When you access the Realtime Compute for Apache Flink console as a Resource Access Management (RAM) user or by using a RAM role and perform operations such as purchasing, viewing, or deleting a workspace, the RAM user or RAM role must have the required permissions. This topic describes the RAM policy types that are supported by Realtime Compute for Apache Flink and how to grant permissions to a RAM user.
Policy types
A policy defines a set of permissions that are described based on the policy structure and syntax. You can use policies to describe the authorized resource sets, authorized operation sets, and authorization conditions. For more information about the policy elements, structure, and syntax, see Policy elements and Policy structure and syntax.
RAM supports the following two types of policy:
System policy: System policies are created and updated by Alibaba Cloud. You can use system policies, but you cannot modify the policies. For more information about the system policies that are supported by Realtime Compute for Apache Flink, see the System policies section of this topic.
Custom policy: You can create, update, and delete custom policies to meet your business requirements. For more information about the custom policies that are supported by Realtime Compute for Apache Flink, see the Custom policies section of this topic.
Procedure
You can attach a policy to a RAM user or RAM role to grant the RAM user or RAM role the access permissions in the policy. This section describes how to grant permissions to a RAM user. The operations for granting permissions to a RAM role are similar to the operations for granting permissions to a RAM user. For more information, see Grant permissions to a RAM role.
Log on to the RAM console as a RAM administrator.
In the left-side navigation pane, choose .
On the Users page, find the required RAM user, and click Add Permissions in the Actions column.
You can also select multiple RAM users and click Add Permissions in the lower part of the page to grant permissions to the RAM users at a time.
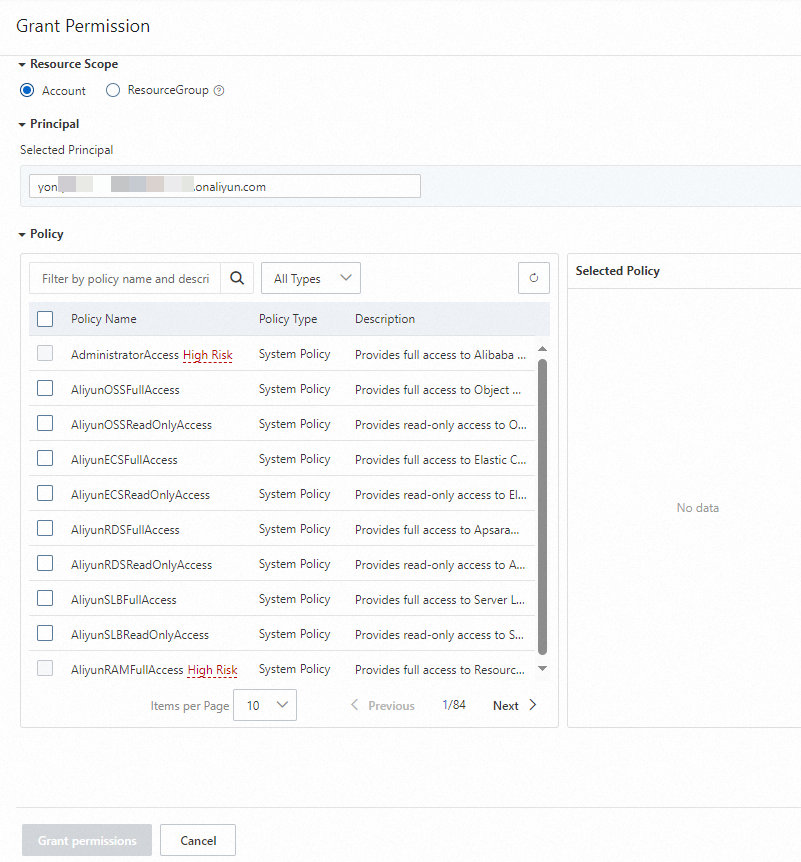
In the Grant Permission panel, grant permissions to the RAM user.
Parameter
Description
Resource Scope
The scope of resources that you can access with the granted permissions. Valid values:
Account: The permissions are granted to the current Alibaba Cloud account.
ResourceGroup: The permissions are valid for a specific resource group.
Principal
The principal is the RAM user to which you want to grant permissions. By default, the current RAM user is specified as the principal. You can also specify another RAM user.
Policy
System policy: For more information about the system policies that are supported by Realtime Compute for Apache Flink, see the System policies section of this topic.
Custom policy: For more information about how to create a custom policy, see Create custom policies. For more information about the custom policies that are supported by Realtime Compute for Apache Flink, see the Custom policies section of this topic. The following sample code provides the document of a policy that allows a RAM user to view the information about all workspaces.
{ "Version": "1", "Statement": [ { "Action": "stream:DescribeVvpInstances", "Resource": "*", "Effect": "Allow" } ] }
Click Grant permissions.
Click Close.
System policies
Permission set | Policy | Description |
All permissions on Realtime Compute for Apache Flink | AliyunStreamFullAccess | Includes all permissions in Custom policies. |
Permissions to access Realtime Compute for Apache Flink in read-only mode | AliyunStreamReadOnlyAccess | Includes all permissions that start with Describe and Query in Custom policies. |
Permissions on Expenses and Costs | AliyunBSSOrderAccess | Allows you to view and pay for orders in the Expenses and Costs console. |
Custom policies
Policies related to Realtime Compute for Apache Flink
In a policy, Action indicates the operation that needs to be performed, Resource indicates the object on which the operation is performed, and Effect specifies whether to allow or deny the operation on the object. For more information about the syntax and structure of RAM policies, see Policy structure and syntax. You must replace the following parameters in a policy with the actual values:
{#regionId}: the ID of the region in which the Realtime Compute for Apache Flink workspace that you want to manage resides.
{#accountId}: the ID of the Alibaba Cloud account.
{#instanceId}: the ID of the Realtime Compute for Apache Flink workspace that you want to manage.
{#namespace}: the name of the namespace.
Policies related to Realtime Compute for Apache Flink workspaces
Permission
Policy document
Purchase a Realtime Compute for Apache Flink workspace
{ "Version": "1", "Statement": [ { "Action": "stream:CreateVvpInstance", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/*", "Effect": "Allow" } ] }View information about a workspace
{ "Version": "1", "Statement": [ { "Action": "stream:DescribeVvpInstances", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/*", "Effect": "Allow" } ] }Release a pay-as-you-go workspace
{ "Version": "1", "Statement": [ { "Action": "stream:DeleteVvpInstance", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId}", "Effect": "Allow" } ] }Renew a subscription workspace
{ "Version": "1", "Statement": [ { "Action": "stream:RenewVvpInstance", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#InstanceId}", "Effect": "Allow" } ] }Scale a subscription workspace
{ "Version": "1", "Statement": [ { "Action": "stream:ModifyVvpPrepayInstanceSpec", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId}", "Effect": "Allow" } ] }Change the maximum quota of a pay-as-you-go workspace
{ "Version": "1", "Statement": [ { "Action": "stream:ModifyVvpInstanceSpec", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId}", "Effect": "Allow" } ] }Change the billing method of a workspace
{ "Version": "1", "Statement": [ { "Action": "stream:ConvertVvpInstance", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#InstanceId}", "Effect": "Allow" } ] }Query the price for creating a workspace
{ "Version": "1", "Statement": [ { "Action": "stream:QueryCreateVvpInstance", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/*", "Effect": "Allow" } ] }Query the price for renewing a workspace
{ "Version": "1", "Statement": [ { "Action": "stream:QueryRenewVvpInstance", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#InstanceId}", "Effect": "Allow" } ] }Query the price for scaling a workspace
{ "Version": "1", "Statement": [ { "Action": "stream:QueryModifyVvpPrepayInstanceSpec", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#InstanceId}", "Effect": "Allow" } ] }Query the price for switching from the pay-as-you-go billing method to the subscription billing method
{ "Version": "1", "Statement": [ { "Action": "stream:QueryConvertVvpInstance", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#InstanceId}", "Effect": "Allow" } ] }Policies related to Realtime Compute for Apache Flink namespaces
ImportantBefore you configure namespace permissions, you must configure the DescribeVvpInstances permission to view existing workspaces. Otherwise, an error is returned.
Permission
Policy document
Create a namespace
{ "Version": "1", "Statement": [ { "Action": "stream:CreateVvpNamespace", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId}/vvpnamespace/*", "Effect": "Allow" } ] }Delete a namespace
{ "Version": "1", "Statement": [ { "Action": "stream:DeleteVvpNamespace", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId}/vvpnamespace/{#namespace}", "Effect": "Allow" } ] }Change resources for a subscription namespace
{ "Version": "1", "Statement": [ { "Action": "stream:ModifyVvpPrepayNamespaceSpec", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId}/vvpnamespace/{#namespace}", "Effect": "Allow" } ] }Change resources for a pay-as-you-go namespace
{ "Version": "1", "Statement": [ { "Action": "stream:ModifyVvpNamespaceSpec", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId}/vvpnamespace/{#namespace}", "Effect": "Allow" } ] }View the namespace list
{ "Version": "1", "Statement": [ { "Action": "stream:DescribeVvpNamespaces", "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId}/vvpnamespace/*", "Effect": "Allow" } ] }NoteAfter you configure the policy, you can click the
 icon to the left of the ID of a specific workspace to view the list of namespaces that are created in the workspace. If you want to log on to the development console of a specific Realtime Compute for Apache Flink namespace, you must have the permission to develop drafts in the namespace. For more information, see Grant namespace permissions.
icon to the left of the ID of a specific workspace to view the list of namespaces that are created in the workspace. If you want to log on to the development console of a specific Realtime Compute for Apache Flink namespace, you must have the permission to develop drafts in the namespace. For more information, see Grant namespace permissions.
Permission operations on related services
ECS-related operations
OSS-related operations
ARMS-related operations
VPC-related operations
RAM-related operations
DLF-related operations
References
For more information about how to use different identities such as Alibaba Cloud accounts, RAM roles, and RAM users to access the Realtime Compute for Apache Flink console, see Supported logon methods.
If you want multiple users to use a Realtime Compute for Apache Flink namespace to perform operations such as draft development and deployment O&M in the development console of Realtime Compute for Apache Flink, you must grant permissions on the namespace to the users. For more information, see Grant namespace permissions.
For more information about the differences between the permissions granted to a RAM user and the permissions on namespaces, see Permission management.
For more information about the API operations related to RAM permission management, see Permission management.
Why am I unable to go to the RAM console after I click Authorize in RAM?