This topic describes how to use Resource Access Management (RAM) to limit the IP addresses that are allowed to access Alibaba Cloud resources. This ensures a higher level of data security.
Scenario
An enterprise has purchased multiple types of Alibaba Cloud resources. The resources include Elastic Compute Service (ECS) instances, ApsaraDB RDS instances, Server Load Balancer (SLB) instances, and Object Storage Service (OSS) buckets. To ensure the service and data security, the enterprise wants to allow only specified IP addresses to access the Alibaba Cloud resources.
In this case, you can create a custom policy based on business requirements. Then, create a RAM user and attach the custom policy to the RAM user. This way, the RAM user can access Alibaba Cloud resources only from the IP addresses that are specified in the custom policy.
Procedure
In this example, a RAM user is allowed to access an ECS instance only from the IP addresses 192.0.2.0/24 and 203.0.113.2.
Create a custom policy as a RAM user who has administrative rights.
Log on to the RAM console, choose in the left-side navigation pane, and then click Create Policy. On the Create Policy page, click the Visual editor or JSON tab to create a custom policy. For more information, see Create custom policies.
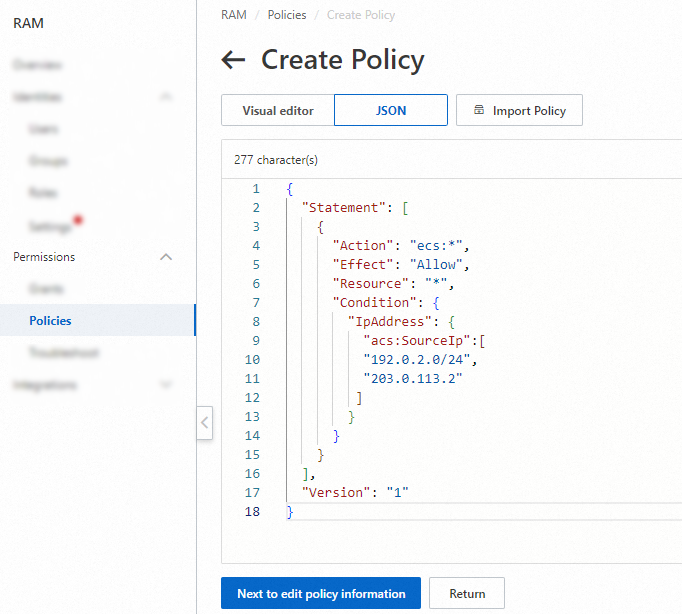
The following sample code shows the policy document:
{ "Statement": [ { "Action": "ecs:*", "Effect": "Allow", "Resource": "*", "Condition": { "IpAddress": { "acs:SourceIp":[ "192.0.2.0/24", "203.0.113.2" ] } } } ], "Version": "1" }NoteThe IP addresses in the preceding code are for reference only. You can change the value of the
acs:SourceIpelement to actual IP addresses.Create a RAM user as a RAM user who has administrative rights.
In the left-side navigation pane, choose and click Create User to create a RAM user. To ensure the account security, we recommend that you select only one access mode for the RAM user. This way, the RAM user for an individual is separated from the RAM user for a program. For more information, see Create a RAM user.
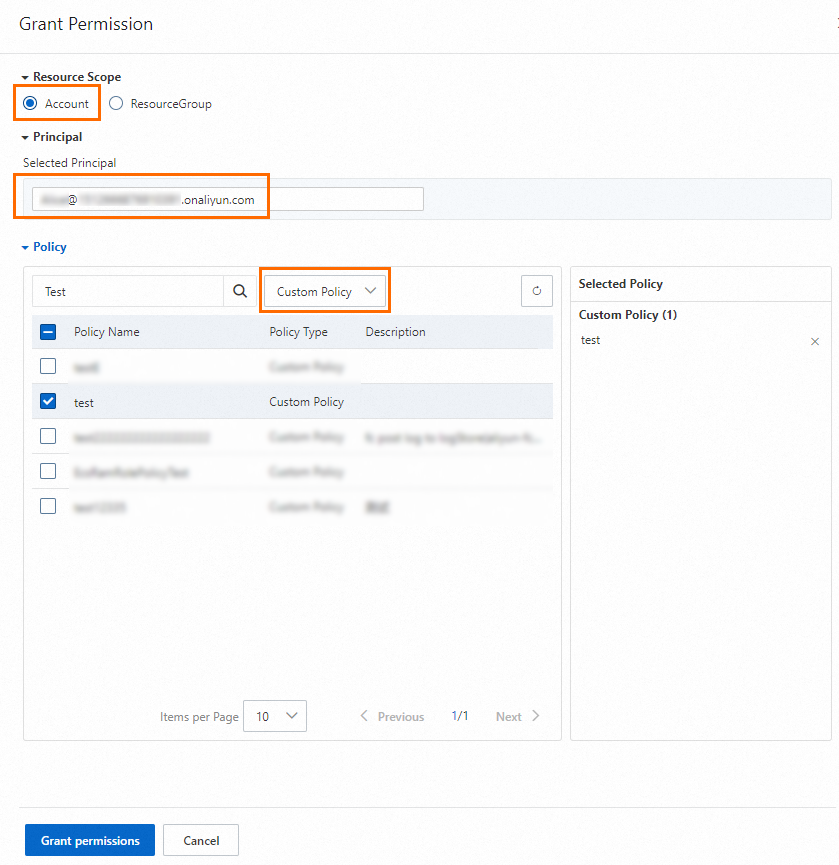
Attach the custom policy to the RAM user as a RAM user who has administrative rights.
On the Users page, find the RAM user that you created and attach the custom policy to the RAM user. For more information, see Grant permissions to a RAM user.
Use the RAM user to access an ECS instance and check whether the custom policy takes effect.
If the RAM user can access an ECS instance from the IP addresses
192.0.2.0/24and203.0.113.2specified in the custom policy and the RAM user cannot access an ECS instance from other IP addresses, the custom policy takes effect.
FAQ
What do I do if a policy does not take effect?
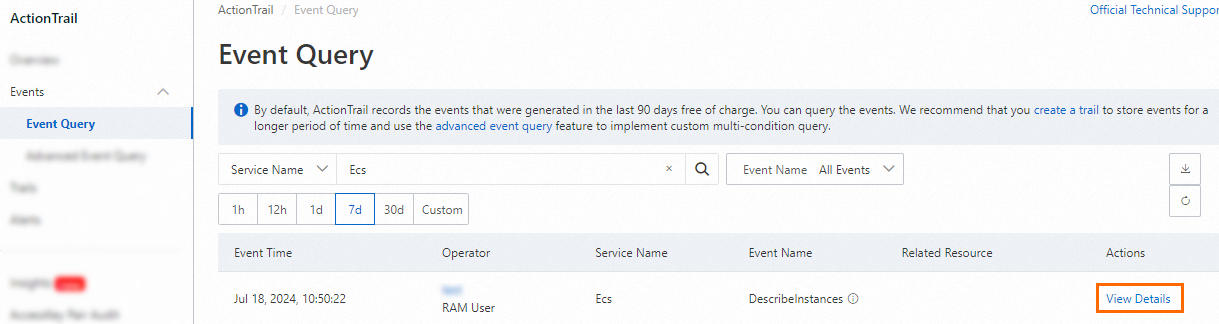
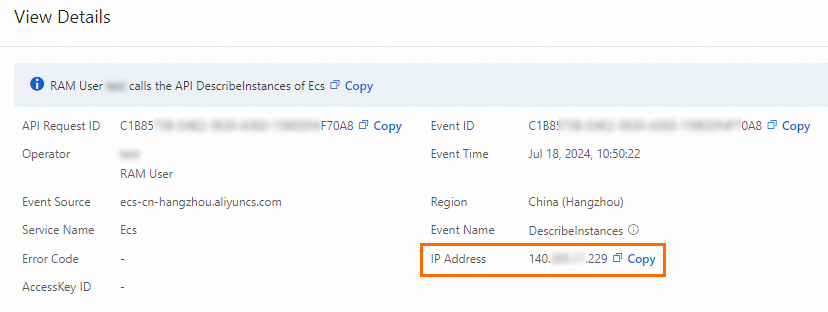
If a policy does not take effect after you attach the policy to a RAM user, the IP address specified in the policy may be incorrect. If the resources specified in the policy are Alibaba Cloud services that work with ActionTrail, view the related events in the ActionTrail console. In the event details panel, obtain the source IP address from which the RAM user initiates the request. Then, modify the IP address in the policy document and check whether the policy takes effect again.
References
This topic describes how to allow specified IP addresses to access Alibaba Cloud resources by specifying a value for the
IpAddresselement in anAllowpolicy. You can also specify a value for theNotIpAddresselement in aDenypolicy. For more information about policy examples, see Access Alibaba Cloud resources by using a specific IP address or CIDR block.For more information about policy elements such as
Effect,Action,Resource, andCondition, see Policy elements.For more information about how to view events in the ActionTrail console, see Use the event query feature to query events.
If you want to use Terraform for access control, you can use Terraform Explorer and run the code from Terraform Explorer. For more information, visit Terraform Explorer.