What is an SLR?
A service-linked role (SLR) is a unique type of Resource Access Management (RAM) role that is linked directly to an Alibaba Cloud service. The service can assume this role to perform actions in other services on your behalf.
An SLR's trust policy is predefined and allows only the linked cloud service to assume it. No other principals, such as a RAM user or another role, can assume an SLR.
An SLR's access policies are also predefined by the cloud service. You cannot modify the policies or attach additional ones. This ensures that the service only has the permissions it needs to function (principle of least privilege).
Why use SLRs?
SLRs simplify the process of granting permissions to Alibaba Cloud services. You don't need to manually create and manage RAM roles for them. SLRs offer several advantages:
Simplified setup: Services that use SLRs handle the RAM role creation and permission configuration for you. For example, when you enable Cloud Config, it automatically creates an SLR that grants it the necessary read access to resources like Elastic Compute Service (ECS) instances and ApsaraDB RDS databases. You don't have to create a RAM role or write policies manually.
Improved security: Because the access policies for an SLR are predefined and cannot be modified, the cloud service cannot perform actions beyond its intended purpose. The locked-down trust policy also prevents misuse of the SLR by other principals.
How it works
The following example shows how Cloud Config uses an SLR:

When you activate Cloud Config, the service creates its SLR—
AliyunServiceRoleForConfig—in your account.Trust policy: Allows only
config.aliyuncs.comto assume the role, which ensures that only Cloud Config can use it.Access policy: Grants permissions to access resources from Alibaba Cloud services such as ECS and ApsaraDB RDS.
The service assumes the SLR. Cloud Config (acting as the service principal
config.aliyuncs.com) assumes this SLR to obtain temporary credentials.The service performs actions. Using the SLR's credentials, Cloud Config makes read-only API calls to services like ECS and ApsaraDB RDS to retrieve configuration data and generate compliance reports.
In this way, Cloud Config can securely and easily access other services without your having to configure complex access policies manually.
Comparison with service roles
SLRs and service roles are both assumed by cloud services but differ in how they are created, managed, and customized.
Aspect | SLR | Service role |
Creation | In most cases, created automatically by the linked service. | Typically manually created by an administrator. |
Maintenance | Managed by the linked service. You cannot modify the role or its policies. | Managed by an administrator. You can modify the role and its policies. |
Deletion | Can only be deleted after all dependent resources in the linked service are removed. | Can be deleted at any time by an administrator. |
Access policy | Predefined by the service and cannot be modified. | User-defined. You can attach and detach policies as needed. |
Trust policy | Predefined to trust only the linked service and cannot be modified. | User-defined. You can specify which principals (including services) can assume the role. |
Many Alibaba Cloud services use SLRs to interact with other services on your behalf. For a complete list of services that work with SLRs, see Services that work with service-linked roles.
Manage SLRs
This section describes the permissions required to manage SLRs and the procedures for creating and deleting them.
You can only create or delete SLRs. You cannot modify an SLR's name, access policies, or trust policy.
A RAM user needs the ram:CreateServiceLinkedRole and ram:DeleteServiceLinkedRole permissions to create and delete SLRs, respectively. These permissions are typically included in the full-access system policy for the corresponding service (such as AliyunResourceDirectoryFullAccess).
Alternatively, you can create a custom policy to grant permissions for managing SLRs for a specific service. The following policy allows a RAM user to create and delete SLRs for the Resource Management service only. For ram:ServiceName values, see the "Service identifier" column in Services that work with service-linked roles.
{
"Version": "1",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ram:CreateServiceLinkedRole",
"ram:DeleteServiceLinkedRole"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"ram:ServiceName": "resourcemanager.aliyuncs.com"
}
}
}
]
}Create an SLR
Automatic creation: In most cases, the linked service creates the SLR for you automatically the first time you use a feature that requires it. This might happen when you enable a service, create a resource, or perform another action in the service's console.
Manual creation: If the SLR was not created automatically, you can create it manually through the RAM console, API, or CLI. For instructions, see Create an SLR.
Although SLRs count toward your account's role quota, their creation is not blocked when the quota is reached; however, the creation of all other role types will be blocked until existing roles are deleted. For more information, see Limitations.
Delete an SLR
Automatic deletion: Some services may automatically delete the SLR when you disable the service or delete all of its associated resources.
Manual deletion: You can manually delete an SLR using the RAM console, API, or CLI. When you attempt to delete an SLR, RAM checks if it is still in use.
If the role is not in use, the deletion succeeds.
If the role is in use, the deletion fails and an error message indicates which resources are still using the role. You must remove those dependent resources before you can delete the SLR. For the specific cleanup steps for each service, see the service's documentation.
Deleting an SLR may cause the linked service to stop functioning correctly. Before deleting an SLR, ensure you no longer need the features provided by the service.
Assume an SLR
Only the linked cloud service can assume its SLR. You cannot directly assume an SLR from the console or by calling AssumeRole as a user or another role.
View the trusted service
You can view the trusted service principal for an SLR by inspecting its trust policy. In the RAM console, navigate to the role's details page and select the Trust Policy tab. The Service field in the Principal element identifies the service that is allowed to assume the SLR.
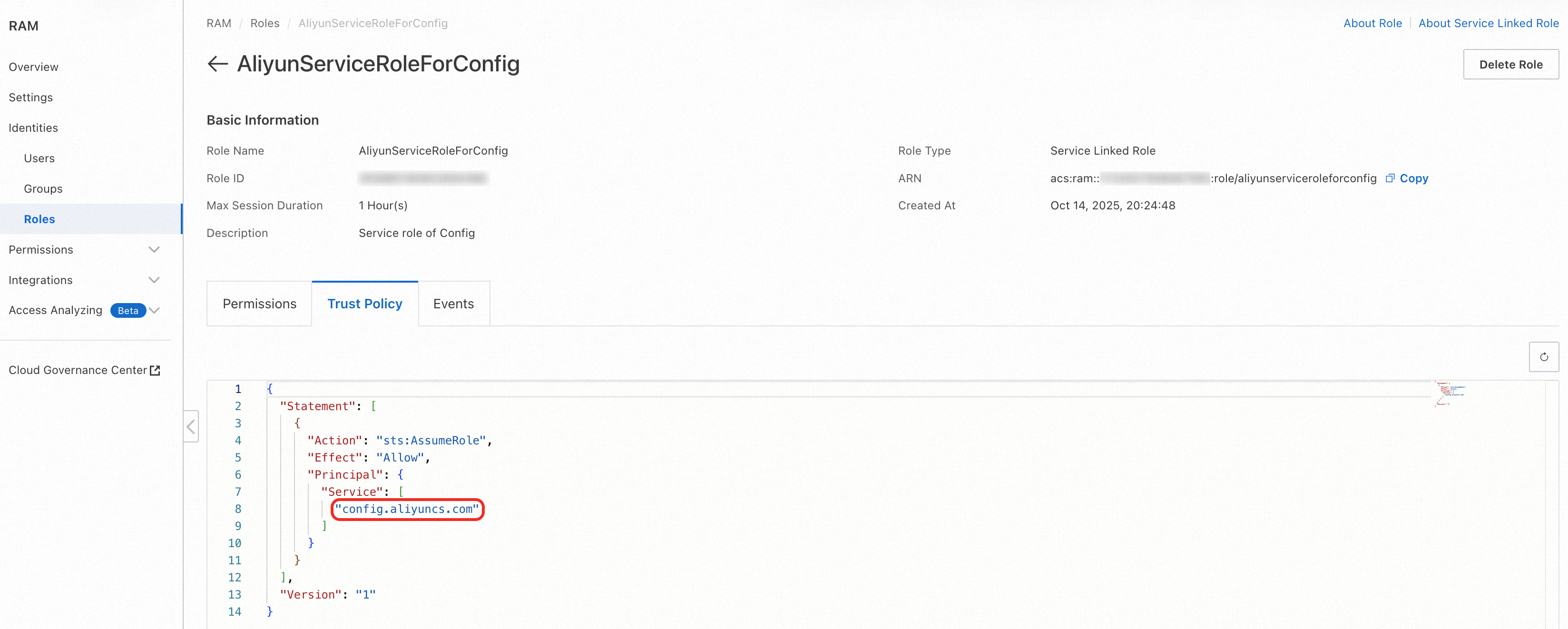
Monitor SLRs with ActionTrail
You can track the creation, deletion, and usage of SLRs by reviewing your ActionTrail logs.
Audit SLR lifecycle and assumption
To track when an SLR is created, deleted, or assumed, search for the following event names in the ActionTrail console:
CreateServiceLinkedRole: Records the creation of an SLR.DeleteServiceLinkedRole: Records the deletion of an SLR.AssumeRole: Records when a service assumes an SLR. In the event details, theuserIdentity.principalIdfield shows the service principal (such astag.aliyuncs.com), and therequestParameters.RoleArnfield shows the ARN of the SLR that was assumed.{ ... "requestParameters": { ... "RoleArn": "acs:ram::ACCOUNT_ID:role/aliyunservicerolefortag", "RoleSessionName": "tag_operate", }, ... "userIdentity": { ... "principalId": "tag.aliyuncs.com", "userName": "tag.aliyuncs.com" }, "eventName": "AssumeRole" }
Audit SLR activity
To see the actions performed by an SLR after it has been assumed, search for the SLR name in the Operator filter.
FAQ
An SLR's access policy seems too broad. Is this a security risk?
No. SLRs are designed with security in mind:
The access policies are crafted by the service team to include only the permissions required for the service to function.
The trust policy is locked and allows only the specific linked service to assume the role.
If you have concerns about the permissions of a specific SLR, consult that service's documentation or contact support.
Why am I unable to delete an SLR?
You cannot delete an SLR if it is still associated with resources in the linked service. The deletion will fail with an error message listing the dependent resources. You must remove those resources first before you can delete the role. For more information, see the "Delete an SLR" section in this topic.