Before you create or update a custom access control policy, you must understand the basic elements of an access control policy. An access control policy consists of the following basic elements: Effect, Action or NotAction, Resource, and Condition.
Element | Description |
Effect | Specifies whether a statement result is an explicit allow or an explicit deny. Valid values:
|
Action or NotAction | Describes one or more API operations that are allowed or denied. You can specify either Action or NotAction in a policy.
|
Resource | Specifies one or more objects that the statement covers. |
Condition | Specifies the conditions that are required for a policy to take effect. |
Effect
The Effect element specifies whether a statement result is an explicit allow or deny. This element is required.
Valid values: Allow and Deny.
If a RAM policy includes an Allow statement and a Deny statement at the same time, the Deny statement takes precedence over the Allow statement.
Example:
"Effect": "Allow"Action/NotAction
The Action element describes one or more API operations that are allowed or denied. This element is required. You can specify either Action or NotAction in a policy.
Valid values are the names of operations from Alibaba Cloud services in the <ram-code>:<action-name> format.
ram-code: the code used in RAM to indicate an Alibaba Cloud service. For more information, see the codes listed in the RAM code column in Services that work with RAM.action-name: the name of one or more API operations in the service.
In most cases, the value of the Action element is not case-sensitive. However, we recommend specifying <ram-code> and <action-name> based on the documents for permissions on Alibaba Cloud services to ensure consistency.
Examples:
Action example
"Action": [ "oss:ListBuckets", "ecs:Describe*", "rds:Describe*" ]NotAction example
The following example policy allows all operations except for those in RAM. Instead of listing all allowed actions, it only specifies the exceptions (ram:*), making the statement more concise.
ImportantUsing the NotAction element may grant broad permissions. Always verify that it meets your security requirements before applying.
{
"Effect": "Allow",
"NotAction": "ram:*",
"Resource": "*"
}Resource
The Resource element specifies one or more objects that the statement covers. This element is required and available only for identity-based policies.
Valid values are the Alibaba Cloud Resource Names (ARNs) of resources in the acs:<ram-code>:<region>:<account-id>:<relative-id> format. Make sure that you specify ARNs based on the documents for permissions on Alibaba Cloud services.
Fields:
acs: the initialism of Alibaba Cloud Service, which indicates the public cloud of Alibaba Cloud.ram-code: the code used in RAM to indicate an Alibaba Cloud service. For more information, see the codes listed in the RAM code column in Services that work with RAM.region: information about the region. If the statement covers a global resource, set this field to an asterisk (*). A global resource can be accessed without the need to specify a region. For more information, see Regions and zones.account-id: the ID of the Alibaba Cloud account. Example:123456789012****.relative-id: the identifier of the service-related resource. The meaning of this element varies based on services. The format of the relative-id element is similar to a file path. For example,relative-id = "mybucket/dir1/object1.jpg"indicates an Object Storage Service (OSS) object.
Example:
"Resource": [
"acs:ecs:*:*:instance/inst-001",
"acs:ecs:*:*:instance/inst-002",
"acs:oss:*:*:mybucket",
"acs:oss:*:*:mybucket/*"
]Condition
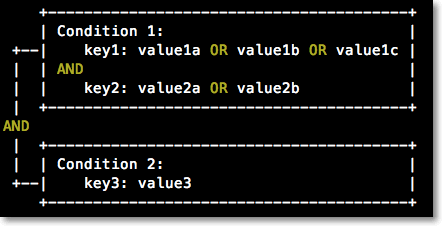
The Condition element specifies the conditions that are required for a policy to take effect.
It is considered a condition block, which contains one or more conditions. Each condition consists of conditional operators, condition keys, and condition values.
The Condition element is optional. The system does not check whether the Condition element is specified. If you want to specify a value for the Condition element, make sure that the spelling and capitalization are correct.
Condition keys are case-sensitive. Case sensitivity for condition values varies based on the conditional operators that you use. If the condition key is of the string type and you use the StringEquals conditional operator, the system performs a case-sensitive match by comparing the value in a request with the condition value. If the key is of the string type and you use the StringEqualsIgnoreCase conditional operator, the system performs a non-case-sensitive match by comparing the value in a request with the condition value.
Evaluation logic
You can specify one or more values for a condition key. If the value in a request matches one of the specified values, the condition is met.
A condition can have multiple keys that are attached to a single conditional operator. This type of condition is met only if all requirements for the keys are met.
A condition block is met only if all conditions are met.
Conditional operators
Conditional operators can be classified into the following categories: string, number, date and time, Boolean, and IP address.
Category
Conditional operator
String
StringEquals
StringNotEquals
StringEqualsIgnoreCase
StringNotEqualsIgnoreCase
StringLike
StringNotLike
Number
NumericEquals
NumericNotEquals
NumericLessThan
NumericLessThanEquals
NumericGreaterThan
NumericGreaterThanEquals
Date and time
DateEquals
DateNotEquals
DateLessThan
DateLessThanEquals
DateGreaterThan
DateGreaterThanEquals
Boolean
Bool
IP address
IpAddress
NotIpAddress
Condition keys
The format of common condition keys is
acs:<condition-key>.Common condition key
Type
Description
acs:CurrentTimeDate and time
The time at which a request is received by the web server.
NoteSpecify the time in the ISO 8601 standard. The time must be in UTC.
For example, use
2023-01-10T20:00:00+08:00or2023-01-10T12:00:00Zto indicate January 10, 2023, 20:00:00 (UTC+8).acs:SecureTransportBoolean
Specifies whether a secure channel is used to send a request. For example, a request can be sent over HTTPS.
acs:SourceIpIP address
The IP address of the client that sends a request.
NoteThe format of common condition keys is
acs:<condition-key>. If the value is a single IP address, you must specify the specific IP address rather than a CIDR block. For example, you must specify 10.0.0.1 rather than 10.0.0.1/32.acs:MFAPresentBoolean
Specifies whether multi-factor authentication (MFA) is used during user logon.
NoteIf MFA for RAM User Logons is set to Required Only for Unusual Logon in the RAM user security settings, the
acs:MFAPresentcondition key becomes invalid. For more information, see Manage security settings of RAM users.acs:PrincipalARNString
The identity of the requester. The condition key can be used only in access control policies of resource directories and trust policies of RAM roles. Example:
acs:ram:*:*:role/*resourcedirectory*.NoteYou can specify an ARN only for a specified RAM role. The name can contain only lowercase letters. You can view the ARN of a RAM role on the role details page in the RAM console.
acs:PrincipalRDIdString
The ID of the resource directory to which the Alibaba Cloud account of the requester belongs. The condition key can be used only in trust policies of RAM roles and OSS bucket policies.
acs:PrincipalRDPathString
The path in the resource directory to which the Alibaba Cloud account of the requester belongs. The condition key can be used only in trust policies of RAM roles and OSS bucket policies.
acs:RequestTag/<tag-key>String
The tag that is passed in a request. <tag-key> indicates a tag key. Replace <tag-key> with the actual tag key. For more information about the supported Alibaba Cloud services and resource types, see Tag Ram Support in Services that work with Tag.
acs:ResourceTag/<tag-key>String
The tag that is bound to the requested resource. <tag-key> indicates a tag key. Replace <tag-key> with the actual tag key. For more information about the supported Alibaba Cloud services and resource types, see Tag Ram Support in Services that work with Tag.
The format of a condition key that is specific to an Alibaba Cloud service is
<ram-code>:<condition-key>.For example,
oss:Delimiteris used to group the names of objects that you want to list by calling the ListObjects operation.For more information about condition keys of each cloud service, see the authorization document of each cloud service.
Examples
The logical relationship between two conditions in a statement is AND. If you want to set the logical relationship between the conditions to OR, you must specify the conditions separately in two statements.
Example 1: Allow only RAM users for whom MFA is enabled and who access ECS instances from the IP address 203.0.113.2 to access the ECS instances.
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": "ecs:*", "Resource": "*", "Condition": { "IpAddress": { "acs:SourceIp": [ "203.0.113.2" ] }, "Bool": { "acs:MFAPresent": [ "true" ] } } } ] }Example 2: Allow only RAM users for whom MFA is enabled or who access ECS instances from the IP address 203.0.113.2 to access the ECS instances.
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": "ecs:*", "Resource": "*", "Condition": { "IpAddress": { "acs:SourceIp": [ "203.0.113.2" ] } } }, { "Effect": "Allow", "Action": "ecs:*", "Resource": "*", "Condition": { "Bool": { "acs:MFAPresent": [ "true" ] } } } ] }
References
The syntax and structure of access control policies are similar to those of the permission policies in RAM. For more information, see Policy structure and syntax.