By default, content distributed by ApsaraVideo VOD is public, meaning anyone with the URL can access it. To prevent unauthorized downloading and hotlinking of your resources, use URL signing in addition to other security measures such as referer-based hotlink protection and IP address allowlist/blocklist. URL signing helps protect your origin server resources by validating an encrypted string and a timestamp in the request URL.
Authentication logic
URL signing in ApsaraVideo VOD prevents hotlinking by coordinating between Alibaba Cloud CDN points of presence (POPs) and your application server. The process involves the following components:
Application server: Generates signed URLs based on predefined rules, including the signing algorithm and key.
User's app or web browser: Requests a resource by sending the signed URL to a POP for verification.
POP: Validates the authentication information, such as the signature string and timestamp, within the signed URL.

The authentication process is as follows:
You configure the rules for generating signed URLs on your application server.
The client requests a signed URL from your application server.
Your application server returns a signed URL for the corresponding resource based on the client's request.
The client uses the signed URL to request the resource from a CDN POP.
The POP validates the authentication information in the signed URL to verify the request.
If authentication fails, the request is denied.
If authentication is successful, the request is processed normally.
If authentication is successful, the POP returns the resource according to its caching logic.
NoteIf the POP does not have the resource cached, it removes the signing parameters from the URL before fetching the content from the origin. This restores the URL to its original format (for example,
http://DomainName/FileName). The original URL is then used to generate a cache key or make the origin fetch request.After the CDN authenticates your request URL, it escapes special characters in the URL, such as
=and+.
Enable and configure URL signing
Ensure that you have configured the generation rules for signed URLs, including the signing algorithm and key, on your application server.
The URL signing logic in ApsaraVideo VOD must match the logic on your application server.
Log on to the ApsaraVideo VOD console.
In the left navigation pane, choose .
Select the domain name for which you want to configure URL signing and click Configure in the Actions column.
Click Resource Access Management.
Click the URL Signing tab, and then click Modify in the Set URL Signing section.
Enable URL Signing and configure the parameters.
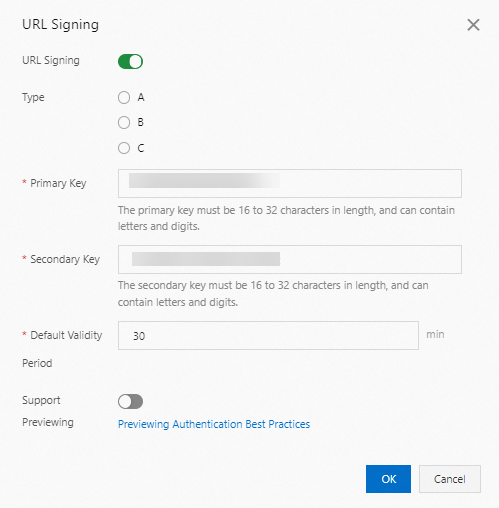
The following table describes the parameters.
Parameter
Description
Type
ApsaraVideo VOD supports three signature calculation methods for CDN acceleration. You can select the appropriate signing method based on encrypted URL format. The following types are supported:
NoteA URL signing error returns a 403 status code:
Invalid MD5 values
Example:
X-Tengine-Error:denied by req auth: invalid md5hash=de7bfdc915ced05e17380a149bd7****Invalid timestamps
Example:
X-Tengine-Error:denied by req auth: expired timestamp=143946****
Primary Key
Enter the primary key for the selected signing method. The key must be 6 to 32 characters long and can contain letters and digits.
Secondary Key
Enter the secondary key for the selected signing method. The key must be 6 to 32 characters long and can contain letters and digits.
NoteThe secondary key has the same permissions as the primary key and is used for smooth key rotation. If you change the primary key, all signed URLs generated with the old key will become invalid. To avoid service interruptions, copy the current primary key to the secondary key field before creating a new primary key. This process ensures that requests signed with the old key remain valid during the transition.
Default Validity Period
The validity period of a signed URL generated by ApsaraVideo VOD. Users can access the content within the time range of
(timestamp + Default Validity Period). After this period, the signature expires.Default value: 30. Unit: minutes.
Example: If the server generates a signed URL at 2020-08-15 15:00:00 (UTC+8) and the Default Validity Period is set to 30 minutes, the signed URL will expire at 2020-08-15 15:30:00 (UTC+8).
Support Previewing
The preview feature enables users to watch only a specified duration of a video or audio file, such as the first five minutes. This is commonly used for subscription-based or paid content. For more information, see Configure the preview feature.
Click OK to complete the configuration.
After you enable and configure URL signing, it takes effect globally for the domain.
If all your media assets are in the ApsaraVideo VOD console, the console automatically generates signed URLs with a validity period. You can also obtain a signed URL by calling the GetPlayInfo operation.
NoteAfter you enable URL signing, URLs for all assets, including videos, audio, thumbnails, and snapshots, require signing.
Disable URL signing
If URL signing is disabled in ApsaraVideo VOD but client requests still include signing parameters, ApsaraVideo VOD cannot restore the original URL from the signed URL. As a result, all requests miss the cache and are forwarded to your origin, resulting in a sharp increase in origin traffic and costs. Therefore, to stop using URL signing, you must disable it on both your application server and in ApsaraVideo VOD.
In the Set URL Signing section, click Modify.
Disable URL Signing.
Remove the signing parameters from the request URLs in your application server.
Generate a signed URL
Generate from the console
To verify that your server has correctly implemented the signing logic, generate a signed URL in the ApsaraVideo VOD console after you configure URL signing.
In the Generate Signed URL section, configure the Original URL and authentication information.
The following table describes the parameters.
Parameter
Description
Original URL
Enter the complete original URL, for example,
https://****.com/ecs.mp4.Type
Select the URL signing type (A, B, or C) that you configured in the Enable and configure URL signing step.
Authentication Key
Enter your Primary Key or Secondary Key that you configured in the Enable and configure URL signing step.
Validity Period
Enter the validity period for the signed URL in seconds. This should match the configuration in the Enable and configure URL signing step.
Click Generate to obtain the Signed URL and Timestamp.

Generate with an SDK
You can integrate the ApsaraVideo VOD SDK into your application server and call the GetPlayInfo operation to generate signed URLs.
Generate with code
You can write your own code to generate signed URLs based on one of the three signing methods.