This topic describes the causes and solutions for 403 errors returned by OSS.
AbnormalBucketOwnerStatus
This error is returned when the account of the bucket owner has an abnormal status.
The status of the bucket owner is abnormal
Cause: The service is unavailable to the owner of the target bucket.
Solution: Check whether the user's Alibaba Cloud account has been deleted or is restricted for security reasons. Also, confirm whether the service has been suspended by Alibaba Cloud due to overdue payments.
AccessDenied
This error is returned when a user does not have the permissions to perform a specific operation.
Access denied by authorizer's policy
Cause: You do not have the required permissions to perform the operation.
Solution: The final permissions of a Security Token Service (STS) token are the intersection of the permissions of the RAM role that you configure in Step 4 and the permissions that you specify in the policy in Step 5. Use the following examples to check the intersection of the permissions that you configured in the two steps.
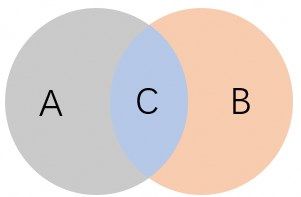
Example 1
In the following figure, A indicates the permissions of the RAM role, B indicates the permissions specified by the policy parameter, and C is the final permissions of the temporary credentials.
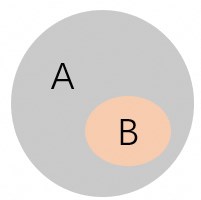
Example 2
In the following figure, A indicates the permissions of the RAM role, and B indicates the permissions specified by the policy parameter. The permissions specified by the policy parameter are a subset of the permissions of the RAM role. Therefore, B is the final permissions of the temporary credentials.
Access denied by bucket policy
Cause: Access is denied by the bucket policy.
Solution: Configure the bucket policy to grant the required permissions. For more information, see Configure bucket policies to authorize other users to access specified resources.
Access denied by VPC endpoint policy
Cause: A policy configured for the VPC where the client resides prevents access to unauthorized buckets within the VPC environment.
Solution: Check the policy that is configured for the VPC where the client resides.
AccessDenied
Cause: You do not have the required access permissions.
Solution:
Ensure that you use the correct AccessKey ID and AccessKey secret. For more information, see Create an AccessKey pair.
Ensure that the RAM user has the required permissions to perform operations on the bucket or object.
Anonymous access is forbidden for this operation
Cause: Anonymous users do not have the required permissions to perform the operation.
Solution: Use a bucket policy to grant anonymous users the permissions to access specified resources in the target bucket. For more information, see Configure bucket policies to authorize other users to access specified resources.
Anonymous user has no right to access this bucket
Cause: Anonymous users do not have the required permissions to access this bucket.
Solution: Use a bucket policy to grant anonymous users the permissions to access the target bucket. For more information, see Configure bucket policies to authorize other users to access specified resources.
Anonymous user has no right to access this object
Cause: Anonymous users do not have the required permissions to access this object.
Solution: Use a bucket policy to grant anonymous users the permissions to access specified resources in the target bucket. For more information, see Configure bucket policies to authorize other users to access specified resources.
Hierarchical namespace is disabled
Cause: The hierarchical namespace feature is disabled for the bucket.
Solution: Enable the hierarchical namespace feature when you create the bucket. Then, you can rename the directory or file. For more information about the regions that support the hierarchical namespace feature and the scenarios in which this feature can be used, see Enable the hierarchical namespace feature.
Invalid according to Policy: Policy Condition failed: " + RelatedUnit; //XXX
Cause: The conditions specified in the policy form field are invalid.
Solution: Ensure that you specify valid conditions in the policy form field. For more information about the supported conditions and matching methods in the policy form field, see Appendix: Post Policy.
Invalid according to Policy: Policy Condition failed: ["eq", "$Content-Type", "image/png"]
Cause: The type of the file to upload does not match the specified Content-Type.
Solution: The Content-Type in a policy is used to limit the type of file that you can upload using a form. If Content-Type is limited to `image/png`, you can upload only files of the `image/png` type. To upload files of other types, add the corresponding Content-Type value to the policy. For a list of common Content-Type values, see How do I set Content-Type (MIME)?.
Invalid according to Policy: Policy expired
Cause: The policy specified in the PostObject request has expired.
Solution: The `policy` form field in a Post request is used to verify the validity of the request. A policy is a JSON text that is encoded in UTF-8 and Base64. The policy declares the conditions that the Post request must meet, including an expiration time. Ensure that the expiration time specified in the policy has not passed. The following code shows the format of a Post policy:
{ "expiration": "2014-12-01T12:00:00.000Z", "conditions": [ {"bucket": "johnsmith" }, ["starts-with", "$key", "user/eric/"] ] }For more information about the conditions supported in a policy, see Appendix: Post Policy.
Invalid date (should be seconds since epoch)
Cause: The timestamp of the request is invalid.
Solution: The value of the `Expires` parameter must be a Unix time, which is the number of seconds that have elapsed since 00:00:00 UTC on January 1, 1970. This value specifies the expiration time of the URL.
Query string authentication requires the Signature, Expires and OSSAccessKeyId parameters
Cause: The signed URL is missing required parameters.
Solution: A signed URL must contain at least the `Signature`, `Expires`, and `OSSAccessKeyId` parameters. The following is an example of a signed URL:
http://oss-example.oss-cn-hangzhou.aliyuncs.com/oss-api.pdf?OSSAccessKeyId=nz2pc56s936**9l&Expires=1141889120&Signature=vjbyPxybdZaNmGa%2ByT272YEAiv****. For more information about signed URLs, see Include a signature in a URL.
Request has expired
Cause: The request has expired.
Solution: Set a reasonable value for the `Expires` parameter. For more information about how to set `Expires` when you upload a file, see PutObject, PostObject, AppendObject, and InitiateMultipartUpload.
Target object does not reside in the same data center as source object
Cause: Cross-region file copy is not supported.
Solution: Objects can be copied only between buckets in the same region. The buckets can be the same or different. For more information, see CopyObject.
The bucket you are attempting to access must be addressed using the specified endpoint. Please send all future requests to this endpoint
Cause: The endpoint used to access the bucket is incorrect.
Solution: Ensure that you use the correct endpoint to access the bucket. For example, if a bucket is in the
oss-cn-hangzhouregion, its public endpoint isoss-cn-hangzhou.aliyuncs.com. For more information about endpoints, see Access OSS over IPv6.
This request is forbidden by kms
Cause: You do not have the required permissions to use KMS.
Solution: Ensure that you have the permissions to use the specified customer master key (CMK) ID. For more information, see Server-side encryption.
You are denied by bucket referer policy
Cause: Hotlink protection verification failed.
Solution: You can restrict access to resources in a bucket by configuring hotlink protection. This involves setting a Referer whitelist and specifying whether to allow empty Referers. Only domain names in the whitelist can access the resources. For more information, see Configure hotlink protection.
You do not have read acl permission on this object
Cause: You do not have the required permissions to read the ACL of the object.
Solution: Contact the object owner to grant you the `GetObjectACL` permission.
You do not have read permission on this object
Cause: You do not have the required permissions to read the object.
Solution: Contact the object owner to grant you the permissions to read the object.
You do not have write acl permission on this object
Cause: You do not have the required permissions to write to the ACL of the object.
Solution: Contact the object owner to grant you the `PutObjectACL` permission.
You do not have write permission on this object
Cause: You do not have the required permissions to write to the object.
Solution: Contact the object owner to grant you the permissions to write to the object.
You have no right to access this object
Cause: The RAM user does not have the required permissions to access this object.
Solution: Confirm whether the RAM user has the required permissions to perform operations on the object. For more information about how to set different access permissions for different scenarios, see Tutorial: Use RAM policies to control access to OSS.
You have no right to access this object because of bucket acl
Cause: You do not have the required permissions to access the object.
Solution: Grant the user the required OSS access permissions, such as `PutObject`, `GetObject`, and `AppendObject`. For more information, see Common examples of RAM policies.
AccessForbidden
This error is returned when a cross-origin resource sharing (CORS) request is not allowed or other access restrictions are in place.
CORSResponse: This CORS request is not allowed. This is usually because the evalution of Origin, request method / Access-Control-Request-Method or Access-Control-Requet-Headers are not whitelisted by the resource's CORS spec
Cause: CORS is not configured or the CORS configuration is incorrect.
Solution: For more information, see Configure cross-origin resource sharing.
AccessKeyIdAndSecurityTokenNotMatch
This error is returned when the provided AccessKey ID and security token do not match.
The OSS access key id and security token you provided does not match
Cause: The AccessKey pair provided by the user does not match the STS token.
Solution: For more information, see Use an STS token to access OSS.
BucketDisable
This error is returned when the bucket is disabled for security reasons.
BucketDisable
Cause: The bucket is disabled for security reasons.
Solution: Check whether your account has overdue payments, or contact technical support to perform a security check.
BucketNotBelongTo
This error is returned when a user attempts to access a bucket that does not belong to them.
The bucket you access does not belong to you
Cause: The current user is not the owner of the target bucket.
Solution: Only the bucket owner has the required permissions to perform this operation.
CnameDenied
This error is returned when a domain name binding operation is denied.
The cname belongs to another user
Cause: The domain name is already bound to another bucket.
Solution: Change the domain name, or verify the ownership of the domain name to forcibly bind it. Verifying the ownership of the domain name unbinds it from the other bucket. For more information, see Bind a custom domain name.
ImageDamage
This error is returned when an uploaded or processed image file is damaged and cannot be identified.
The image file may be damaged
Cause: The image file is missing information or is damaged, which prevents the system from identifying or processing it.
Solution: Ensure the integrity of the source file. If the file is damaged, upload the local file again.
InvalidAccessKeyId
This error is returned when the provided AccessKey ID is in an incorrect format, does not exist, or is disabled.
The OSS Access Key Id contains non-acceptable characters, which accepts only alphanumeric characters[0-9a-zA-Z] and several special characters[._=]
Cause: The entered AccessKey ID contains unsupported characters.
Solution: Re-enter the correct AccessKey ID of the RAM user or Alibaba Cloud account. For more information, see Create an AccessKey pair.
The OSS Access Key Id you provided does not exist in our records
Cause: The temporary access credential has expired.
Solution: Use a temporary AccessKey pair (AccessKey ID and AccessKey secret) to request a temporary access credential from the app server. For more information, see Obtain a temporary access credential.
The OSS Access Key Id you provided is disabled
Cause: The AccessKey ID is disabled.
Solution: Re-enable the AccessKey pair.
InvalidObjectState
This error is returned when an object is in a state that does not support the current operation.
The operation is not valid for the object's state
Cause: When you download an Archive object, an invalid object state error occurs in the following two cases:
A `RestoreObject` request was not submitted, or the last submitted `RestoreObject` request has timed out.
A `RestoreObject` request was submitted, but the data restoration operation is not complete.
Solution: For more information, see RestoreObject.
InvalidSecurityToken
This error is returned when the provided security token is invalid.
The security token you provided is invalid
Cause: The STS token is invalid.
Solution: For more information, see Use an STS token to access OSS.
KmsInDebt
This error is returned when access to the KMS service is denied because the Alibaba Cloud account has an overdue payment.
Current user is indebted
Cause: When your Alibaba Cloud account has an overdue payment, your access to Key Management Service (KMS) is denied.
Solution: Ensure that your Alibaba Cloud account does not have an overdue payment.
KmsInDebtOverdue
This error is returned when a payment for the KMS service is overdue.
Current user is indebted Overdue
Cause: A payment for the KMS service is overdue.
Solution: Renew the KMS service promptly to ensure continued use.
KmsUbsmsInvalidBid
This error is returned when the requester has not activated the KMS service.
Your account partner does not have KMS Service
Cause: The requester has not activated the KMS service.
Solution: Before you use server-side encryption with KMS-managed keys (SSE-KMS) to encrypt OSS data, you must activate the KMS service. For more information, see Activate KMS.
NonStandardHostForbidden
This error is returned when the host used does not conform to the standard OSS domain name format.
Your host is invalid. Please use Open Storage Service standard host
Cause: The host format is incorrect.
Solution: Use the standard domain name format to access OSS resources. For more information, see Access OSS over IPv6.
PermanentRedirect
This error is returned when the endpoint used to access a bucket is inconsistent with the actual endpoint of the region where the bucket is located.
The bucket you are attempting to access must be addressed using the specified endpoint. Please send all future requests to this endpoint
Cause: When you use an SDK to access a bucket in OSS, the endpoint is not specified or an incorrect endpoint is specified. For example, this error occurs if you create a bucket in the China (Qingdao) region but use the default endpoint
oss-cn-hangzhou.aliyuncs.comto send a request.Solution: Ensure that the endpoint in the request is the same as the actual endpoint of the bucket. For example, to access buckets in the China (Qingdao) and China (Hangzhou) regions, we recommend that you create multiple OSS clients and configure the clients with the
oss-cn-hangzhou.aliyuncs.comandoss-cn-qingdao.aliyuncs.comendpoints respectively.
RequestTimeTooSkewed
This error is returned when the difference between the request time and the current time on the OSS server is too large.
The difference between the request time and the current time is too large
Cause: The request is initiated more than 15 minutes after or before the current time on the OSS server.
Solution: Check the system time of the device that sends the request and adjust it to the correct time based on the time zone.
The system time of the device that sends the request is adjusted based on the following standards:
OSS uses Greenwich Mean Time (GMT). The system time of your device must be adjusted to GMT or its corresponding time zone. GMT is the time in the zero time zone, also known as Coordinated Universal Time (UTC).
To view the time zone on a Windows system, click .
For example, +08:00 in the time zone bar indicates that the system time zone of the device is UTC+8.
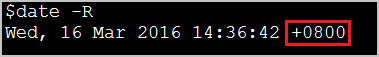
To view the time zone on a Linux or Unix system, run the
date -Rcommand to view the time and time zone.In the following figure, +0800 indicates that the system time zone of the device is UTC+8.
OSS is available in multiple regions, and all regions use GMT for timekeeping. The system time of the device sending the request must be synchronized with a standard time source.
SecondLevelDomainForbidden
This error is returned when you use a second-level domain name to access OSS or the domain name format is incorrect.
Please use virtual hosted style to access
Cause: The host format is incorrect.
Solution: When you access the OSS service over the internet, use a URL to represent the OSS resource that you want to access. The structure of an OSS URL is
<Schema>://<Bucket>.<Public Endpoint>/<Object>. `Schema` can be `HTTP` or `HTTPS`. `Bucket` is the name of your bucket. `Public Endpoint` is the endpoint for public access to the data center where the bucket is located. `Object` is the access path of the file uploaded to OSS.For example, if the region is China (Hangzhou), the bucket name is `examplebucket`, and the object access path is
destfolder/example.txt, the access URL ishttps://examplebucket.oss-cn-hangzhou.aliyuncs.com/destfolder/example.txt.
The bucket you are attempting to access must be addressed using OSS third level domain
Cause: The request domain name for the bucket is not a third-level domain name.
Solution: For network requests to OSS, all request domain names must be third-level domain names that contain information about the specified bucket, except for the `GetService` (ListBuckets) API operation. The structure of a domain name is
BucketName.Endpoint. `BucketName` is the name of your bucket, and `Endpoint` is the regional endpoint of the bucket. Example:https://examplebucket.oss-cn-hangzhou.aliyuncs.com.
SecurityTokenExpired
This error is returned when the provided security token has expired.
The security token you provided has expired
Cause: The STS token has expired.
Solution: Request a new STS token from the STS service.
SecurityTokenNotSupported
This error is returned when a security token is used in a region or for an API operation that does not support STS tokens.
Security token is not supported in this region
Cause: The current region does not support the use of STS tokens.
Solution: For more information about which regions support the use of STS tokens, see Endpoints.
This interface does not support security token
Cause: The current API operation cannot be called using the permissions of an STS token.
Solution: STS tokens are suitable only for temporarily authorizing specific users to access OSS resources. To grant other users access to a bucket, see Access control overview to select an appropriate authorization mechanism.
SignatureDoesNotMatch
This error is returned when the signature provided by the client is inconsistent with the signature calculated by the server.
The request signature we calculated does not match the signature you provided
Cause: When you use an API operation or an SDK to access OSS, the client must include signature information for the OSS server to perform identity authentication. If the server returns this error message, the signature provided in the request is inconsistent with the signature calculated by the server, and the request is rejected.
Solution: Perform the following steps to troubleshoot the issue.
Ensure that the AccessKey ID and AccessKey secret used for signing are correct.
You can use the AccessKey ID and AccessKey secret to log on to ossbrowser to verify that they are correct. For more information, see Install ossbrowser 1.0.
Check whether the signature algorithm is correct.
OSS provides two request methods that include signatures: Include a signature in the header and Include a signature in the URL. The algorithms for these two signature methods are as follows:
Include a signature in the header
StringToSign = VERB + "\n" + Content-MD5 + "\n" + Content-Type + "\n" + Date + "\n" + CanonicalizedOSSHeaders + CanonicalizedResource Signature = base64(hmac-sha1(AccessKeySecret, StringToSign)Include a signature in the URL
StringToSign = VERB + "\n" + CONTENT-MD5 + "\n" + CONTENT-TYPE + "\n" + EXPIRES + "\n" + CanonicalizedOSSHeaders + CanonicalizedResource Signature = urlencode(base64(hmac-sha1(AccessKeySecret, StringToSign)))
If your business scenario allows, we recommend that you use an SDK to access OSS. This way, you do not need to manually calculate the signature. For more information, see Use an Alibaba Cloud SDK to initiate a request.
Compare the
StringToSignfield in the response body with the content of your request to check for differences.The
StringToSignfield indicates the string-to-sign. The string-to-sign is the content that needs to be encrypted using the AccessKey secret in the signature algorithm.The following code provides a request example:
PUT /bucket/abc?acl Date: Wed, 24 May 2023 02:12:30 GMT Authorization: OSS qn6q**************:77Dv**************** x-oss-abc: mymetaThe string-to-sign calculated for the preceding request is:
PUT\n\n\nWed, 24 May 2023 02:12:30 GMT\nx-oss-abc:mymeta\n/bucket/abc?acl
TransferAccelerationDisabled
This error is returned when transfer acceleration is used in a region where this feature is not supported.
Transfer acceleration is disabled
Cause: The current region does not support the transfer acceleration feature.
Solution: Contact technical support to resolve this issue.
UserDisable
This error is returned when the user account is disabled or the OSS service is not activated.
UserDisable
Causes:
The account has an overdue payment or is disabled for security reasons.
The OSS service is not activated.
Solutions:
Check whether the account has an overdue payment, or contact technical support to perform a security check.
Activate the OSS service.
WORMConfigurationLocked
This error is returned when an attempt is made to delete a retention policy after it is locked.
The WORM Configuration is locked
Cause: An attempt is made to delete a retention policy after it is locked.
Solution: After a retention policy is locked, you cannot delete the policy or shorten its retention period. You can only extend the retention period. For more information, see Retention policies.