Use a VPC policy to control which resources authorized users can access. You can combine this with a bucket policy to specify which users can access your resources. This ensures that your cloud data is accessed only from within a secure network environment and reduces the risk of unauthorized access.
Prerequisites
A virtual private cloud (VPC) is created in the same region as the bucket. For more information, see Create and manage a VPC.
Background information
The following architecture shows how to control data access at both the source and the destination:
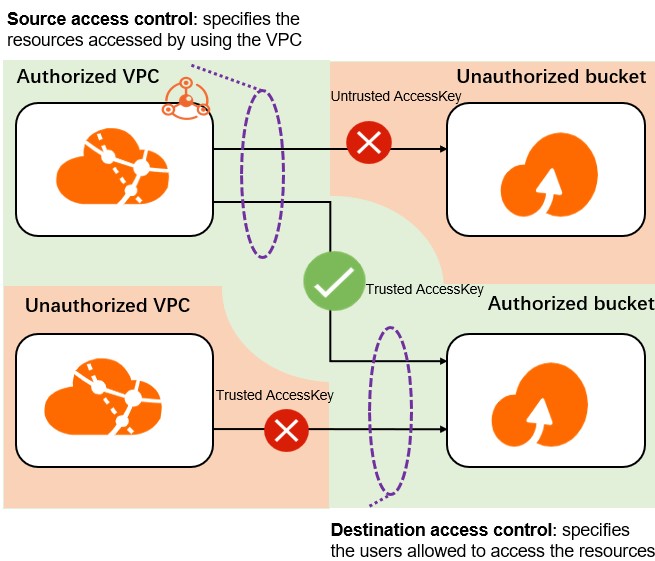
This architecture shows the following:
Allowed access
A trusted user uses an AccessKey to access an authorized bucket from within a specified VPC.
Access denied
An untrusted user uses an AccessKey to access an unauthorized bucket from within the specified VPC.
A trusted user uses an AccessKey to access an authorized bucket from outside the specified VPC.
Scenario
A user with the UID 174649585760xxxx creates a bucket named examplebucket in Object Storage Service (OSS) to store important business data. The user also creates multiple ECS instances to run services. The service environment is built in a VPC with the ID t4nlw426y44rd3iq4xxxx.
The user wants to allow only the specified VPC to access the OSS resource, examplebucket. This controls access to the data stream at the VPC source. The user also needs to block all OSS access requests from outside this VPC. This controls access to the data stream at the bucket destination.
Step 1: Configure a VPC policy
Use a VPC policy to allow the VPC with the ID t4nlw426y44rd3iq4xxxx to access only the resources in the examplebucket bucket in OSS.
Log on to the VPC console.
In the navigation pane on the left, click Endpoints.
In the top navigation bar, select the region where you want to create the gateway endpoint.
Click the Gateway Endpoints tab, and then click Create Endpoint.
On the Create Endpoint page, set the following parameters, and then click Create.
Parameter
Description
Endpoint Name
Enter a name for the gateway endpoint.
Endpoint Type
Select the type of endpoint to create. This tutorial uses Gateway Endpoint.
Endpoint Service
Click Select Service and select the endpoint service for OSS.
VPC
Select the VPC in which to create the gateway endpoint.
Route Table
Select the route table to associate with the gateway endpoint.
Resource Group
Select the resource group to which the endpoint belongs.
Description
Enter a description for the endpoint.
Endpoint Policy
Enter the following endpoint policy.
{ "Statement": [ { "Action": "oss:*", "Effect": "Allow", "Principal": ["174649585760xxxx"], "Resource": ["acs:oss:*:*:examplebucket", "acs:oss:*:*:examplebucket/*"] } ], "Version": "1" }ImportantIf a VPC policy is not configured, the VPC can access all buckets in the same region by default. If a VPC policy is configured, the VPC can access buckets in the same region only when the request is explicitly allowed by the policy.
Step 2: Configure a bucket policy
Use a bucket policy to block access to OSS resources from any VPC other than the VPC with the ID t4nlw426y44rd3iq4xxxx.
Log on to the OSS console.
In the navigation pane on the left, click Buckets, and then click examplebucket.
In the navigation pane on the left, choose Permission Control > Bucket Policy.
On the Bucket Policy tab, click Add by Syntax.
Click Edit, and then enter the following bucket policy.
ImportantIf you set
Principalto*in a policy that contains a Deny rule, ensure that the VPC can access the bucket. Otherwise, no users can access the bucket, including users who log on to the console. For testing purposes, you can specify a Resource Access Management (RAM) user as thePrincipal. If you encounter access issues, you can log on to the console with your Alibaba Cloud account to modify the policy.{ "Statement" : [ { "Action": ["oss:*"], "Effect": "Deny", "Principal": ["*"], "Resource": "acs:oss:*:*:*", "Condition": { "StringNotEquals" : { "acs:SourceVpc": ["vpc-t4nlw426y44rd3iq4xxxx"] } } } ] , "Version": "1" }Click Save. In the dialog box that appears, click OK.