This topic describes how to use an over-privileged identity analyzer to detect over-privileged identities in your resource directory or in the current account.
Overview
What is an over-privileged identity analyzer?
An over-privileged identity analyzer helps detect over-privileged identities in your resource directory or in the current account. An over-privileged identity analyzer continuously monitors all Resource Access Management (RAM) identities in your resource directory or in the current account and generates findings for over-privileged identities. RAM identities are RAM users and RAM roles. The findings generated by the analyzer are classified into the following types: Super User, Super Role, Privileged User, Privileged Role, Inactive User, Inactive Role, Over-Privileged User, and Over-Privileged Role. Each finding contains information about the permissions that are granted to a RAM identity and the time when the permissions were last used by the RAM identity.
Super User and Super Role: RAM identities have full permissions to manage all resources in an account. For example, if the AdministratorAccess policy is attached to a RAM user or RAM role, the RAM user or RAM role has full permissions to manage all resources in an account.
Privileged User and Privileged Role: RAM identities have privileges to perform high-risk operations. RAM identities with such privileges can grant more permissions to themselves or other identities. For more information, see Privileges.
Inactive User and Inactive Role: RAM identities use no permissions to access resources within the period specified by the The period for unused accesses parameter.
Over-Privileged User and Over-Privileged Role: RAM identities have service-level and operation-level permissions that are not used within the period specified by the The period for unused accesses parameter.
Analyzer scope
An over-privileged identity analyzer checks the permission audit information about all RAM identities in your resource directory or in the current account and generates findings based on the information. The analyzer does not check service-linked roles. The permission audit feature allows you to check the permissions that are granted to a RAM identity and the time when the permissions were last used by the RAM identity. An over-privileged identity analyzer and the permission audit feature support the same policy types, cloud services, and audit granularities. For more information, see Overview.
Create an over-privileged identity analyzer
Log on to the RAM console as a RAM user who has administrative rights.
In the left-side navigation pane, choose .
On the Analyzers page, click Create Analyzer. On the Create Analyzer page, enter an analyzer name, set Analyzer Type to Over-Privileged, configure The period for unused accesses, and select an analyzer scope. Then, click Create Analyzer.
Unused Access Age is used to determine whether permissions are idle. Valid values: 1 to 180. Default value: 90. Unit: days. For example, if you set Unused Access Age to 90, the permissions that are not used for more than 90 days are considered idle.
NoteOnly the management account of a resource directory can set Analyzer Scope to Resource Directory.

After you create the analyzer, the analyzer checks the RAM identities and permissions. The system requires a specific period of time to generate findings.
View and handle the findings
View the findings
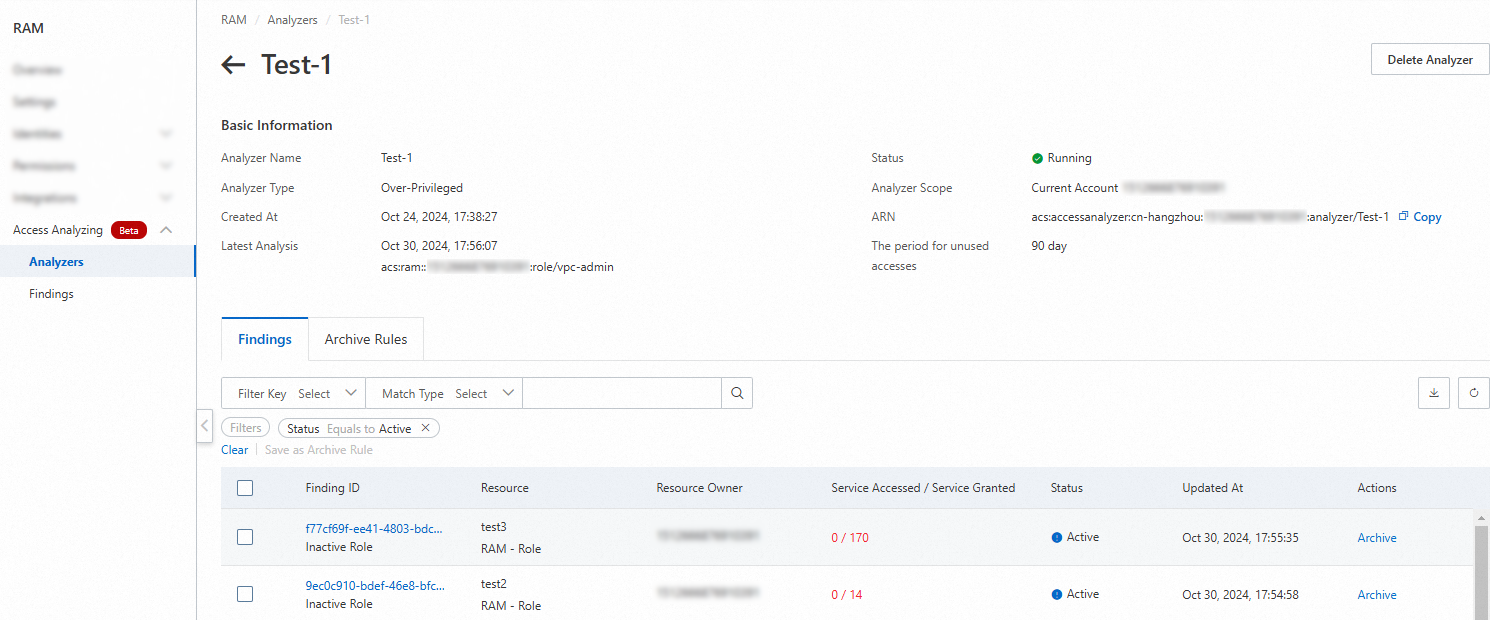
You can view the findings on the Analyzers or Findings page.
The following figure shows the Analyzers page.
The following figures show the Findings page in different layouts.
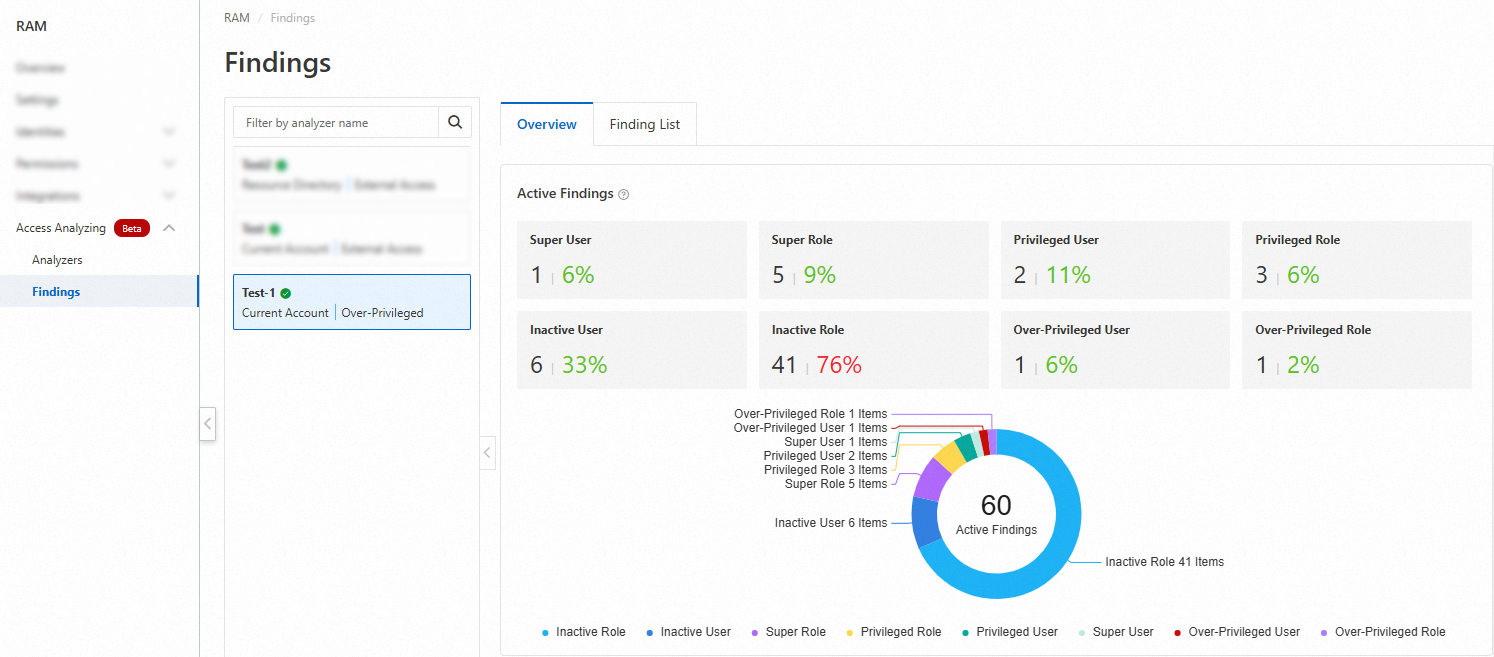
The following figures show the findings in graphs.
The following figure shows the findings for the current account.
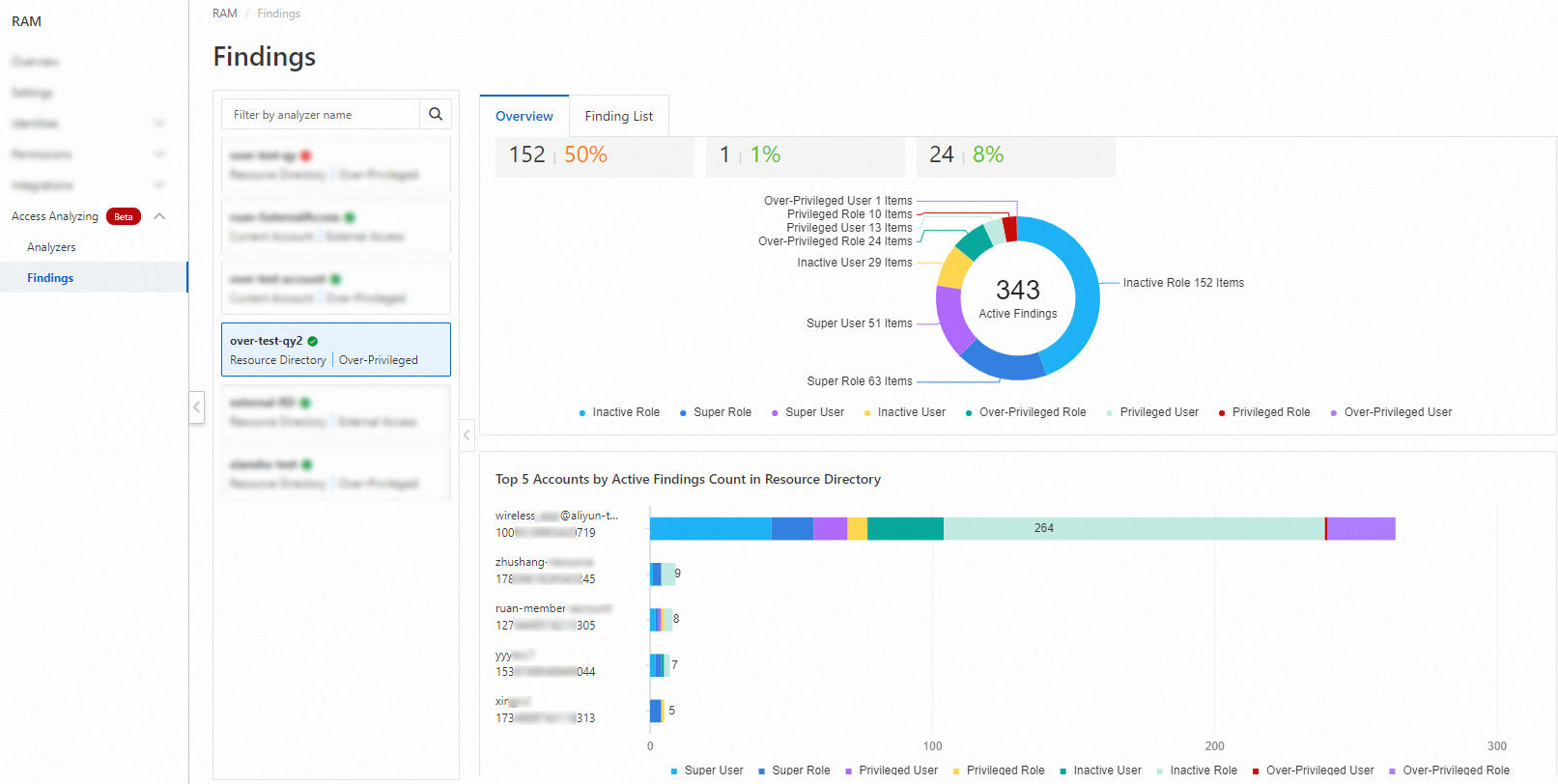
The following figure shows the findings for the resource directory. The top five members with the largest numbers of active findings in the resource directory are displayed.
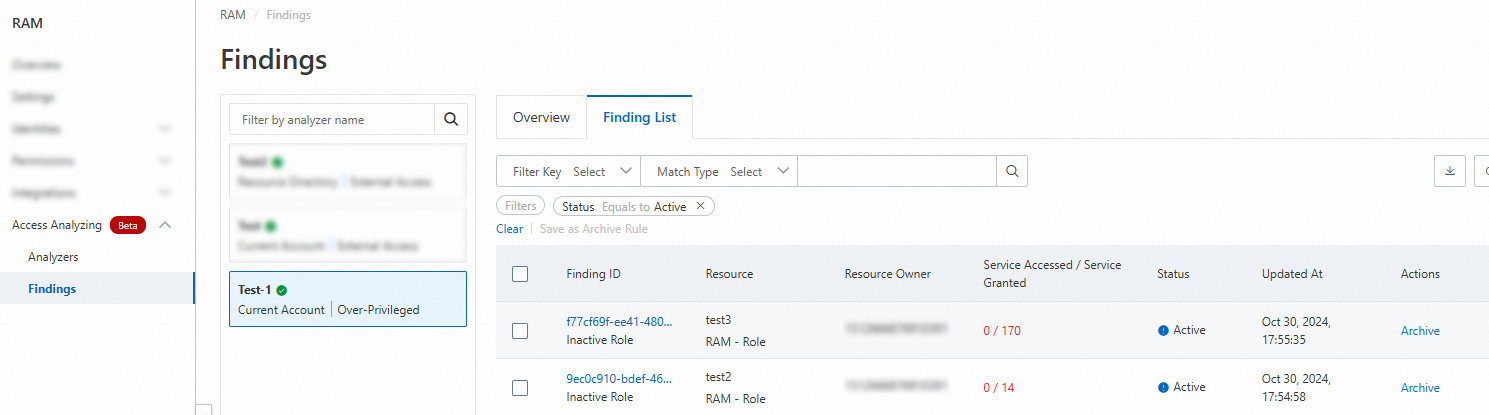
The following figure shows the findings in a list.
Filter the findings
You can search for specific findings based on filter conditions, such as Resource, Resource Type, Resource Owner, Status, and Finding Type.
The filter conditions in the console prevail.
For example, you can configure the following conditions to view the findings about RAM users.
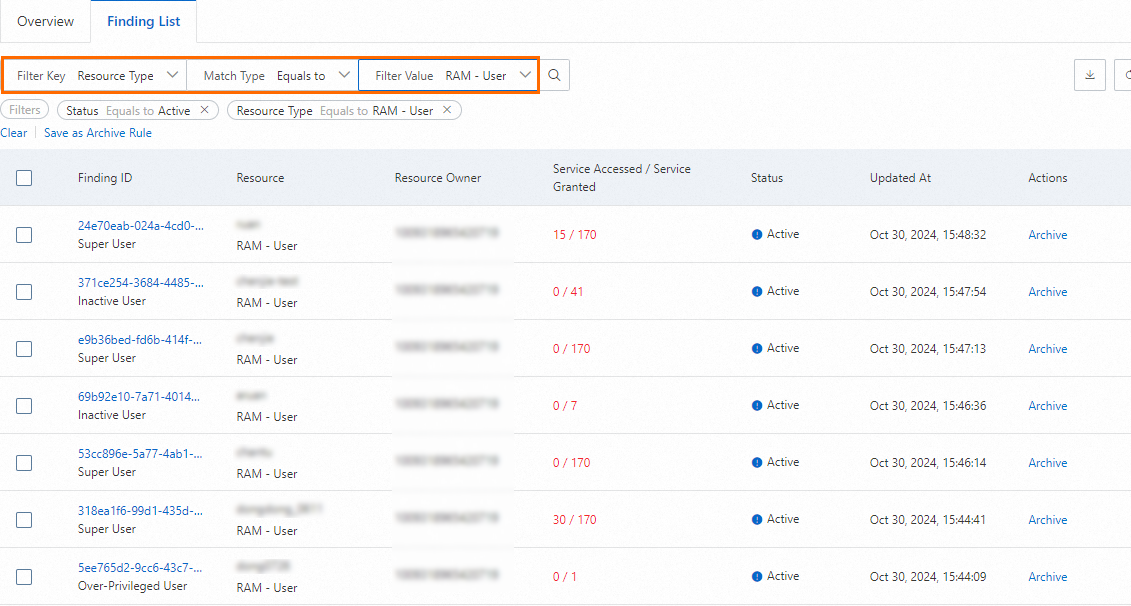
The types of the findings about RAM users may include Super User, Privileged User, Inactive User, and Over-Privileged User. You can further configure the finding type as the filter condition based on the findings. For example, you can set Finding Type to Over-Privileged User to search for the findings about over-privileged users.
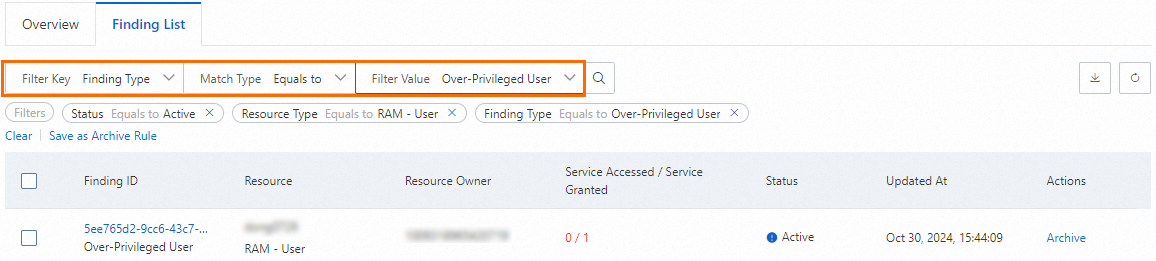
View the details of a finding
In the finding list, find the finding that you want to manage and click the ID in the Finding ID column.
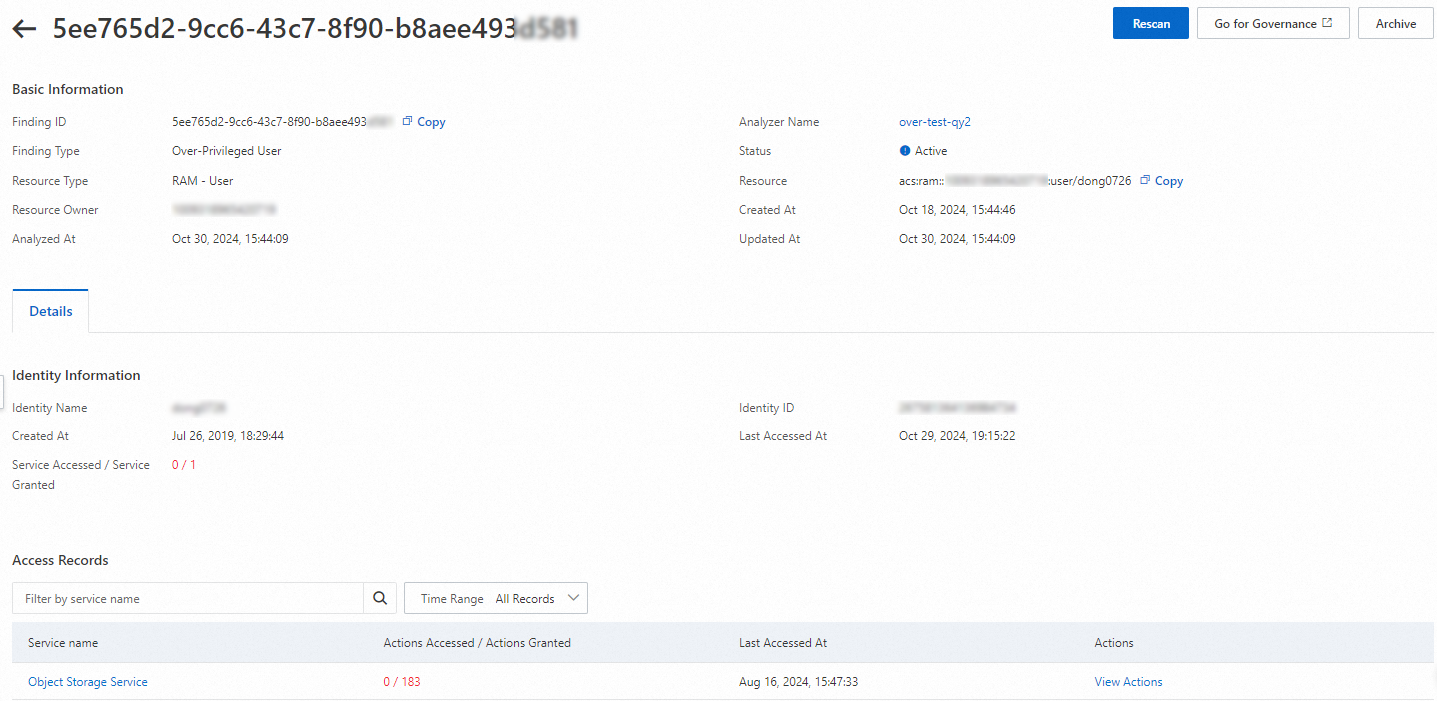
You can perform one of the following operations based on the finding:
If the granted permissions are required, click Archive to archive the finding.
If the granted permissions are not required, click Go for Governance or Copy Resource URL to perform governance operations on the corresponding page. If the resource involved belongs to the current account, click Go for Governance. Otherwise, click Copy Resource URL.
Automatically archive the findings
Apart from manually archiving a single finding, you can create archive rules to automatically archive findings that do not require governance.
On the Findings page, configure filter conditions and click Save as Archive Rule to create an archive rule. After you create the archive rule, new findings are automatically archived.
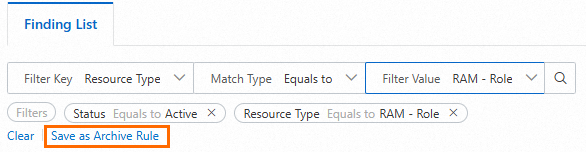
Findings that are generated before the archive rule is created are not automatically archived. To archive the findings, perform the following operations: Go to the Analyzers page, click the name in the Analyzer Name column, click the Archive Rules tab, find the required archive rule, and then click Apply Archive Rule in the Actions column.
Privileges
Cloud service | High-risk operation |
RAM | ram:AddUserToGroup |
ram:AttachPolicyToGroup | |
ram:AttachPolicyToRole | |
ram:AttachPolicyToUser | |
ram:CreateAccessKey | |
ram:CreatePolicyVersion | |
ram:DeletePolicy | |
ram:DeletePolicyVersion | |
ram:DetachPolicyFromGroup | |
ram:DetachPolicyFromRole | |
ram:DetachPolicyFromUser | |
ram:RemoveUserFromGroup | |
ram:SetDefaultPolicyVersion | |
ram:UpdateAccessKey | |
ram:UpdateRole | |
ram:CreateLoginProfile | |
ram:UpdateLoginProfile | |
ram:SetSecurityPreference | |
ram:RestoreAccessKeyFromRecycleBin | |
ram:SetUserSsoSettings | |
ram:CreateSAMLProvider | |
ram:UpdateSAMLProvider | |
ram:UpdateOIDCProvider | |
ram:AddClientIdToOIDCProvider | |
ram:AddFingerprintToOIDCProvider | |
Resource Management | ram:AttachPolicy |
ram:DetachPolicy | |
resourcemanager:EnableResourceDirectory | |
resourcemanager:CreateResourceAccount | |
resourcemanager:InviteAccountToResourceDirectory | |
resourcemanager:UpdateAccount | |
resourcemanager:DisableControlPolicy | |
resourcemanager:UpdateControlPolicy | |
resourcemanager:DeleteControlPolicy | |
resourcemanager:AttachControlPolicy | |
resourcemanager:DetachControlPolicy | |
resourcemanager:RegisterDelegatedAdministrator | |
CloudSSO | cloudsso:EnableDelegateAccount |
cloudsso:UpdateUserStatus | |
cloudsso:ResetUserPassword | |
cloudsso:SetLoginPreference | |
cloudsso:AddUserToGroup | |
cloudsso:RemoveUserFromGroup | |
cloudsso:SetExternalSAMLIdentityProvider | |
cloudsso:AddExternalSAMLIdPCertificate | |
cloudsso:AddPermissionPolicyToAccessConfiguration | |
cloudsso:RemovePermissionPolicyFromAccessConfiguration | |
cloudsso:UpdateInlinePolicyForAccessConfiguration | |
cloudsso:ProvisionAccessConfiguration | |
cloudsso:DeprovisionAccessConfiguration | |
cloudsso:CreateAccessAssignment | |
cloudsso:DeleteAccessAssignment | |
cloudsso:CreateSCIMServerCredential | |
cloudsso:UpdateSCIMServerCredentialStatus | |
cloudsso:SetSCIMSynchronizationStatus |