When you use Serverless App Engine (SAE) to manage applications, a container is used as a temporary environment in which applications run and O&M is not required. SAE provides the built-in lightweight webshell feature in the SAE console to allow you to view and debug containers. This way, you can efficiently troubleshoot online issues. The base image of SAE application containers can be used by application runtimes, and the unstable application containers are for temporary use only. You do not need to enable SSH for the base image but only need to include the executable /bin/bash command in your code. We recommend that you prepare all required O&M tools to perform troubleshooting.
Limits
The webshell feature does not support Windows images.
Network environments
SAE applications are deployed in self-managed virtual private clouds (VPCs) that support the namespace feature. You can logically isolate service calls of middleware. A namespace can be associated with only one vSwitch in the VPC, but a vSwitch can be associated with multiple namespaces. The IP addresses of resources in a VPC can be accessed only within the VPC, and applications cannot interact with each other across VPCs. Namespaces are used to logically isolate middleware service calls. Applications in different namespaces are isolated in middleware service calls, such as service discovery and configuration delivery.
For information about the working mechanism and product introduction of VPC, see Service architecture.
The characteristics of VPC and SAE determine that SAE application containers cannot connect to services (except Alibaba Cloud services such as OSS and Container Registry) outside the VPC. If you do not configure additional settings, your SAE application containers run in an isolated network, and you cannot directly access the containers.
The following code provides an example on the failure in accessing an application container.
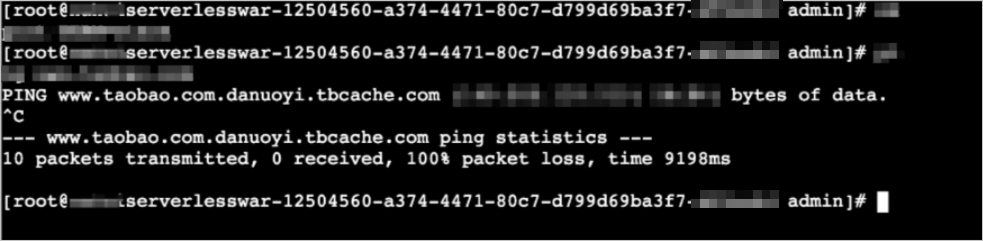
If you want your application instances to access services on the Internet, you must purchase a NAT gateway, and configure Source Network Address Translation (SNAT) for the vSwitch in the VPC. For more information, see Configure a NAT gateway for an SAE application to enable Internet access.
SNAT allows application instances in a VPC to access the Internet when no public IP addresses are assigned to the instances. You can configure SNAT entries for the instances to use elastic IP addresses (EIPs) that are associated with the NAT gateway. This way, the instances can call services over the Internet and obtain Internet resources. For more information, see Products with access to the Internet.
Build an image
SAE can work with Container Registry, allowing you to build and manage images. SAE provides the centos:7 base image, programming languages, codec, time zone, and development environments such as OpenJDK.
Containers are designed to facilitate application running and SAE integrates only a limited number of tools by default. If SAE integrates an excessive number of tools, the resource consumption of the tools may affect the status of applications. If you need tools that are not integrated in SAE, you must build images or obtain images from OSS. For more information, see Create an image to deploy a Java application.
Display the webshell window in full screen
You can perform the following steps to display the webshell window in full screen:
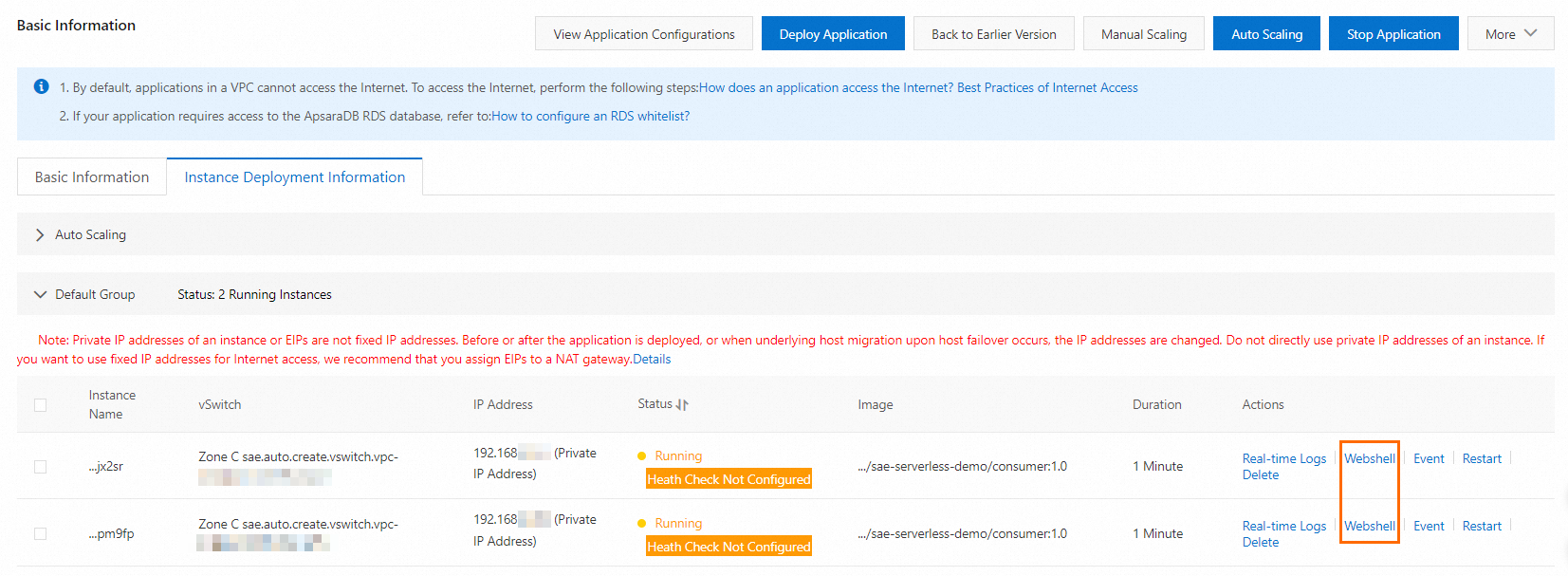
Log on to the SAE console.
In the left-side navigation pane, click Applications. In the top navigation bar, select a region. Then, click the name of an application.
On the Basic Information page, click the Instance Deployment Information tab.
In the Default Group section of the Instance Deployment Information tab, find the instance that you want to manage and click Webshell in the Actions column.
Optional. When the webshell window appears, click the
 icon in the upper right corner to display the window in full screen.
icon in the upper right corner to display the window in full screen. Run commands in the webshell window based on your business requirements to view and debug your containers.
For more information, see Obtain the metadata of application instances and Check the health status of applications.
Obtain the metadata of application instances
After you deploy an application to SAE, you can obtain the metadata of an application instance, including the security group ID, VPC ID, and vSwitch ID.
Metadata location | Description |
/etc/podinfo/sgId | The path in which the security group ID resides. |
/etc/podinfo/vpcId | The path in which the VPC ID resides. |
/etc/podinfo/vswitchId | The path in which the vSwitch ID resides. Note When multiple vSwitches exist, the vSwitch IDs are separated with commas (,). |
You can log on to the SAE console and run the following commands in the webshell window to verify the security group ID, VPC ID, and vSwitch ID.
Run the following command to open the
podinfodirectory:cd /etc/podinfo/NoteIf a
can't cd to /etc/podinfo/error is reported when you run the command, you can restart the instance or re-deploy the application.Run the following command to view all metadata files of the instance:
lsExpected output:
sgId vpcId vswitchIdRun the following commands based on your business requirements to verify the metadata of the application instance:
Run the following command to obtain the ID of the security group:
cat sgIdExpected output:
sg-2ze4ddm2rqgenvcx****sh-4.2#Run the following command to obtain the VPC ID:
cat vpcIdExpected output:
vpc-2zeqku2oevokwm66b****sh-4.2#Run the following command to obtain the vSwitch ID:
cat vswitchIdExpected output:
vsw-2zewmy4ynhljytzhu****sh-4.2#
Copy a command to install O&M components
You can log on to the SAE console, and perform the following steps to copy a command in the webshell window based on your business requirements. The command is used to install O&M components.
The commands installed in the webshell window are invalid after the container is rebuilt. For common commands, we recommend that you install them when you create an image.
Click the
 icon in the upper right corner of the webshell window.
icon in the upper right corner of the webshell window. In the Copy Command dialog box, select the required components, preview the displayed command, and then click Copy. The Select Install Components parameter provides the following options:
Install openssh: OpenSSH is a free and open source implementation of the SSH protocol. OpenSSH provides the server-side backend program and client tool to encrypt data that is transmitted in remote control and file transfer. You can install OpenSSH and then use remote debugging to implement the following functions: remote login over the SSH protocol, and file upload and download by using sftp and scp. This way, you can debug an SAE application instance to meet an unexpected requirement.
Install net-tools (netstat): The netstat command is used to monitor the network status. You can run this command to display the route table, active network connections, and the status of network interfaces.
Install iroute (ss): The socket statistics (ss) command is used to display socket statistics that are similar to the information obtained by running the netstat command. Compared with running the netstat command, you can quickly obtain more information about TCP connections by running the ss command.
Paste the command that you copied in the webshell window and press Enter to execute the command.
Check the health status of applications
Perform routine checks on applications
You can perform routine checks or upload and download logs to check the health status of SAE applications. Multiple routine checks are available. For example, you can check the process, thread, and Java virtual machine (JVM) of Java applications. This section describes how to check the process of a Java application and how to perform online analysis on a Java application.
Run the following command to check whether the Java application has available processes:
ps -ef | grep javaNoteIn a container, the main process is used to start an application. If the application is stopped, the container exits. SAE automatically restarts the container to prevent service interruptions.
If no processes are available, run the
dmesg | grep -i killcommand to check the out of memory (OOM) logs.If the OOM logs exist, the application process is stopped. You need to check the log file named
hs_err_pid{PID}.login the working directory to identify the cause.
You can also use the open source software Arthas provided by Alibaba Cloud to perform online analysis on Java applications. We recommend that you integrate Arthas into the test image to perform routine checks. Arthas can display the loading status of Java classes in real time. This way, you can view the input and output parameters and environment variables.
Connect the application to the Internet.
For more information, see Configure a NAT gateway for an SAE application to enable Internet access.
Run the following command to download Arthas:
sudo wget https://alibaba.github.io/arthas/arthas-boot.jarRun the following command to start Arthas:
sudo java -jar arthas-boot.jar
Upload and download logs to check the health status of applications
If routine checks cannot provide the required information, you can upload logs that are collected from the containers to the cloud, and then download the logs to your on-premises machine for application analysis.
If log files are smaller than or equal to 10 MB in size, you can use the built-in webshell feature of SAE. For information, see Use the webshell feature to upload and download files.
If log files are larger than 10 MB in size, you can upload the log files to OSS. The OSS service is compatible with all network environments in Alibaba Cloud. You can perform the following steps to use OSS to upload and download logs.
Install the OSS command-line tool ossutil in the container. For more information, see Install ossutil.
In this example, the user of the 64-bit CentOS wants to download the logs. If the application is not connected to the Internet, the root user must download the log file to the on-premises machine, upload the downloaded file to OSS, and then obtain an internal address that can be accessed within the VPC from OSS to download the file.
Run the following command to download ossutil:
sudo wget http://gosspublic.alicdn.com/ossutil/1.5.0/ossutil64Run the following command to modify the execution permissions on the ossutil installation package:
sudo chmod 755 ossutil64
Configure the ossutil and specify the internal endpoint of the VPC in the region where your application resides. Specify the AccessKey pair of the account that you want to use to receive uploaded files, view existing buckets, and check whether your OSS service is available.
NoteMake sure that the OSS service is activated for your Alibaba Cloud account. The account may not be the account that is used to manage SAE applications.
Make sure that buckets are created. For more information, see Create buckets.
Run the following command to create a configuration file that stores OSS access information:
You can follow the on-screen instructions to specify your AccessKey pair and endpoint information. You do not need to specify the Security Token Service (STS) token.
./ossutil64 configRun the following command to list all buckets:
Check whether the account can be used. If an error is reported, the configuration is invalid.
./ossutil64 lsSample output:
CreationTime Region StorageClass BucketName 2021-12-08 18:53:46 +0800 CST oss-cn-hangzhou Standard oss://test-bucketRun the following command to create a simulated log file named sae-app.log.
echo "Hello" > sae-app.logRun the following command to upload the log file to a specified bucket:
./ossutil64 cp sae-app.log {bucket-address}Sample code:
./ossutil64 cp sae-app.log oss://test-bucket
Use one of the following methods to verify the result.
Method 1: Run the following command to view the uploaded log file:
./ossutil64 ls oss://test-bucketSample output:
LastModifiedTime Size(B) StorageClass ETAG ObjectName 2021-12-08 19:26:18 +0800 CST 6 Standard 09F7E02F1290BE211DA707A266F1**** oss://cri-55md3gmii09m****-chart/sae-app.log Object Number is: 1 0.047758(s) elapsedMethod 2: Find your log file in the OSS console or by using tools. Then, download the file to your on-premises machine, and choose a tool to analyze the application status.