Alibaba Cloud can synchronize Okta users to Resource Access Management (RAM) based on System for Cross-domain Identity Management 2.0 (SCIM 2.0) and security authorization of Open Authorization (OAuth) applications.
Prerequisites
A RAM user who has administrative rights or a RAM user who has the OAuth management permissions is used to perform all operations in the RAM console.
An Okta administrator (super administrator) is used to perform all operations on the Okta portal.
Background information
Create a user: After Okta assigns a user to an application, a RAM user with the same username is automatically created in the RAM console. The domain name suffix of the Okta username is automatically replaced with the domain name of the RAM user.
Change user attributes: If you select Push Profile Updates in Okta, the user attributes of the RAM user with the same username are automatically changed in the RAM console when you change the user attributes of the Okta user. Only the changes in the UserName and DisplayName parameters can be synchronized to the RAM console.
When you delete or unassign a user in Okta, the state of the user changes to
active=falsein Okta. However, the state change cannot be synchronized to the RAM console because a RAM user does not support the enabled or disabled state.You cannot synchronize user groups in Okta to the RAM console.
Step 1: Create an OAuth application and grant permissions on the OAuth application in the RAM console
Create an OAuth application.
Log on to the RAM console.
In the left-side navigation pane, choose .
On the Enterprise Application tab, click Create Application.
On the Create Application page, configure the parameters.
Configure Application Name and Display Name.
Set Application Type to Native Application.
Configure Access Token Validity.
Configure Refresh Token Validity.
Click Create Application.
Grant permissions on the OAuth application.
On the Enterprise Application tab, find the application that you want to manage.
On the OAuth Scope tab, click Add OAuth Scope.
In the Add OAuth Scope panel, select /acs/scim.
Click OK.
Create an application secret for the OAuth application.
Click the Application Secret tab, and then click Create Secret.
In the Create Secret dialog box, view and copy the created application secret and click Close.
ImportantThe application secret (AppSecretValue) is displayed only during creation and cannot be queried. Save the secret at the earliest opportunity.
Step 2: Create an application in Okta
Log on to the Okta portal.
In the upper-right corner of the Okta portal, click the account name and select Your Org from the drop-down list.
In the left-side navigation pane, choose .
On the Applications page, click Create App Integration.
In the Create a new app integration dialog box, select SAML 2.0 and click Next.
In the General Settings step of the page that appears, enter AliyunSSODemo in the App name field and click Next.
In the Configure SAML step, configure the parameters and click Next.

In the Single sign on URL field, enter the value of
Locationthat you obtained in Step 1: Download the Security Assertion Markup Language (SAML) SP metadata file of Alibaba Cloud.In the Audience URI field, enter the value of
entityIDthat you obtained in Step 1: Download the Security Assertion Markup Language (SAML) SP metadata file of Alibaba Cloud.In the Default RelayState field, enter a URL. Then, the system redirects you to the URL after logon.
NoteFor security purposes, you must enter a URL that points to an Alibaba website in the Default RelayState field. For example, you can enter a URL that contains the following domain names: *.aliyun.com, *.hichina.com, *.yunos.com, *.taobao.com, *.tmall.com, *.alibabacloud.com, or *.alipay.com. If you leave this parameter empty, you are redirected to the homepage of the Alibaba Cloud Management Console.
Select Persistent for Name ID format.
Select Email for Application username.
On the Feedback page, select a type for the application and click Finish.
Step 3: Configure SCIM synchronization in Okta
Enable SCIM synchronization.
In the application created in Step 2: Create an application in Okta, click the General tab.
In the App Settings section, click Edit.
Select Enable SCIM provisioning and click Save to enable SCIM synchronization.
Configure SCIM parameters.
Click the Provisioning tab.
In the left-side navigation pane, click Integration.
In the SCIM Connection section, click Edit and configure the following parameters.
SCIM connector base URL: Enter
https://scim.aliyun.com.Unique identifier field for users: Enter
userName.Supported provisioning actions: Select Import New Users and Profile Updates and Push New Users.
NotePush Profile Updates is optional and specifies whether to enable automatic user attribute update.
Authentication Mode: Select OAuth 2.
Configure OAuth 2 parameters.
Access token endpoint URI: Enter
https://oauth.alibabacloud.com/v1/token.Authorization endpoint URI:
https://signin.alibabacloud.com/oauth2/v1/auth.Client ID: Enter the ID of the OAuth application that you created in Step 1: Create an OAuth application and grant permissions on the OAuth application in the RAM console.
Client Secret: Enter the secret that you created in Step 1: Create an OAuth application and grant permissions on the OAuth application in the RAM console.
Click Save.
Obtain the callback URL.
On the Provisioning tab, click Integration in the left-side navigation pane.
In the lower part of the page, click Authenticate with xxx.
On the page that appears, copy the callback URL (redirect url).
Log on to the RAM console. In the OAuth application that you created in Step 1: Create an OAuth application and grant permissions on the OAuth application in the RAM console, enter the callback URL.
Return to the current page in the Okta portal, click Authenticate with xxx, and then log on to the Alibaba Cloud Management Console to complete the verification.
Configure user synchronization parameters.
On the Provisioning tab, click To App in the left-side navigation pane.
In the Provisioning to App section, click Edit.
In the Create User section, select Enable and click Save.
NoteIf you enabled Push Profile Updates in the SCIM Connection section, you must set Push Profile Updates in this section to Enable.
In the <App Name> Attribute Mappings section, configure attribute mappings to delete unnecessary attributes and retain only the attributes shown in the following figure.
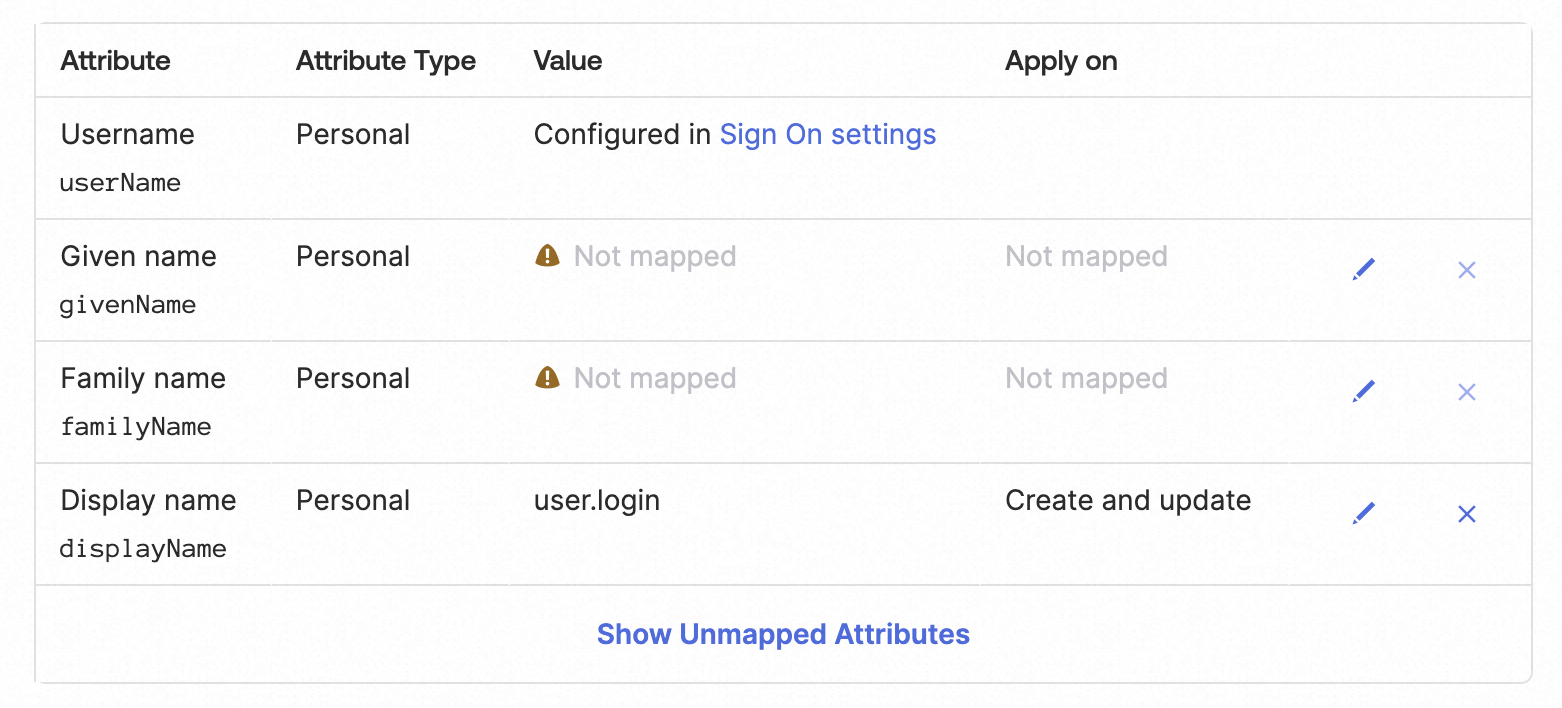
On the Sign on tab, click Edit.
Set Application username format to Okta username prefix and click Save.
Assign users to the application.
On the Assignments tab, click Assign.
Click Assign to People to assign users to the application.
If an issue occurs during the synchronization, you can click View Logs to view the logs and address the issue.
Verify the result
After you complete the preceding steps, Okta users are automatically synchronized to the RAM console. You can log on to the RAM console and view the synchronized users in the RAM user list. The Synchronization Type of the synchronized users is SCIM User Synchronization.