This topic describes how to create RAM users for an Alibaba Cloud account and authorize them to access different resources.
Procedure
Log on to the RAM console by using an Alibaba Cloud account or as a RAM administrator.
In the left-side navigation pane, choose .
On the Users page, click Create User.
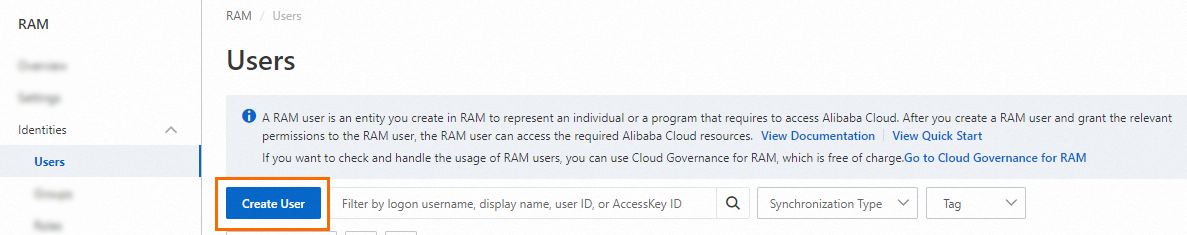
In the User Account Information section of the Create User page, configure the following parameters:
Logon Name: The logon name can be up to 64 characters in length, and can contain letters, digits, periods (.), hyphens (-), and underscores (_).
Display Name: The display name can be up to 128 characters in length.
Tag: Click the
 icon and enter a tag key and a tag value. Adding tags helps you categorize and manage RAM users.
icon and enter a tag key and a tag value. Adding tags helps you categorize and manage RAM users.
NoteYou can click Add User to create multiple RAM users at a time.
Select an Access Mode and configure the corresponding parameters.
Click OK and complete the security verification. An AccessKey pair is automatically generated for the RAM user.
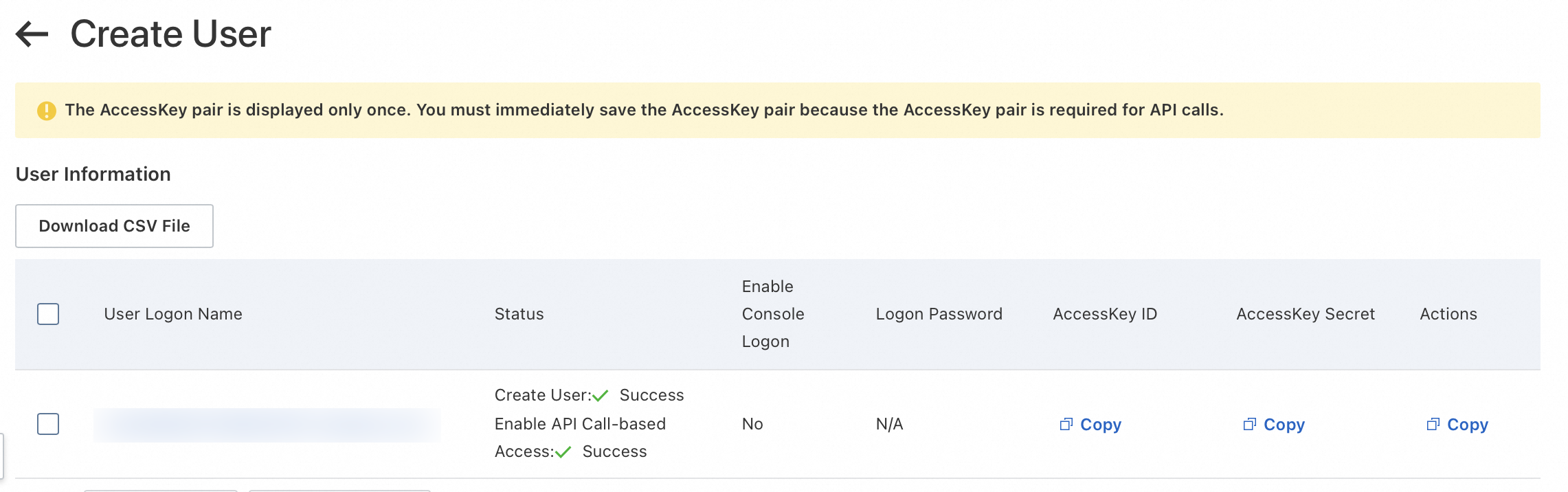
Click Copy in the Actions column and save the copied user information including the AccessKey ID and AccessKey secret.
ImportantKeep the AccessKey pair secure. The AccessKey secret is displayed only when the RAM user is created. You cannot view the AccessKey secret after you close the creation page.
On the Users page, find the created RAM user and click Add Permissions in the Actions column.
In the Grant Permission panel, grant permissions to the RAM user.
Specify the authorization scope.
Set the Resource Scope parameter to Account. Intelligent Media Services (IMS) does not allow you to set the Resource Scope parameter to ResourceGroup. For more information about resource groups, see Differences and relationships among the Resource Directory, Resource Group, and Tag services.
- Specify the principal. The principal is the RAM user to which you want to grant permissions. By default, the current RAM user is specified. You can also specify another RAM user.
Select policies in the Policy section.
Use system policies
Select System Policy from the drop-down list, enter AliyunICE in the search box, and then select system policies based on your business requirements.
Policy
Description
API operation
AliyunICEFullAccess
Permissions to manage and operate all IMS resources
This policy grants permissions on all operations of IMS.
AliyunICEReadOnlyAccess
Read-only permissions on all IMS resources
This policy grants permissions on all read-only operations of IMS, such as Get, Describe, Search, and List operations.
Use custom policies
Select Custom Policy from the drop-down list and select custom policies based on your business requirements. If no custom policies are available, you can create one. For more information, see Create custom policies or the Sample custom policies section of this topic.
NoteYou can attach a maximum of five policies to a RAM user at a time. If you want to attach more than five policies to a RAM user, repeat the operation.
To control risks, we recommend that you abide by the principle of least privilege.
If you want to use IMS SDK for iOS or Android, you must specify the
AliyunOSSFullAccesspolicy or a custom Object Storage Service (OSS) policy based on your business requirements. This is because the SDK needs to upload files to OSS.
Click Grant permissions.
Optional. Authorize the RAM user to log on to the Alibaba Cloud Management Console. For more information, see the "Enable console logon for a RAM user" section of the Manage console logon settings for a RAM user topic.
Sample custom policies
This section describes only the parameters of the sample policy for granting the read-only permissions on some IMS resources. The parameters of other sample policies in this section are not described because the parameters are similar.
Grant the read-only permissions on some IMS resources
{ "Version": "1", "Statement": [ { "Action": [ "ice:GetMediaProducingJob", "ice:GetEditingProject", "ice:GetMediaInfo", "ice:ListMediaBasicInfos", "ice:SearchEditingProject" ], "Resource": "*", "Effect": "Allow", "Condition": { "IpAddress": { "acs:SourceIp": "192.168.0.1" } } } ] }Parameter description
Parameter
Required
Description
Version
Yes
The policy version. Set the value to 1 for IMS.
Statement
Yes
The statement. A single policy can contain multiple statements. Each statement contains the following elements: Action, Resource, Effect, and Condition.
Action
Yes
The action. Each action corresponds to an API operation. Specify the value in the
ice:API operation nameformat. Separate multiple actions with commas (,). You can specify multiple actions to configure a permission group.Resource
Yes
The one or more IMS resources that can be accessed by authorized users. Asterisks (
*) can be used as wildcards. Specify the value in theacs:ice:<regionId>:<accountId>:*format. The Resource parameter can also have multiple values, which means multiple resources. TheregionIdfield is not supported. Set the regionId field to*. IMS does not classify resources. We recommend that you set the Resource parameter to an asterisk (*) oracs:ice:*:*:*if you want to grant permissions on media assets.Effect
Yes
Specifies whether a statement result is an explicit allow or an explicit deny. Valid values: Allow and Deny. The system checks the statements one by one for each request. If the value of the Effect parameter is
Allowin all matched statements, the request is allowed. If the value of the Effect parameter isDenyin one matched statement or no statements are matched, the request is denied.ImportantIf a policy includes both an
Allowstatement and aDenystatement, theDenystatement takes precedence over the Allow statement.Condition
No
The access control conditions of the policy. For more information, see the "Condition" section of the Policy elements topic.
Grant the read-only permissions on all IMS resources
{ "Version": "1", "Statement": [ { "Action": [ "ice:Get*", "ice:List*", "ice:Search*", "ice:Describe*" ], "Resource": "acs:ice:*:*:*", "Effect": "Allow" } ] }Grant full permissions including the write permissions on IMS resources
{ "Statement": [ { "Effect": "Allow", "Action": "ice:*", "Resource": "acs:ice:*:*:*" } ], "Version": "1" }