Simple Message Queue (formerly MNS) allows an Alibaba Cloud account to grant permissions on resources to Resource Access Management (RAM) users. This prevents risks of exposing the AccessKey pair of the Alibaba Cloud account. Only authorized RAM users are allowed to manage resources in the SMQ console, and publish and subscribe to messages by using SDKs or API operations.
Scenarios
Enterprise A purchases the SMQ service. The employees of Enterprise A need to manage SMQ resources, such as queues and topics. Employees with different roles require different permissions.
The following section describes specific scenarios:
For security reasons, Enterprise A does not want to disclose the AccessKey pair of its Alibaba Cloud account to employees. Instead, Enterprise A wants to create different RAM users for the employees and grant different permissions to the RAM users.
A RAM user can only use resources for which the user is authorized. Resource usage and costs are not separately calculated for the RAM user. All expenses are billed to the Alibaba Cloud account of Enterprise A.
Enterprise A can revoke the permissions granted to a RAM user and delete a RAM user at any time.
In this scenario, the Alibaba Cloud account of Enterprise A can grant its employees fine-grained permissions on resources.
Method 1: Grant permissions to a RAM user on the Users page
Log on to the RAM console as a RAM administrator.
In the left-side navigation pane, choose .
On the Users page, find the required RAM user, and click Add Permissions in the Actions column.
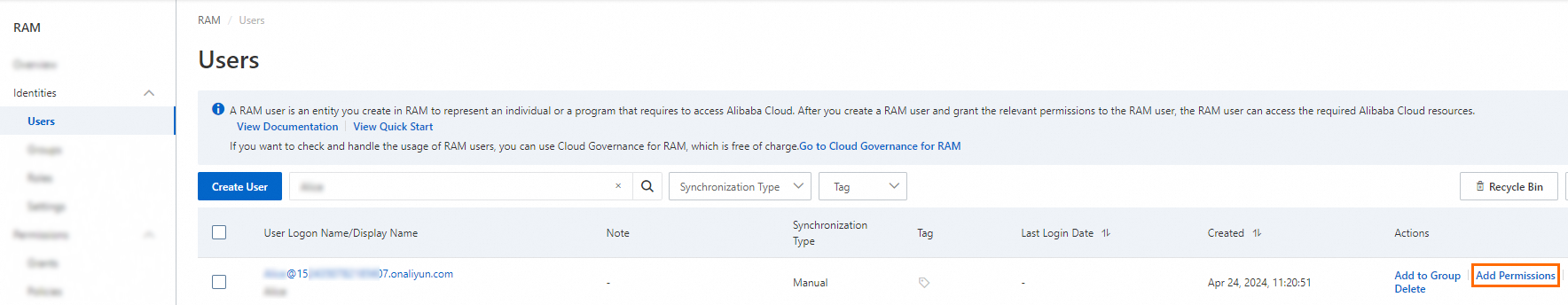
You can also select multiple RAM users and click Add Permissions in the lower part of the page to grant permissions to the RAM users at a time.
In the Grant Permission panel, grant permissions to the RAM user.
Configure the Resource Scope parameter.
Account: The authorization takes effect on the current Alibaba Cloud account.
ResourceGroup: The authorization takes effect on a specific resource group.
ImportantIf you select Resource Group for the Resource Scope parameter, make sure that the required cloud service supports resource groups. For more information, see Services that work with Resource Group. For more information about how to grant permissions on a resource group, see Use a resource group to grant a RAM user the permissions to manage a specific ECS instance.
Configure the Principal parameter.
The principal is the RAM user to which you want to grant permissions. The current RAM user is automatically selected.
Configure the Policy parameter.
A policy contains a set of permissions. Policies can be classified into system policies and custom policies. You can select multiple policies at a time.
System policies: policies that are created by Alibaba Cloud. You can use but cannot modify these policies. Version updates of the policies are maintained by Alibaba Cloud. For more information, see Services that work with RAM.
NoteThe system automatically identifies high-risk system policies, such as AdministratorAccess and AliyunRAMFullAccess. We recommend that you do not grant unnecessary permissions by attaching high-risk policies.
Custom policies: You can manage and update custom policies based on your business requirements. You can create, update, and delete custom policies. For more information, see Create a custom policy.
Click Grant permissions.
Click Close.
Method 2: Grant permissions to a RAM user on the Grants page
Log on to the RAM console as a RAM administrator.
In the left-side navigation pane, choose .
On the Permission page, click Grant Permission.
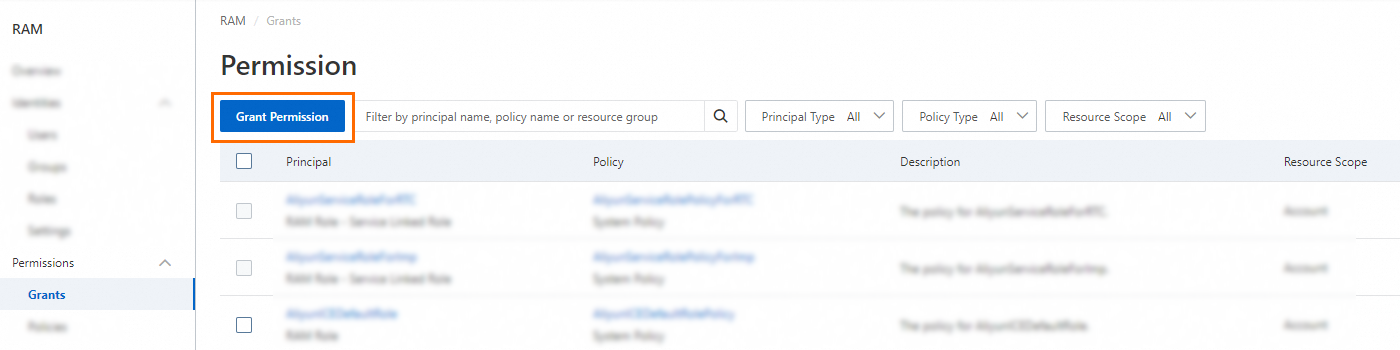
In the Grant Permission panel, grant permissions to the RAM user.
Configure the Resource Scope parameter.
Account: The authorization takes effect on the current Alibaba Cloud account.
Resource Group: The authorization takes effect on a specific resource group.
ImportantIf you select Resource Group for the Resource Scope parameter, make sure that the required cloud service supports resource groups. For more information, see Services that work with Resource Group. For more information about how to grant permissions on a resource group, see Use a resource group to grant a RAM user the permissions to manage a specific ECS instance.
Configure the Principal parameter.
The principal is the RAM user to which you want to grant permissions. You can select multiple RAM users at a time.
Configure the Policy parameter.
A policy contains a set of permissions. Policies can be classified into system policies and custom policies. You can select multiple policies at a time.
System policies: policies that are created by Alibaba Cloud. You can use but cannot modify these policies. Version updates of the policies are maintained by Alibaba Cloud. For more information, see Services that work with RAM.
NoteThe system automatically identifies high-risk system policies, such as AdministratorAccess and AliyunRAMFullAccess. We recommend that you do not grant unnecessary permissions by attaching high-risk policies.
Custom policies: You can manage and update custom policies based on your business requirements. You can create, update, and delete custom policies. For more information, see Create a custom policy.
Click Grant permissions.
Click Close.
What to do next
After you create a RAM user by using an Alibaba Cloud account, you can distribute the RAM user name and password or AccessKey pair information of the RAM user to other employees. Other employees can log on to the console or call an API operation of the service as the RAM user based on the following steps:
Log on to the console.
Open the RAM User Logon page in the browser.
On the RAM User Logon page, enter the RAM user name and then click Next. Enter the password of the RAM user and then click Login.
NoteThe RAM user name is in the format of
<$username>@<$AccountAlias>or<$username>@<$AccountAlias>.onaliyun.com.<$AccountAlias>is the account alias. If an account alias is not set, the ID of the Alibaba Cloud account is used by default.On the homepage of the console, click an authorized service to access the console of this service.
Call an API operation with the AccessKey pair of the RAM user.
Use the AccessKey ID and AccessKey secret of the RAM user in the code.