Background
The Domain Name System (DNS) helps translate domain names to IP addresses. It is necessary for a technology enterprise to build an internal DNS. When an enterprise migrates all its services to Alibaba Cloud, the enterprise must guarantee successful connection between the on-premises network and Alibaba Cloud to manage its business in the cloud. In this case, Alibaba Cloud DNS plays a key role in the addressing service of the enterprise. It is difficult while essential for many enterprises to use Alibaba Cloud DNS to resolve internal domain names on their on-premises networks after they migrate services to Alibaba Cloud.
This topic describes how to use Alibaba Cloud DNS for internal domain name resolution based on the virtual private network (VPN) connections to Alibaba Cloud.
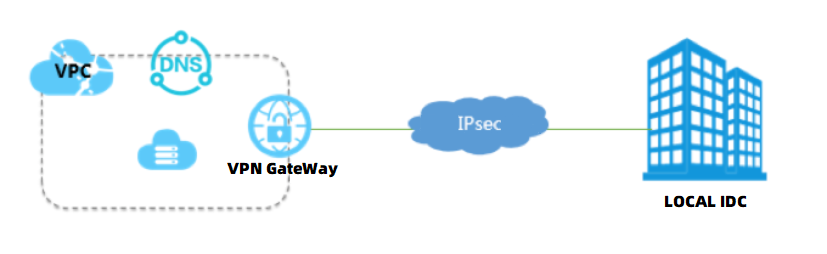
Scenarios
The DNS servers deployed in virtual private clouds (VPCs) support PrivateZone, which is the private domain name resolution service provided by Alibaba Cloud. By using the Internet Protocol security (IPsec)-VPN feature that provides a site-to-site connection, you can connect the on-premises network of your enterprise, such as the network of the on-premises data center or a branch, to a VPC. The following describes how to use the PrivateZone feature of Alibaba Cloud DNS to resolve private domain names through a VPN Gateway.
Prerequisites
The IP address of a DNS server that supports PrivateZone is prepared. The following table lists the IP addresses of available DNS servers.
No. | IP address of DNS server |
1 | 100.100.2.136/32 |
2 | 100.100.2.138/32 |
A VPN Gateway is created. To purchase a VPN Gateway, visit
https://www.alibabacloud.com/product/vpn-gateway
The configuration is as follows:
1. Create an IPsec-VPN connection between the VPN Gateway and a DNS server.
Create an IPsec-VPN connection on the VPN Gateway that you have created.
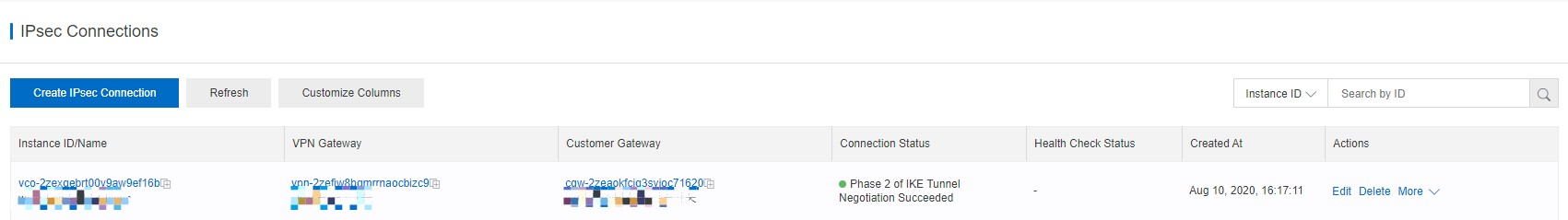
Click Edit in the Actions column. On the page that appears, turn on the Advanced Configuration switch and set the parameters as needed. The following table lists the basic configuration parameters and parameters of the Internet Key Exchange (IKE) configuration.
Parameter | Default or suggested value |
Name | Specify a custom value. |
VPN Gateway | The value is automatically generated. |
Customer Gateway | The value is automatically generated. |
Local Network | 192.168.0.0/16. Replace the value with the actual classless inter-domain routing (CIDR) block of the VPC. |
Remote Network | 10.0.0.0/24. Replace the value with the actual CIDR block of the on-premises data center. |
Effective Immediately | Yes |
Pre-Shared Key | Specify a custom value. |
Version | ikev1 |
Negotiation Mode | main |
Encryption Algorithm | aes |
Authentication Algorithm | sha1 |
DH Group | group2 |
SA Life Cycle (seconds) | 86400 |
LocalId | 39.96.2.138. Replace the value with the actual IP address of the VPN Gateway. |
Remoteld | 39.96.0.248. Replace the value with the actual IP address of the customer gateway. |
The following table lists the parameters of the IPsec configuration.
Parameter | Default or suggested value |
Encryption Algorithm | aes |
Authentication Algorithm | sha1 |
DH Group | group2 |
SA Life Cycle (seconds) | 86400 |
2. Create an IPsec-VPN connection between the VPN Gateway and the on-premises data center.
Click Create IPSec Connection to create another IPsec-VPN connection on the same VPN Gateway. Then, click Edit in the Actions column. On the page that appears, turn on the Advanced Configuration switch, set Local Network to 100.100.2.136/32, and then set other parameters to values the same as those of the IPsec-VPN connection created in the preceding step. Do not assign other values to parameters except for Local Network. Otherwise, the negotiation in the first phase might fail. The following table lists the basic configuration parameters and parameters of the IKE configuration.
Parameter | Default or suggested value |
Name | Specify a custom value. |
VPN Gateway | Specify a custom value. |
Customer Gateway | Specify a custom value. |
Local Network | 100.100.2.128/25. Replace the value with the actual CIDR block of the DNS server. |
Remote Network | 192.168.0.0/16. Replace the value with the actual CIDR block of the VPC. |
Effective Immediately | Yes |
Pre-Shared Key | Specify a custom value. |
Version | ikev1 |
Negotiation Mode | main |
Encryption Algorithm | aes |
Authentication Algorithm | sha1 |
DH Group | group2 |
SA Life Cycle (seconds) | 86400 |
LocalId | 39.96.0.248. Replace the value with the actual IP address of the VPN Gateway. |
Remoteld | 39.96.2.128. Replace the value with the actual IP address of the customer gateway. |
The following table lists the parameters of the IPsec configuration.
Parameter | Default or suggested value |
Encryption Algorithm | aes |
Authentication Algorithm | sha1 |
DH Group | group2 |
SA Life Cycle (seconds) | 86400 |
3. Contact the network engineers of your enterprise to configure your on-premises network.
Create an IPsec-VPN connection on the customer gateway that resides on your on-premises network by following the preceding parameter configuration. For more information about the configuration, see the statement of work provided by the involved device vendor.
Configure on-premises routes to direct the route 100.100.2.136/32 to the IPsec tunnel over the on-premises customer gateway.
4. Check the negotiation result of the IPsec tunnel.
The negotiation will be successful if all the configurations are correct. To resolve any issue that occurs during the configurations, contact our technical experts or the network engineers of your enterprise for help.
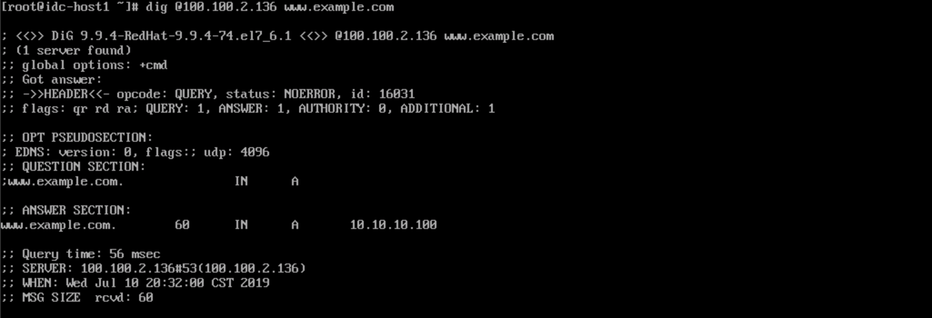
5. Verify the domain name resolution service.
Run the ping command to verify the network connectivity to the DNS server. The latency depends on the Internet connection from the on-premises data center to the VPN Gateway of Alibaba Cloud.

Use the specified DNS server, whose IP address is 100.100.2.136 in this example, to resolve a private domain name.
After the verification is passed, you can use a DNS server that is deployed in a VPC to resolve private domain names of your on-premises network through an Alibaba Cloud VPN Gateway.