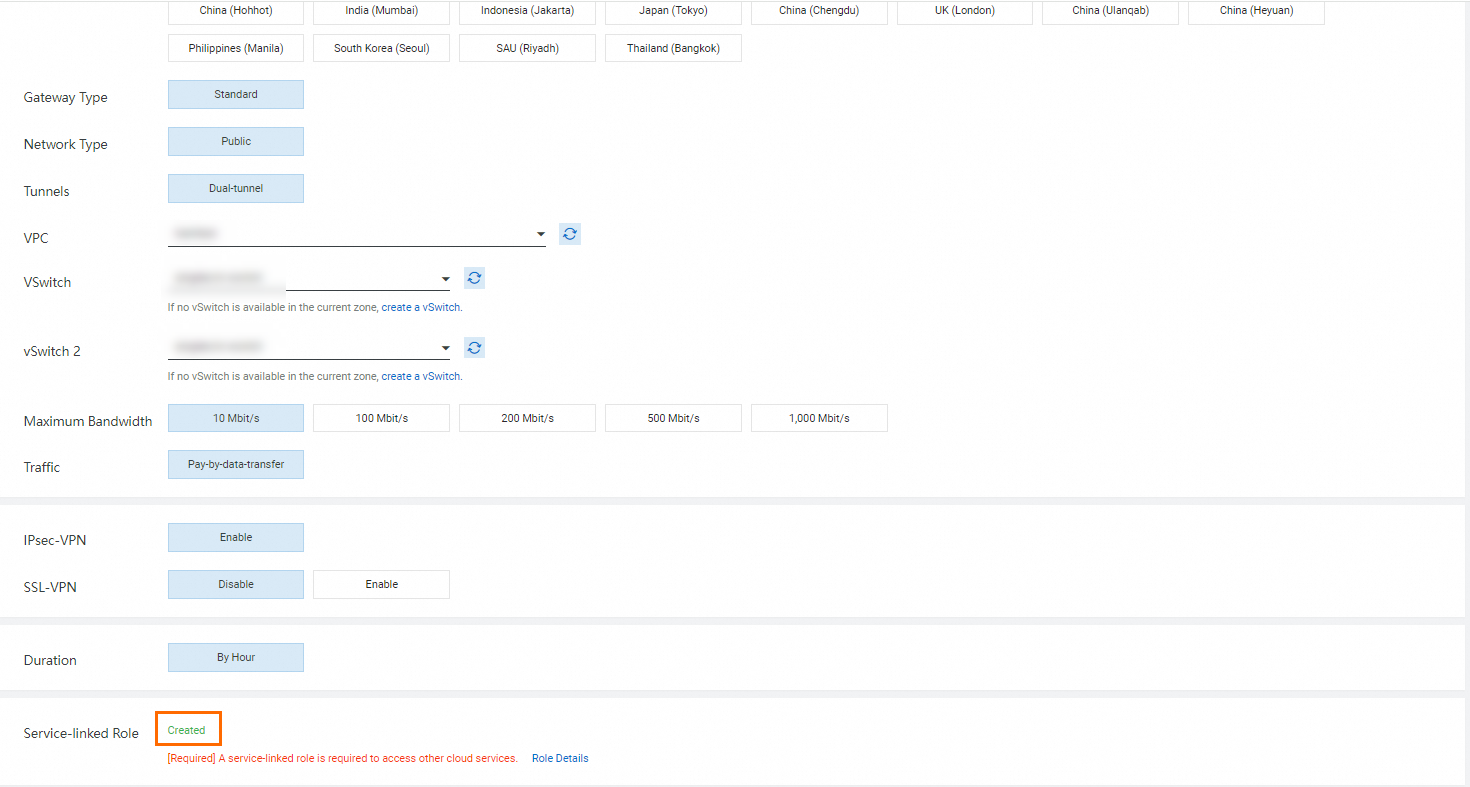
Procedure
- Log on to the VPN gateway console.
In the top menu bar, select the region of the VPN gateway.
On the VPN Gateways page, click the ID of the VPN gateway that you want to manage.
In the upper-right corner of the details page, click Enable Zone Redundancy.
In the Enable Zone Redundancy dialog box, specify a vSwitch and enable environment verification. Make sure that the requirements are met and click Enable.
If the environment verification failed, refer to the Prerequisites section of this topic for troubleshooting.
After you click Enable, the system starts the upgrade.
What to do next
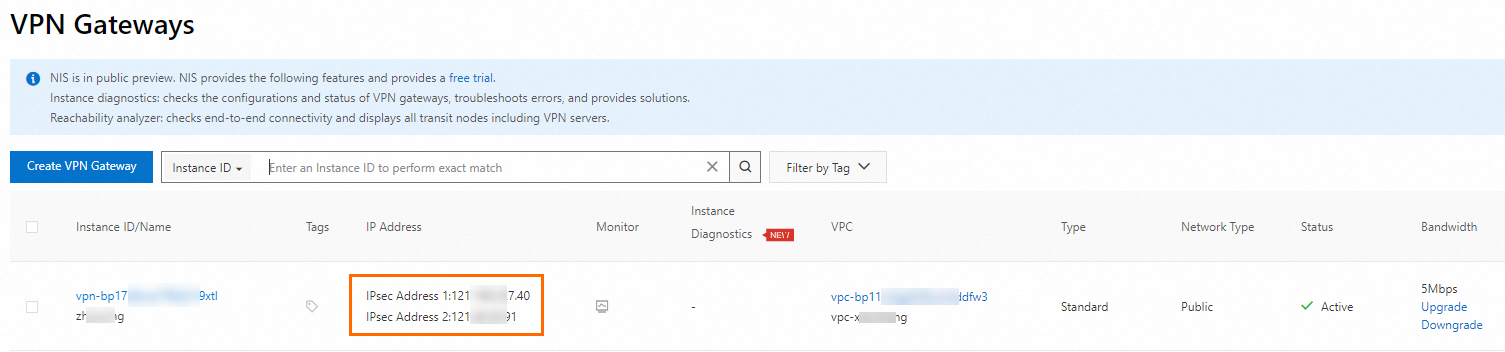
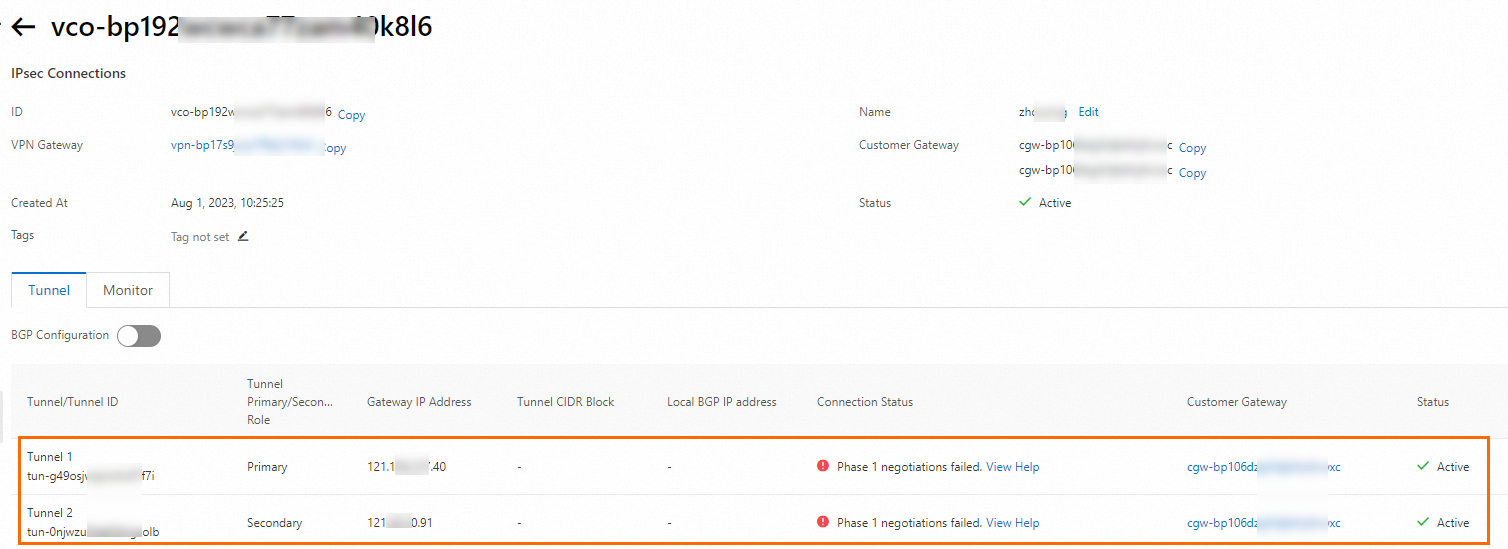
When you use a dual-tunnel IPsec-VPN connection, make sure that the active tunnel and standby tunnel are available. If you configure or use only one of the tunnels, IPsec-VPN connection redundancy based on active/standby tunnels and zone-disaster recovery are not supported.