The threat analysis and response feature provides predefined detection rules that can be used to detect security alerts, analyze collected logs, identify attack chains, and generate security events. You can enable or disable predefined detection rules. You can also create custom detection rules to ensure that generated security events meet your business requirements.
Multi-account management
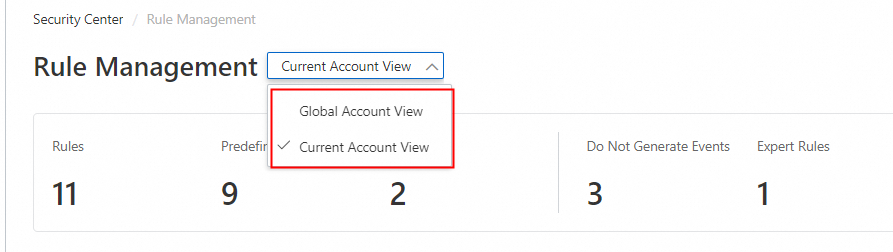
If you configure the multi-account management feature and use the global administrator account to log on to the Security Center console, you must select an appropriate view before you can create custom detection rules or manage datasets on the Rule Management page. The following list describes the supported views:
Current Account View: The detection rules and datasets that are created take effect only on the log data within the current account.
Global Account View: The detection rules and datasets that are created take effect on the log data within the Alibaba Cloud accounts managed by the threat analysis and response feature.
For more information, see Centrally manage multiple accounts.
Manage detection rules
You can use detection rules to detect alerts and analyze logs of cloud services. You can specify a log range, matching fields, and aggregation fields in a rule to define the logic of automatic detection and log analysis for threat analysis and response. This helps identify security risks in your business systems in an efficient manner. The threat analysis and response feature supports predefined detection rules and custom detection rules. You can enable or disable predefined detection rules based on your business requirements. You can also create custom alert and event detection rules.
Enable or disable a predefined detection rule
Security Center provides a variety of predefined detection rules to generate alerts and events. The types of rules are Process Abnormal Behavior, Web Attack Successfully, Malicious Domain Query, Abnormal Login, Abnormal Network Flow, Malicious Network Access, and Abnormal Web Access. You can view the details of, enable, or disable a predefined detection rule. You cannot modify or delete predefined detection rules.
Log on to the Security Center console. In the top navigation bar, select the region of the asset that you want to manage. You can select China or Outside China.
In the left-side navigation pane, choose .
On the Predefined tab, view the predefined detection rules.

Optional. Find the required predefined detection rule and click Details in the Actions column to view the basic information, logic, and event generation settings of the rule.
Find the predefined detection rule that you want to manage and turn on or turn off the switch in the Rule Status column.

Create a custom detection rule
If predefined detection rules cannot meet your business requirements, you can perform the following steps to create a custom detection rule:
Log on to the Security Center console. In the top navigation bar, select the region of the asset that you want to manage. You can select China or Outside China.
In the left-side navigation pane, choose .
On the Custom tab, click Create Rule.
On the Create Rule page, configure the parameters.
Parameter
Description
Basic information
Specify the basic information about the rule.
Rule Name: Enter a name for the rule.
Rule Description: Enter a description for the rule for easy identification.
Threat Level: Select a risk level of the alerts or events that you want to generate by using the rule from the drop-down list. For more information about risk levels, see Risk levels.
Threat Type: Select a type of the threats that you want to identify by using the rule from the drop-down list. For more information about alert types, see Alert types.
Rule Logic Settings
Configure aggregation settings for security alerts.
Log Scope: Select the category and types of logs on which you want the rule to take effect.
Security Center displays available log types based on the cloud services that are added to the threat analysis feature.
Match Field: Specify the fields and field values based on which alerts and events are matched. Security Center displays available fields based on the settings that you specify in the Log Scope section.
You can add multiple fields to a field group for matching. To add another field, you can click Add Field. Multiple fields are evaluated by using a logical AND.
You can create multiple field groups. To create another field group, you can click Add Field Group. Multiple field groups are evaluated by using a logical OR.
Aggregation Field: Select the fields that you want to use for event aggregation.
Maximum Logs: Specify the condition based on which alerts are generated.
Statistical Period: Specify the time period of alerts that you want to aggregate.
Security Center aggregates alerts from logs of the specified type within the specified statistical period based on the aggregation fields.
Event Generation Settings
Specify whether to aggregate the alerts that are generated based on the rule into events.
If you select Yes, only the alerts that are generated based on the rule are aggregated into events. The following event aggregation methods are available:
Use Built-in Event Aggregation Rule: Alerts that are generated based on the rule are aggregated into predefined events. A predefined event refers to an event that is generated based on a predefined detection rule.
Aggregate Each Alert to Event: Each alert is aggregated into an event.
Aggregate All Rule-triggered Alerts into Event:
If you select this method, you need to configure the Execution Cycle parameter. During the time period specified by the Execution cycle parameter, alerts that are generated based on the rule are aggregated into one event. The maximum time period that you can specify is 24 hours.
Optional. Click Test and select a test method. The system tests whether the rule takes effect.
The following test methods are available:
Simulation Data: If you select this test method, you need to write SQL statements to test whether the rule takes effect. When you write SQL statements, you can refer to the example provided in the Simulated data value section on the Test page. After you enter simulated data values, click Test.
Business Data: If you select this test method, your actual business data is used to test whether the rule takes effect. Click Test to view the following information: the line chart of the numbers of alerts and events that are generated based on the rule, the list of alerts, and the list of events.
By default, the test is run for seven days. You can also click Publish or End Test to end the test in advance. After you click Publish, the rule immediately takes effect. After you click End Test, you need to click the
 icon to return to the Rule Management page. The rule is automatically created and disabled.
icon to return to the Rule Management page. The rule is automatically created and disabled. If you do not test the rule, confirm the rule settings on the Create Rule page and click Publish.
If you do not want the rule to immediately take effect, you can click Save as Draft to save the rule.
After the custom detection rule is created, you can view the details of, test, enable, disable, edit, and delete the rule on the Rule Management page.
Manage datasets
If you want to manage multiple data objects that are applicable to a specific scenario in a centralized manner, you can create a dataset and define the data objects in the dataset. Data objects include IP address blacklists and whitelists, lists of core assets, and indicators of compromise (IOC)-related custom threat intelligence. Datasets are two-dimensional tables that are used to maintain custom data lists. You can reference a dataset in a detection rule or Security Orchestration Automation Response (SOAR) playbook multiple times.
Create a dataset
In the left-side navigation pane, choose .
On the Dataset tab, click Add Dataset. The Add Dataset panel appears.
In the Dataset section, click Download File Template to download the dataset template file to your computer. Enter the required information in the dataset template file and save it.
Take note of the following items:
Before you upload the dataset template file, you must specify a primary key, which is used to search for and match logs. The primary key column cannot contain NULL or duplicate values.
If the primary key column contains duplicate values, the system automatically removes the duplicates.
The size of the dataset template file cannot exceed 3 MB.
The dataset template file can contain no more than 5,000 rows.
Each value in the dataset template file cannot exceed 200 bytes in length.
Return to the Add Dataset panel, configure the Dataset Name and Dataset Description parameters, upload the dataset template file, configure the Dataset Primary Key parameter, and then click Next.
The system automatically checks the validity of the values in the uploaded file. If a value is invalid, modify the value as prompted.
On the Verify and Create tab, confirm the information in the uploaded file and click OK.
What to do next
You can directly reference a dataset when you create a custom detection rule and SOAR playbook. For more information, see Handle security events and Step 1: Create a playbook.
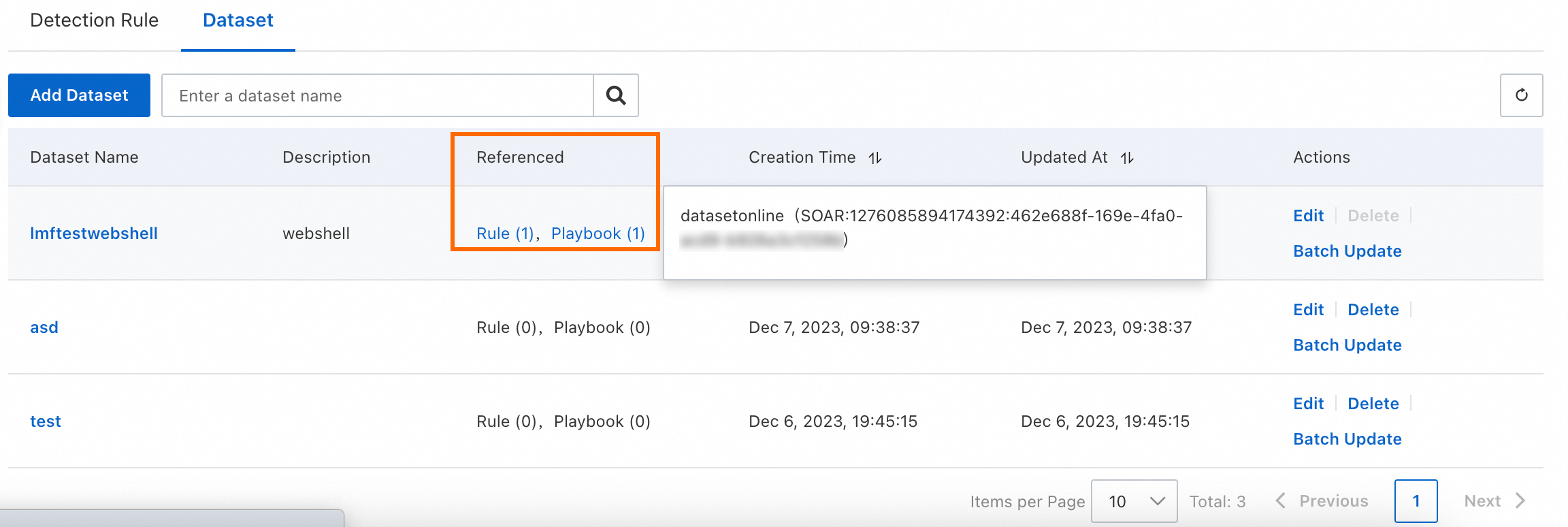
You can view reference information about a dataset in the Referenced column of the dataset on the Dataset tab.
More operations
To add data to a dataset or remove data from a dataset, find the dataset and click Edit in the Actions column.
To update multiple rows in a dataset at a time, open and edit the dataset template file that is saved on your computer, find the dataset on the Dataset tab, and then click Batch Update in the Actions column to upload the file.
To delete a dataset that you no longer use, find the dataset and click Delete in the Actions column.
NoteYou cannot delete a dataset that is referenced in a detection rule or playbook.
Configuration examples on custom detection rules
This section provides examples that you can refer to when you create custom detection rules in typical scenarios.
Union SQL injection
IP address of the scanner that attacks WAF
Suspicious sensitive command executed by a Java process
Host brute-force attack
Host connected to mining domain names
HTTP request burst
References
To ensure system security, we recommend that you view and handle security events that are generated by the threat analysis and response feature at the earliest opportunity. For more information, see Handle security events.
You can use the log management feature of threat analysis and response to quickly query logs and view information about logs. This helps reduce the difficulty of log management in a multi-resource environment. For more information, see Manage logs.
You can call rule management-related API operations to query rules, update the status of custom detection rules, and delete custom detection rules. For more information, see Rule Management.