Compared with NGINX Ingresses, Application Load Balancer (ALB) Ingresses are fully managed and do not require manual O&M. In addition, ALB Ingresses support higher elasticity. You can use the migration tool provided by Container Service for Kubernetes (ACK) to migrate traffic from NGINX Ingresses to ALB Ingresses. The migration tool can automatically convert NGINX Ingress configurations to ALB Ingresses configurations. You do not need to perform manual configurations. This topic describes how to use Alibaba Cloud DNS to gradually migrate traffic from an NGINX Ingress to an ALB Ingress after you convert NGINX Ingress configurations to ALB Ingresses configurations. The process is transparent to users.
Migration process
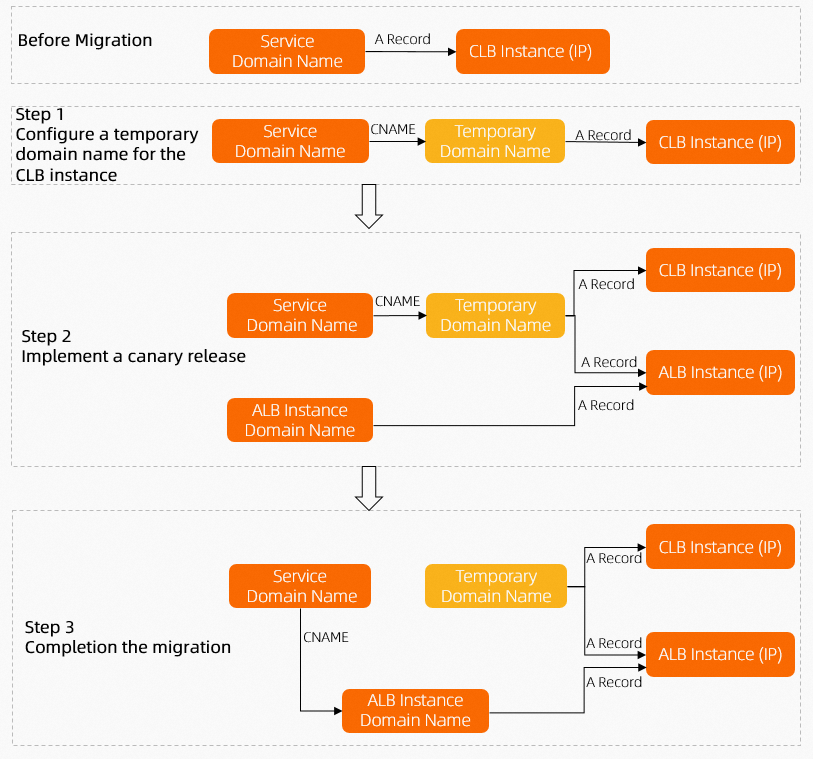
Resolve a domain name to an NGINX Ingress and an ALB Ingress and gradually adjust the weights of the Ingresses. This ensures transparent migration for your business. The following figure shows the procedure for migrating traffic by using Alibaba Cloud DNS. For more information about each step, see Migration example.
Alibaba Cloud DNS is not the only solution for transparent migration. The migration example in this topic is for reference only.

Migration example
This example demonstrates the migration process.
A company installed the NGINX Ingress controller in an ACK cluster and configured an Internet-facing LoadBalancer Service for the controller. The controller is automatically associated with an Internet-facing Classic Load Balancer (CLB) instance. The company configured a DNS record to map the domain name www.example.net to the CLB instance. Requests destined for the domain name are resolved to the CLB instance, which forwards the requests to backend pods.

Step 1: Configure an ALB Ingress
As businesses develop, the performance of NGINX Ingresses cannot meet business requirements. NGINX Ingresses also generate high O&M costs. The company wants to migrate network traffic from the NGINX Ingress to an ALB Ingress. During the migration process, the company uses the migration tool provided by ACK to convert NGINX Ingress configurations to ALB Ingress configurations, and add the ALB Ingress to the DNS resolution configurations. In the DNS resolution configurations, the ALB Ingress has a lower priority than the NGINX Ingress.
DNS does not allow you to add the same domain name to an A record and a CNAME record at the same time. CLB instances receive requests by using IP addresses whereas ALB instances use the default domain names. For more information, see What is ALB? Therefore, the company needs to configure a temporary domain name for the CLB instance to allow requests to be distributed to the NGINX Ingress and ALB Ingress based on weights.

Step 2: Gradually migrate traffic to the ALB Ingress
After the company runs tests and verifies that the ALB Ingress can forward traffic as expected, the company increases the weight of the DNS record for the ALB Ingress to allow more traffic to the ALB Ingress.

Step 3: Delete resources related to the NGINX Ingress
After all traffic is migrated to the ALB Ingress, the company deletes DNS configurations related to the NGINX Ingress, releases resources related to the NGINX Ingress, and uninstalls the NGINX Ingress controller. After the company completes Step 1 to Step 3, all network traffic is migrated from the NGINX Ingress to the ALB Ingress. The migration process is transparent to users.

Prerequisites
A kubectl client is connected to the ACK cluster. For more information, see Obtain the kubeconfig file of a cluster and use kubectl to connect to the cluster.
Step 1: Configure an ALB Ingress
Log on to the ACK console and install the ALB Ingress controller in the cluster that you want to migrate. For more information, see Manage the ALB Ingress controller. Set Gateway Source to None because the migration tool automatically converts the
AlbConfig,IngressClass, andIngress.ImportantTo allow access from the ALB Ingress to an ACK dedicated cluster, grant access permissions to the ALB Ingress controller before you deploy Services. For more information, see Authorize an ACK dedicated cluster to access the ALB Ingress controller.
Create a YAML file named ingress2albconfig.yaml and copy the following content to the file:
apiVersion: batch/v1 kind: Job metadata: name: ingress2albconfig namespace: default spec: template: spec: containers: - name: ingress2albconfig image: registry.cn-hangzhou.aliyuncs.com/acs/ingress2albconfig:latest command: ["/bin/ingress2albconfig", "print"] restartPolicy: Never serviceAccount: ingress2albconfig serviceAccountName: ingress2albconfig backoffLimit: 4 --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: system:ingress2albconfig rules: - apiGroups: - networking.k8s.io resources: - ingresses - ingressclasses verbs: - get - list - watch - update - create - patch --- apiVersion: v1 kind: ServiceAccount metadata: name: ingress2albconfig namespace: default --- kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: system:ingress2albconfig roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: system:ingress2albconfig subjects: - kind: ServiceAccount name: ingress2albconfig namespace: defaultRun the following code to run the Job. The Job automatically converts the configurations of the NGINX Ingress controller to
AlbConfig,IngressClass, andIngressconfigurations and outputs the configurations. You can view the configurations in the logs.kubectl apply -f ingress2albconfig.yamlExpected output:
job.batch/ingress2albconfig created clusterrole.rbac.authorization.k8s.io/system:ingress2albconfig created serviceaccount/ingress2albconfig created clusterrolebinding.rbac.authorization.k8s.io/system:ingress2albconfig createdView the pod to which the Job belongs.
kubectl get pod -l job-name=ingress2albconfigExpected output:
NAME READY STATUS RESTARTS AGE ingress2albconfig-vw*** 0/1 Completed 0 16mView the logs of the pod.
kubectl logs ingress2albconfig-vw*** # Replace it with the Pod name obtained in the last step.The following code shows the expected output. After you use the kubectl to deploy the resources to the cluster, the ALB Ingress is configured.
apiVersion: alibabacloud.com/v1 kind: AlbConfig metadata: creationTimestamp: null name: from_nginx spec: config: accessLogConfig: {} edition: Standard name: from_nginx tags: - key: converted/ingress2albconfig value: "true" zoneMappings: - vSwitchId: vsw-xxx # Replace it with the ID of the vSwitch in the VPC. - vSwitchId: vsw-xxx # Replace it with the ID of the vSwitch in the VPC. listeners: - port: 80 protocol: HTTP --- apiVersion: networking.k8s.io/v1 kind: IngressClass metadata: creationTimestamp: null name: from_nginx spec: controller: ingress.k8s.alibabacloud/alb parameters: apiGroup: alibabacloud.com kind: AlbConfig name: from_nginx scope: null --- apiVersion: networking.k8s.io/v1 kind: Ingress metadata: annotations: alb.ingress.kubernetes.io/listen-ports: '[{"HTTP":80}]' creationTimestamp: null name: from_ingress1 namespace: default spec: ingressClassName: from_nginx rules: - http: paths: - backend: service: name: nginx-svc-g1msr port: number: 80 path: / pathType: Prefix status: loadBalancer: {}
Automatically converted annotations
The migration tool automatically converts the NGINX Ingress annotations in the following table to ALB Ingress annotations.
The NGINX Ingress annotations not in the following table are ignored. We recommend that you check the configurations of the ALB Ingress after the conversion to prevent invalid configurations.
Step 2: Gradually migrate traffic to the ALB Ingress
Before you start the migration process, compare the forwarding rules between the NGINX Ingress and the ALB Ingress to ensure that the forwarding rules are the same. All the configurations must be tests in case issues arise.
We recommend that you switch network traffic during off-peak hours.
Configure a temporary domain name for the CLB instance
DNS does not allow you to add the same domain name to an A record and a CNAME record at the same time. In addition, ALB instances use the default domain name to provide services. Therefore, you must configure a temporary domain name for the CLB instance.
Log on to the Alibaba Cloud DNS console.
On the Domain Name Resolution page, find and click the domain name
www.example.net. This domain name points to the IP address of the CLB instance.On the DNS Settings page, click Add DNS Record. In the Add DNS Record panel, configure the following parameters and click OK.
Parameter
Description
Record Type
Select CNAME from the drop-down list.
Hostname
Enter the prefix of the domain name. In this example,
wwwis specified.DNS Request Source
Select Default.
Record Value
Enter the temporary domain name. In this example,
web0.example.netis specified.TTL
Specify a time-to-live (TTL) value for the CNAME record to be cached on the DNS server. In this example, the default value is used.
On the DNS Settings tab, find the A record that maps the domain name
www.example.netto the IP address of the CLB instance and click Modify in the Actions column.In the Modify DNS Record panel, modify the value of the Hostname parameter and click OK. In this example, the Hostname parameter is set to web0. The other parameters are not modified.
NoteAfter you complete the configurations, the domain name
www.example.netis mapped toweb0.example.net, which is resolved to the IP address of the CLB instance by the A record.
Add a CNAME record for the ALB instance
Run the following command to query the domain name of the ALB instance:
kubectl get albconfigThe following code block shows the expected output.
alb-a8mmh2tqbmrm11****.cn-hangzhou.alb.aliyuncs.comis the domain name of the ALB instance.NAME ALBID DNSNAME PORT&PROTOCOL CERTID AGE from_nginx alb-a8mmh2tqbmrm11**** alb-a8mmh2tqbmrm11****.cn-hangzhou.alb.aliyuncs.com 20mOn the DNS Settings page, click Add DNS Record. In the Add DNS Record panel, configure the following parameters and click OK.
Parameter
Description
Record Type
Select CNAME from the drop-down list.
Hostname
Enter the prefix of the domain name. In this example,
wwwis specified.DNS Request Source
Select Default.
Record Value
Enter the domain name of the ALB instance.
TTL
Specify a TTL value for the CNAME record to be cached on the DNS server. In this example, the default value is used.
Configure weights for the CNAME records
On the Domain Name Resolution page, click Weight Settings in the left-side navigation pane.
On the Weighted Round-robin page, click EnableWeight in the Actions column and click Set Weight.
In the Set Weight panel, configure weights for the DNS records of the CLB and ALB instances. Set the weight of the DNS record for the CLB instance to 100. Set the weight of the DNS record for the NLB instance to 0.
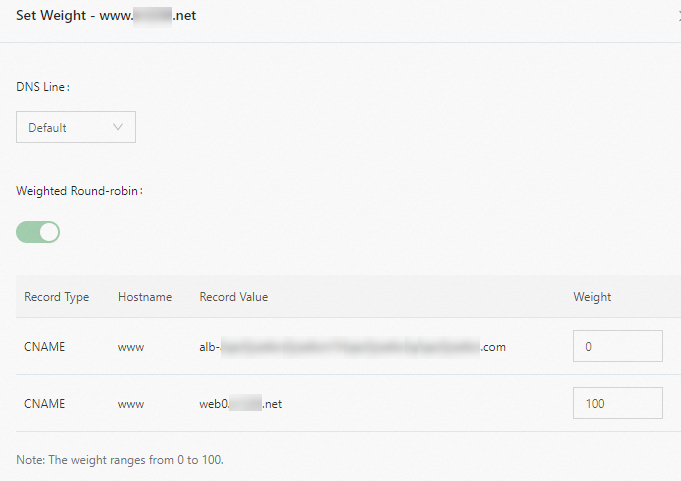
Gradually reduce the weight of the DNS record for the CLB instance and gradually increase the weight of the DNS record for the ALB instance. Make sure that your services are not affected.
Log on to the worker node on which the pods of the Service are deployed and run the
digcommand multiple times to check the traffic volume.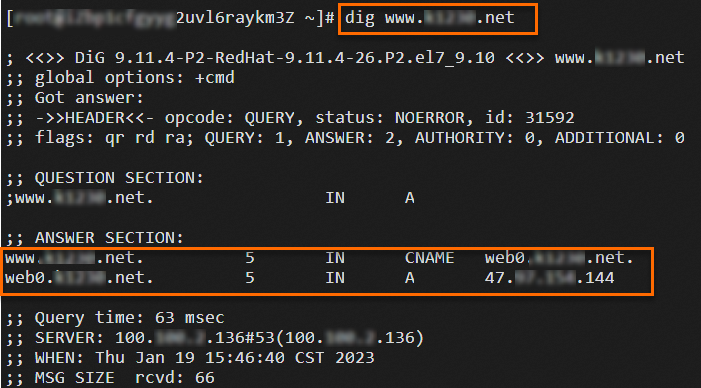
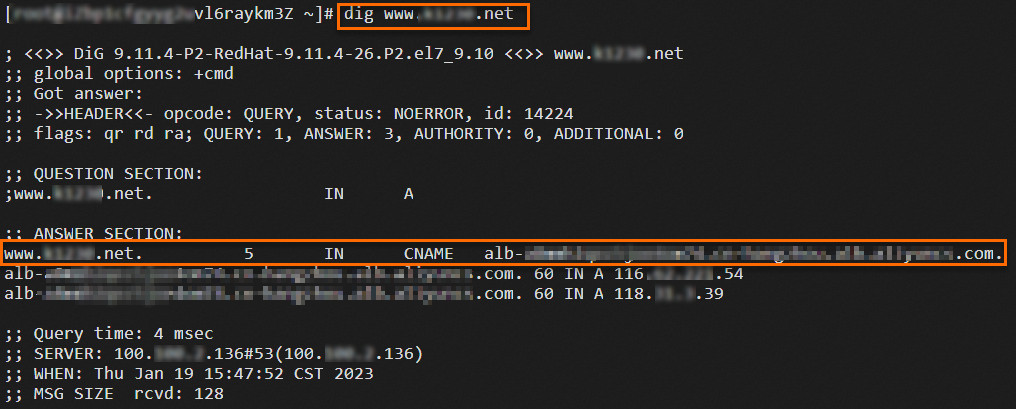
Gradually reduce the weight of the CLB DNS record to 0 while gradually increase the ALB DNS record to 100.
Step 3: Delete resources related to the NGINX Ingress
After you close all persistent connections on the NGINX Ingress and no traffic is forwarded to the NGINX Ingress, you can release redundant resources after a period of observation.
Log on to the Alibaba Cloud DNS console and delete all DNS records that are related to the NGINX Ingress.
Uninstall the NGINX Ingress controller.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage, and click the cluster name. In the left-side navigation pane, choose .
Find the NGINX Ingress and choose
 > Delete in the Actions column. In the message that appears, click OK.
> Delete in the Actions column. In the message that appears, click OK. In the left-side navigation pane, choose . Click the Networking tab, find the Nginx Ingress Controller card, and then click Uninstall.
In the message that appears, click OK.
NoteThe CLB instance that is associated with the NGINX Ingress controller is released along with the NGINX Ingress controller. You are no longer charged for the released resources.
References
ALB supports multiple configuration methods. For more information, see Use AlbConfig to configure ALB instances.
For more information about how to enable HTTPS for the ALB Ingress, see Configure certificates for encrypted communication over HTTPS.
For more information about the annotations supported by the ALB Ingress, see ALB Ingress GlobalConfiguration dictionary.