You can configure permission policies in the Resource Access Management (RAM) console to secure encryption rules against malicious changes by database administrators (DBAs) or developers. This topic describes how to create a permission policy and assign the permission policy to a user or user group.
Background information
If you enable PolarDB Always-confidential, you can configure encryption rules in the PolarDB console. The encryption rules can protect content that can be queried by users from being stolen by DBAs or developers and ensure that the sensitive data of a user is accessible to only the user. For more information, see Manage encryption rules. In most cases, DBAs and developers also have the permissions to access the PolarDB console. A solution is needed to prevent DBAs and developers from maliciously changing encryption rules in the PolarDB console and ensure that sensitive data rules are secure and reliable.
You can resolve this issue by managing the permissions of RAM users in the RAM console. You can create multiple RAM users within an Alibaba Cloud account and assign the RAM users to developers and DBAs. Then, manage the permissions of the RAM users. This way, the RAM users do not have the permissions to modify the rules in the PolarDB console.
Procedure
Create a RAM user
Log on to the RAM console and create a RAM user. For more information, see Create a RAM user.
Create a permission policy
Log on to the RAM console.
In the left-side navigation pane, choose Permissions > Policies. On the Policies page, click Create Policy.
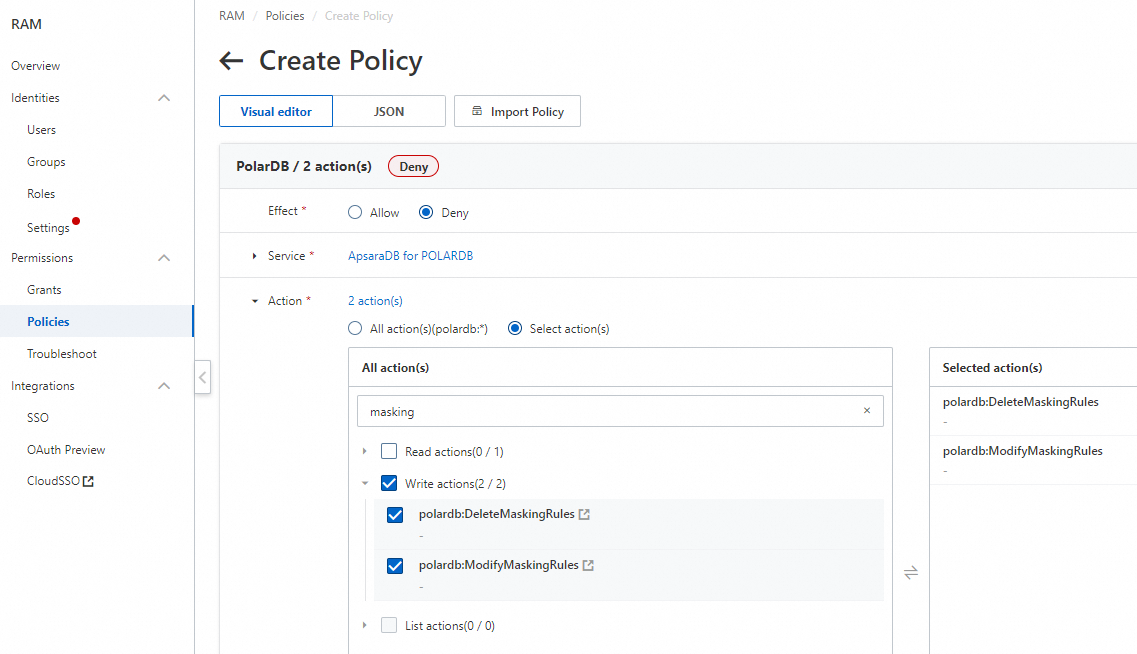
In the Visual editor tab, configure the following settings:
In the Effect section, select Deny.
In the Service section, select ApsaraDB for POLARDB.
In the Action section, expand the Write actions parameter and select
polardb:ModifyMaskingRulesandpolardb:DeleteMaskingRules. You can use the MaskingRules keyword as a filter to allow only the two actions to be displayed.
Click Next to edit policy information.
Configure the policy name and click OK. In this example, the name of the policy is set to Not allowed to modify sensitive rules. You can configure the name of the policy name based on your business requirements.
Assign a permission policy to a RAM user
Log on to the RAM console.
In the left-side navigation pane, choose Identities > Users.
Find the RAM user that you want to manage and click Add Permissions in the Actions column.
On the Add Permissions page, click Custom Policy and select the "Not allowed to modify sensitive rules" policy.
Then, click OK.
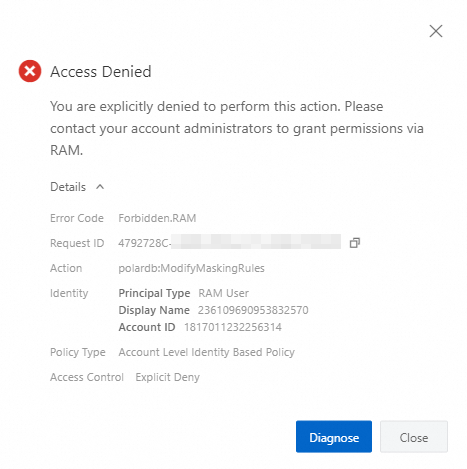
After you assign the policy to a RAM user, the RAM user cannot modify or delete the encryption rules even if the user has administrative permissions on the PolarDB cluster. If the RAM user attempts to modify encryption rules, the following error message appears: