To access Realtime Compute for Apache Flink's Management Console via a Resource Access Management (RAM) identity and perform operations such as viewing, purchasing, or deleting workspaces, you must have the necessary permissions. To ensure security, all access principals must be granted the corresponding permission policies in the RAM console by the Alibaba Cloud account administrator who purchased the Flink workspace. This topic describes the supported permission policies and the procedure for configuring authorization.
Authorization scenarios
Scenario | Description | Cause and solution |
Unable to access the Management Console | You cannot see any workspace information, and the following error is displayed.
| This indicates you do not have permission to access the Management Console. Contact the Alibaba Cloud account administrator who purchased the workspace to grant you at least read-only access to Realtime Compute for Apache Flink ( |
Unable to perform a specific operation |
| This indicates that the current account does not have permission to perform this operation. To proceed, contact the Alibaba Cloud account administrator who purchased the workspace to adjust the custom permission policy based on your specific requirements and complete the corresponding authorization by following the authorization procedure. For example, as shown in the image on the left, your account requires permissions related to resource scaling for subscription workspaces. |
Policy types
A permission policy is a set of permissions defined by a syntax structure that precisely describes the authorized resource set, operation set, and authorization conditions. The RAM console supports the following two types of permission policies:
System policy: Ready-to-use permission sets created, updated, and managed by Alibaba Cloud. Realtime Compute for Apache Flink-related system policies:
Permission set
Policy
Description
Full access to Realtime Compute for Apache Flink
AliyunStreamFullAccessIncludes all permissions available in Custom policies.
Read-only access to Realtime Compute for Apache Flink
AliyunStreamReadOnlyAccessIncludes
HasStreamDefaultRoleand all permissions that start withDescribe,Query,Check,List,Get, andSearchin Permissions on workspace and namespace management.Permissions to view and pay for orders in Expenses and Costs
AliyunBSSOrderAccessAllows you to view and pay for orders in the Expenses and Costs console.
Permissions to unsubscribe in Expenses and Costs
AliyunBSSRefundAccessAllows you to unsubscribe from orders in the Expenses and Costs console.
Custom policy: Permission sets defined and managed by users. You manage the policy versions yourself. For more information about the custom policies supported by Realtime Compute for Apache Flink and how to create them, see Permissions on workspace and namespace management and (Optional) Step 1: Create a custom policy.
Prerequisites
You have read and understood the authorization notes.
Authorization procedure
(Optional) Step 1: Create a custom policy
A custom policy is recommended to include read-only access to Realtime Compute for Apache Flink and more granular permissions, including custom permission policies and permission operations on related products. The following is an example of a custom policy for read-only access to Realtime Compute for Apache Flink, which is equivalent to the AliyunStreamReadOnlyAccess system policy.
{
"Version": "1",
"Statement": [
{
"Action": [
"stream:Describe*",
"stream:Query*",
"stream:Check*",
"stream:List*",
"stream:Get*",
"stream:Search*",
"stream:HasStreamDefaultRole"
],
"Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId}/vvpnamespace/{#namespace}",
"Effect": "Allow"
}
]
}Steps and examples for creating custom permission policies: Create a custom permission policy and Custom permission policy examples.
In a permission policy,
Actionindicates the operation to be performed,Resourceindicates the object on which the operation is performed, andEffectindicates whether the authorization allows or denies the action. For more information, see Policy elements and Policy structure and syntax. Replace the following parameters in the policy code with your actual values:{#regionId}: The region where your workspace is located.
{#accountId}: Your Alibaba Cloud account UID.
{#instanceId}: The ID of your workspace.
{#namespace}: Your namespace name.
Step 2: Attach the target policy to members
Attaching a permission policy to a RAM identity grants them the access permissions specified in that policy. This section describes how to grant a policy to a RAM user. The procedure for granting permissions to a RAM role is similar. For more information, see Grant permissions to a RAM role.
Log on to the RAM console as a RAM administrator.
In the left-side navigation pane, choose .
On the Users page, find the required RAM user, and click Add Permissions in the Actions column.
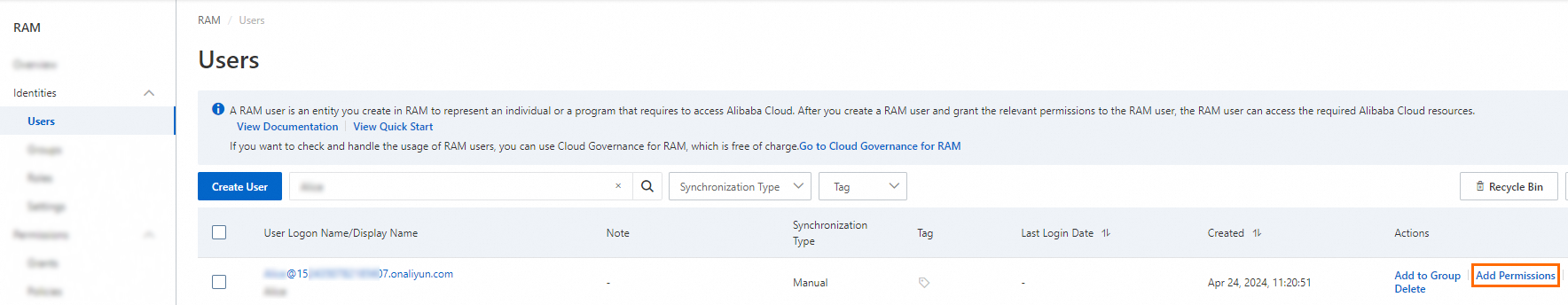
You can also select multiple RAM users and click Add Permissions in the lower part of the page to grant permissions to the RAM users at a time.
In the Grant Permission panel, add permission policies for the RAM user.
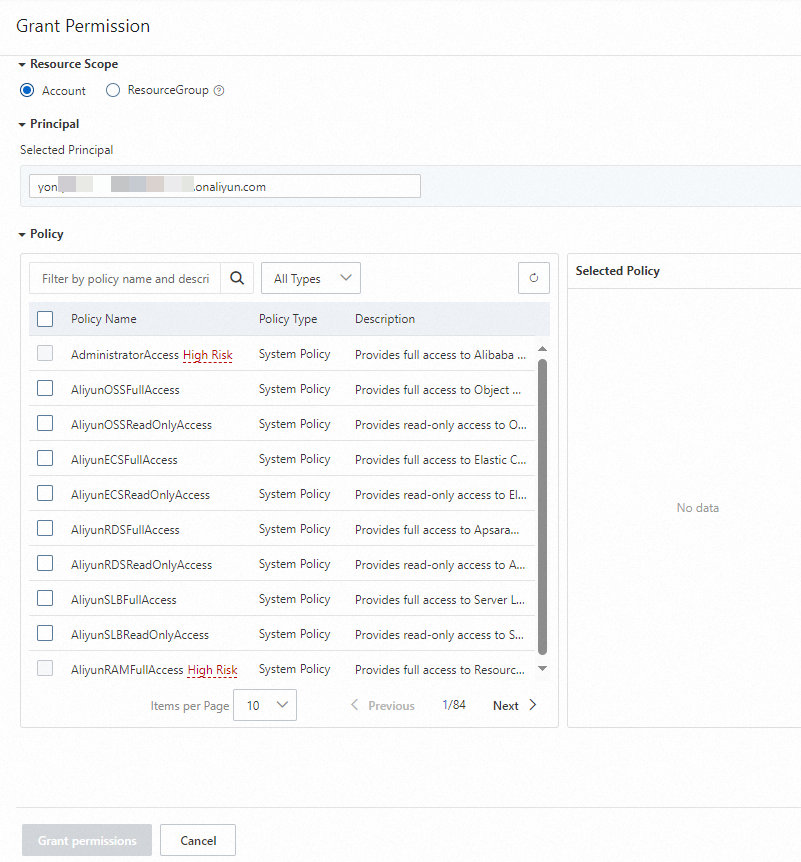
Parameter
Description
Resource Scope
Select the required resource scope:
Account: The permissions are granted to the current Alibaba Cloud account.
ResourceGroup: The permissions are valid for a specific resource group.
Principal
The principal is the RAM user to which you want to grant permissions. Defaults to the RAM user selected in step 3. You can also specify another RAM user.
Policy
Select a system or custom policy.
Click Grant permissions.
Click Close.
Step 3: Log on to Management Console after authorization
After the authorization is complete, the RAM identity can log on to or refresh the current Management Console page to perform operations.
Logon type | Logon method | How to log on |
RAM user | RAM user login | Log on to the Alibaba Cloud Management Console as a RAM user |
RAM role | RAM user assumes a role within the same Alibaba Cloud account to log on | |
RAM user assumes a role of another Alibaba Cloud account to log on | Use a RAM role to grant permissions across Alibaba Cloud accounts | |
Resource directory member | RAM user of the management account assumes a member RAM role to log on | Use a RAM role to log on to the Alibaba Cloud Management Console |
Log on via a member's RAM user | Log on to the Alibaba Cloud Management Console as a RAM user | |
Log on via a cloud account (root user) (not recommended) | Log on to the Alibaba Cloud Management Console as the root user of a member | |
CloudSSO user logs on via a RAM role | ||
CloudSSO user logs on via a RAM user |
Custom policy examples
Example 1: A RAM user creates a subscription workspace
Example 2: A RAM user creates a subscription workspace (with existing system policy)
Example 3: A RAM user releases a subscription workspace
RAM user releases a pay-as-you-go Flink workspace
RAM user scales resources for a subscription namespace
Custom policies
Permissions on workspace and namespace management
Before configuring namespace permissions, first grant permission to view existing workspaces (DescribeVvpInstances) to avoid permission errors.
Workspace management
{
"Version": "1",
"Statement": [
{
"Action": [
"stream:CreateVvpInstance",
"stream:DescribeVvpInstances",
"stream:DeleteVvpInstance",
"stream:RenewVvpInstance",
"stream:ModifyVvpPrepayInstanceSpec",
"stream:ModifyVvpInstanceSpec",
"stream:ConvertVvpInstance",
"stream:QueryCreateVvpInstance",
"stream:QueryRenewVvpInstance",
"stream:QueryModifyVvpPrepayInstanceSpec",
"stream:QueryConvertVvpInstance"
],
"Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#InstanceId}",
"Effect": "Allow"
}
]
}action | Description |
| Create workspaces. |
| View workspaces. |
| Release a workspace. |
| Renew a subscription workspace. |
| Scale a subscription workspace. |
| Adjust the Compute Unit (CU) quota of a pay-as-you-go workspace. |
| Change the billing method of a workspace. |
| Query the price for creating a workspace. |
| Query the price for renewing a workspace. |
| Query the price for scaling a workspace. |
| Query the price for converting from pay-as-you-go to subscription. |
For purchasing Realtime Compute for Apache Flink and viewing workspaces, change Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId} to "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/*".
Namespace management
{
"Version": "1",
"Statement": [
{
"Action": [
"stream:CreateVvpNamespace",
"stream:DeleteVvpNamespace",
"stream:ModifyVvpPrepayNamespaceSpec",
"stream:ModifyVvpNamespaceSpec",
"stream:DescribeVvpNamespaces"
],
"Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId}/vvpnamespace/{#namespace}",
"Effect": "Allow"
}
]
}action | Description |
| Create a namespace. |
| Delete a namespace. |
| Change resources for a subscription namespace. |
| Change resources for a pay-as-you-go namespace. |
| View namespaces under a workspace. After configuring this policy, you can click the |
To create and view a namespace, you can use "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId}/vvpnamespace/*",.


 icon to the left of the target workspace ID to view the list of namespaces under that workspace. To access the Development Console of a specific namespace, get relevant Development Console permissions for the namespace. For more information, see
icon to the left of the target workspace ID to view the list of namespaces under that workspace. To access the Development Console of a specific namespace, get relevant Development Console permissions for the namespace. For more information, see