The feature of container asset overview allows you to perform security-related operations on your assets, such as clusters, containers, images, and applications, in a visualized manner. The feature also displays the network topology of your containers, which allows you to manage your containers in a more efficient manner. You can use this feature to obtain the up-to-date security information and network connections of your containers. This topic describes how to view the overall information about your containers.
Prerequisites
The feature of container asset overview displays the image vulnerability information that is obtained by using the feature of container image scan. If you want to view container risks, you must enable container image scan and scan images. For more information, see Enable container image scan and Scan images.
If you do not enable container image scan when you use container asset overview, you can view only the server vulnerabilities and the network topology of the current cluster. You cannot view the container vulnerabilities in the current cluster. To ensure the security of the container runtime environment, we recommend that you enable container image scan.
Background information
Security Center automatically refreshes the network topology of running containers and security information about the current cluster on the Container Asset Overview tab at intervals of 1 minute. This ensures that you can view the up-to-date network topology and security information.
Limits
Only the Ultimate edition of Security Center supports this feature. For more information about how to purchase and upgrade Security Center, see Purchase Security Center and Upgrade and downgrade Security Center.
Scenarios
Compliance with classified protection requirements
Container asset overview displays the network topology of your assets to ensure that your system meets the requirements of classified protection.
Visualization
Container asset overview automatically displays the ports that are exposed on the Internet. You can perform security-related operations on your assets, such as clusters, containers, images, and applications, in a visualized manner.
Procedure
Log on to the Security Center console. In the top navigation bar, select the region of the asset that you want to manage. You can select China or Outside China.
In the left-side navigation pane, click Overview.
On the Overview page, click the Container Asset Overview tab.
On the Container Asset Overview tab, view the overall information about your container assets.
The following figure shows the sections on the Container Asset Overview tab. The following list describes the operations that you can perform in each section.
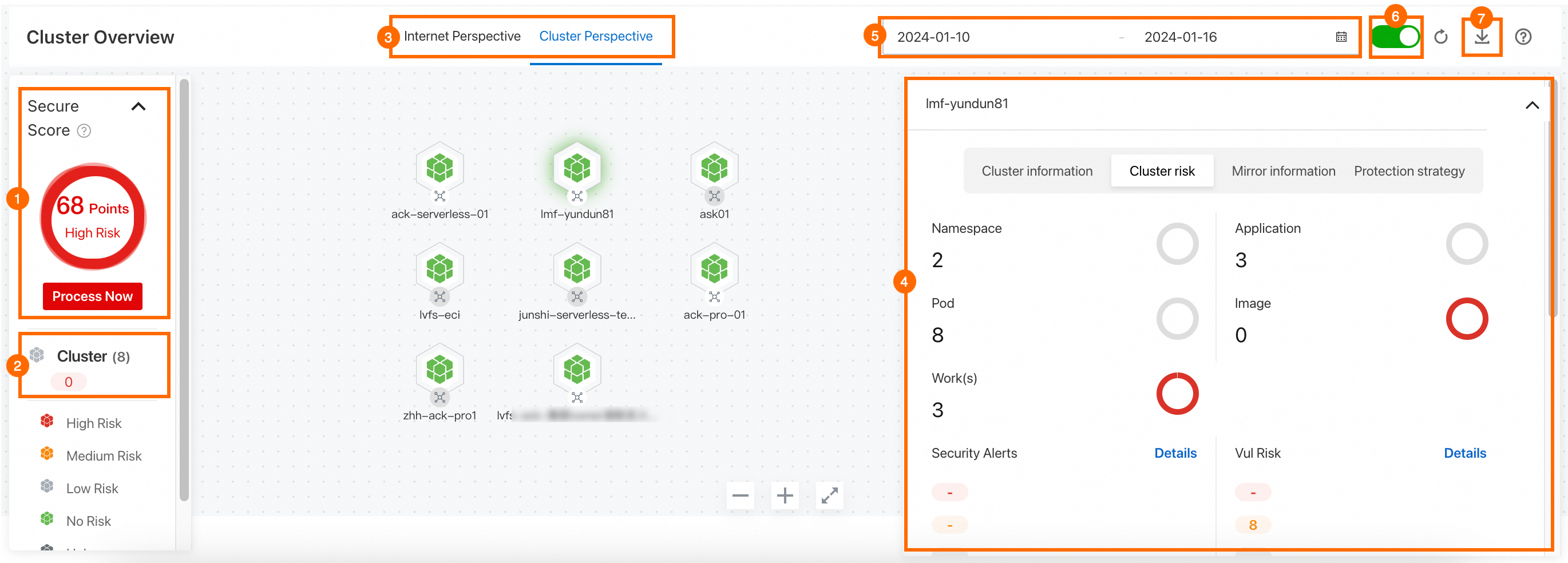
View the security score of your container assets (marked 1 in the figure)
In the left-side section of the Container Asset Overview tab, you can view the security score of your container assets. The security score is calculated based on the security information of your container assets. If you want to handle the risks in your container assets, you can click Fix Now to go to the Security Risk panel. A higher security score indicates fewer risks in your container assets. For more information about the security score, see Security score.
View the total numbers of clusters, applications, containers, nodes, and images, and the numbers of vulnerable clusters, applications, containers, nodes, and images (marked 2 in the figure)
In the left-side section of the Container Asset Overview tab, you can view the total numbers of clusters, applications, containers, nodes, and images. You can also view the numbers of vulnerable clusters, applications, containers, nodes, and images. A number in red indicates the number of vulnerable assets. If you want to view the details of a specific type of assets, you can click the asset type to go to the Assets page.
View the network topology of a cluster by perspective (marked 3 in the figure)
On the Container Asset Overview tab, the network topology of a cluster is displayed by perspective. You can view the network topology on the Internet Perspective or Cluster Perspective tab. In the upper part of the network topology, you can click Internet Perspective or Cluster Perspective based on your business requirements.
View the details and security information of a cluster (marked 4 in the figure)
On the Container Asset Overview tab, click the required cluster. In the panel that appears, you can view the information about the cluster on the following tabs: Cluster information, Cluster risk, Mirror information, and Protection strategy.
Cluster information
On the Cluster information tab, you can view the following basic information about the cluster: Name and Cluster Type. You can also view the numbers of the following items in the cluster: Namespace, Pod, Work(s), Application, and Image.
Cluster risk
On the Cluster risk tab, you can view the security risks of the cluster, such as Security Alerts, Baseline Risks, and Application Vul(s). Click Details to the right of Security Alerts. On the details page of the cluster or the vulnerability list of the Image Security page, view the details of the detected risks and handle the risks. For more information about how to handle risks, see View and handle alert events, Vulnerability fixing overview, and View and handle detected image risks.
Mirror information
On the Mirror information tab, you can view the images that belong to the cluster. Find an image whose image repository is not added to Security Center and click Access Now on the right side to go to the Image Security page. On the Image Security page, you can add the image repository to Security Center. For more information about how to add an image repository to Security Center, see Add image repositories to Security Center.
Protection strategy
On the Protection strategy tab, you can view Defense details. The defense details include the following information: Number of intercepted alarms in the past 7 days, Total number of rules, and Defensive status. Click Create rules to go to the Create rules panel. In the panel, you can create protection rules for the cluster.
View the network topology of a cluster in a specified time range (marked 5 in the figure)
By default, the Container Asset Overview tab displays the overview of your cluster traffic in the last seven days. You can use the date picker in the upper-right corner of the Container Asset Overview tab to specify a time range based on your business requirements. Then, the tab displays the overview of your cluster traffic within the specified time range. You can specify a time range within the last seven days.
Turn on or turn off Enable the network topology of all clusters (marked 6 in the figure)
By default, the network topology of all clusters is enabled. After you enable the network topology of all clusters, a small number of CPU resources are consumed. If you do not require the network topology of all clusters, you can click the
 icon in the upper-right corner of the Container Asset Overview tab and click the
icon in the upper-right corner of the Container Asset Overview tab and click the  icon. If you want to view the network topology of all clusters, you can turn on Enable the network topology of all clusters. Note
icon. If you want to view the network topology of all clusters, you can turn on Enable the network topology of all clusters. NoteWe recommend that you turn on Enable the network topology of all clusters so that you can obtain the security status of each node in the network topology of all clusters.
Export a container asset overview (marked 7 in the figure)
You can click the
 icon in the upper-right corner of the Container Asset Overview tab to export a container asset overview. The exported container asset overview is in the PNG format.
icon in the upper-right corner of the Container Asset Overview tab to export a container asset overview. The exported container asset overview is in the PNG format. View the container asset overview of a cluster
You can use one of the following methods to view the container asset overview of a cluster:
On the Cluster information tab, click View to the right of Container Network Topology.
On the Container Asset Overview tab, click the
 icon below the cluster.
icon below the cluster.
On the page that displays the container asset overview of the cluster, an application is a node in the overview. The overview provides the communication links among all containers in the cluster.
In the left-side section of the page, you can turn on or turn off Show only connected applications, Display port information, and Hide lines to view the topology information based on your business requirements.
In the left-side section of the page, you can view all namespaces that belong to the cluster. You can click the
 icon to the right of a namespace to hide or show the namespace. You can also click the
icon to the right of a namespace to hide or show the namespace. You can also click the  icon to the right of a namespace to hide or show the details of the namespace. Note
icon to the right of a namespace to hide or show the details of the namespace. NoteIf a cluster contains a large number of applications, the container asset overview of the cluster is hidden by default.
Click an application in the container asset overview of the cluster and view the following information in the panel that appears: pod information, Mirror information, and Network connection. On the pod information tab, move the pointer over the name of a pod. Then, the pod details message appears. In the message, click View assets to view the information such as Vulnerability and Alerts.