To allow multiple users to collaborate in a namespace in the development console of Realtime Compute for Apache Flink, such as performing SQL development and O&M, you can add members to the namespace and assign roles that have predefined permissions to the members. You can also create custom roles to grant permissions based on your business requirements. This improves the flexibility of permission management and ensures security. This topic describes how to create custom roles, add members, and assign roles to members.
Common issues and solutions
You fail to access a namespace after you log on to the development console of Realtime Compute for Apache Flink. A message appears to indicate that no namespace is available within your account.
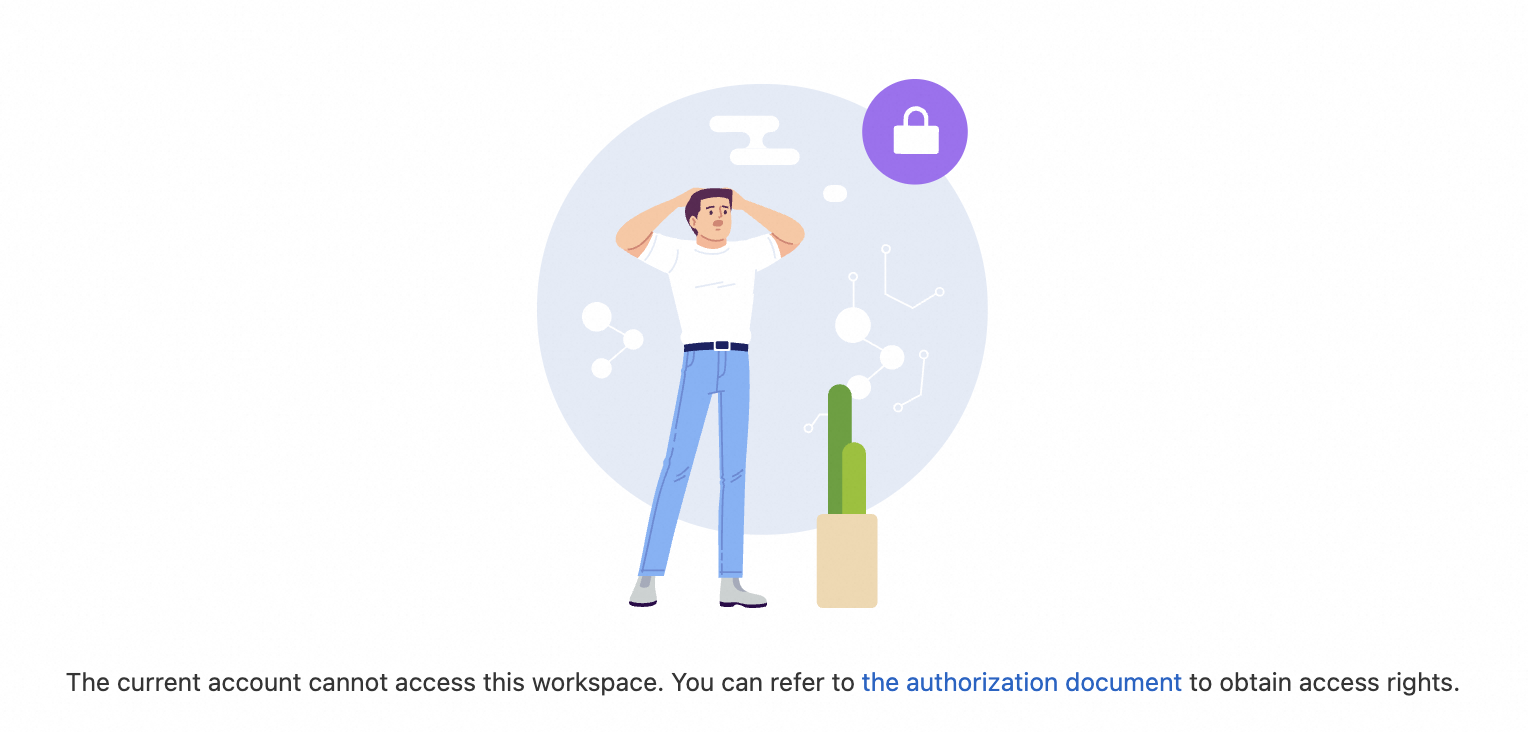
This issue indicates that you do not have the permissions to access the current namespace. To obtain the permissions to access the namespace, contact the namespace owner or a member who has the permissions to manage members. For more information about how to grant the permissions, see the Manage members section of this topic. After you obtain the permissions, reopen or refresh the page to access the namespace.
You cannot use specific features or you cannot perform specific operations in a namespace. For example, you cannot deploy, start, or stop a job.
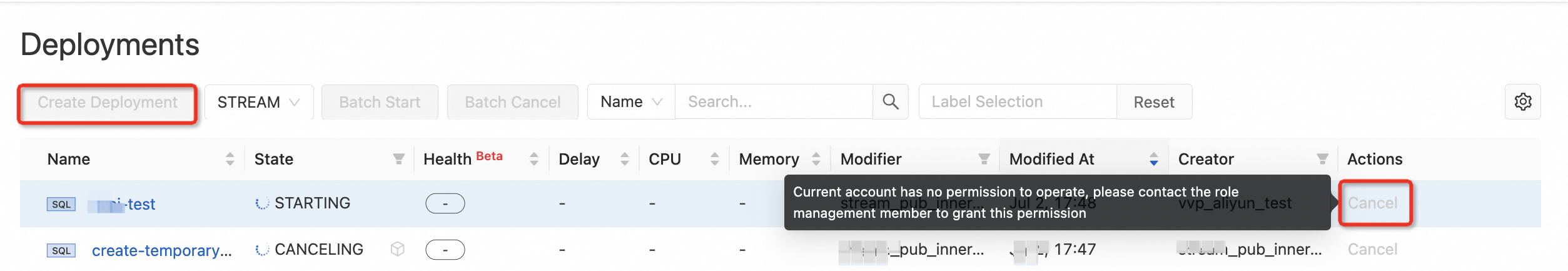
This issue indicates that you do not have the permissions to perform the corresponding operations. To obtain the permissions, click the Role Management tab on the Permissions page to view the permissions of different roles and the members to whom the roles are assigned. Then, contact the namespace owner or a member who has the permissions to manage roles. For more information about roles and role permissions, see the Manage roles section of this topic.
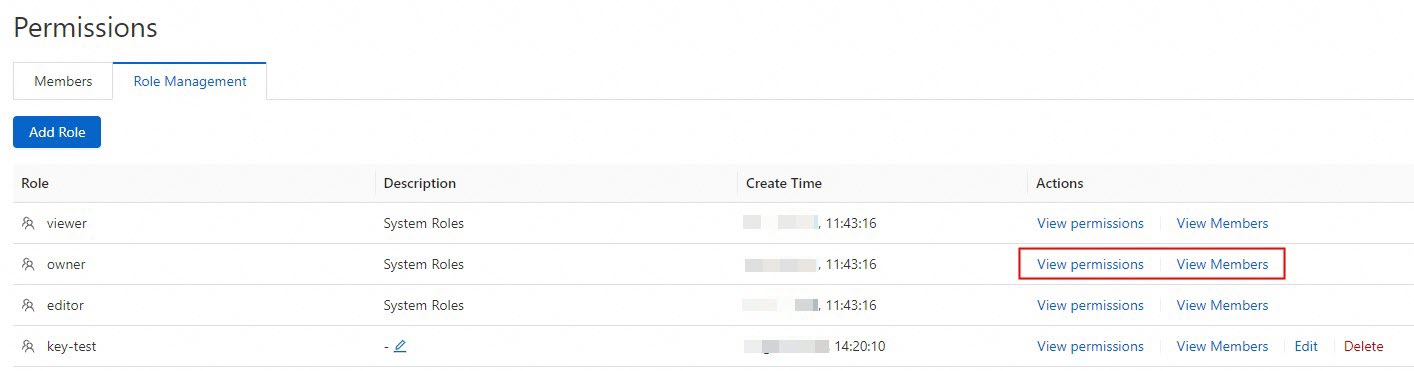
Manage members
Add a member
Log on to the development console of Realtime Compute for Apache Flink as a member who has the permissions to add members, such as a namespace owner.
In the top navigation bar, select the namespace that you want to manage from the drop-down list.
In the left-side navigation pane, choose . On the Permissions page, click the Members tab.
On the Members tab, click Add Member. In the Add Member dialog box, add a member and select a role for the member by configuring the following parameters.
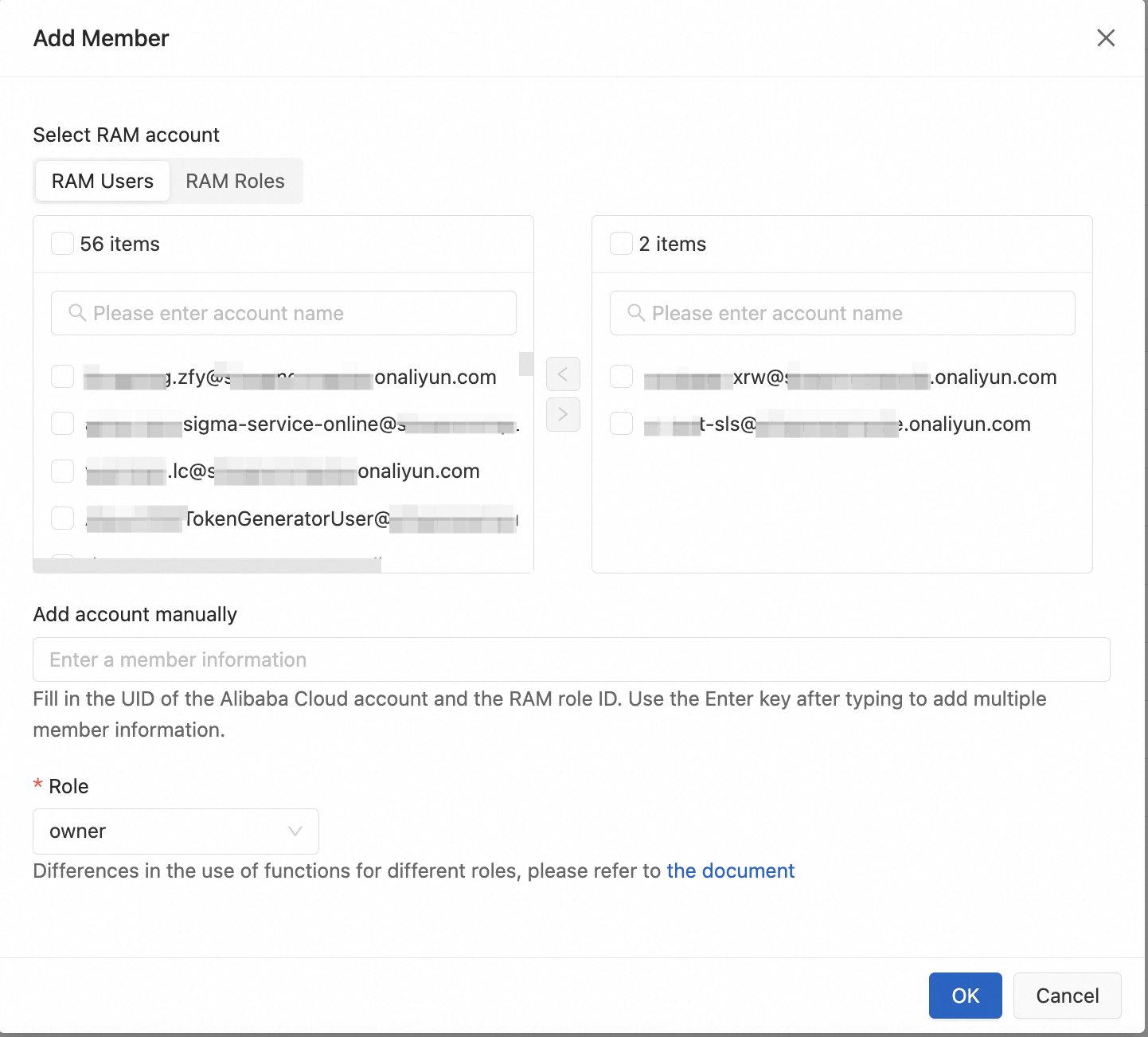
Select RAM account: Select an existing Resource Access Management (RAM) user or RAM role in the current Alibaba Cloud account. You can select multiple RAM users and RAM roles.
Add account manually: Enter the ID of another Alibaba Cloud account, a RAM user, or a RAM role that you want to add.
NoteFor more information about how to view the ID of an Alibaba Cloud account, a RAM user, or a RAM role, see the View the ID of an Alibaba Cloud account, a RAM user, or a RAM role section of this topic.
Role: Select a predefined or custom role from the drop-down list. To view the permissions of a role, find the role that you want to view on the Role Management tab and click View permissions in the Actions column.
Click OK.
The added member can log on to the development console of Realtime Compute for Apache Flink to access and use the namespace.
NoteIf the member has already logged on, the member can refresh the page to access the namespace.
Modify and delete a member
Modify a member
Make sure that you have the permissions to modify members. On the Members tab, find the member who you want to modify and click Edit in the Actions column. You can assign another predefined or custom role to the member. For more information about how to view the permissions of an existing custom role, see the View permissions of and members associated with a role section of this topic.
Delete a member
Make sure that you have the permissions to delete members. On the Members tab, find the member who you want to delete and click Delete in the Actions column. After the member is deleted, the member immediately has no permission to access the namespace.
Manage roles
Roles and role permissions
Realtime Compute for Apache Flink supports the roles of the following types:
Predefined roles: owner, editor, and viewer. Predefined roles cannot be deleted and their permissions cannot be modified.
Custom roles: Custom roles can be created, modified, and deleted by members who are assigned the owner role or a role that has the related permissions. A custom role must have a larger scope of permissions than the viewer role. You can create up to 10 custom roles in a namespace.
Only members who are assigned the editor or owner role can be granted permissions that are not included in the following table, such as the permissions to manage metadata or manage user-defined functions (UDFs) in SQL.
The following table describes the permissions of different roles.
First-level permission | Second-level permission | owner | editor | viewer | Associated permissions for custom roles |
Use the extract, transform, and load (ETL) feature for SQL development | View SQL drafts | ✓ | ✓ | ✓ | N/A |
Create and modify SQL drafts | ✓ | ✓ | By default, the permissions to view SQL drafts are included. | ||
Debug SQL drafts | ✓ | ✓ | By default, the permissions to create and modify SQL drafts and view session clusters are included. | ||
Validate SQL drafts | ✓ | ✓ | By default, the permissions to debug SQL drafts are included. | ||
Delete SQL drafts | ✓ | ✓ | By default, the permissions to view SQL drafts are included. | ||
Deploy SQL drafts | ✓ | ✓ | By default, the permissions to validate SQL drafts are included. | ||
View UDF JAR files | ✓ | ✓ | ✓ | N/A | |
Manage deployments | View deployments | ✓ | ✓ | ✓ | N/A |
Create JAR and Python deployments | ✓ | ✓ | By default, the permissions to view deployments and artifacts are included. | ||
Update deployment configurations | ✓ | ✓ | By default, the permissions to view deployments are included. | ||
Delete deployments | ✓ | ✓ | By default, the permissions to view deployments are included. | ||
Start/Stop jobs | ✓ | ✓ | By default, the permissions to view deployments are included. | ||
Manage artifacts | View artifacts | ✓ | ✓ | ✓ | By default, the permissions to view deployments are included. |
Upload artifacts | ✓ | ✓ | By default, the permissions to view artifacts are included. | ||
Delete artifacts | ✓ | ✓ | By default, the permissions to view artifacts are included. | ||
Download artifacts | ✓ | ✓ | By default, the permissions to view artifacts are included. | ||
Manage session clusters | Delete session clusters | ✓ | ✓ | By default, the permissions to view session clusters are included. | |
View session clusters | ✓ | ✓ | ✓ | N/A | |
Create session clusters | ✓ | ✓ | By default, the permissions to view session clusters are included. | ||
Update session cluster configurations | ✓ | ✓ | By default, the permissions to view session clusters are included. | ||
Start/Stop session clusters | ✓ | ✓ | By default, the permissions to view session clusters are included. | ||
Perform security-related operations | View members | ✓ | ✓ | ✓ | N/A |
Create members | ✓ | By default, the permissions to view members are included. | |||
Modify members | ✓ | By default, the permissions to view members are included. | |||
Delete members | ✓ | By default, the permissions to view members are included. | |||
View roles | ✓ | ✓ | ✓ | N/A | |
Create roles | ✓ | By default, the permissions to view roles are included. | |||
Modify roles | ✓ | By default, the permissions to view roles are included. | |||
Delete roles | ✓ | By default, the permissions to view roles are included. | |||
View variables | ✓ | ✓ | ✓ | N/A | |
Create variables | ✓ | ✓ | By default, the permissions to view variables are included. | ||
Delete variables | ✓ | ✓ | By default, the permissions to view variables are included. | ||
Manage configurations | View job templates | ✓ | ✓ | ✓ | N/A |
Modify job templates | ✓ | ✓ | By default, the permissions to view job templates are included. |
Create a custom role
Log on to the development console of Realtime Compute for Apache Flink as a member who is assigned the owner role or a role that has the permissions to manage roles.
In the top navigation bar, select the namespace that you want to manage from the drop-down list.

In the left-side navigation pane, choose . On the Permissions page, click the Role Management tab.
On the Role Management tab, click Add Role. In the Add a custom role panel, configure the parameters. The following table describes the parameters.
Parameter
Description
Role Name
The name of the custom role. The name can be up to 64 characters in length and can contain digits, letters, and hyphens (-). The name must start with a letter.
Role Notes
The description or supplementary information of the role. For example, you can specify the purpose of the role or the scope of the permissions granted to the role. The description can be up to 256 characters.
Role Permissions
Add permissions based on the viewer or editor role. A custom role must have a larger scope of permissions than the viewer role.
When you add a permission, the associated permissions are automatically selected to ensure the integrity of access control. For more information about the associated permissions of a specific permission, see the "Roles and role permissions" section of this topic.
Click OK. The added role appears in the list.
View, modify, and delete a role
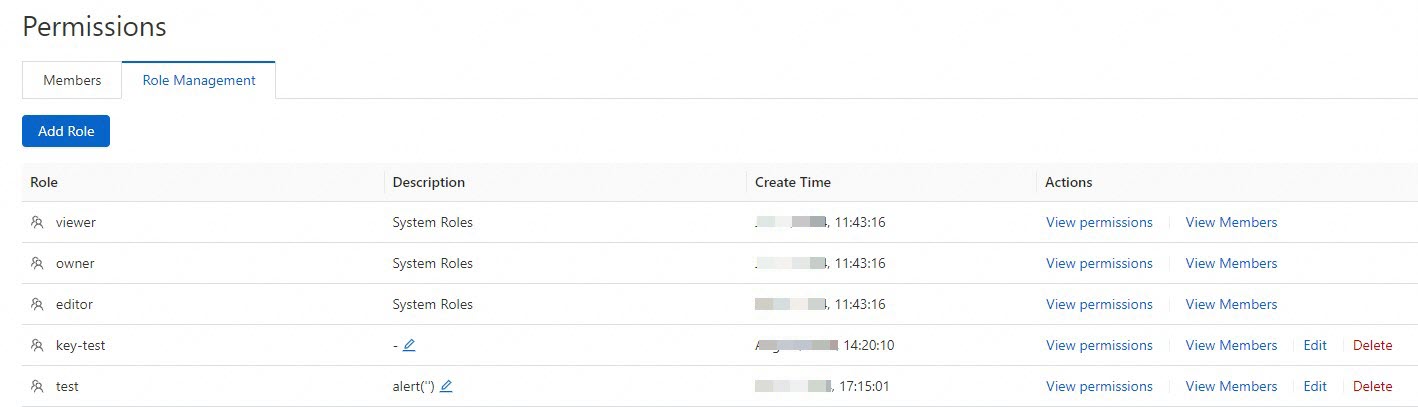
View permissions of and members associated with a role
On the Role Management tab, find the role that you want to manage and click View permissions in the Actions column to view the permissions of the role. Click View Members in the Actions column to view all members to which the role is assigned.
Modify role permissions
Predefined roles: You cannot modify the permissions of a predefined role.
Custom roles: If you have the permissions to modify a role, click Edit in the Actions column to add or remove permissions based on your business requirements.
Delete a role
Predefined roles: You cannot delete a predefined role.
Custom roles: Before you delete a custom role, find the associated members and assign different roles to the members or remove the members from the namespace. This operation requires the permissions to manage members and reduces security risks. For information about how to manage members, see the Modify and delete a member section of this topic. After you confirm that the role is not assigned to any members and you have the permissions to delete roles, click Delete in the Actions column to delete the role.
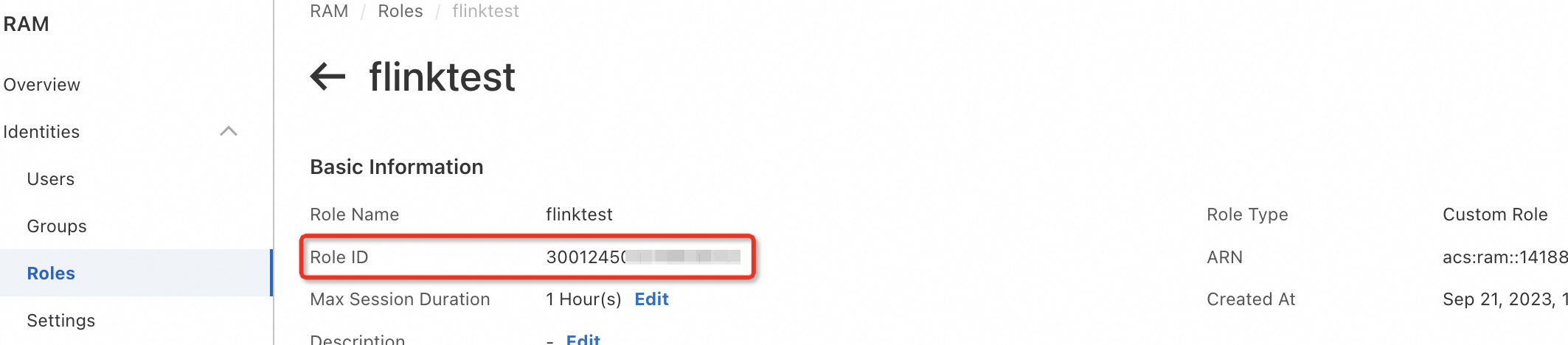
View the ID of an Alibaba Cloud account, a RAM user, or a RAM role
View the ID of an Alibaba Cloud account: Log on to the management console of Realtime Compute for Apache Flink and click the profile picture in the upper-right corner to go to Account Center. You can view the account ID on the Basic Information page.
View the ID of a RAM user: For more information, see View the information about a RAM user.
View the ID of a RAM role: For more information, see View the information about a RAM role.
References
To use a RAM user or a RAM role to access the management console of Realtime Compute for Apache Flink and purchase, view, or delete a workspace, you must complete grant permissions to RAM users. For more information, see Grant permissions to a RAM user.
For more information about the differences between the namespace permissions described in this topic and RAM permissions, see Permission management.
For more information about how to use different identities, such as Alibaba Cloud accounts, RAM roles, or RAM users, to log on to the management console of Realtime Compute for Apache Flink, see Supported logon methods.